IPFS Connect Istanbul 2023: IPVM - Bringing Wasm-Based Edge Compute to IPFS

[docdrop](IPFS Connect Istanbul 2023: IPVM - Bringing Wasm-Based Edge Compute to IPFS

15 views 22 Nov 2023
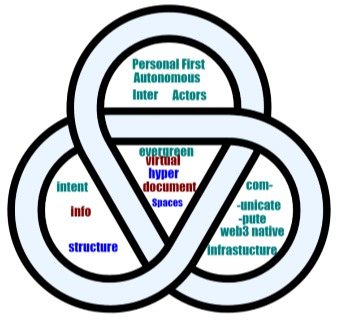
The advent of TCP/IP and the web produced an explosion of innovation by radically lowering the barrier to entry to connect over the network. Thanks to new technical and social innovations, we now have the building blocks for the next generation of open services: location-free verifiable data and computation.
Verifiable computation opens the door to content-addressed function invocations, results, and workflows. This radically lowers the complexity of historical architectures (e.g. the LAMP stack), networked, and distributed systems. Not only is this easier to reason about, it also (paradoxically) enables superlinear scaling: the more it gets used, the more efficient it becomes!
This talk presents UCAN Invocations and the Interplanetary VM (IPVM). Code in this model can run anywhere (even offline), respects data privacy, and services interoperate seamlessly out of the box without pre-negotiation. Since computation doesn't happen in a vacuum, we will also describe how the workflow planner interacts with existing services and how to lift them into this seamless paradigm.)
15 views 22 Nov 2023
The advent of TCP/IP and the web produced an explosion of innovation by radically lowering the barrier to entry to connect over the network. Thanks to new technical and social innovations, we now have the building blocks for the next generation of open services: location-free verifiable data and computation.
Verifiable computation opens the door to content-addressed function invocations, results, and workflows. This radically lowers the complexity of historical architectures (e.g. the LAMP stack), networked, and distributed systems. Not only is this easier to reason about, it also (paradoxically) enables superlinear scaling: the more it gets used, the more efficient it becomes!
This talk presents UCAN Invocations and the Interplanetary VM (IPVM). Code in this model can run anywhere (even offline), respects data privacy, and services interoperate seamlessly out of the box without pre-negotiation. Since computation doesn't happen in a vacuum, we will also describe how the workflow planner interacts with existing services and how to lift them into this seamless paradigm.

















.jpg)









 for
- concept : FAIR snarf
for
- concept : FAIR snarf





