the blue plane is also a gully
https://hyp.is/400alBEAEe-CiTPy83Uu9A/www.youtube.com/watch?v=NdSD07U5uBs
the blue plane is also a gully
https://hyp.is/400alBEAEe-CiTPy83Uu9A/www.youtube.com/watch?v=NdSD07U5uBs
sanity is relative to the things we believe are true
sanitty < is
mimetic signatures
Memetic signature
Salience landscape
Symmathetic signature
those that are on the Forefront of evolutionary change are largely operating in silos with little in the way of shared infrastructure
unconscious economy
They are heavily interconnected
delivered is via profoundly and progressively disempowering architecture
Apps
returning to that uh sanity
Indigenious worldviee
our systems for Collective sense making meaning making and choice making are themselves breaking down
breaking down
Wow Person Centric Architecture and the MAP Memetic Activation Platform MAP
https://via.hypothes.is/https://www.youtube.com/watch?v=sfB7zCwOpo8
via.hypothes.is now loads youtube videos with transcripts with the docdrop.org annotator preloaded
looks like hypothes.is is automatically brings up transcript for annotations!
No need to have the browser extension installed can signup to hypothesis and make reading active and social and annotate!
fostering co-creation of a world that works for all
Memetic Activation Platform MAP
https://via.hypothes.is/https://www.youtube.com/watch?v=sfB7zCwOpo8
via.hypothes.is now loads youtube videos with transcripts with the docdrop.org annotator preloaded
Represents elements with an attribute name of attr whose value is exactly value.
document.querySelectorAll('meta[property="og:image"]')[0]
document.querySelectorAll('meta[property="og:image"]')[0].content
'https://i.ytimg.com/vi/sfB7zCwOpo8/hqdefault.jpg'

Privacy
yes
make it as hard as possible to switch to a different provider.
hard to switch
leaving all control of it to them.
leave control to them
companies like Tumblr can purge content from their servers and leave people without a platform.
Tumbl purge content no platform
they get to be the ones that decide how and what you can share
they decide what u can share
Publishing content on the web is already easy
publishing is easy
The link you get back is used to find devices in the P2P network that have a copy of your data so that you can start downloading from them.
link find the 1 who has a copy
all I need to publish content is to run a command
publish by running a command
With P2P tech, you're able to scale your content up just by way of the protoco
P2P tech
scale up by protocol
pay for additional third parties in front of their content.
pay additional third parties
need to be just as easy, if not easier, to set up as an existing CDN
easier cheaper than CDN
sharing the load amongst everyone that's accessed it.
sharing load amongst those accessing it
Content Distribution Costs
n order to convince people to adopt something, you need it to be 10 times better than what they have already
convince 10x better
looking for existing places to shove it into rather than solving an actual problem
A Killer App For P2P
Better be called a maker App
high level API for "lists of posts"
API for list of posts
should be some sort of service for backing people's feeds up when they're offline
backing up service?
"create an account" on their local device, set up tags for their profile, and find other people by their tags.
create an account on their own devices
Makes it easy to share data between users Emphasizes users owning their own data Works offline and shares data on the local network Makes it easy to form ad-hoc communities
No to SQL? Anti-database movement gains steam – My Take
TypePadhttps://natishalom.typepad.com › 2009/07 › no-to-sql-an...TypePadhttps://natishalom.typepad.com › 2009/07 › no-to-sql-an...Jul 9, 2009 — Eric Lai published a provoking article on Computerworld magazine titled “No to SQL? Anti-database movement gains steam” where he pointed to
Showing results for egregore(function(){var q='egregore';var fprsl=document.getElementById('fprsl');fprsl.onclick = function(e){var orig = document.getElementsByName('q')[0].value;if(google.ac&&google.ac.ou){google.ac.ou(q);}else{document.getElementsByName('q')[0].value=q;} document.getElementById("fprs").outerHTML='';document.title = document.title.replace(orig,q);google.log('','&ved='+fprsl.dataset['ved'],'',fprsl);e.preventDefault();};})();Search instead for aggregore

The moment where my dislexia strikes gold
aggregor is a web browse
Web browser integrate P2P protocols
Interview with Mauve, the Creator of Agregore
Agregore IPFS Development Environment V3
using this
BitTorrent Web - Sketchup
BitTorrent + Markdown + Native UI + Content Authoring = Local-First Web
Mauve's Blog
x
My data is in a useful format:
useful formats
Credible exit

Sphere servers are superpeers, personal IPFS gateways that live in the cloud and do a handful of useful things. Your sphere server…
Sphere servers are super peers
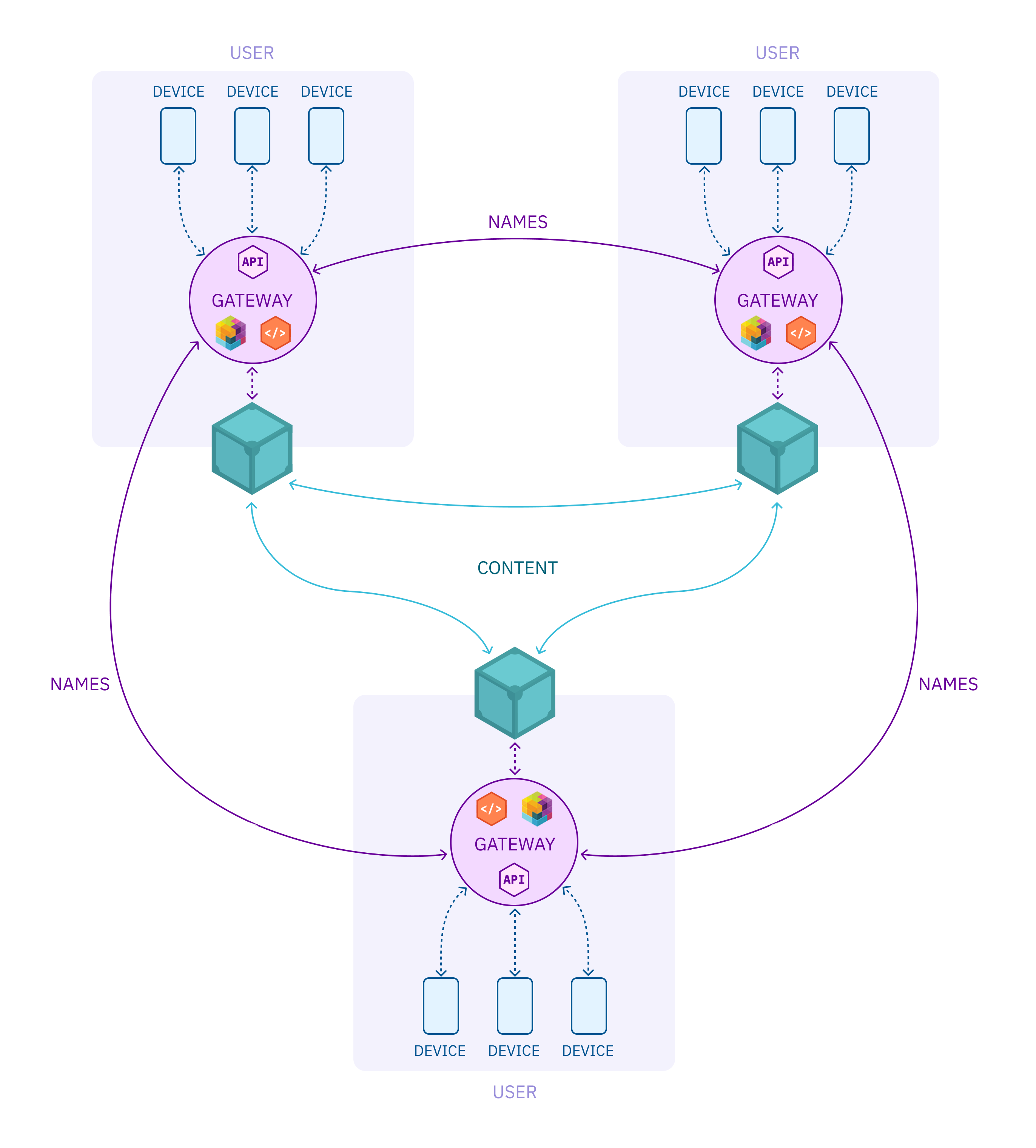 personal IPFS gateways that live in the cloud
personal IPFS gateways that live in the cloud
Sphere Server: your personal IPFS gateway
from < Agora - tutorial - part 2 - impb
P2PU course platform aka Lernanta
Interplanetary Micro Blog IPFS, Web Components, HTML5
A proof of concept application to create and maintain a peer 2 peer blog using the IPFS protocol handlers in the Agregore Web browser.
Interplanetary Micro Blog
Wow
IPFS, Web Components, HTML5
A proof of concept application to create and maintain a peer 2 peer blog using the IPFS protocol handlers in the Agregore Web browser.
Projects
Vizualizing complexity in Gentoo
P2PU badge platform
An open badge issuing platform built to encourage project based learning and peer feedback. None of the gamification hoohaa. I worked with the always insightful Vanessa Gennarelli to build this project from concept to pre-MVP and handed it over to the trustworthy hands of Erika Pogorelc to launch and shephard.
Unbreakout
Unbreakout
What if doing breakouts in Zoom calls could be collaborative and fun? That is what this proof of concept project explores. Users get to create breakouts and can choose what session to join while engaging in a light weight and interactive interface.
Zoom breakout
Learning Circles
Learning Circles
The b(ack)log
from << Agregore - tutorial - part 3
Octasphere
A nice picture of (dependency) hell
dependency hell
And now let's get the index.html and lib.js from the web and add them to our site using the function we just defined.
getting lib.hjs and index.html from the web https://www.thebacklog.net/projects/agregore-web-apps/amt3.js'
https://www.thebacklog.net/projects/agregore-web-apps/amt3-index.tmpl
to https://hyp.is/E4-QqA73Ee-RRKP8GhMMag/www.thebacklog.net/
If you want to create something, you serve it directly from your computer, and when somebody downloads their content they will also re-share it.
creator serve it from their computer
when somebody download they will re-share
for - Indy Learning Commons
The distributed web works by removing central web servers and instead using Peer to Peer connections directly between people to load data
distributed web p2p connections

Agregore Explore the distributed web
The Internet is hard to archive.
indeed
from - Agregore
blocking = theft is the criminalization of the inalienable right to privacy.
blocking = theft

Basic Mode

The advanced popup user interface includes a point-and-click firewall that is configurable on a per-site basis.

wide-spectrum content blocker

from - Agregore
is not an "ad blocker", it is a wide-spectrum blocker, which happens to be able to function as a mere "ad blocker". But it can also be used in a manner similar to NoScript (to block scripts) and/or RequestPolicy (to block all 3rd-party servers by default), using a point-and-click user interface.
not an adblocker
wide spectrum blocker

Cloud storage Jump to bottom gwarser edited this page Mar 27, 2024 · 60 revisions
from - Agregore
Pin Manager
📌 Agregore pin manager
Let's create a function to fetch the contents of a directory. Normally when we fetch an IPFS directory in the Agregore Browser, it checks to see if there is an index file present and if so, it returns that file. To disable that, we add the querystring ?noResolve to the end of the directory URL
create list dir
We can get a list of list of all the files in a directory in IPFS by adding '?noResolve' to the path.
noResolve
you should now see a directory listing
x
Agregore Browser IPFS Development Environment
Load the script and create index.html:
``
let script = document.createElement('script')
script.src = 'lib.js'
document.head.appendChild(script)
setTimeout( () => updateSite('index.html',<html>
<head><title>Page title</title></head>
<br />
<body>
</html>`), 1000) ```
Define and save the updateSite function
javascript
async function updateSite(filename, content){
let cid = window.location.hostname
const resp = await fetch(`ipfs://${cid}/${filename}`, {method: 'put', body: content})
const newLocation = resp.headers.get('location')
window.location = new URL(newLocation).origin
}
updateSite('lib.js', updateSite.toString())
Start with a blank site:
window.location = 'ipfs://bafybeiczsscdsbs7ffqz55asqdf3smv6klcw3gofszvwlyarci47bgf354'
have a minimum viable site that we can update!!
``
updateSite('index.html',<html>
<head><title>Page title</title></head>
<br />
<body>
O, hey darkness, you're still there?
<script src="lib.js"></script> </body></html>`) ```
do a PUT request to the current IPFS content ID
create a basic HTML file
``
let newPageContent =<html>
<head><title>Page title</title></head>
<br />
<body>
</html>let cid = window.location.hostname
const resp = await fetch(ipfs://${cid}/index.html`, {method: 'put', body: newPageContent})
const newLocation = resp.headers.get('location')
window.location = newLocation
```
open the developer tools.

This is a special IPFS address for an empty directory.
open empty directory
sepcial IPFS address
enter the following address: ipfs://bafyaabakaieac/
create a basic development environment for a site hosted on IPFS
development hosted IPFS
Agregore Browser IPFS Development Environment

Sociocratic Neighbourhood Circles in Europe
x
you don't 00:03:40 have control over it since other people will upload your name and phone number without your knowledge
You do not have control over identifying information
Your Pseudonym should work under your control and anything related to that

I used web app creator to make a clickable link for it on Ubuntu touch
web app creatorgive it a clickable link on unubntu touch
get it visible on far sites
visible on "far sites"
only the front end is open source on telegram
frontend only
database because of this encryption the database is not searchable by content
database is not searcheable by content
if data is stored on the users' device
searches has to be run their under owner control
with forward secrecy
"forward secrecy"
=
pseudo anonymity you assign yourself an identity and there's no way to verify your actual identity
=
quantum computers and how they can be used to break asymmetric 00:05:43 encryption which is the basis of private public keys
quantum break assymetric PPK
nice to see you in telegram
telegram
symmetric encryption
it
metadata is captured across platforms
matadata captured
match associations not only inside whatsapp but throughout all of Facebook properties
facebook properties
simply knowing who you're talking to in 00:03:52 a time pattern of communication is sufficient metadata to guess connection and even what you're talking about this alone is a breach of privacy
time pattern of communication
sufficient for identification
that is the source of p2p trust
a contact list reveals so much information about you and your circle
contact list information circle
Brax me is truly focused on pseudo anonymity in social media
Pseudonumity for SaaS
an immediate relationship map
reveals so much about you and your circle
the promotion of contact lists which was used initially to make apps viral
contact lists viral
those two items alone break my privacy in a big way
doesn't allow uploading of contact lists
no upload of contact list =
huge differences one is starting with sign up
Brac me is - focused on psudo anonymity - in social media
doesn't require a phone number as your login
no phone number for login
or email or anything else
going open-source stops me from generating an income from licensing
stop generating income
safe social media and messaging
he people on it are focused on privacy
people around it
focused on privacy
a community service 00:01:21 and not as a money
community service
not money maker
the app has just been promoted by word-of-mouth and my social media
focus on privacy and not just encryption
privacy not just encryption
intended to be just a simple thing for doing encrypted 00:00:54 messaging
encrypted messaging
privacy focus social media app

international team of artists creators and engineers
who are we
mononomous Mauve cross platform lowers the barier of entry
Servers Bad - build uo networks 0 barrier of entry 0 requires expertise - have your own machine - what kind of webserver to host - everything hinges around server - have to go to the server - no internet connection - all that data is lost - holdeing bad from - personal hosting - not trully minde - google product will die 0 change 0 goes out of business - anything I did is gone - too hard to setup
web without the server
IPFS Community Meetup - November 17 2020

Use the same `fetch()` API browsers provide for HTTP, but for IPFS
intro video
intro video

🌠🌓 InterPlanetary File System 🌗🌠) is a
🌠🌓 InterPlanetary File System 🌗🌠) is a - distributed system
for storing and accessing - files, - sites, - apps and - data!
In short, it simplifies the web development process. As long as you have a basic knowledge of web dev (JS, HTML etc.) you can make apps that are shareable right away!
create apps that are shareable right away
The Technical Evolution of Vannevar Bush’s Memex
https://www.google.co.uk/search?q=trailblaze+memex+bush#ip=1
The process of making trails was called “trailblazing”, and was based on a mechanical provision “whereby any item may be caused at will to select ...
Brax.Me - Privacy Focused Social Media - Fully operational platform
x
Rob Braxman Tech
FAIRPHONE | THE NETHERLANDS

Brax.Me App FAQ #techsupport This FAQ is for the Brax.Me App itself. If you want to know how to do something on Brax.Me, this is the place for that. Open Membership
x
Murena Smartphones

What is a single egregore? How is an egregore formed? What unites people? Is there an egregore among…See more

http://indy.memplex.net.ipns.localhost:48084/annote.htm?p=ipfs://bafybeidvswhu57sqbhwn7bvmmbxre6nav2la3smxk5rddtvoubkyqf563a/
http://indy.memplex.net.ipns.localhost:48084/annote.htm?p=ipfs://bafybeidvswhu57sqbhwn7bvmmbxre6nav2la3smxk5rddtvoubkyqf563a/
http://indy-memplex-net.ipns.localhost:48084/annote.htm?p=ipfs://bafybeiackl4z6rco5foatut3azt43q2mqgvx6kyo434qs2alu5yniiwia4/#annotations:t0RLaAxTEe-HUGv0nuJGZw
Install Brave Browser and enable brave://ipfs
or
get agregore browser
using brave desktop
A great place to start if you want to create apps using Agregore ✨
create apps with agregore
network-as-a-service organization.

Mauve's Blog source code
blog
Mauve Signweaver
Mobile version of the Agregore browser for Android, based on Chromium and Bromite
Termux Terminal emulator with packages
![]()
An example chat app using Hypercore Protocol extension messages in Agregore

An minimal blogging platform using IPFS Protocol Handlers and Markdown
minimal blogging platform with IPFS
Containerized Examples
A good FreeNX alternative is X2Go.

FreeNX

X2Go - everywhere@home

Give FreeNX a try.

About URL rewriting
EZproxy
live in the present moment and find the compassion that exists all around and within us.

The Five Reiki Gokai or Principles

NNTP
nntp
but most news administrators will ignore these requests unless a local user requests the group by name.
create groups by a team
news.announce.newgroups,
news announc newsgroups
RFD (Request For Discussion)
Request for discussion
There was a rapid growth of alt.* as a result, and the trend continues to this day. Because of the anarchistic nature with which the groups sprang up, some jokingly referred to ALT standing for "Anarchists, Lunatics and Terrorists" (a backronym).
backronym anarchistic lunatics and terrorists
This situation resulted in the creation of an alt.* (short for "alternative") Usenet hierarchy,
alt.usenet hierarchy
n the Great Renaming of 1986–1987,
great renaming
comp.* — Discussion of computer-related topics news.* — Discussion of Usenet itself sci.* — Discussion of scientific subjects rec.* — Discussion of recreational activities (e.g. games and hobbies) soc.* — Socialising and discussion of social issues. talk.* — Discussion of contentious issues such as religion and politics. misc.* — Miscellaneous discussion—anything which does not fit in the other hierarchies.
main topic hierarcies
the early community was the pioneering computer society
pioneering computer society
The news admin (the administrator of a news server)
news admin
regarding anything a member chooses to discuss as on-topic
on-topic
called a "post".
hence hyperpost
usenet
maintain a level of robust data persistence
rubust persistence
Network News Transfer Protocol (NNTP)
ipnntp
Typically, the newsgroup is focused on a particular topic of interest.
topic of interest
BROADCASTING INTERNET DATAGRAMS
RFC plain text
BROADCASTING INTERNET DATAGRAMS
Broadcasting Internet Datagrams
x
Internet Official Protocol Standards
internet official protocl standards
http://www.rfc-editor.org/
x
typewrote

Request for Comments
x
Collected Grammar
grammar
Multipurpose Internet Mail Extensions (MIME) Part Two: Media Types
RFC
absence of online connectivity
re-imagining online connectivity
autonomous interpersonal usenet newesgroups
discussion groups, known as newsgroups,
reimagining newsgroups
About Android app to run Javascript files from the filesystem in Node.js
node.js android
Connecting Android Apps to localhost, Simplified
How to create Web Server in Browser

repeatable process of _producing a lot of software_ by big teams with variation in experience and headcount
where the programmers are fungible - not the software -
they produce
If te software could be fungible capable of organic
re - usable - mixable - sumable
digital executable artifats
auto-poietic co-evolving body of organic growth
we would not need big teams
and the realm of software itself will become - an Open Sea of - effective articulation of capabilities
that are tinkerable capable of self-organization and autopoietic synthetic symmathetic growth living everrgreen and permanent
a systems that are lifelike co-evol
at scale in the long tail of the internet
Compared to Go, Rust looks like Common Lisp looked like to a Java programmer of old
The highest possible praise
Let's overcome the "Curse of LISP"
Why is Google in love with purposely-impaired languages like Go, Dart?
purposely-impared languages
cause they do not really want to empower people
but machines and only the people behind the machines
We the people should fight the buttleriabn jihad now before the machines get all the firepower
"mediocre by design"
yep
"Google has the intellectual firepower to be going where no programmer has gone before, yet languages like Go remain solidly in well-understood and, for the most part, commonly-implemented territory. I have no doubt that this is a good strategic move on Google's part, and that Go solves a number of important problems that Google faces, but I was disappointed that Google hadn't taken a more experimental and research-focused approach.
Google intellectual firepower
boldy go where no programmer has gone before
and transcend programming itself
"CERN has the intellectual firepower to be going where no physicist has gone before, yet their experiments remain solidly in the realm of existing scientific methods and, for the most part, mathematical models. Smashing atoms together may be interesting, but it makes me want collide my brain with a wall"
intellectual firepower CERN
About Flowistry is an IDE plugin for Rust that helps you focus on relevant code.

www.willcrichton.net