Host any Data that you do not have a right to reproduce,
right to reproduce
Host any Data that you do not have a right to reproduce,
right to reproduce
Passwords cannot be recovered.
passwords are not recoverable
Under no circumstances will Peergos be liable for any reason for the existence or content of any Data on Peergos.
Peergos not liable for content
in receipt of a public sharing link
Peergos (including, if you so authorise, making your Data available to other users in receipt of a public sharing link).
You should keep a local backup of any Data stored using Peergos
need a local running mirror and/or IPFS Desktop or Brave IPFS
PEERGOS TERMS OF USE
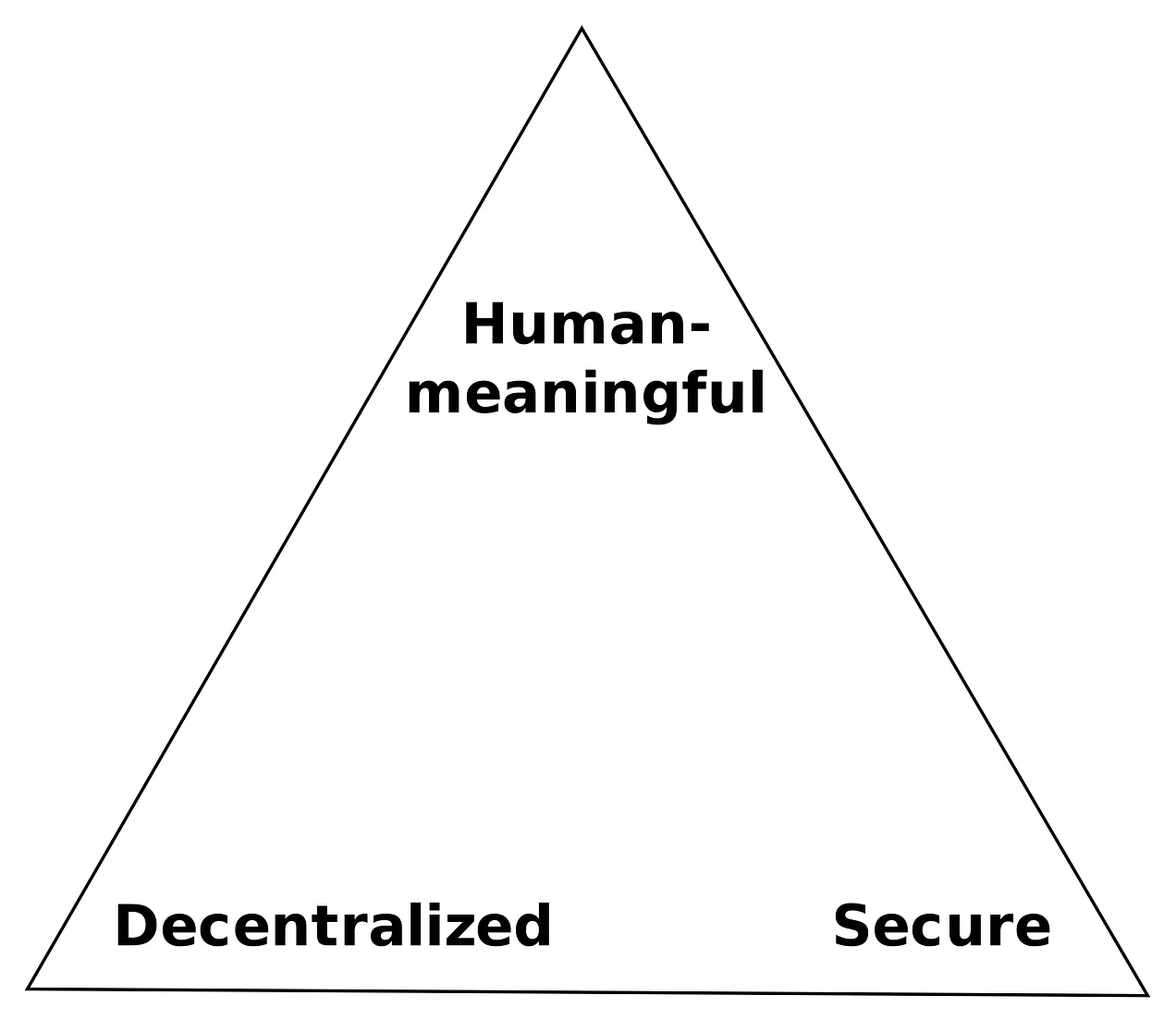
Secure, decentralized, meaningful, pick two
!- threads :
Peergos is building the next web - the private web, where end users are in control.
your private online space
privacy is a fundamental human right
privacy right
Imagine never having to log in to an app ever again.
Never having to log into an app ever!
Peergos is built on top of IPFS. You can run Peergos on your own machine and still access your files through any other Peergos server.
It is the x,y coordinates of the text baseline start position (in the left bottom corner of the first char).
answer
Understanding SVG <text> x-y coordinates and padding
It is the x,y coordinates of the text baseline start position (in the left bottom corner of the first char).
fill-opacity
The fill-opacity attribute is a presentation attribute defining the opacity of the paint server (color, gradient, pattern, etc.) applied to a shape.
``` <svg viewBox="0 0 400 100" xmlns="http://www.w3.org/2000/svg">
<circle cx="50" cy="50" r="40" />
<circle cx="150" cy="50" r="40" fill-opacity="0.7" />
<circle cx="250" cy="50" r="40" fill-opacity="50%" />
<circle cx="350" cy="50" r="40" style="fill-opacity: .25;" /> </svg> ```
Rainbow Stock Images

“Richard Of York Gave Battle In Vain”

ROYGBIV or VIBGYOR Rainbow Color Codes

Can I change the fill color of an svg path with CSS?
<path style="" fill="#333333"
img.src = "data:image/svg+xml;base64,"+btoa(xml);
img.src = "data:image/svg+xml;base64,"+btoa(xml);
set img.src to dynamic svg element
jsfiddle perma.jsfiddle w3s.jsfiddle
.google.search - "lazy encyiption"
This is a lazy encryption system
.for: lazy encyption
in that it's not designed to - securely obscure data,
but rather that it is designed to - prevent people from reading data - without first taking steps to decrypt it.
This makes this system useful for - hiding clues in games,
where people can use a deciphering tool within the game itself if they really want to spoil the answer. Other uses are left to the imagination.
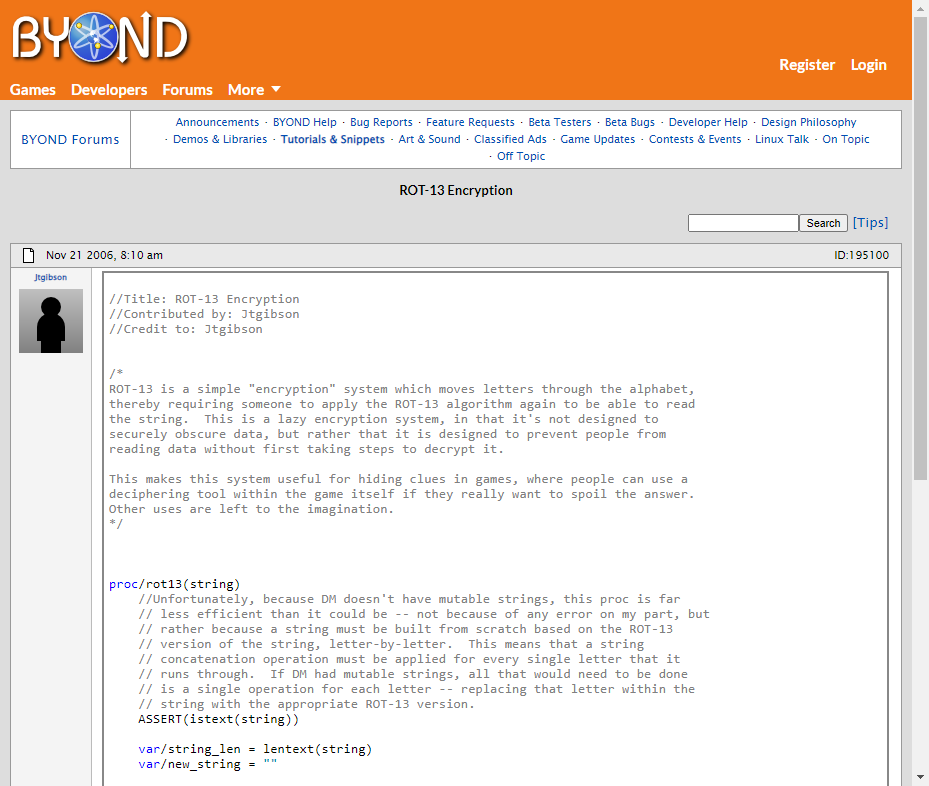
.for: lazy encryption

160IPFS
IPFS is a - global, - versioned, - peer-to-peer - filesystem.
It combines ideas from - Git, - BitTorrent, - Kademlia, - SFS, and the - web.
It is like - a single bittorrent swarm, - exchanging git objects.
IPFS provides - an interface - as simple as the HTTP web,
but with - permanence - built in.

0Spot-On Encryption Suite
Spot-On is Encryption software that securely connects two friends for chat, group chat, email, file sharing and file transfers with magnet links and P2P web search.

.from: "android peergos - Google Searc…" (www.google.co.uk)
Cloud Storage Services and other similar apps like Peergos
Peergos is a secure and private online space where you can store, share and view your photos, videos, music and documents.
.to "Peergos: Secure and private on…"(alternativeto.net)

Nov 29, 2023 — Our crowd-sourced lists contains more than 10 apps similar to Peergos for Windows, Linux, Mac, Android and more ... Android and Self-Hosted apps ...
self-hosted apps alternatives
 .to: "Peergos Alternatives: Top 10 C…"
(alternativeto.net)
.to: "Peergos Alternatives: Top 10 C…"
(alternativeto.net)
.google.search: android peergoss
.google.search: android+peergos
PeergosPeergos is a secure and private online space where you can store, share and view your photos, videos, music and documents.

This allows you to store "deep bookmarks"
to things in Peergos which don't reveal anything to someone who get's access you your bookmarks!
All you need is your username and your password
Can do away with that too
It is not tied to any other data like your phone number or email address.
.for - No Account
Dec 21, 2023 — Consider a lazy encryption scheme that does not encrypt a message at all:
does not encrypt at all
lazy re-encryption.
.to.do-search - lazy enciption
secret link mechanism for sharing files with people who do not have peergos accounts.
.for - Indy.Web.Mesh.Net/Hub/One/Dialog/Linminal
sharing files with people who do not have peergos account!
Following can be revoked
following allows sharing between peers
Following is a one-way mechanism
following one way
The web interface can be accessed from a public server over https or from your machine if you run Peergos locally.
same for the IndyWeb
location independence!
You even load it directly from ipfs and log in!
Entirely client side load it from IPFS and log in!
aim to be as convenient to use as existing centralised services,
as convenient and usable as centralised services
Hashes and signatures are all verified client side
client side verification
Because the server only ever sees encrypted data you can also tell it to directly store your data in a standard cloud storage provider like Backblaze or Amazon
.query - or IPFS?
Peergos is fully self hostable
.to.do : must try it out for self osting
no central surveillance point that an attacker could monitor all file transfers
no central suveilance point
Free and Open Source Enterprise Resource Planning (ERP)
entrprise Resource Plannig
FOSS

.from: .search: custom app update
The most agile ERP on the planet ERPNext is the world's best free and open source ERP
Open source ERP
.for - custom app - peergos

Updating custom app
frappe
Black Chess Rook ♜
emoji.for: peergos
Powerful rich text editor framework with a modular architecture, modern integrations, and features like collaborative editing
available via Peergos,net
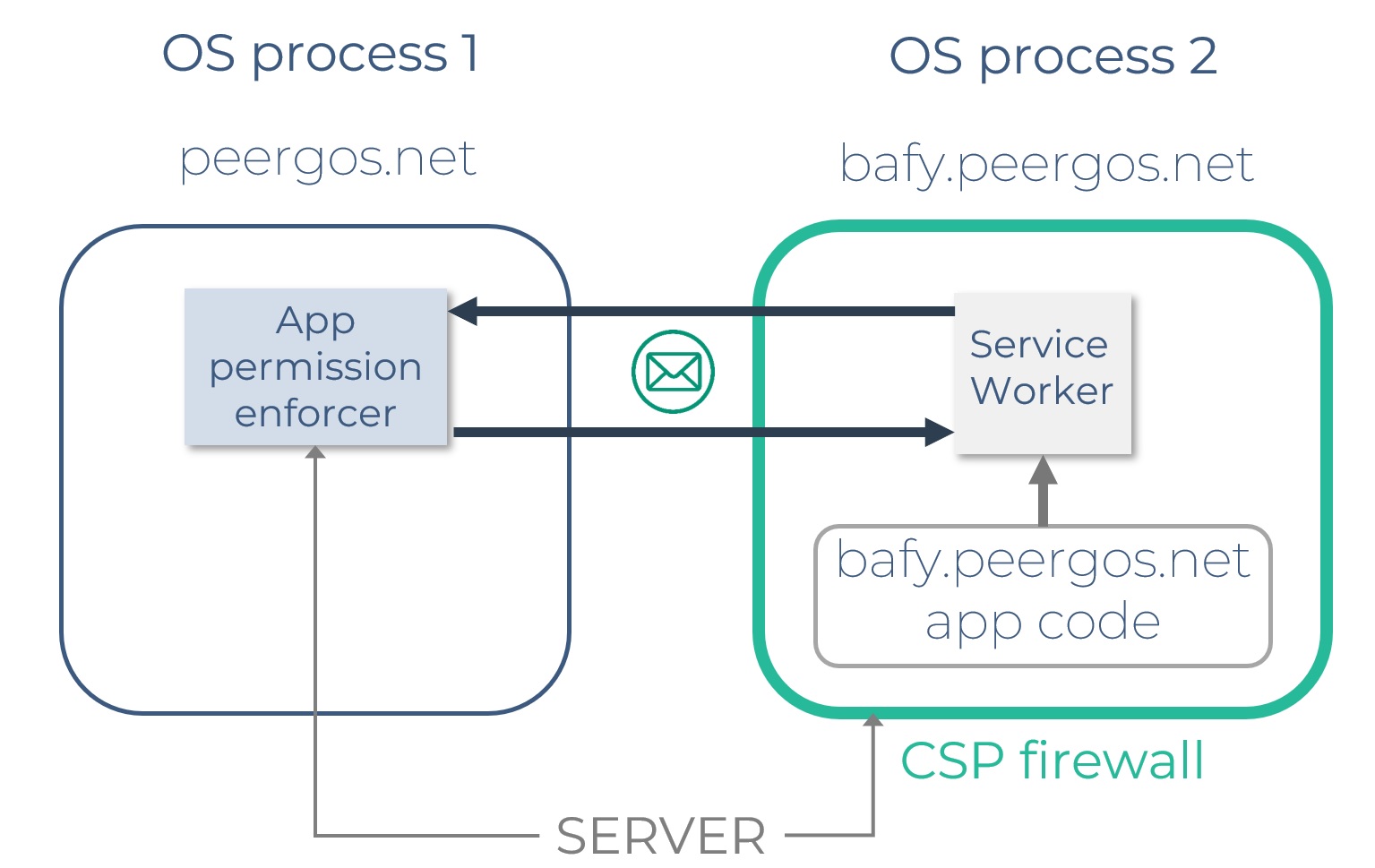
Make WebRTC usable as a backend for Service Workers to fulfill requests from a peer-to-peer network
Make WebRTC usable as a backend for Service Workers to fulfill requests from a peer-to-peer network w3c/webrtc-pc#2553)
WebRTC as a backend
Make WebRTC usable as a backend for Service Workers to fulfill requests from a peer-to-peer network w3c/ServiceWorker#1522
pretty much what we do for indyweb
WebRTC can be used for exfiltration w3c/webappsec-csp#92,
This is where we came from
"The fetch event lets us intercept every network request made by the PWA in the service worker's scope, for both same-origin and cross-origin requests"
complications?
Publish app to well known location: halo.dxos.org
Using the app, users can:
from: https://hyp.is/9c5qEuHxEe6Ulo-hzKcczg/github.com/w3c/webappsec-csp/issues/92
https://github.com/dxos/.github/raw/main/profile/github-repo-banner.png
.from: - https://hyp.is/KZJ21uHyEe6Ul8Mvpg5jwQ/github.com/w3c/webrtc-pc/issues/230
.from: https://hyp.is/VrBThOH0Ee6jrOcx2gl1Fw/github.com/w3c/webappsec-csp/issues/92
a peer-to-peer network is no good if nobody can seed data back after downloading it
p2p seed back data
Make WebRTC usable as a backend for Service Workers to fulfill requests from a peer-to-peer network
Problems define their own solutions
for indy,web.mesh.net.work
Adding a New Search Engine Shortcut
SigmaOShttps://sigmaos.com › tips › browsers › how-to-change-...SigmaOShttps://sigmaos.com › tips › browsers › how-to-change-...About featured snipp
.how.to: change search engine in brave
Chrome - set search bar to google.co.uk, not google.com?
zhenyasav mentioned this issue Oct 10, 2022 HALO application dxos/dxos#1630
.to: HALO application
amark mentioned this issue Feb 15, 2022 Add support for WebRTC Data Channel in Workers w3c/webrtc-pc#230
some implementations send media without requiring the other party to have learned the sender's password (the focus of ICE consent is to make sure the other party wants to receive your data, not on whether you want to send it to him).
ICE consent
ensure that the other party wants to receive your data
Oh, and in answer to @martinthomson 's prescient post from 3 years ago, (link above) it would be pretty simple to exfiltrate data over DTMF (which was added in the meanwhile). It would be only slightly harder to do it over G711. So I don't believe this is a data-channel issue. In my view it is an ICE issue - ICE is supposed to be the webRTC consent mechanism. Ice-lite breaks that.
exfiltrate
ice-lite braks that
connect-src already supports urls: Content-Security-Policy: connect-src https://example.com/ So it would be trivial to add stun: and/or turn: urls to it, like: Content-Security-Policy: connect-src https://example.com/ stun:stun.services.mozilla.com
connect-src supports urls
More and more sites are (ab)using WebRTC to pull data from remote servers through browsers with no obvious way for users to be informed about such connections to remote servers, and no mean to prevent these connections from happening on a per-site basis. I observe that such use is spreading fast. Example:
pull data from remote servers without users knowledge
WebRTC can be used for exfiltration
from: "Custom Apps -" (book.peergos.org)
exfiltration

TypeScript implementation of the DXOS protocols, SDK, and toolchain.

.from: https://hyp.is/KZJ21uHyEe6Ul8Mvpg5jwQ/github.com/w3c/webrtc-pc/issues/230
DXOS The Decentralized Operating System

Add support for WebRTC Data Channel in Workers #230
self.link: google.search - peergos install upgrade custom app
.google.search : peergos+install+upgrade+custom+apps
.pern.an0: peergos install upgrade custom app - Google Search
Aug 2, 2022 — We have an application sandbox to run custom apps. How does it work? An app in Peergos is basically just a folder of HTML5 assets. The
to: "A better web" (peergos.org) let people own their - identity and - data - grant web app access to these
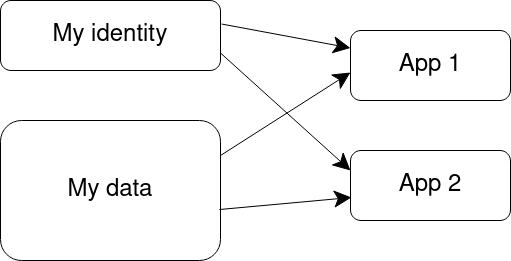
An app in Peergos is basically just a folder of HTML5 assets. The ...
to: "A better web" (peergos.org)

instead of the current
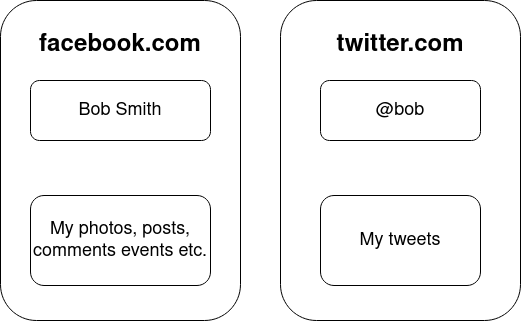
We run a server at https://peergos.net/. There are a limited number of free accounts available. You can upgrade to a paid account to get more storage. Tech
.google.search : peergos+install+upgrade+custom+apps
.pern.an0: peergos install upgrade custom app - Google Search

Peergos Apps are a way to extend the Peergos platform to add custom functionality

it cannot make any external requests which could be used to exfilrate data [0].
exfiltrate data
with webrt
to
- "WebRTC can be used for exfiltr…"
(github.com)

google.search: peergos install upgrade custom apps
The immersive programming experience Pharo is a pure object-oriented programming language and a powerful environment, focused on simplicity and immediate feedback (think IDE and OS rolled into one).
from - Writing Code Without Plain Tex…

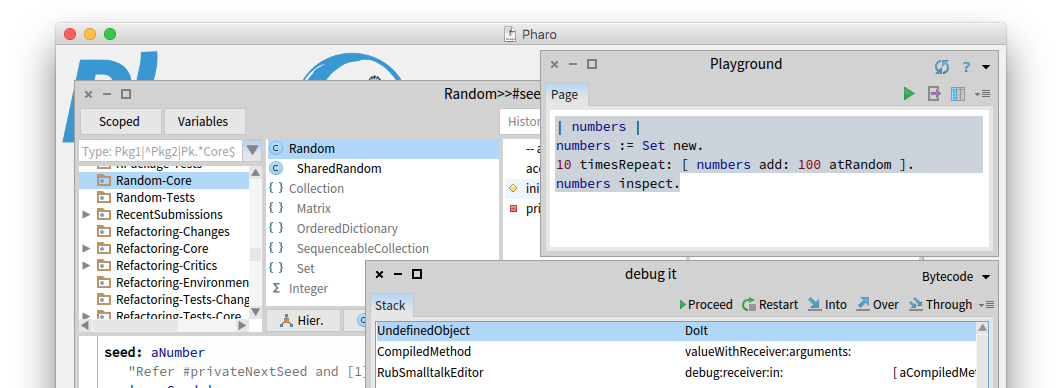
Pharo Smalltalk stores every method in a separate files
Julia REPL
= Beyond REPL
Julia is wonderful because it can integrate with other languages and the Unix shell so well.
julia inyegrate
pure functional programming and static typing
pure functional static typing
prefer dynamically typed languages such as Lua and Julia
dynamically typed language - Lua - Julia
study the history
recapitulable replayable history with provenance is key indeed entire context
no code for you to forget to change or update to reflect the new change
yes
based around manipulating plain text files
absurd indeed
one true way of doing things
no one true way but all ways worthy of using must be amenable to be morphed into any otther
Unison doesn’t store source code; it stores ASTs
ASTs
able to track the history of each function.
track history of each function
tracks changes at the level of individual functions and type definitions instead of at the level of files
track changes individual functions
that's not enough
Tighter Integration Between Tools and Language
indeed
have to add enough qualifiers to uniquely identify the function you are calling
add enough qualifiers
typically avoid all the long package import ceremony found in Java
package import ceremony
it will never fail to build.
too bad
duplicating the old hierarchy with new hashes

Writing Code Without Plain Text FilesThe Unison programming language doesn’t store code in files, but in a database. What is that like?
source - "Writing Code Without Plain Tex…" (itnext.io)

The Unison programming language doesn’t store code in files, but in a database. What is that like?

personal.archived - https://ipfs.indy0.net/ipfs/QmQz4CcH6Buwb48hi4skRuXbwf5wVvMPpDqJDbKcBbb4uB?p=QmaZHodquC4dhjn8Ct6GG9zFvJjfYD6j4AoAmAakeTygdG - in: https://hypothes.is/a/UY8YsuBMEe6Jnkt8qYLGRA - from: https://hypothes.is/a/UY8YsuBMEe6Jnkt8qYLGRA - by: gyuri
What Makes Smalltalk Unique?Exploring the implication of software development without files

ParaChat Chat Replacement
<svg xmlns="http://www.w3.org/2000/svg" viewBox="0 0 201 34" xml:space="preserve" style="fill-rule:evenodd;clip-rule:evenodd;stroke-linejoin:round;stroke-miterlimit:2"><path d="m.441-.163-.009.012a.247.247 0 0 1-.138.055C.249-.096.213-.13.19-.166a.362.362 0 0 1-.024-.146c0-.064.01-.128.037-.187.024-.055.062-.12.131-.14a.345.345 0 0 1 .064-.005l.008.001a.034.034 0 0 1 .023.031c0 .018-.02.081-.03.099l-.023.035a.077.077 0 0 0-.014.039c0 .016.014.036.039.036.06 0 .105-.131.105-.187 0-.053-.016-.08-.061-.117a.043.043 0 0 0-.007-.006L.432-.719A.147.147 0 0 0 .35-.741a.227.227 0 0 0-.142.052L.17-.66c-.113.088-.151.231-.151.353 0 .076.009.172.066.238.038.044.093.08.165.08.101 0 .174-.058.236-.132a.039.039 0 0 0 .009-.023c0-.01-.007-.03-.029-.03-.009 0-.018.006-.025.011Z" style="fill-rule:nonzero" transform="translate(-.132 28.947) scale(38.95234)"/><path d="m.071-.073.01.007a.044.044 0 0 0 .028.008.058.058 0 0 0 .04-.016c.006-.005.009-.012.012-.017l.007-.017c.006-.011.007-.021.008-.029s0-.017.003-.026a.78.78 0 0 1 .108-.206c.003.022.003.044.005.064l.007.146C.3-.138.3-.117.305-.097c.001.006.004.011.006.016l.009.014c.01.018.03.03.056.03.038 0 .056-.025.066-.047a.156.156 0 0 0 .01-.059c0-.07-.007-.205-.028-.274C.411-.46.38-.519.328-.519a.065.065 0 0 0-.037.012.059.059 0 0 0-.02.018 1.029 1.029 0 0 0-.087.121c.002-.05.005-.1.005-.15L.186-.596C.183-.636.173-.678.124-.678a.066.066 0 0 0-.051.025c-.038.044-.046.39-.046.446 0 .029.001.058.008.086a.076.076 0 0 0 .027.04l.009.008Z" style="fill-rule:nonzero" transform="translate(19.616 28.947) scale(38.95234)"/><path d="M.158-.129C.155-.131.155-.133.155-.133c0-.041.095-.1.146-.129a.761.761 0 0 0 .008.094l-.023.009-.048.024a1.508 1.508 0 0 1-.043.016.119.119 0 0 1-.025-.005L.158-.129Zm.173.044C.346-.049.377 0 .434 0A.065.065 0 0 0 .5-.063a.091.091 0 0 0-.009-.036.296.296 0 0 1-.028-.075C.455-.21.454-.247.452-.283.45-.323.45-.364.447-.404.443-.48.426-.553.334-.553c-.059 0-.128.036-.149.081a.065.065 0 0 0-.004.02c0 .015.007.028.03.028l.022-.002.019-.003a.313.313 0 0 1 .043-.004c.002.024.002.047.002.07L.27-.365c-.109 0-.263.119-.263.238 0 .076.064.139.162.139.078 0 .118-.041.162-.097Z" style="fill-rule:nonzero" transform="translate(37.34 28.947) scale(38.95234)"/><path d="M.093.096C.099.115.13.129.148.129A.054.054 0 0 0 .174.123C.196.109.203.012.203-.015c.005-.12.006-.24.017-.361a.4.4 0 0 0 .118-.03.03.03 0 0 0 .013-.025.031.031 0 0 0-.018-.028.338.338 0 0 0-.107-.018.277.277 0 0 0-.003-.068C.219-.572.205-.603.168-.603c-.02 0-.031.012-.042.026a.462.462 0 0 0-.04.132c-.019.007-.077.029-.077.052 0 .009.008.024.027.024l.038.003c-.012.096-.02.194-.02.291a.322.322 0 0 0 .039.171Z" style="fill-rule:nonzero" transform="translate(56.66 28.947) scale(38.95234)"/><path d="M.158-.129C.155-.131.155-.133.155-.133c0-.041.095-.1.146-.129a.761.761 0 0 0 .008.094l-.023.009-.048.024a1.508 1.508 0 0 1-.043.016.119.119 0 0 1-.025-.005L.158-.129Zm.173.044C.346-.049.377 0 .434 0A.065.065 0 0 0 .5-.063a.091.091 0 0 0-.009-.036.296.296 0 0 1-.028-.075C.455-.21.454-.247.452-.283.45-.323.45-.364.447-.404.443-.48.426-.553.334-.553c-.059 0-.128.036-.149.081a.065.065 0 0 0-.004.02c0 .015.007.028.03.028l.022-.002.019-.003a.313.313 0 0 1 .043-.004c.002.024.002.047.002.07L.27-.365c-.109 0-.263.119-.263.238 0 .076.064.139.162.139.078 0 .118-.041.162-.097Z" style="fill-rule:nonzero" transform="translate(67.41 28.947) scale(38.95234)"/><path d="M.193-.082C.168-.106.167-.155.167-.187c0-.061.017-.17.061-.218a.031.031 0 0 1 .011-.009.058.058 0 0 1 .025-.005l.009.005.016.013a.086.086 0 0 0 .047.019.025.025 0 0 0 .018-.008C.364-.397.37-.424.37-.435c0-.059-.054-.122-.136-.122-.164 0-.217.235-.217.362 0 .045.006.086.022.13.019.049.069.111.146.111.09 0 .163-.103.163-.189 0-.013-.009-.026-.029-.026l-.007.002a.019.019 0 0 0-.007.002l-.01.005a.248.248 0 0 0-.092.069.09.09 0 0 1-.01.009Z" style="fill-rule:nonzero" transform="translate(86.73 28.947) scale(38.95234)"/><path d="M.174-.136a.694.694 0 0 1-.005-.091c0-.042.003-.082.003-.123a.188.188 0 0 0-.007-.058C.158-.429.143-.448.112-.448c-.084 0-.093.187-.093.247 0 .064.003.209.106.234a.085.085 0 0 0 .023.003c.07 0 .12-.089.15-.144.006.046.021.092.077.092.049 0 .073-.035.073-.08A1.099 1.099 0 0 1 .443-.21l.001-.068C.444-.33.442-.407.37-.407c-.01 0-.02.002-.028.006C.32-.392.299-.36.295-.342l-.002.013-.02.038c-.03.054-.062.106-.099.155Z" style="fill-rule:nonzero" transform="translate(100.988 28.947) scale(38.95234)"/><path d="M.151-.026.16-.041c.003-.006.006-.012.006-.018a.023.023 0 0 0-.009-.018l.001-.024c0-.024.003-.047.005-.071a4.34 4.34 0 0 1 .01-.108c.006-.055.009-.111.013-.166.002-.033.005-.068.005-.102a.477.477 0 0 0-.012-.113C.174-.674.161-.696.135-.696c-.028 0-.039.023-.043.036a.688.688 0 0 0-.03.131c-.017.13-.039.258-.039.389 0 .055.006.142.08.142a.05.05 0 0 0 .048-.028Z" style="fill-rule:nonzero" transform="translate(118.594 28.947) scale(38.95234)"/><path d="M.158-.129C.155-.131.155-.133.155-.133c0-.041.095-.1.146-.129a.761.761 0 0 0 .008.094l-.023.009-.048.024a1.508 1.508 0 0 1-.043.016.119.119 0 0 1-.025-.005L.158-.129Zm.173.044C.346-.049.377 0 .434 0A.065.065 0 0 0 .5-.063a.091.091 0 0 0-.009-.036.296.296 0 0 1-.028-.075C.455-.21.454-.247.452-.283.45-.323.45-.364.447-.404.443-.48.426-.553.334-.553c-.059 0-.128.036-.149.081a.065.065 0 0 0-.004.02c0 .015.007.028.03.028l.022-.002.019-.003a.313.313 0 0 1 .043-.004c.002.024.002.047.002.07L.27-.365c-.109 0-.263.119-.263.238 0 .076.064.139.162.139.078 0 .118-.041.162-.097Z" style="fill-rule:nonzero" transform="translate(126.345 28.947) scale(38.95234)"/><path d="M.171-.243C.175-.285.18-.325.183-.367v-.017c0-.037-.013-.08-.057-.08-.03 0-.05.029-.058.045a.89.89 0 0 0-.05.294c0 .045.003.121.046.159.01.008.026.017.042.017.023 0 .05-.018.056-.041C.19-.132.227-.261.3-.387c.012.021.033.041.065.041a.07.07 0 0 0 .07-.07c0-.032-.04-.108-.085-.118a.083.083 0 0 0-.022-.003c-.024 0-.045.022-.051.036l-.016.042c-.016.035-.033.067-.048.102-.016.038-.03.075-.042.114Z" style="fill-rule:nonzero" transform="translate(145.666 28.947) scale(38.95234)"/><ellipse cx="2729.05" cy="1066.99" rx="51.426" ry="37.826" style="fill:#fff" transform="matrix(.16337 0 0 .16337 -267.184 -158.735)"/><path d="M180.72 32.719c-8.29 0-15.018-6.73-15.018-15.019S172.43 2.682 180.72 2.682c8.289 0 15.018 6.73 15.018 15.018a15 15 0 0 1-.17 2.265 24.428 24.428 0 0 0 3.434-.812 1.234 1.234 0 0 1 1.57 1.465c-1.838 6.866-9.972 12.06-19.738 12.1h-.114Zm-6.066-19.771c.985 0 1.784 1.08 1.784 2.411 0 1.332-.799 2.413-1.784 2.413-.983 0-1.784-1.081-1.784-2.413 0-1.331.8-2.411 1.784-2.411Zm6.899 0c.985 0 1.784 1.08 1.784 2.411 0 1.332-.799 2.413-1.784 2.413-.983 0-1.782-1.081-1.782-2.413 0-1.331.799-2.411 1.782-2.411Z"/></svg>
ParaChat Replacement
Chatacular can be directly connected to your app's authentication system.
authentication system
add stunning embeddable chatrooms to their website. No coding, just chatting. Click and go!
Stunning group chats for your websiteUse Chatacular to create chatrooms that your users will love using!
from - https://hyp.is/xs75FOD-Ee6qpTdBlniOJQ/www.scaledrone.com/blog/javascript-chat-room-tutorial/
Are We Watching The Internet Die?

20 Years of Open Source building XWiki and CryptPad
for - XWiki - CryptPad - FOSDEM 2024
Unicode Character “‽” (U+203D)
emoji - interrobang

<svg width="128" height="128" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" enable-background="new 0 0 128 128" viewBox="0 0 128 128"><linearGradient id="a"><stop offset="0" stop-color="#ff5252"/><stop offset=".2061" stop-color="#fd4d4d"/><stop offset=".4365" stop-color="#f64040"/><stop offset=".6787" stop-color="#ea2a2a"/><stop offset=".9274" stop-color="#da0b0b"/><stop offset="1" stop-color="#d50000"/></linearGradient><linearGradient id="b" gradientUnits="userSpaceOnUse" x1="77.996" x2="77.996" xlink:href="#a" y1="3.708" y2="122.64"/><linearGradient id="c" gradientUnits="userSpaceOnUse" x1="79.45" x2="79.45" xlink:href="#a" y1="3.708" y2="122.64"/><linearGradient id="d" gradientUnits="userSpaceOnUse" x1="26.013" x2="26.013" xlink:href="#a" y1="4.4313" y2="123.33"/><circle cx="78" cy="112" fill="url(#b)" r="12"/><path d="m72.14 88.57c-2.3 0-4.12-1.94-4-4.23.29-5.21 1.14-9.5 2.55-12.88 1.77-4.25 5.28-8.92 10.52-14s8.56-8.7 9.96-10.85c2.15-3.27 3.22-6.81 3.22-10.63 0-5.04-1.25-8.89-3.75-11.55s-6.17-3.98-11-3.98c-4.62 0-8.34 1.3-11.17 3.9-2.11 1.95-3.44 4.41-3.97 7.39-.33 1.86-2.02 3.17-3.91 3.17h-11.67c-2.38 0-4.27-2.07-3.98-4.43.93-7.46 4.07-13.51 9.42-18.16 6.38-5.55 14.8-8.32 25.28-8.32 10.8 0 19.23 2.74 25.27 8.23 6.05 5.49 9.07 13.15 9.07 23 0 8.77-4.09 17.4-12.25 25.9l-9.77 9.62c-.1.1-.2.2-.29.31-2.89 3.37-4.61 8.01-5.16 13.92-.19 2.04-1.92 3.6-3.97 3.6h-10.4z" fill="url(#c)"/><g fill="#424242" opacity=".2"><path d="m78 103.01c4.96 0 9 4.04 9 9s-4.04 9-9 9-9-4.04-9-9c0-4.97 4.04-9 9-9m0-3c-6.63 0-12 5.37-12 12s5.37 12 12 12 12-5.37 12-12-5.38-12-12-12z"/><path d="m79.64 7c9.98 0 17.81 2.51 23.26 7.45 5.44 4.94 8.09 11.73 8.09 20.78 0 7.92-3.83 15.92-11.39 23.79l-9.74 9.59c-.16.16-.31.32-.46.49-3.29 3.84-5.27 9.08-5.87 15.59-.05.49-.48.88-.99.88h-10.4c-.37 0-.62-.2-.73-.31-.11-.12-.3-.37-.28-.75.27-4.84 1.05-8.84 2.32-11.89 1.61-3.85 4.92-8.23 9.84-13 5.45-5.29 8.85-9.01 10.37-11.36 2.47-3.76 3.72-7.88 3.72-12.27 0-5.81-1.54-10.39-4.56-13.61-3.08-3.27-7.51-4.93-13.19-4.93-5.38 0-9.82 1.58-13.2 4.69-2.6 2.39-4.24 5.44-4.89 9.07-.07.39-.49.7-.96.7h-11.66c-.4 0-.66-.22-.77-.35-.13-.14-.27-.38-.23-.71.85-6.76 3.6-12.08 8.41-16.27 5.78-5.03 13.62-7.58 23.31-7.58m0-3c-10.48 0-18.9 2.77-25.27 8.31-5.35 4.65-8.49 10.71-9.42 18.16-.3 2.36 1.6 4.43 3.98 4.43h11.67c1.89 0 3.58-1.31 3.91-3.17.53-2.98 1.85-5.44 3.97-7.39 2.82-2.6 6.54-3.9 11.17-3.9 4.84 0 8.5 1.33 11 3.98 2.5 2.66 3.75 6.51 3.75 11.55 0 3.81-1.07 7.35-3.22 10.63-1.4 2.15-4.72 5.77-9.96 10.85s-8.75 9.75-10.52 14c-1.41 3.38-2.26 7.67-2.55 12.88-.13 2.29 1.7 4.23 4 4.23h10.4c2.05 0 3.78-1.56 3.97-3.6.55-5.9 2.27-10.54 5.16-13.92.09-.11.19-.21.29-.31l9.77-9.62c8.17-8.5 12.25-17.13 12.25-25.9 0-9.85-3.02-17.51-9.07-23-6.05-5.47-14.48-8.21-25.28-8.21z"/></g><g fill="url(#d)"><ellipse cx="26.01" cy="112" rx="12" ry="11.99"/><path d="m32.15 92.01h-12.27c-2.19 0-3.98-1.74-4.03-3.91l-1.83-79.97c-.05-2.24 1.77-4.09 4.03-4.09h15.93c2.26 0 4.08 1.85 4.03 4.09l-1.83 79.97c-.05 2.17-1.84 3.91-4.03 3.91z"/></g><g fill="#424242" opacity=".2"><path d="m26.01 103c4.96 0 9 4.03 9 8.99s-4.04 8.99-9 8.99-9-4.03-9-8.99 4.04-8.99 9-8.99m0-2.99c-6.63 0-12 5.37-12 11.99s5.37 11.99 12 11.99 12-5.37 12-11.99c0-6.63-5.37-11.99-12-11.99z"/><path d="m33.98 7.04c.39 0 .63.2.75.31.13.14.29.37.28.71l-1.83 79.97c-.01.54-.47.98-1.03.98h-12.27c-.56 0-1.02-.44-1.03-.98l-1.83-79.97c-.01-.34.15-.57.28-.71.11-.12.36-.31.75-.31zm0-3h-15.93c-2.26 0-4.08 1.85-4.03 4.09l1.83 79.97c.05 2.17 1.84 3.91 4.03 3.91h12.27c2.19 0 3.98-1.74 4.03-3.91l1.83-79.97c.05-2.24-1.77-4.09-4.03-4.09z"/></g></svg>
called an “interrobang,”
The exclamation question mark emoji shows two punctation marks right next to each other: an exclamation point and a question mark. It is also called an “interrobang,” and can be used to truly convey a feeling of dramatic confusion or shock. It is a bold emoji that can add flavor to any text about a bizarre situation.
Exclamation question mark
This emoji can be used to express curiosity, confusion, or interest. ‼️ double exclamation mark. The double exclamation mark emoji is two bold, red exclamation ...
to [⁉️ Exclamation question mark emoji]
for - interrobang - inquiry
(https://hypothes.is/a/FJm2POBXEe66DBuMpVlFMA)

google.search - utf8icon red exclamation question mark
from - google.search interrobang
The Unison programming language doesn’t store code in files, but in a database. What is that like?

personal.archived - from: https://itnext.io/writing-code-without-plain-text-files-cb8f1ed2c0ad - by: gyuri
Alkotói portrék a magyar irodalomból


"maker, author, poet," variant of poiētēs, from poein, poiein "to make, create, compose."
"maker, author, poet," variant of poiētēs, from poein, poiein "to make, create, compose."
"one endowed with the gift and power of imaginative invention and creation, attended by corresponding eloquence of expression, commonly but not necessarily in a metrical form"
gift and power of imaginative invention
poet (n.)
etymology
http://127.0.0.1:48084/ipfs/QmcUXsXGQSYE5ehp5NhxoxQjihTdTP4vpkJ6NVzppyhhED
https://hypothes.is/a/YK4WKN7jEe6uN_vQ6ORS4A
https://stackoverflow.com/questions/11753485/set-img-src-to-dynamic-svg-element
TUDOD, HOGY NINCS BOCSÁNAT
Think different

Apple’s design displays text from its 1997–2002 Think Different ad campaign
Here’s to the crazy ones. The misfits. The rebels. The troublemakers. The round pegs in the square holes.The ones who see things differently. They’re not fond of rules. And they have no respect for the status quo. You can quote them, disagree with them, glorify or vilify them. About the only thing you can’t do is…

Rightwards Arrow Over Leftwards Arrow ⇄
for - translate
A lélek mértéke a nosztalgiák és a lelkifurdalások, a tiszta vágyak és a tiszta megbánások.
The soul's measure are the nostalgies and remorse, the pure desires and true regrets.
Hiszen igaz: a művész azért művész, hogy az illúziót valóra váltsa, a költő azért költő, hogy a lehetetlent letesse.
Since true:
the artist is artist to realise the illusion.
the poet is poet, to let the impossible be
AZ ELÉGEDETLENSÉG KÖNYVÉBŐL
src: https://oszkdk.oszk.hu/storage/00/00/75/99/dd/1/OsvatE_Azelegedetlenseg_9789633645024_PDF.pdf
AZ ELEGEDETLENSEG KONYVEBOL GONDOLATOK, AFORIZMAK
x
WHY GATHERING OF TRIBES
x
The proxy server must not be placed in a network where sensitive resources are accessible via an intranet
must not
others may use your server to hide actual IP from the destination server.
hide originating ip
Adding a security section in the documentation? #152
for Cors Anywhere
PSA: Public demo server (cors-anywhere.herokuapp.com) will be very limited by January 2021, 31st #301
restricted by opt int
How to Execute After Page Load in JavaScript ?
called after entire page loaded
window.onload = function() {
...
};
How to Execute After Page Load in JavaScript - GeeksforGeeks
💖 simple emoji support for node.js projects
```import * as emoji from 'node-emoji'
emoji.emojify('I :heart: :coffee:!') // 'I ❤️ ☕️!'
emoji.find('heart') // { emoji: '❤', name: 'heart' } emoji.find('❤️') // { emoji: '❤', name: 'heart' }
emoji.get('unicorn') // 🦄 emoji.get(':unicorn:') // 🦄
emoji.has(':pizza:') // true emoji.has('🍕') // true emoji.has('unknown') // false
emoji.random() // { name: 'house', emoji: '🏠' }
emoji.replace('I ❤️ coffee!', 'love', { preserveSpaces: true }) // 'I love coffee!'
emoji.search(':uni:') // [ { emoji: '🦄', name: 'unicorn' }, ... ]
emoji.strip('I ❤️ coffee!') // 'I coffee!'
emoji.unemojify('🍕 for 💃') // ':pizza: for :dancer:'
emoji.which('🦄') // 'unicorn'
```
Nov 20, 2023 — Friendly emoji lookups and parsing utilities for Node.js. 💖. Latest version: 2.1.3, last published: 3 months ago. Start using node-emoji in ...(function(){var eid='z9PoV';var a=google.c.mcar;var b=a?0:Date.now(),c=document.getElementById(eid);google.c.mfrvt(b,c);google.c.ub();c&&!a&&google.c.maft(b,c);})();
Package
emoji.for - node.package
A package (parcel), as contains items ordered online. Depicted at various angles as a light-brown, cardboard box, with a shipping label and its top taped shut.
Commonly used for content concerning shipping, delivery, and moving as well as for boxes more generally.
We can start by displaying title and favicon. Because of CORS limitation on frontend we'll need a backend server. An easy way is to use CORS Anywhere. Its demo ...
Okay-ish way get title and fav…
to - Rob--W/cors-anywhere
google.search - get favicon browser only
Okay-ish way get title and favicon on the browser
CORS Anywhere.
How can i get the favicon url from a website url using flutter Ask Question
google.search - get favicon for site
Liminal ConsultingDeepening Visionary Service
MoreBeautifulWorld
an MVP for ProjectLiminality in the form of an Obsidian plugin

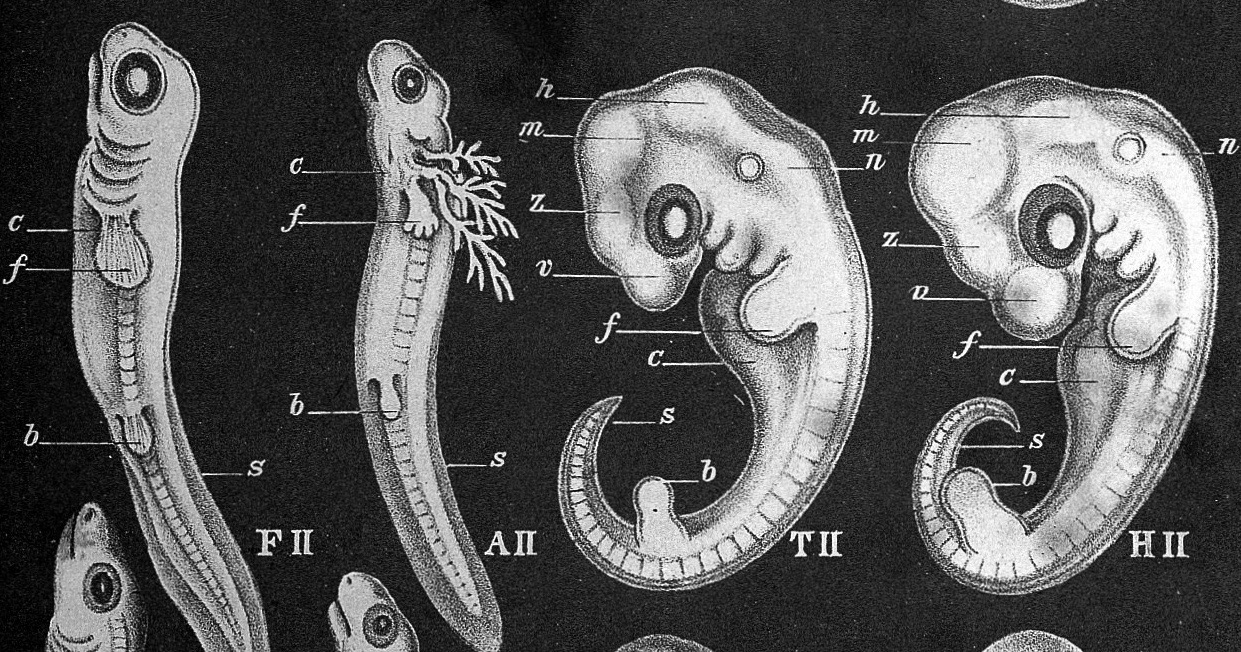
it’s the organism that controls the genome!

Oct 6, 2021 — This phrase suggests that an organism's development will take it through each of the adult stages of its evolutionary history, or its phylogeny.
New York Botanical Gardenhttps://www.nybg.org › blogs › science-talk › 2017/02New York Botanical Gardenhttps://www.nybg.org › blogs › science-talk › 2017/02

“ontogeny recapitulates phylogeny”
recapitulation
google.search: philogenetic recapitulation
your content will be publicly accessible, and may be used and re-shared by others on Linktree and across the internet.
will be reshared accross the internet
import { name as circleName } from "https://example.com/shapes/circle.js";
import https
Load optimized npm packages with no install and no build tools.
for - htmx - browser native indy applets
<svg class="hero-logo mt6 mb2 svelte-194ivpm" xmlns="http://www.w3.org/2000/svg" viewBox="0 0 111 24"><title>Skypack </title><path fill="currentColor" d="M38.63 8.71v.36H35.8v-.36c0-1.74-1.09-2.43-2.82-2.43-1.74 0-2.53.69-2.53 1.81s.8 1.67 2.68 2.06l.51.11c3.26.69 5.32 1.81 5.32 4.6 0 2.79-2.24 4.71-5.76 4.71-3.51 0-6.01-1.95-6.01-5.25v-.22h2.82v.22c0 1.81 1.19 2.75 3.15 2.75 1.95 0 2.93-.87 2.93-2.1 0-1.27-1.01-1.7-2.97-2.14l-.51-.11c-3.19-.69-5-1.77-5-4.53 0-2.75 2.1-4.45 5.36-4.45 3.27.01 5.66 1.68 5.66 4.97zM46.45 12.84l5 6.44h-3.37L44.5 14.5l-1.48 1.27v3.51h-2.79V4.04h2.75v8.4l4.49-3.95h4.05l-5.07 4.35z"></path><path fill="currentColor" d="M63.06 8.49l-5.9 15.13h-2.97l1.52-3.66-4.49-11.47h2.97l2.86 7.78h.22l2.86-7.78h2.93zM63.89 8.49h2.68v1.45h.22c.65-.94 1.7-1.77 3.58-1.77 2.57 0 4.89 2.17 4.89 5.68s-2.32 5.68-4.89 5.68c-1.88 0-2.93-.83-3.51-1.7h-.22v5.76h-2.75V8.49zm8.62 5.4c0-2.14-1.27-3.37-2.97-3.37-1.7 0-2.97 1.23-2.97 3.37s1.27 3.37 2.97 3.37c1.7-.01 2.97-1.24 2.97-3.37zM81.27 8.2c2.82 0 4.6 1.45 4.6 4.16v6.95h-2.61v-1.27h-.33c-.18.47-.9 1.56-2.9 1.56-2.21 0-3.95-1.23-3.95-3.48 0-2.21 1.74-3.37 4.16-3.37h2.97v-.62c0-1.01-.62-1.77-1.99-1.77-1.38 0-2.03.72-2.21 1.7l-2.53-.83C77 9.61 78.44 8.2 81.27 8.2zm-.69 9.16c1.52 0 2.61-.94 2.61-2.39v-.18h-2.75c-1.01 0-1.63.51-1.63 1.27s.61 1.3 1.77 1.3zM92.71 8.2c3 0 4.81 1.77 5.32 4.16l-2.64.58c-.14-1.3-.94-2.35-2.61-2.35s-2.9 1.23-2.9 3.29c0 2.1 1.27 3.29 2.9 3.29 1.67 0 2.46-.98 2.68-2.35l2.64.62c-.62 2.35-2.35 4.13-5.39 4.13-3.15 0-5.61-2.35-5.61-5.68 0-3.37 2.46-5.69 5.61-5.69zM105.56 12.84l5 6.44h-3.37l-3.62-4.78-1.48 1.27v3.51h-2.75V4.04h2.75v8.4l4.49-3.95h4.05l-5.07 4.35zM16.06 11.5l-4.09-2.04 4.09-2.04c.19-.1.31-.29.31-.5 0-.21-.12-.41-.31-.5l-5.09-2.54a.55.55 0 00-.5 0L5.39 6.42c-.19.09-.31.28-.31.5V12c0 .19.1.37.26.48.02.01.03.02.05.02l4.09 2.04-4.09 2.04c-.19.1-.31.29-.31.5 0 .21.12.41.31.5l5.09 2.54c.08.04.17.06.25.06.08 0 .17-.02.25-.06l5.09-2.54c.19-.1.31-.29.31-.5V12a.596.596 0 00-.32-.5zm-5.33-6.51l3.84 1.92-3.84 1.92-3.84-1.91 3.84-1.93zM6.2 7.81l3.28 1.64L6.2 11.1V7.81zM6.89 12l3.84-1.92L14.56 12l-3.84 1.92L6.89 12zm3.28 3.44v3.28l-3.28-1.64 3.28-1.64zm5.09 1.31l-3.97 1.99V14.9l3.97-1.99v3.84z"></path><path fill="currentColor" d="M10.73 24c-.09 0-.17-.02-.25-.06L.31 18.86a.567.567 0 01-.31-.5V5.65c0-.21.12-.41.31-.5L10.48.06a.55.55 0 01.5 0l10.17 5.09c.19.1.31.29.31.5v12.71c0 .21-.12.41-.31.5l-10.17 5.09c-.09.03-.17.05-.25.05zm-9.62-5.98l9.61 4.81 9.61-4.81V6l-9.61-4.81L1.11 6v12.02z"></path></svg>
🅐 Negative Circled Latin Capital Letter A
🅐
emoji.for - project liminality
tempt us to grant them absolute power with utopian promises of superhuman autonomy and dystopian threats of subhuman servitude
promises
Human, ForeverThe Digital Politics of Spiritual War

Man Technologist
emoji 👨💻 =
for - tech - tech.mix - Indy0.Net - dream.code - dreaming in code
Thought Balloon
emoji.for - thought - dreaming - dreaming in code
A large cloud-like shape more commonly known as a thought bubble.
Used to represent thinking, or thoughts, and commonly used in comics to display the thoughts of a drawn character. May also be used to represent a dream, or daydream.
Nut and Bolt
🔩
for - object
A metal bolt with a nut threaded around it, as by a wrench. Often positioned at a 45° angle, the head of the bolt at the upper left. Commonly used for various content concerning tools, building, and construction. May also be used for other hardware, including screws.
Construction
🚧 for - development - dev - emoji - work - make
Heart Exclamation
emoji.for - Clue 💡❣️
A decorative exclamation mark, where a heart forms the top part of the symbol, and a circle the lower part. Similar to the way to the man in business suit levitating also creates a similar shape.
Standalone test spies, stubs and mocks for JavaScript. Works with any unit testing framework. Get Started

Become a sponsor
