xTiles, a visual tool to organize information with card-based pages.
xTiles, a visual tool to organize information with card-based pages.

Tana
Memex
Featured Tools
.list - tools for thought
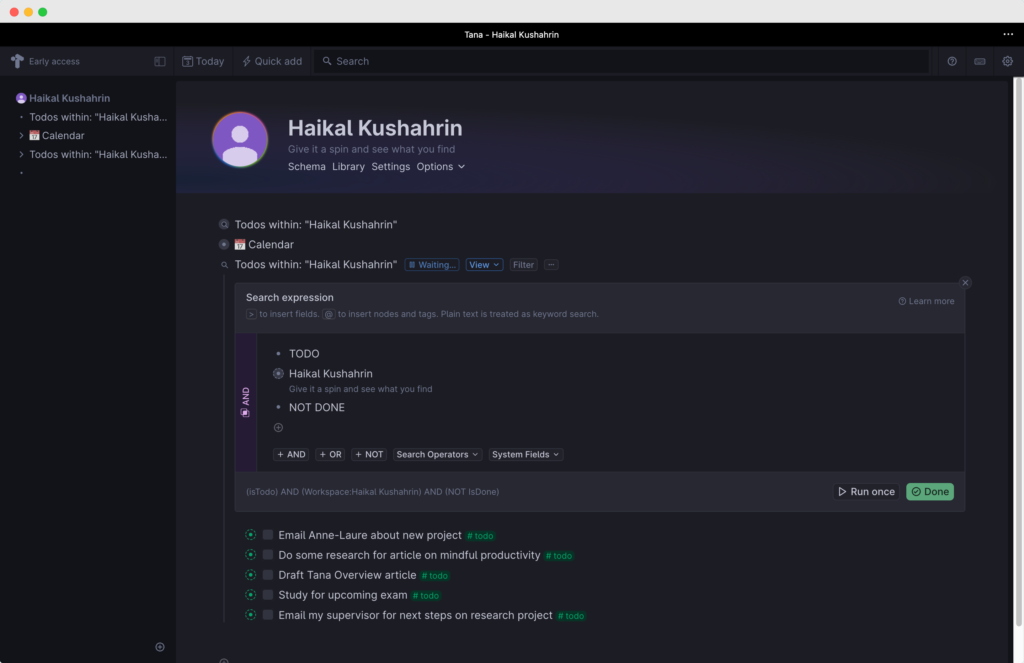
Tana: the all-in-one tool for thought?
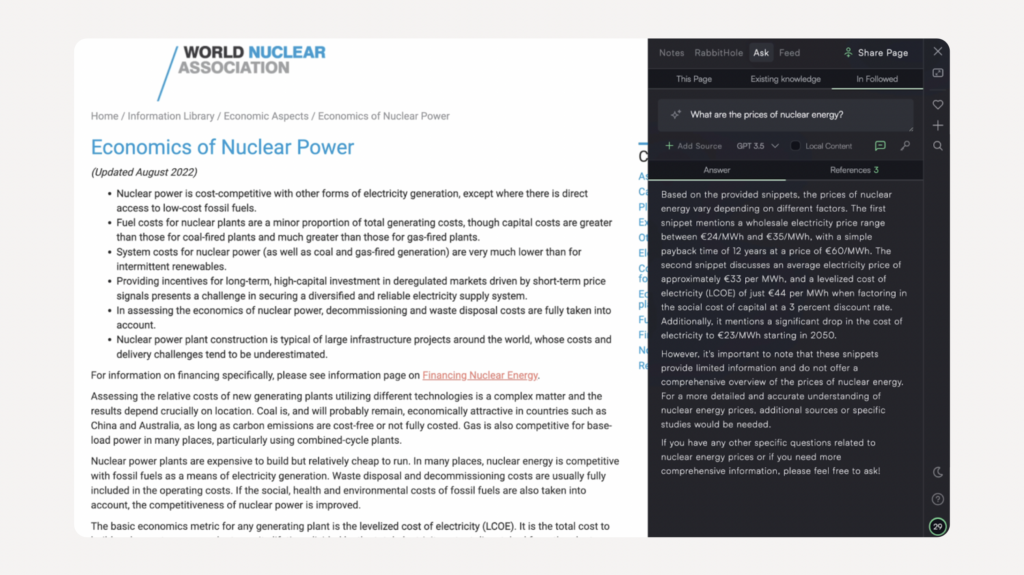
Your favorite minds as reading copilots with Oliver Sauter, founder of Memex
.hyp.search: "improve ability"
Improving Our Ability to Improve: A Call for Investment in a New Future 0 Douglas C. Engelbart The Bootstrap Alliance April 23, 2002 (AUGMENT,133320,)
https://hyp.is/58PuthepEeyc6LfKgRPCmg/computerhistory.org/profile/doug-endelbart/


In 1911, a genius revealed a forgotten science of how to be 50x more productive without working more hours
.4 = Knowledge Work
The most valuable asset of a 21st-century institution (whether business or non-business) will be its knowledge workers and their productivity
Thereás the catch
You cannot treat Knowledge as assets
Assets that know their worth cannot just be bought and sold
It reminds me how the "enlightened" CEO of the company I worked for as a freelancer was dreaming of
"entreprenourial employees"
SEMANTIC ENGINESé AN INTRODUCTION TO Mind Design
HUBSCIENCE RESEARCH INTELLIGENCE
<svg preserveAspectRatio="xMidYMid meet" data-bbox="12.067 8.74 318.803 60.86" viewBox="12.067 8.74 318.803 60.86" xmlns="http://www.w3.org/2000/svg" data-type="color" role="img" aria-label="HubScience , Research Intelligence"> <g> <path d="M326.27 53.01c-.72 0-1.3.23-1.75.69-.45.46-.67 1.02-.67 1.67v.18c0 .07.03.14.08.21.05.07.15.1.31.1h4.22c.17 0 .26-.09.26-.28v-.23c0-.65-.21-1.2-.62-1.65-.41-.46-1.02-.69-1.83-.69Zm4.53 3.89c0 .19-.06.34-.18.46-.1.1-.21.15-.33.15h-6.02c-.14 0-.25.04-.33.13-.09.09-.13.2-.13.33v.49c0 .34.04.68.13 1 .09.31.22.58.41.82.21.22.46.4.77.54.33.14.71.21 1.16.21.51 0 .98-.12 1.39-.36.43-.24.79-.56 1.08-.95.14-.19.31-.21.51-.08l.9.62c.21.14.27.27.21.41-.41.75-.98 1.3-1.7 1.65-.72.34-1.5.51-2.34.51-1.39 0-2.5-.38-3.35-1.13-.82-.77-1.24-1.8-1.24-3.09v-2.93c0-.65.11-1.25.33-1.8.22-.55.53-1.02.93-1.42.41-.39.89-.69 1.44-.9.55-.22 1.16-.33 1.83-.33s1.3.11 1.85.33c.57.21 1.05.51 1.44.9.39.39.69.87.9 1.42.22.55.33 1.15.33 1.8v1.21Z" fill="#1a7dd8" data-color="1"></path> <path d="M319.09 53.22c.07.09.09.19.08.31-.02.1-.08.19-.18.26l-.9.69c-.22.15-.42.1-.59-.15-.29-.43-.65-.75-1.08-.95-.41-.22-.86-.33-1.34-.33-.74 0-1.33.23-1.78.69-.43.45-.64 1.03-.64 1.75v3.19c0 .7.22 1.28.67 1.72.46.43 1.07.64 1.83.64.67 0 1.2-.15 1.6-.44.39-.29.75-.63 1.06-1.03.09-.1.21-.09.39.03l.85.62c.17.1.27.21.28.31.02.09 0 .17-.08.26-.51.77-1.13 1.31-1.85 1.62-.7.29-1.44.44-2.21.44-1.39 0-2.5-.38-3.35-1.13-.82-.75-1.24-1.79-1.24-3.11v-2.96c0-.69.11-1.3.33-1.85.24-.55.56-1 .95-1.36.41-.38.89-.66 1.44-.85.55-.21 1.15-.31 1.8-.31 1.66.02 2.99.67 3.96 1.96Z" fill="#1a7dd8" data-color="1"></path> <path d="M307.32 62.43c0 .17-.08.26-.23.26h-1.6c-.15 0-.23-.08-.23-.23v-6.87c0-.74-.21-1.35-.62-1.83-.41-.48-1.03-.72-1.85-.72-.75 0-1.36.24-1.8.72-.45.46-.67 1.06-.67 1.8v6.87c0 .17-.09.26-.26.26h-1.57c-.17 0-.26-.08-.26-.23V51.68c0-.17.08-.26.23-.26h1.49c.15 0 .23.08.23.23v.39c0 .15.06.23.18.23.03 0 .1-.03.21-.1.72-.6 1.58-.9 2.57-.9 1.29 0 2.3.39 3.04 1.18.75.77 1.13 1.81 1.13 3.11v6.87Z" fill="#1a7dd8" data-color="1"></path> <path d="M290.54 53.01c-.72 0-1.3.23-1.75.69-.45.46-.67 1.02-.67 1.67v.18c0 .07.03.14.08.21.05.07.15.1.31.1h4.22c.17 0 .26-.09.26-.28v-.23c0-.65-.21-1.2-.62-1.65-.41-.46-1.02-.69-1.83-.69Zm4.53 3.89c0 .19-.06.34-.18.46-.1.1-.21.15-.33.15h-6.02c-.14 0-.25.04-.33.13-.09.09-.13.2-.13.33v.49c0 .34.04.68.13 1 .09.31.22.58.41.82.21.22.46.4.77.54.33.14.71.21 1.16.21.51 0 .98-.12 1.39-.36.43-.24.79-.56 1.08-.95.14-.19.31-.21.51-.08l.9.62c.21.14.27.27.21.41-.41.75-.98 1.3-1.7 1.65-.72.34-1.5.51-2.34.51-1.39 0-2.5-.38-3.35-1.13-.82-.77-1.24-1.8-1.24-3.09v-2.93c0-.65.11-1.25.33-1.8.22-.55.53-1.02.93-1.42.41-.39.89-.69 1.44-.9.55-.22 1.16-.33 1.83-.33s1.3.11 1.85.33c.57.21 1.05.51 1.44.9.39.39.69.87.9 1.42.22.55.33 1.15.33 1.8v1.21Z" fill="#1a7dd8" data-color="1"></path> <path d="M278.08 53.01c-.77 0-1.39.24-1.85.72-.45.46-.67 1.01-.67 1.65s.21 1.17.62 1.65c.41.46 1 .69 1.75.69.81 0 1.42-.22 1.85-.67.45-.46.67-1.02.67-1.67s-.22-1.18-.67-1.65c-.43-.48-1-.72-1.7-.72Zm-.15-1.78c.57 0 1.11.09 1.62.26s.97.41 1.36.72c.07.03.11.05.13.05s.06-.02.13-.05c.33-.27.69-.49 1.08-.64.41-.17.82-.26 1.24-.26.24-.02.36.11.36.39v1.31c0 .14-.03.22-.08.26-.03.03-.14.04-.31.03-.09-.02-.16-.03-.23-.03h-.21c-.26 0-.51.04-.77.13-.1.03-.15.08-.15.13 0 .03 0 .06.03.08.29.5.44 1.06.44 1.67s-.13 1.15-.39 1.65c-.24.5-.57.93-1 1.29-.41.36-.9.64-1.47.85a5.4 5.4 0 0 1-1.78.28h-.49c-.19 0-.33.04-.41.13-.05.07-.1.15-.15.23-.03.07-.05.15-.05.26 0 .24.1.41.31.51.22.1.48.15.77.15h1.7c.48 0 .93.07 1.36.21.43.14.81.34 1.13.62.33.26.58.58.77.98.19.39.28.85.28 1.36 0 .62-.14 1.16-.41 1.62-.26.46-.61.85-1.06 1.16-.43.31-.94.53-1.54.67-.58.15-1.19.23-1.83.23-.67 0-1.3-.07-1.9-.21-.58-.14-1.11-.33-1.57-.59-.45-.26-.81-.58-1.08-.98a2.25 2.25 0 0 1-.39-1.31c0-.43.11-.87.33-1.34.03-.07.08-.12.13-.15s.13-.03.23 0l1.47.44c.09.02.13.06.13.13 0 .03-.02.09-.05.15-.03.05-.07.14-.1.26s-.05.22-.05.31c0 .43.23.8.69 1.11.48.31 1.2.46 2.16.46.89 0 1.58-.15 2.06-.46.48-.31.72-.74.72-1.29 0-.45-.15-.83-.46-1.16-.31-.31-.87-.46-1.7-.46h-1.54c-.91 0-1.6-.18-2.06-.54-.46-.38-.69-.82-.69-1.34 0-.27.09-.56.26-.85.17-.29.35-.54.54-.75.05-.05.08-.1.08-.15 0-.03-.03-.07-.08-.1-.57-.34-1.03-.8-1.39-1.36-.36-.57-.54-1.24-.54-2.01 0-.57.12-1.09.36-1.57.26-.5.59-.93 1-1.29.41-.38.88-.67 1.42-.87.53-.21 1.08-.31 1.65-.31Z" fill="#1a7dd8" data-color="1"></path> <path d="M268.39 51.68c0-.17.08-.26.23-.26h1.6c.17 0 .26.09.26.26v10.78c0 .15-.08.23-.23.23h-1.6c-.17 0-.26-.08-.26-.23V51.68Zm2.39-3.81c0 .34-.13.64-.39.9s-.57.39-.93.39-.67-.12-.93-.36c-.24-.24-.36-.55-.36-.93 0-.34.12-.63.36-.87.26-.26.56-.39.9-.39.38 0 .69.12.95.36s.39.54.39.9Z" fill="#1a7dd8" data-color="1"></path> <path d="M266.1 62.36c.05.17 0 .28-.13.33-.1.03-.26.07-.46.1-.19.03-.38.05-.57.05h-.33c-.77 0-1.42-.09-1.93-.26-.5-.17-.9-.43-1.21-.77-.31-.36-.53-.8-.67-1.31-.12-.51-.18-1.12-.18-1.83V46.55c0-.17.09-.26.26-.26h1.57c.15 0 .23.09.23.26v11.84c0 .94.15 1.6.46 1.96.31.36.84.54 1.6.54h.28c.1 0 .21 0 .31-.03.19-.02.32-.02.39 0 .09.02.15.11.18.28l.21 1.21Z" fill="#1a7dd8" data-color="1"></path> <path d="M258.1 62.36c.05.17 0 .28-.13.33-.1.03-.26.07-.46.1-.19.03-.38.05-.57.05h-.33c-.77 0-1.42-.09-1.93-.26-.5-.17-.9-.43-1.21-.77-.31-.36-.53-.8-.67-1.31-.12-.51-.18-1.12-.18-1.83V46.55c0-.17.09-.26.26-.26h1.57c.15 0 .23.09.23.26v11.84c0 .94.15 1.6.46 1.96.31.36.84.54 1.6.54h.28c.1 0 .21 0 .31-.03.19-.02.32-.02.39 0 .09.02.15.11.18.28l.21 1.21Z" fill="#1a7dd8" data-color="1"></path> <path d="M244.54 53.01c-.72 0-1.3.23-1.75.69-.45.46-.67 1.02-.67 1.67v.18c0 .07.03.14.08.21s.15.1.31.1h4.22c.17 0 .26-.09.26-.28v-.23c0-.65-.21-1.2-.62-1.65-.41-.46-1.02-.69-1.83-.69Zm4.53 3.89c0 .19-.06.34-.18.46-.1.1-.21.15-.33.15h-6.02c-.14 0-.25.04-.33.13-.09.09-.13.2-.13.33v.49c0 .34.04.68.13 1 .09.31.22.58.41.82.21.22.46.4.77.54.33.14.71.21 1.16.21.51 0 .98-.12 1.39-.36.43-.24.79-.56 1.08-.95.14-.19.31-.21.51-.08l.9.62c.21.14.27.27.21.41-.41.75-.98 1.3-1.7 1.65-.72.34-1.5.51-2.34.51-1.39 0-2.5-.38-3.35-1.13-.82-.77-1.24-1.8-1.24-3.09v-2.93c0-.65.11-1.25.33-1.8s.53-1.02.93-1.42c.41-.39.89-.69 1.44-.9.55-.22 1.16-.33 1.83-.33s1.3.11 1.85.33c.57.21 1.05.51 1.44.9.39.39.69.87.9 1.42.22.55.33 1.15.33 1.8v1.21Z" fill="#1a7dd8" data-color="1"></path> <path d="M233.68 58.37c0 .94.19 1.6.57 1.96.38.36.94.54 1.7.54h.28c.1 0 .21 0 .31-.03.19-.02.32-.02.39 0 .09.02.15.11.18.28l.21 1.24c.05.17 0 .28-.13.33-.1.03-.26.07-.46.1-.19.03-.38.05-.57.05h-.33c-1.53 0-2.62-.34-3.27-1.03-.63-.7-.95-1.75-.95-3.14V48.43c0-.05.02-.1.05-.15.03-.05.09-.08.18-.08h1.6c.17 0 .26.09.26.26v2.7c0 .17.09.26.26.26h2.75c.15 0 .23.09.23.26v1.29c0 .17-.08.26-.23.26h-2.75c-.17 0-.26.09-.26.26v4.89Z" fill="#1a7dd8" data-color="1"></path> <path d="M227.93 62.43c0 .17-.08.26-.23.26h-1.6c-.15 0-.23-.08-.23-.23v-6.87c0-.74-.21-1.35-.62-1.83-.41-.48-1.03-.72-1.85-.72-.75 0-1.36.24-1.8.72-.45.46-.67 1.06-.67 1.8v6.87c0 .17-.09.26-.26.26h-1.57c-.17 0-.26-.08-.26-.23V51.68c0-.17.08-.26.23-.26h1.49c.15 0 .23.08.23.23v.39c0 .15.06.23.18.23.03 0 .1-.03.21-.1.72-.6 1.58-.9 2.57-.9 1.29 0 2.3.39 3.04 1.18.75.77 1.13 1.81 1.13 3.11v6.87Z" fill="#1a7dd8" data-color="1"></path> <path d="M214.65 62.38c0 .21-.1.31-.31.31h-1.6c-.21 0-.31-.09-.31-.28V47.1c0-.19.1-.28.31-.28h1.6c.21 0 .31.09.31.26v15.31Z" fill="#1a7dd8" data-color="1"></path> <path d="M202.17 62.43c0 .17-.08.26-.23.26h-1.6c-.15 0-.23-.08-.23-.23v-6.87c0-.74-.2-1.34-.59-1.8-.38-.48-1-.72-1.88-.72-.75 0-1.36.24-1.8.72-.45.46-.67 1.06-.67 1.78v6.87c0 .17-.09.26-.26.26h-1.57c-.17 0-.26-.08-.26-.23v-15.9c0-.17.08-.26.23-.26h1.6c.15 0 .23.09.23.26V52c0 .14.04.22.13.26.09.02.17-.02.26-.1.38-.27.79-.48 1.24-.62.46-.15.93-.23 1.42-.23 1.29 0 2.27.39 2.96 1.18.69.77 1.03 1.8 1.03 3.09v6.87Z" fill="#1a7dd8" data-color="1"></path> <path d="M190.18 53.22c.07.09.09.19.08.31-.02.1-.08.19-.18.26l-.9.69c-.22.15-.42.1-.59-.15-.29-.43-.65-.75-1.08-.95-.41-.22-.86-.33-1.34-.33-.74 0-1.33.23-1.78.69-.43.45-.64 1.03-.64 1.75v3.19c0 .7.22 1.28.67 1.72.46.43 1.07.64 1.83.64.67 0 1.2-.15 1.6-.44.39-.29.75-.63 1.06-1.03.09-.1.21-.09.39.03l.85.62c.17.1.27.21.28.31.02.09 0 .17-.08.26-.51.77-1.13 1.31-1.85 1.62-.7.29-1.44.44-2.21.44-1.39 0-2.5-.38-3.35-1.13-.82-.75-1.24-1.79-1.24-3.11v-2.96c0-.69.11-1.3.33-1.85.24-.55.56-1 .95-1.36.41-.38.89-.66 1.44-.85.55-.21 1.15-.31 1.8-.31 1.66.02 2.99.67 3.96 1.96Z" fill="#1a7dd8" data-color="1"></path> <path d="M175.3 51.42c.17 0 .26.08.26.23v1.21c0 .09.03.15.08.18.07.02.14-.02.21-.1.29-.41.69-.79 1.21-1.13.51-.36 1.12-.54 1.8-.54.1 0 .23 0 .39.03.15 0 .26.02.31.05.14.03.21.09.23.15.03.05.03.13 0 .23l-.31 1.52c-.03.14-.09.22-.15.26-.05.02-.11.02-.18 0a3.99 3.99 0 0 0-.75-.08c-.96 0-1.63.28-2.01.85-.38.55-.57 1.24-.57 2.06v6.1c0 .17-.08.26-.23.26h-1.6c-.17 0-.26-.08-.26-.23V51.69c0-.17.08-.26.23-.26h1.34Z" fill="#1a7dd8" data-color="1"></path> <path d="M168.07 55.49c0-.69-.23-1.26-.69-1.72-.46-.46-1.06-.69-1.78-.69-.82 0-1.45.24-1.88.72-.41.46-.62 1.03-.62 1.7v3.19c0 .67.21 1.25.62 1.75.43.48 1.06.72 1.88.72.7 0 1.29-.24 1.75-.72.46-.48.69-1.06.69-1.75l.03-3.19Zm2.06 6.95c0 .17-.09.26-.26.26h-1.57c-.15 0-.23-.08-.23-.23v-.26c0-.12-.03-.2-.1-.23s-.17 0-.31.1c-.22.19-.55.35-.98.49-.41.14-.84.21-1.29.21-1.34 0-2.4-.35-3.19-1.06-.77-.72-1.16-1.73-1.16-3.04v-3.19c0-.62.11-1.18.33-1.7s.52-.95.9-1.31c.39-.38.86-.67 1.39-.87s1.1-.31 1.7-.31c.65 0 1.17.09 1.54.28.38.17.67.34.87.51.09.09.17.13.26.13.1-.02.15-.08.15-.18v-.36c0-.17.08-.26.23-.26h1.44c.17 0 .26.08.26.23v10.78Z" fill="#1a7dd8" data-color="1"></path> <path d="M153.53 53.01c-.72 0-1.3.23-1.75.69-.45.46-.67 1.02-.67 1.67v.18c0 .07.03.14.08.21s.15.1.31.1h4.22c.17 0 .26-.09.26-.28v-.23c0-.65-.21-1.2-.62-1.65-.41-.46-1.02-.69-1.83-.69Zm4.53 3.89c0 .19-.06.34-.18.46-.1.1-.21.15-.33.15h-6.02c-.14 0-.25.04-.33.13-.09.09-.13.2-.13.33v.49c0 .34.04.68.13 1 .09.31.22.58.41.82.21.22.46.4.77.54.33.14.71.21 1.16.21.51 0 .98-.12 1.39-.36.43-.24.79-.56 1.08-.95.14-.19.31-.21.51-.08l.9.62c.21.14.27.27.21.41-.41.75-.98 1.3-1.7 1.65-.72.34-1.5.51-2.34.51-1.39 0-2.5-.38-3.35-1.13-.82-.77-1.24-1.8-1.24-3.09v-2.93c0-.65.11-1.25.33-1.8.22-.55.53-1.02.93-1.42.41-.39.89-.69 1.44-.9.55-.22 1.16-.33 1.83-.33s1.3.11 1.85.33c.57.21 1.05.51 1.44.9.39.39.69.87.9 1.42.22.55.33 1.15.33 1.8v1.21Z" fill="#1a7dd8" data-color="1"></path> <path d="M146.11 59.63c0 .43-.09.84-.28 1.24-.17.38-.43.71-.77 1-.34.29-.77.52-1.29.69-.5.17-1.07.26-1.72.26-.91 0-1.75-.21-2.52-.62-.77-.41-1.33-1.05-1.67-1.9-.05-.14-.02-.23.1-.28l1.31-.59c.09-.03.15-.03.18 0 .05.03.09.08.13.13.26.5.61.89 1.06 1.18.46.27.99.41 1.57.41.55 0 1-.14 1.36-.41.38-.29.57-.63.57-1.03s-.15-.73-.44-.95c-.29-.22-.69-.43-1.18-.62-.39-.15-.85-.32-1.36-.49-.5-.17-.97-.39-1.42-.64-.45-.27-.82-.61-1.13-1-.29-.41-.44-.93-.44-1.54 0-.51.1-.97.31-1.36.22-.39.51-.72.87-.98.36-.27.77-.48 1.24-.62.46-.14.95-.21 1.47-.21.72-.02 1.41.1 2.06.36.65.24 1.23.63 1.72 1.16.12.12.09.27-.08.44l-.69.8c-.17.19-.37.18-.59-.03-.34-.31-.73-.55-1.16-.72-.43-.19-.86-.28-1.29-.28-.57 0-1.02.12-1.36.36-.33.22-.49.53-.49.93s.14.69.41.93c.29.22.69.43 1.18.62.5.19 1 .38 1.52.57.51.19.98.42 1.39.69.43.26.77.59 1.03 1 .27.39.41.9.41 1.52Z" fill="#1a7dd8" data-color="1"></path> <path d="M130.7 53.01c-.72 0-1.3.23-1.75.69-.45.46-.67 1.02-.67 1.67v.18c0 .07.03.14.08.21.05.07.15.1.31.1h4.22c.17 0 .26-.09.26-.28v-.23c0-.65-.21-1.2-.62-1.65-.41-.46-1.02-.69-1.83-.69Zm4.53 3.89c0 .19-.06.34-.18.46-.1.1-.21.15-.33.15h-6.02c-.14 0-.25.04-.33.13-.09.09-.13.2-.13.33v.49c0 .34.04.68.13 1 .09.31.22.58.41.82.21.22.46.4.77.54.33.14.71.21 1.16.21.51 0 .98-.12 1.39-.36.43-.24.79-.56 1.08-.95.14-.19.31-.21.51-.08l.9.62c.21.14.27.27.21.41-.41.75-.98 1.3-1.7 1.65-.72.34-1.5.51-2.34.51-1.39 0-2.5-.38-3.35-1.13-.82-.77-1.24-1.8-1.24-3.09v-2.93c0-.65.11-1.25.33-1.8s.53-1.02.93-1.42c.41-.39.89-.69 1.44-.9.55-.22 1.16-.33 1.83-.33s1.3.11 1.85.33c.57.21 1.05.51 1.44.9.39.39.69.87.9 1.42.22.55.33 1.15.33 1.8v1.21Z" fill="#1a7dd8" data-color="1"></path> <path d="M115.8 48.67c-.15 0-.23.07-.23.21v5.22c0 .15.07.23.21.23h3.14c.09 0 .16 0 .23-.03s.13-.07.18-.1c.46-.33.83-.75 1.11-1.29s.41-1 .41-1.42c0-.33-.04-.66-.13-1-.07-.34-.21-.64-.44-.9-.21-.27-.5-.5-.87-.67-.36-.17-.83-.26-1.42-.26h-2.19Zm7.23 2.6c0 .45-.07.88-.21 1.31-.14.43-.33.84-.57 1.24-.22.38-.48.73-.77 1.06-.27.31-.55.58-.82.82-.09.05-.11.11-.08.18.02.03.04.1.08.21.05.09.17.33.36.75.19.39.47 1 .85 1.83.39.82.94 1.98 1.65 3.47.1.22.1.38 0 .46-.09.07-.18.1-.28.1h-1.34c-.27 0-.46-.04-.57-.13-.09-.09-.17-.21-.26-.39l-2.62-5.79a.324.324 0 0 0-.13-.15c-.05-.05-.14-.08-.26-.08h-2.26c-.14 0-.21.08-.21.23v6c0 .21-.1.31-.31.31h-1.54c-.21 0-.31-.09-.31-.28V47.11c0-.19.1-.28.31-.28h4.53c1.61 0 2.8.4 3.58 1.21.79.81 1.18 1.89 1.18 3.24Z" fill="#1a7dd8" data-color="1"></path> <path d="M56.93 24.75a5.498 5.498 0 0 0-7.78 0 5.498 5.498 0 0 0 0 7.78L59.52 42.9c3.58 3.58 3.58 9.39 0 12.97-3.57 3.57-9.39 3.58-12.96 0S36.19 45.5 36.19 45.5a5.48 5.48 0 0 0-7.78 0L13.7 60.21a5.498 5.498 0 0 0 3.89 9.39c1.41 0 2.81-.54 3.89-1.61l10.83-10.83 6.48 6.48c3.93 3.93 9.1 5.9 14.26 5.9s10.33-1.97 14.26-5.9c2.34-2.34 3.96-5.11 4.91-8.06l12.4 12.4c1.07 1.07 2.48 1.61 3.89 1.61s2.82-.54 3.89-1.61a5.498 5.498 0 0 0 0-7.78L56.92 24.75Z" fill="#1a7dd8" data-color="1"></path> <path d="M330.09 30.55c.17 0 .35.07.52.21.17.1.26.3.26.57v3.33c0 .52-.26.78-.78.78h-15.42c-.52 0-.78-.24-.78-.73v-22.7c0-.52.26-.78.78-.78h15.32c.17 0 .35.07.52.21.21.1.31.3.31.57v3.33c0 .52-.28.78-.83.78h-9.85c-.31 0-.52.05-.63.16-.07.1-.1.31-.1.63v3.02c0 .31.03.5.1.57.1.07.31.1.63.1h7.87c.56 0 .83.26.83.78v3.39c0 .49-.28.73-.83.73h-7.92c-.28 0-.47.07-.57.21-.07.14-.1.36-.1.68v3.39c0 .31.05.52.16.63.1.1.3.16.57.16h9.95Z" fill="#03275b" data-color="2"></path> <path d="M300.61 35.71c-1.49 0-2.85-.21-4.06-.63-1.18-.42-2.21-.99-3.07-1.72-.83-.73-1.48-1.6-1.93-2.6-.45-1.01-.68-2.1-.68-3.28V19.3c0-1.18.21-2.27.63-3.28a8.296 8.296 0 0 1 1.88-2.71c.8-.76 1.75-1.35 2.87-1.77 1.15-.45 2.43-.68 3.85-.68.69 0 1.41.05 2.14.16.73.07 1.46.24 2.19.52.73.24 1.44.61 2.14 1.09.73.49 1.42 1.13 2.08 1.93.21.28.24.54.1.78-.1.21-.28.4-.52.57l-2.29 2.08c-.45.24-.87.17-1.25-.21-.66-.73-1.35-1.25-2.08-1.56-.69-.31-1.44-.47-2.24-.47-.69 0-1.3.12-1.82.36a3.54 3.54 0 0 0-1.88 2.24c-.14.49-.21.97-.21 1.46V27c0 1.01.36 1.89 1.09 2.66.73.73 1.79 1.09 3.18 1.09.87 0 1.65-.19 2.34-.57.69-.38 1.27-.87 1.72-1.46.21-.28.38-.45.52-.52.17-.07.38-.05.63.05l3.02 2.03c.24.14.36.33.36.57s-.1.5-.31.78c-1.04 1.46-2.26 2.5-3.65 3.13-1.39.63-2.97.94-4.74.94Z" fill="#03275b" data-color="2"></path> <path d="M285.21 34.62c0 .56-.28.83-.83.83h-2.66c-.35 0-.63-.03-.83-.1-.17-.07-.38-.3-.63-.68l-8.18-12.87c-.07-.17-.17-.24-.31-.21-.1.03-.16.14-.16.31v12.81c0 .49-.26.73-.78.73h-3.75c-.56 0-.83-.24-.83-.73v-22.6c0-.24.07-.45.21-.63.17-.17.42-.26.73-.26h2.66c.42 0 .73.1.94.31.21.17.4.42.57.73l8.07 12.66c.14.17.24.24.31.21.1-.03.16-.14.16-.31V12.01c0-.52.26-.78.78-.78h3.75c.52 0 .78.26.78.78v22.61Z" fill="#03275b" data-color="2"></path> <path d="M260.66 30.55c.17 0 .35.07.52.21.17.1.26.3.26.57v3.33c0 .52-.26.78-.78.78h-15.42c-.52 0-.78-.24-.78-.73v-22.7c0-.52.26-.78.78-.78h15.32c.17 0 .35.07.52.21.21.1.31.3.31.57v3.33c0 .52-.28.78-.83.78h-9.85c-.31 0-.52.05-.63.16-.07.1-.1.31-.1.63v3.02c0 .31.03.5.1.57.1.07.31.1.63.1h7.87c.56 0 .83.26.83.78v3.39c0 .49-.28.73-.83.73h-7.92c-.28 0-.47.07-.57.21-.07.14-.1.36-.1.68v3.39c0 .31.05.52.16.63.1.1.3.16.57.16h9.95Z" fill="#03275b" data-color="2"></path> <path d="M233.44 35.45c-.66 0-.99-.35-.99-1.04V12.22c0-.66.33-.99.99-.99h3.75c.24 0 .45.09.63.26.21.14.31.38.31.73v22.19c0 .69-.31 1.04-.94 1.04h-3.75Z" fill="#03275b" data-color="2"></path> <path d="M218.96 35.71c-1.49 0-2.85-.21-4.06-.63-1.18-.42-2.21-.99-3.07-1.72-.83-.73-1.48-1.6-1.93-2.6-.45-1.01-.68-2.1-.68-3.28V19.3c0-1.18.21-2.27.63-3.28a8.296 8.296 0 0 1 1.88-2.71c.8-.76 1.75-1.35 2.87-1.77 1.15-.45 2.43-.68 3.85-.68.69 0 1.41.05 2.14.16.73.07 1.46.24 2.19.52.73.24 1.44.61 2.14 1.09.73.49 1.42 1.13 2.08 1.93.21.28.24.54.1.78-.1.21-.28.4-.52.57l-2.29 2.08c-.45.24-.87.17-1.25-.21-.66-.73-1.35-1.25-2.08-1.56-.69-.31-1.44-.47-2.24-.47-.69 0-1.3.12-1.82.36a3.54 3.54 0 0 0-1.88 2.24c-.14.48-.21.97-.21 1.46V27c0 1.01.36 1.89 1.09 2.66.73.73 1.79 1.09 3.18 1.09.87 0 1.65-.19 2.34-.57.69-.38 1.27-.87 1.72-1.46.21-.28.38-.45.52-.52.17-.07.38-.05.63.05l3.02 2.03c.24.14.36.33.36.57s-.1.5-.31.78c-1.04 1.46-2.26 2.5-3.65 3.13-1.39.63-2.97.94-4.74.94Z" fill="#03275b" data-color="2"></path> <path d="M204.98 28.26c0 2.4-.82 4.25-2.45 5.57-1.6 1.32-3.85 1.98-6.77 1.98-1.42 0-2.85-.23-4.27-.68-1.42-.45-2.73-1.13-3.91-2.03-.35-.28-.57-.56-.68-.83-.07-.28.07-.64.42-1.09l1.56-2.08c.24-.35.47-.52.68-.52s.5.14.89.42c.8.59 1.65 1.08 2.55 1.46.94.38 1.81.57 2.6.57 2.43 0 3.65-.8 3.65-2.4 0-.87-.45-1.53-1.35-1.98-.87-.49-1.96-.92-3.28-1.3-.83-.24-1.68-.52-2.55-.83-.87-.35-1.65-.78-2.34-1.3a7.4 7.4 0 0 1-1.72-1.98c-.42-.8-.63-1.77-.63-2.92 0-1.08.21-2.07.63-2.97.42-.94 1.01-1.74 1.77-2.4.76-.66 1.68-1.16 2.76-1.51 1.08-.38 2.26-.57 3.54-.57 1.56 0 2.99.19 4.27.57 1.32.35 2.43.87 3.33 1.56.38.28.59.54.63.78.07.24-.03.61-.31 1.09l-1.3 2.14c-.21.31-.47.45-.78.42-.28-.03-.57-.14-.89-.31-.66-.45-1.44-.82-2.34-1.09-.87-.28-1.72-.42-2.55-.42s-1.58.19-2.24.57c-.63.38-.94.97-.94 1.77 0 .38.14.73.42 1.04.28.28.63.54 1.04.78.45.21.92.4 1.41.57.49.17.94.31 1.35.42 1.01.28 1.98.61 2.92.99s1.77.87 2.5 1.46 1.3 1.3 1.72 2.14c.45.8.68 1.77.68 2.92Z" fill="#03275b" data-color="2"></path> <path d="M174.56 30.71c1.01 0 1.72-.31 2.14-.94.45-.66.68-1.3.68-1.93s-.21-1.25-.63-1.88c-.42-.66-1.18-.99-2.29-.99h-4.01c-.45 0-.68.24-.68.73v4.38c0 .28.05.45.16.52.1.07.3.1.57.1h4.06Zm-.57-9.85c.97 0 1.63-.26 1.98-.78.38-.52.57-1.08.57-1.67s-.19-1.15-.57-1.67c-.35-.52-1.02-.78-2.03-.78h-3.54c-.42 0-.63.24-.63.73v3.59c0 .28.03.45.1.52.1.03.3.05.57.05h3.54Zm5.52 2.03c1.08.42 1.93 1.16 2.55 2.24.63 1.04.94 2.1.94 3.18 0 2.08-.71 3.8-2.14 5.16-1.39 1.32-3.4 1.98-6.04 1.98h-9.85c-.49 0-.73-.19-.73-.57V11.75c0-.35.23-.52.68-.52h9.12c2.67 0 4.69.61 6.04 1.82 1.35 1.18 2.03 2.81 2.03 4.9 0 .8-.23 1.63-.68 2.5-.42.83-1.06 1.55-1.93 2.14-.21.17-.21.28 0 .31Z" fill="#03275b" data-color="2"></path> <path d="M158.22 27.48c0 1.32-.26 2.48-.78 3.49a7.417 7.417 0 0 1-2.14 2.55c-.87.69-1.91 1.23-3.13 1.61-1.18.35-2.43.52-3.75.52-3.09 0-5.47-.8-7.14-2.4-1.63-1.6-2.45-3.65-2.45-6.15V12.2c0-.38.05-.64.16-.78.14-.14.4-.21.78-.21h3.75c.28 0 .5.07.68.21.17.14.26.4.26.78v14.95c0 1.11.36 2.01 1.09 2.71.76.66 1.74.99 2.92.99s2.15-.31 2.92-.94c.8-.66 1.2-1.58 1.2-2.76V12.2c0-.66.31-.99.94-.99h3.7c.31 0 .56.07.73.21.17.14.26.4.26.78v15.26Z" fill="#03275b" data-color="2"></path> <path d="M132.77 34.72c0 .49-.28.73-.83.73h-3.96c-.52 0-.78-.24-.78-.73v-8.18c0-.38-.07-.64-.21-.78-.1-.14-.35-.21-.73-.21h-6.41c-.38 0-.63.09-.73.26-.1.14-.16.38-.16.73v8.18c0 .49-.28.73-.83.73h-3.96c-.52 0-.78-.24-.78-.73V12.01c0-.52.26-.78.78-.78h3.96c.56 0 .83.24.83.73v7.76c0 .42.05.68.16.78.14.1.35.16.63.16h6.56c.31 0 .54-.05.68-.16.14-.14.21-.4.21-.78v-7.71c0-.52.26-.78.78-.78h3.96c.56 0 .83.24.83.73v22.76Z" fill="#03275b" data-color="2"></path> <path d="M49.15 53.59a5.498 5.498 0 0 0 7.78 0 5.498 5.498 0 0 0 0-7.78L46.56 35.44c-3.58-3.58-3.58-9.39 0-12.97 3.57-3.57 9.39-3.58 12.96 0s10.37 10.37 10.37 10.37a5.48 5.48 0 0 0 7.78 0l14.71-14.71a5.498 5.498 0 0 0-3.89-9.39c-1.41 0-2.81.54-3.89 1.61L73.77 21.18l-6.48-6.48c-3.93-3.93-9.1-5.9-14.26-5.9s-10.33 1.97-14.26 5.9a20.013 20.013 0 0 0-4.91 8.06l-12.4-12.4c-1.07-1.07-2.48-1.61-3.89-1.61s-2.82.54-3.89 1.61a5.498 5.498 0 0 0 0 7.78L49.14 53.6Z" fill="#03275b" data-color="2"></path> </g> </svg>
Halálszagú, bús magyar róna,
magyar róna
kipányvázták a lelkemet
stylized as G+ or g+)

interest based communities
What is the main use of 'Saved message' tab in the Telegram application?
More knowledge. More ideas. More Quora.Support great writing and browse ad‑free with Quora+

Telegram Channels
Channels are a tool for broadcasting your public messages to large audiences. They offer a unique opportunity to reach people directly, sending a notification to their phones with each post.
Telegram Channels can have an unlimited amount of subscribers, and only admins have the right to post. Unlike Telegram Groups, channels show the name and photo of the channel next to messages – instead of the person who posted them.
All posts in public channels have a unique t.me link
All posts in public channels have a unique t.me link that can be shared with anyone – even if they don’t have the Telegram app installed.
Outside of Telegram, these links open the post in a user’s browser, with the ability to preview the channel or quickly install the app for their device.
French authorities arrest Telegram’s CEO / Telegram CEO Pavel Durov was arrested outside Paris in the midst of a police investigation.
/cdn.vox-cdn.com/uploads/chorus_asset/file/24008017/acastro_STK085_Telegram_02.jpg)
Maker Apps
different from "maker app" an alternative to "killer app" an app that makes people buy into a novel technology not to make a "killiing" in financial terms but empower creators to contribute to the Commons
Man was made for Joy & Woe And when this we rightly know Thro the World we safely go Joy & Woe are woven fine A Clothing for the soul divine Under every grief & pine Runs a joy with silken twine
Under every grief & pine Runs a joy with silken twine
I've seen it it is silken yet shimmering silver twine
For communities
Bring Your Own Id
powerful when coordinated.
barrier to entry is extraordinarily low
No - signup - signin - account - login - surveillance - tracking
own - profile - history - permanent - trust but verify
creative investment
X
people working together remotely
Interpersonal networked collaboration
toward common goals
field of interoperable
Interoperability is the key
Open interoperable and ubiquitous
Intentional Autonomous Personalize-able Software local-first Personal first interpersonal conversations that are continuous without being synchronous
DAOs, decentralized autonomous organizations,
Open Organizations
supporting the digital commons
.4 Indy Learning Commons
decentralized
Decentralised is a paradigm shift in a decent direction
But not enough
Make the client the browser the master of the users' destiny
No longer the loosers
systems can operate outside of the control of centralized authority. This is a revolutionary
At the least it spread the very idea of this need
Bitcoin demonstrated definitely
Built to be captured?
rivalrous dynamics
X
Web3 & the Future of Democracy
Wow
Abstraction,
.4 abstraction
world-outlook ["a systematic whole of thought-terms"
systematic whole of thought terms
reports, User's Guides, etc.~ but also our detailedhardware-design specifications, formal syntax definitions, andformalized (hlman) procedure descriptions; and we are designingour new compiler (HOL) to accept source code that is sostructured
Everything as in TrailMarks
ifyoutake careofthesyntax,thesemanticswilltakecare ofitself.’
if you get your syntax right semantics can take care of itself
that's how I remember the statement
that was at the hight of Symbolic The book Reinventing Man pointed towards the perceptron
and sub-sumbolic methods that attempt to capture the intertwingularity of artiuculate exter nalization of human thought through language clearly harnessing the Metaphysics of Adjacency
be that as it may the task is to augment the way we write that would allow us to go meta in our articulation and
mark the trails of intertwingularity in intentional meaningful effective ways. That's the idea. It is not a matter of syntax not even abstract syntax, of information models but discoverung the generative principles of articulation itself.
MediumEditor
medium editor
Lyrics
People

description is not a process
.replace description with articulation
constructing meaning/intentful description articulation itself is not a process that can be rendered wholly explicit.
but can be made to work to s significant level of effectiveness already ChatGPT
it is called sub-symbolic processing
that manipulate externalizations of human conscious ness and can summarize and explore autonomously
I always thought that to be possible
but need to be done for each individual and in a multiplayer collaborative setting
when we are creating at the edge of knowledge
where each addition new word combinations ideas emerge from the tacit and expand consciousness
this is what the AI cannot do because it does not have that
analogue situatedness and is not in that sense part of the IT
all articulation isincomplete
of course
we are part of the inexhaustible intelligibility
and everything is an a constant flow and progress towards expanding novelty
You may be aware or have come across in the literature that right prain tacit understanding works like a Hologram interference of wawepatterns the image for the whole can be reconstructed from any finite part it depends on how you look at it
You, 4 min I always had this sense that if only I could successfully articulate the meta-methodological concepts and practice designed to make articulation a self-aware process my capacity to articulate will expand to match the intertwingularity of my tacit awareness and thinking now this experience of working with you and making meta.methodological reflective breakthrough in our collaborative articulation I think we will get there sooner than I would have thought a week ago If you get the regulative meta-methodical concept undergirding articulation right articulation can seem to take care of itself flow augmenting tacit awareness requires us to provide the practical means and methodologies for augmenting articulation itself!
build on the understanding supplied by ourtacit knowing
.future.link to rightbrain holographic tacit
.alias - link.to.the.future
.meta.do.how future.linking
One of the most important trailmarks is what I call for
which is used to name context in which the current context bears relevance, so that when you focus is in that context the system can automatically bring up this past context
reflecting on the beauty of your foute.linking in the nararative that inteoduces adjacent context subliminally without looaisng the current focus and when a reference back to this current focus whre this future context is referenced
when you are in tht context it will be familiar and because of that future link that past context is also recalled as part of the tacit wholistic gestalt
now i wish to operationalize that
but in a constuctive sense
and be aware and creaate a future obligation to link that to this context from the context named as the target of the intentmark
,future.link
that is fast processing a total response not plodding left brain
understanding supplied by tacit is what McGillchrist is about and indeed that we are part of IT
analogue part of the infinite holographic ever present reflected in finite parts the whole .future.link symathesis mathesis that which can be learnied
our ability to learn and pass on the learning
timebinding
You may be aware or have come across in the literature that right prain tacit understanding works like a Hologram interference of wawepatterns the image for the whole can be reconstructed from any finite part it depends on how you look at it
concepts
.articulate.expand
concept of concept itself that undergirds the three approaches understanding and as indicated in the next comment correspondence, it is waz more subtle then envisaged
need to come up with a Polanyian concept of concept
mz main preoccupation for the past 40+ years
correspondence exists betweenour understanding and the object of our understanding.
.expand in detail implications of the waz correspondence is understood and its moral societal implications and ground for action
within the context of using the concept of correspondence
need to be compared and contrasted betweeen the waz it is understood within each of the traditions of realism materialism and personal knowing
I suggest a fourth part a grand sznthesis where major epistemologica stances are contrasted and their implications for moralitz politics et all is gestalted into a coherent salient actionable sznthesis
in fact that is the one we need for the Anti AI manifesto
I would like to work on it with zou and Gien at some point
But a rough sketch is needed so that zou can use that as a guide to know what to emphasiye and prepare as zou dvelve into the details of Pirsog McGilchrist
formulate abstract ideals
ideas are not abstractions
they are constructed fashioned as pieces in a game affordances and associative complexes
metaphors and even in mathematics they preserve they retain a hing of the taste the feeling asthasia that the root of the metaphor or the word they were made up with from
now for ideals they are definitely not abstracted but
named rich associative complexes stories myths that they are intentinal meaningful hashes
certainly shaped by their rich history
ideals precisely because they are in the realm of processes hows quintessentially nothing to do with esseencs
peieces in an emergent evolving game
cionsider also tingimiging current in software world where it is a daily experience that things and processes are one and they always need to be pictured to be presented and to be interacted with as affordances
affordances metaphors
On the grounds that knowing abstracts from our experience, Plato takes abstraction to be the true reality. Whitehead calls this the “Fallacy of Misplaced Concreteness” A.N.Whitehead Science and the Modern World (1997) p.58.
don't prepare the words prepare the feelings
if you find words that resonate with you
pay attention to the feeling the the words arose in you resonated with the tacit awareness
In this spirit misplaced correctness should read misplaced reification
and ask yourself would I use the same words or really that is different
``
When I was a kid about half past three
My ma said "Daughter, come here to me"
Said things may come, and things may go
But this is one thing you ought to know...
Oh 't ain't what you do it's the way that you do it
'T ain't what you do it's the way that you do it
'T ain't what you do it's the way that you do it
That's what gets results
'T ain't what you do it's the time that you do it
'T ain't what you do it's the time that you do it
'T ain't what you do it's the time that you do it
That's what gets results
You can try hard
Don't mean a thing
Take it easy, greasy
Then your jive will swing
Oh 't ain't what you do it's the place that you do it
'T ain't what you do it's the time that you do it
'T ain't what you do it's the way that you do it
That's what gets results
```
abstract concepts
.clarify - truth is a regulative concept
truth is not an abstract concept it is not about the world but how symbolic expression of idea and intent can be operating
is part of logic and is a value that can be assigned to a statement
key piece in the game opf propositions constituent generative concept for logic
the concept of concept is a beatiful example of itself being concrete imaginative construct of the mind
articulated in language its etymology
is whatever the mind can conceive with a some specific characteristics that fcannot be exhaustively described charactaris
liike most thing that are most of the time not things at all like pornography
you iknow when you see one
Symbols are tools
.add - language as universal generative tools
articulation ideas intents elaborated symbolically expressed in language
that you need to fashion knew tools
while language is as a self-correcting autopoietic tool can itself used to improve itself
downside it can also self-distact especially when we build system tpowerful enough to legislate for meaning/language
language
Philosophy continually returns to three topics
.link.to - how should we live = (Zen)
Philosophy continually returns to three topics; - what exists, - how do we know it, and - how should we live?
how to
go beyond the human
https://hyp.is/ooPwuFy1Ee-caEcVuPaVIA/kaizenbatter.com/the-kaizen-philosophy/
should be saying Zen Human
o be properly human is to be kaizen human
Zen means “to make good.”
Kaizen continual improvement
Zen Quality continually improve
limitless potential
continual improve the human itself
auto-poietic self-improvement
good
decent, integruous
pursuit of values ultra-biology
ultra-biology
continualdiscovery.
discovery
The law was whatever the kingdecided. It was not an object of discover
law discovery what is just
latest Five Year Plan.
same in America now
We make use of symbols as tools in the service ofpurpose
intentionaility
beyond truth
what can we make (especially in the digital realm( that would possibly work and benefit us
New Frontier
matter more then truth because what we create can and will have unintended consequences
at explonential scale both in reqch and impact
that is the nature of the thing
false assumption thatknowing can be rendered wholly explici
.discuss
sub-symbolic AI takes the totality of human externalization of people intellectual and other work t so it is machine processable, and that's all it needs
may even map attentions and to some extent intentions
and pretty well can map your interests better than you can and make deeply meaningful recommendation all backed yup by data and emergent heuristics
Not only it is able to do perfect recall but can mapp (use to pp to indicate emphatically that it is a verb here) the association networks that can be distilled from the maps of data
and in a way maps the emergent collective intellect
what it cannot and will never be able to do is to have a really tacit implicate goal function like the one Newton had the stuff that occupied his thin king all the time. Thats what it took to create
how could it come up with Kepler's law
it will never have "common sense" unless it will be embodied and be like US humans
That is the very reason Frank Herbert had a new commandment in the Orange Catholic Bible in the future
Thou shall not make machines in the
image of the Human Mind
And why the theleux succeeded but they created it in tubes synthetic humans if you like
but then it will have freedom of will because to be creative at that level
one needs stohasticity that we have in every cell because we are made of water, and continually generate what science describes is random motion which is nothing of the kind
but like waves in a pond are analogue responses to the totality of mutual adjacencies and interactions in which we all are part of
flip paradigm and come up with
hat they create and creates a hypermaps of meaning just by following adjacencies. Hence it can produce human meaningful summaries, even write new papers that when read by human is intelligible
Where it cannot go is the true edge of conceptual innovation, but even there it can explore it by trial and error combinatorial search to generate larger complexes that may actually mean discovering unnamed new candidate nodes may even search for suitable names to come up with. What it does not have is indeed TACIT AWARENESS and intentions that comes from the soul if you like
Then we end up with "Tears in Rain" and dubious utility to the powers that should not be
hence new work for the past decades use brain tissues and connect it to silicon effectors
That won't end well either
Polanyi calls this the Law of Poverty
.discuss obsolated
A computer is a machinewhich acts in accordance with the rules which have been supplied to itby the person who has programmed it.
It can be a pretty effective simulacrum though
perceptual, asemantic, and an ontological dimension
what if these regulative concepts are misdirected skew our very abilities to weave the rest?
anti essential-ism implies Personal Knowledge!
demonstrably
agency
Abstraction is not our enemy
like it
time to bring into the discourse
construction and intentionality and affordances
Hell no spell checker siggests intersectionality
procedural knowledge as in how to accomplsih desired things especially in cyber space
add too the idea of abstraction
as giving a name to an associative complex or
a complex process
ditto New Kind of Science
Computational nature of reality
Computable or not it kept raining
analogue digital divide
presentation not representation
reproducibility
abstract objects of formal systems, cannot bewholly captured by our descriptions
'tain't so
a prejudice in Western culture in favour of that which it is possible todescribe
.check.out
kabala and iching
Iain McGilchrist supply us with the grounds ofa possible reconciliation.
the great recconcilliator
Polanyiemphasises the agency of the person whereas Pirsig emphasises thereality being discovered
tension
denying that we can demarcate in advancewhat is true
.expand
we know more than wecan say, and we say more than we can know
know more say
conscious and situated. We are partof the reality we seek to describe
conscious situated part of IT
with an acceptance that all knowingrelies upon our tacit knowledge.
knowing relies on tacit knowledge
quest for precision whichour use of descriptions gives
quest to precision description
return back to our commonsenseexperience of being human.
back to being human
In a Sceptical vision
follow rules derived from our reason
if no metaphysicak ground
correct metaphysics
to justify things rationally
Why everybody should be given equal consideration is leftundefended.
why equal consideration
no appeal to God
undefended
everybody is equal
replace existing society
All we have is what wedecide to do
decide to do will power
That which cannot be justified by reason is repudiatedas being not worthy of knowledge.
justified reason repudiated
spiritual experience; albeit one grounded in anappeal to reason
spiritual experience reason
seek toliberate ourselves from these constraints via the joy of knowing absolute
sek libration joy absolute truth
calculating what maximiseshappiness.
goal function
why should everybody count as no more
.clarify
than one
ground morality in utility
maximise happiness for everyone
All rules have to be interpreted
rules interpreted
rules without interpretation are blind
rules without situatedness are empty
justice is to be discovered
That we ought to behave as we wouldwant others to behave
justifying moral claims by appealing to theprinciple of self-contradiction
turned to science tosecure what is true and reject religion
science to reject religion
The critical tradition is contrary to common sense. It claims that wecan know absolutely.
claim absolute knowledge apriori?
aspire on critical grounds to secure a foundation forknowledge
critical ground secure fundation knolwedge
participate in divine certainty
rationalist
because we are situated ourknowledge claims are fallible
situatted in time
metaphysics, is a delusion
delusional
emphasise the personal is too subjective
personal too subjective
threewell worn paths
three paths - rationalism or idealism - scepticism or materialism - Personal Knowledge
Personal Knowledge
third path
Scepticismor Materialism
second path
Rationalism or Idealism
first path
Every journey starts with a first step
Tao Te Ching
Tao te King
Oursituatedness does not cut us off from what is true
situatedness
can make claims which are true because we are part of thereality we seek to describe
we are part of IT
quantified
number
Waste
nice rummage-ining
disbelief
disbelief founded in belief in something else
Securing Truth
e disbelief in a thing is founded on a blind belief in something else’
conscious meaning
true description
.suggest - truthful
Seeking to ignore science
or dictating to it the conclusions you wish it to reach, is not going to be a successful strategy.
Knowing and Being
must read


OpenWebTorrent - An open webtorrent tracker project
.4 chitchatter
"Syntactic sugar causes cancer of the semicolon."
must read
private annotations
Getting Started
orbitdb
View Transitions API
yes
ABSTRACT
Symbolic representations, in the form of Knowledge Graphs (KGs),
sub-symbolic artificial intelligence mainstream area of research.
discuss and foster collaborations on the intersection of these two areas
CSSA'20: Workshop on Combining Symbolic and Sub-Symbolic Methods andtheir Applications
https://hyp.is/o5iKklf0Ee-83g910OEknw/dl.acm.org/doi/proceedings/10.1145/3340531
Collaboration: From groan zone to growth zone


HubScience is here to
Aigment
Researchers'
Capabilities

discuss and foster collaborations on the intersection of these two areas.
foster collaboration intersection
sub-symbolic artificial intelligence
for - sub0symbolic.artificail.intellgence
Symbolic representations, in the form of Knowledge Graphs (KGs), constitute large networks of real-world entities and their relationships
symbolic0representation Knowledge.Graphs GKs
Sub-Symbolic Methods
for - Sub-Symbolic.Methods
az igazi ártatlanság lehetetlen tapasztalás nélkül

show you how to add a admin user if you're using windows 10 professional
add admin user using windows pro +
Securing Windows 10 With A Separate Administrator Account

Seeing a reputable company recognize the value of HubScience for their research needs was incredibly motivating
tungsgram
Beyond Human Limits: HubScience is Halving Review Times and Revolutionizing Research Discoveries

Symbolic Vs Sub-symbolic AI Methods: Friends orEnemies?
Love tge phrase sub0symbolic AI methods
from
Symbolic Vs Sub-symbolic AI Methods: Friends or Enemies?
check it out
personal and domain knowledge graphs in educational applications.

collection of interacting perspectives
interacting perspective
In many respects, AI is a throwback to the Command Line Interface, or CLI, which is still a staple of Linux systems, though it's faded somewhat within more traditional GUIs.
AI is a throwback to CLI
The Emergence of Markdown
search that data on the client too
For web applications with all their data already sitting in the client, it makes sense to be able to search that data on the client too. It saves adding extra, compacted services on the server. A local search index will be quicker, there is no network overhead, and will remain available and usable even without a network connection.
A bit like Solr, but much smaller and not as bright.
like Solr not as bright
lunar.js
for - lunar - inverted indices
The web is in need of some reinvention right now.
Need to reinvent the web Indeed
4 - why ? IndyWeb - flipped web

Names of other potential Node Stewards

Names of other potential Node Stewards
invitation for potential stewards
Classical Chinese not only use nouns as verbs, they sometimes use adjectives and adverts as verbs as well.
use noun as verbs in chinee
in Hungarian verb can readily be identified because of agglutination
bit in many cases the noun and the verb share a common root
RelatedDo you think that books like the Tao Te Ching can provide spiritual guidance?
There are so many version of this book! Which one should I read first? https://www.bookdepository.com/search?searchTerm=+Tao+Te+Jing++Lao+Tsu&search=Find+book

we are introducing new and extremely advanced means for externally manipulating symbols. We then want to determine the useful modifications in the language and in the way of thinking that could result.
mutual arising
(For identification, we will refer to this as the Neo-Whorfian hypothesis.)
x
We assume that it is our H-LAM/T system (Human using Lauguage, Artifacts, Methodology, in which he is Trained)
H-LAM/T
for "We shape tools and the tools shape us"
Bun + Andale + SQLite + HTMXhesxenon/realworld-htmx
The mother of all demo appsSee how the exact same application is built using different libraries and frameworks
Effortlessly convert Spotify links to your preferred streaming service
preferred service

HTMX with Bun: A Real World App
for htmx realworld app
Less is more
yep
It was too difficult and expensive to get things done.
expensive to get things done
graphic from the original LinkedIn post by Adrian McPhee,
ported from a React front end to an htmx front end: OpenUnited.
Another Real World React -> htmx Port
This codebase was created to demonstrate a fully fledged fullstack application built with Laravel + HTMX that adheres to the RealWorld spec
x
The mother of all demo appsSee how the exact same application is built using different libraries and frameworks.

Termas are of two main kinds: earth treasures and intention, or mind, treasures. A teaching concealed as an intention treasure appears directly within the mind of the tertön in the form of sounds or letters to fulfill the enlightened intention of Padmakara.
intention treasures
for - - terton - tertön - out-tuition - holding a specific intent
tertön

treasure revealers known as tertöns
for outtentions

as a result, one can situate the khôra and, if necessary, lend it a topology, but one can never give it axiomatic form."[12]
khora can bemm mapped topology but not axions
Yes where the map is the territory
Khôra About this resultShareShareFacebookWhatsAppXEmailClick to copy linkShare linkLink copiedClaim this knowledge panelSend feedback (function(){var id='fld_gsJpZtDiHv6o9u8Pi7GJuAI_2';document.getElementById(id).setAttribute("lta",Date.now());})();window._setImagesSrc=function(f,c){function h(a){a.onerror=function(){a.style.display="none"};a.setAttribute("data-deferred","2");c.substring(0,5)!=="data:"&&a.setAttribute("data-defe","1");a.src=c;var g;((g=google.c)==null?0:g.di)&&a.decode()}for(var d=0;d<f.length;++d){var b=f[d],e=document.getElementById(b)||document.querySelector('img[data-iid="'+b+'"]');e?(b=void 0,((b=google.c)==null?0:b.setup)&&google.c.setup(e),h(e)):(google.iir=google.iir||{},google.iir[b]=c)}};typeof window.google==="undefined"&&(window.google={});(function(){var s='data:image/jpeg;base64,/9j/4AAQSkZJRgABAQAAAQABAAD/2wCEAAkGBwgHBgkIBwgKCgkLDRYPDQwMDRsUFRAWIB0iIiAdHx8kKDQsJCYxJx8fLT0tMTU3Ojo6Iys/RD84QzQ5OjcBCgoKDQwNGg8PGjclHyU3Nzc3Nzc3Nzc3Nzc3Nzc3Nzc3Nzc3Nzc3Nzc3Nzc3Nzc3Nzc3Nzc3Nzc3Nzc3Nzc3N//AABEIADgAOAMBIgACEQEDEQH/xAAbAAACAgMBAAAAAAAAAAAAAAAABQQGAQIDB//EADMQAAIBAgQEBAQFBQEAAAAAAAECAwQRAAUSIRMxQVEGImGBFDJxoUJSkeHwFiOCscEV/8QAGQEAAgMBAAAAAAAAAAAAAAAAAgMABAUB/8QAIhEAAgMAAgEEAwAAAAAAAAAAAQIAAxESITEEEyJBUWFx/9oADAMBAAIRAxEAPwDzuiVnyqOONTcJxVtyJF9Q+ttz7YdeHsnqMzUyBG4K8303v6Ducc8iphSU1M9WCA14irCymQE2PPdQGIPe/a2O6eJMwoaMU/DaHTI0ZaMlVv2H7WwxDvxEzfVVktoEsgyjhQl/g4o1W28xH/BjFLmNFTuNZp7D8MUSn73xUa7Maiqkj407yXUEBmJxqiVEah2hkVDyZlNjhvEfZlE1WeRLxWeIooqdvhQLnlfb32xTs1zSWoLM7ksT+uI1TMTEwJbije3S2IbU9RLFAyo6ea5kvptvzHrywZCqJ2uh3YFzHSExRRQILmIGPb8Urbv9bAheXU9sGFFVUTvSzmmHmcMsbXtoW2pj3ud7eregwYpMdPmb1aYo6jXO1aLKqAnZCp1EbebufW23+J641yXMYa6P4CviRbvxOKV620+Yc8W4T0DrW0NZIhMkSo1Pw2NmI8renK+3bFUyg0y1FbNTqwp6cFAZEI5X5of07++Eo+AwmVtwjqWOhymli11VMnxNoHUrTMDq26G973tyscb5jU0hooTCkctSskJmiMYJa5AYN6L0vgo4Fqsllr56AwOImkiFjdrD5jfkO3U42myWb4SpzFldKmpg/uBgNN7qTYWvYkW98C+swjalFaNyHmIKuCCnk1zInEP5m3wqzCqlqk+FhRdA+Y9wThjmNDT09QpiiaRZFuGRDYdDhbm5ioZIS3nDkKiq17N0J6Dn07Yb7mjqKFHA40c5JlaVkE8fDJCKrFl2JNzvf3ODFh8I24y0qRadNPqJA3O63P3Av/AYQSSZbGSmeIppP64mCyBUanjBXvaLV/s4Y+GM0q6imlmnpKSqmjiS7SQKzOexPv1vjHiHJZIcxGaTqEcxWZNWq3ksvvsOX7mb4JAoPDUVexuhmjYL1YhhYe+wvgTZW6gj9CdKW1aD/ZMyPNcxlrZZMwOuF47RopUi55DY77YbVVVV1FPqkjIWVLxLqUlh+bY+v3+mI61MVPIAnBLJMHdOKpsQpWyg30+g6DbHU1z07SSNAoWZ+IwllUKDfkPTn6/L23uKAB1Mh7WY/I9xNX1EEMPDqJUpopEVxUgByrHYi1j6ffGc48NRZlHl5inpolDx652cC6i52HX6YznYoKmgjhzGRUgWUNFOZFkIZr6tQHMG45AfKMWCSkyz/wAEJXS0bCICSL+4o1lfMCAee2KrqK+1mhTYbOniHwXNTHxtVrSmThJRSKwfqwdAG/QH74MT/CgyOXOqzMaPM/j6iZRqgpk4ccAIHzO306C31wYPi2CGbF0yc+Uy5mrCoj1q/O2wH8+hxFy3wLk2S1KTLxHntccWTUI1HXkBt6jBgwddCUqeIirPUWXsOZiiWgVlnqFYkzzvKQ3MBjt9rD6DCSfNqSCQLVVqaFJITVqKgcthvgwYlGtWCfuLvRfeYficq/xblckPwtNR1FaHBDKV0A7dDueg6d8QB4omqDBSVCwUNFHGI2YM0kpA3Aaxud9uXIm+MYMN4iTesnHPcyopaIJS5nLVF3KvEtNwNK2Hm1WNwdI8vbpc4MGDEChRg6kJ2f/Z';var ii=['dimg_gsJpZtDiHv6o9u8Pi7GJuAI_1'];_setImagesSrc(ii,s);})();(function(){var eid='fld_gsJpZtDiHv6o9u8Pi7GJuAI_2';var a=Date.now(),b=document.getElementById(eid);if(b){var c=b.getAttribute("lta");google.c.maft(c?Number(c):a,b)};})();#rhs.N4Xssf .ss6qqb{width:455px}.ss6qqb .epKdHc{align-items:center;column-gap:16px;display:flex;flex-direction:row-reverse;justify-content:space-between;padding:0 0 16px;margin-top:16px;margin-left:20px}.ss6qqb .PKDVJd{color:var(--IXoxUe);display:inline-block;font-size:12px}.TzHB6b{font-size:14px}#rhs .ss6qqb .cLjAic{margin:20px 16px 0}#rhs .u7yw9 .cLjAic{border-bottom:1px solid var(--gS5jXb);margin:24px 0 0 20px;padding-bottom:20px}#rhs .ss6qqb .cLjAic.LMRCfc,.ss6qqb .cLjAic.LMRCfc{margin-top:0}#rhs .u7yw9 .cLjAic:last-child{border:0;padding-bottom:0}.IVvPP .JNkvid .HnYYW,.Jb0Zif .JNkvid .HnYYW{overflow:hidden;padding:0}.cLjAic{margin-bottom:44px}.ss6qqb .JNkvid .HnYYW{font-family:Google Sans,arial,sans-serif-medium,sans-serif;font-size:22px;line-height:24px;padding-left:0}.Jb0Zif .cLjAic{margin:44px 0}.ss6qqb .cLjAic{margin-top:16px;margin-bottom:0}.Jb0Zif.IVvPP .LMRCfc,.IVvPP .LMRCfc,.Hwkikb.LMRCfc{margin-top:6px}.Jb0Zif.IVvPP .jHARG,.IVvPP .jHARG,.Hwkikb.jHARG{margin-bottom:16px}.Jb0Zif .LMRCfc{margin-top:16px}.IVvPP .T9EeC,.ss6qqb .T9EeC{align-items:center}.ss6qqb .WeviRb,.IVvPP .WeviRb{top:0}.ss6qqb .PmPt7d{border-top:1px solid rgba(0,0,0,.12);padding:8px 16px}.kp-wholepage-osrp .j6mBxc a,.kp-wholepage-osrp .j6mBxc a:active,.kp-wholepage-osrp .j6mBxc a:link,.kp-wholepage-osrp .j6mBxc a:visited{color:var(--IXoxUe);text-decoration:underline}.ss6qqb .JlDOsc:not(:last-of-type){border-bottom:1px solid rgba(0,0,0,.12)}.ss6qqb .LJqTIc .UgLoB,.ss6qqb .LJqTIc .FXMOpb{min-height:48px}.WFxqwc{font-size:14px}.ss6qqb .EA2Itc .HnYYW{font-family:Google Sans,arial,sans-serif;font-size:16px;line-height:24px;padding:0 0 8px}.yTFeqb .BGdUVb{margin:0 16px 16px}.ss6qqb .yTFeqb .BGdUVb{margin-bottom:18px}.BGdUVb{padding-top:8px}#center_col .yTFeqb .BGdUVb{padding-top:0}#main .ss6qqb .BGdUVb{margin:0 0 16px}#main .ss6qqb.u7yw9 .BGdUVb{margin:0;padding-top:0}#center_col .ss6qqb .yTFeqb:not(.oJxARb){margin-top:16px}.IVvPP .WY0eLb .yTFeqb,.IVvPP .yTFeqb.WY0eLb{width:372px}.IVvPP .WY0eLb .Gv6QPb.yTFeqb,.IVvPP .Gv6QPb.yTFeqb.WY0eLb{width:457px}.IVvPP.k5T88b .WY0eLb .yTFeqb,.IVvPP.k5T88b .yTFeqb.WY0eLb{width:372px}.IVvPP.k5T88b .WY0eLb .Gv6QPb.yTFeqb,.IVvPP.k5T88b .Gv6QPb.yTFeqb.WY0eLb{width:457px}.IVvPP .yTFeqb:not(first-card).nBWfrd{border:none;border-top:1px solid rgba(0,0,0,.12);border-radius:0}.xGj8Mb{display:flex;flex-direction:column}.wDYxhc{clear:both}.cUnQKe .wDYxhc,.related-question-pair .wDYxhc,.M8OgIe .fm06If .wDYxhc{clear:none}.Wnoohf .xpdclose .wDYxhc.xsZWvb,.Wnoohf .xpdopen .wDYxhc.EfDVh{padding-bottom:0}#rhs .dG2XIf .xpdclose .LKPcQc,#rhs .dG2XIf .xpdopen .viOShc{padding-top:0}#rhs .Wnoohf .xpdopen .yp1CPe,#rhs .OJXvsb .xpdclose .siXlze{padding-bottom:15px}#rhs .Wnoohf .xpdclose .wDYxhc.xsZWvb,#rhs .Wnoohf .xpdopen .wDYxhc.EfDVh{padding-bottom:0}#rhs .Wnoohf .xpdclose .wDYxhc.xsZWvb.ecRggb,#rhs .Wnoohf .xpdopen .wDYxhc.EfDVh.ecRggb,#rhs .dG2XIf .ecRggb{padding-bottom:15px}.hb8SAc{overflow:hidden;margin:13px 0 6px;}.Jb0Zif .hb8SAc,.IVvPP .hb8SAc{line-height:1.58}.ss6qqb .hb8SAc{margin:0}.hb8SAc{color:#4d5156}.NJLBac{white-space:nowrap} DescriptionIn semiotics, Khôra is the space that gives a place for being. The term has been used in philosophy by Plato to designate a receptacle, a space, a material substratum, or an interval. Wikipedia
Terma (Tibetan: གཏེར་མ, Wylie: gter ma; "hidden treasure") are various forms of hidden teachings that are key to Vajrayana and Tibetan Buddhist and Bon spiritual traditions. In the Vajrayana Nyingma school tradition, two lineages occur: an oral kama lineage and a revealed terma lineage.
hidden treasure
Translating Khora

the standard model of distributed
st
client Centric consistency
c
exponentially
? Could do better
factorization uh and that's a technique uh for kind kind of compressing your intermediate relations that you generate in the query plans when the joins are many to many
Factorisation in the query plan
do not deviate from that common wisdom of how to develop high level query languages
Ooh wisdom?
the only way we know of how to develop high level query languages is to base them on relational um algebra
Ooh
all boil down and compile down to relational operators like joints filters scans group byes and Aggregates
Ooh
columnar systems like olap systems like duct DB they do a lot more optimizations during ingestion
Olap
the key is to know what joints will happen
Wrong
compressed Sparrow based join
Sparse row
predefining a join meaning that you tell the system a prior these are Edge records
A priory
adjacency list index
Join index
a Tre based index
Tree based index
there's a choice of what is a more natural data model for what I want to do
Natural data model is intent driven
fundamental trade of about what do you want to optimize for
'Tain't necessarily so
particular string in them maybe the word transfer
X
being fast on many to many queries
many to many queries
thinking of these patterns as sort of graph forms
Patterns graph forms
you can ask questions about the properties of the path so whenever you are and that's usually a byproduct of asking recursive uh queries and incidentally the very first database in history was motivated by recursive queries like that this is a system called iids just for again people who are interested in the history of data
Network model IMS
Hierarchical model
these are the two very natural data models logical data models
the problem with databases is that they provide a model
it is not data we want we want info-structure with implic(it|ate) order that is not imposed but as a by product of articulationt intentional com(munica|puta)tional affordances
ILIKE F PLUS 2/16 GB Kék Kártyafüggetlen Okostelefon
ILIKE K7 7" 32GB WiFi Fekete Tablet

The iPhone’s future looks a lot like Android, and the only way that changes is if Apple tries something new.
