just tabbing through the different columns of the spreadsheet.
tabbing through fields in a wizard?

just tabbing through the different columns of the spreadsheet.
tabbing through fields in a wizard?

If the process is forked depending on users’ inputs and the forking is transparent to the users, then they don’t need to bother with the path that does not apply to them.
forking is transparent
Wizards Show Less Information on the Page
dynamic page
Dynamic Form or Wizard?
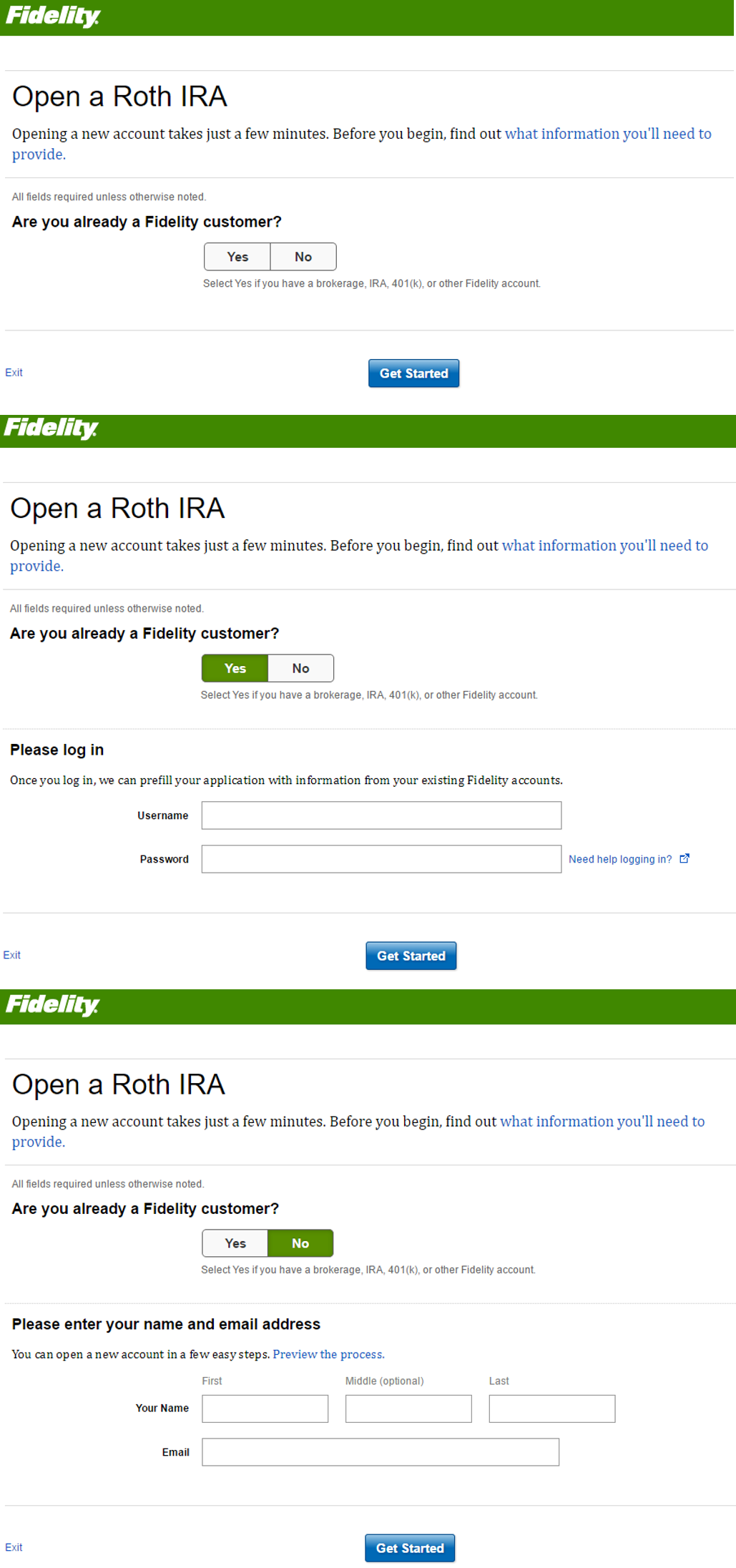
Turbotax: The form (left) is a close replica of the paper tax form, but can be filled in digitally, while the wizard (right) takes users step by step through the process of filling taxes.
https://media.nngroup.com/media/editor/2017/04/18/turbotax-combined.png
from - search : hci qizard pattern
Layman Pascal introduced his Metaphysics of Adjacency in two threads on the IPS forum
PBS-award-winning Metaphysics of Adjacency
metaphysics of adjacency
GENERATIVE (EN)CLOSURES, BUBBLES,AND MAGIC CIRCLES:A Chat about Integral Postmetaphysical Spiritualityand Religion
-4: Metaphysics of Adjacency
Principles of Adjacency (draft)
An ancient universe of “things” has for centuries been losing ground to flowing visions of energy, information & interpretation. Flow is activity. Activity requires Time & Space together. Activity appears AS locations and durations. This is dynamic adjacency. It is the connective or disconnective “room” combined with synchronous or asynchronous durations of occurence precisely in and as this “room”.
universer of things flowing vision of energy
Click to Edit
offer inline editing
The click to edit pattern provides a way to offer inline editing of all or part of a record without a page refresh.
This pattern starts with a UI that shows the details of a contact. The div has a button that will get the editing UI for the contact from /contact/1/edit)
// What We Need for bootstrapping Indy HyperMedia Plexuses,
associative complexes, as - PLEX : - the MEMEpleX so that We May Augment our Thinking - unenclosable evergreen apPLEXes,, HTMxPLEXes, - Autnonomous InterPersonal communicaPLEXes

not components or anything like that

rather they're just sort of examples like copy and pasteable examples or you know like just to give you some ideas of what what can we accomplish with these tools and so here we have a div that's targeting itself
generalized hypermedia maybe um what uh what can we accomplish with
what can we accomplish with it
-2: https://hyp.is/xW4zBi_IEe6RDCNxbiXyxw/htmx.org/examples/


roughly I'd say there's about a dozen or so core attributes to the library

can check out htmx.org reference if you want to see them all as well as you know all the events and so forth that htmx triggers I'm pretty rich environment but not the the core of it is very small at the end of the day you can probably get your head around htmx I'd say in a day or so if you have some HTML slash web development experience so that's great it's pretty small but the question is okay we've generalized hypermedia maybe um what uh what can we accomplish with
HX select

allows you to select a chunk from the return earned HTML so if you only want some you know bit from within a larger document we can select just that out to be swapped into the Dom
HX include

allows you to include inputs by default if there's a form wrapping around an element it'll include it but HX include lets you do that a little bit more dynamically
HX indicator

is an attribute that allows you to show an indicator when a request is in flight so that users add feedback to Something's occurring that's often very good to do from usability standpoint
a few more attributes um so for example HX swap

**swap ** how the new content is swapped in
would allow you if you wanted to use an HX swap attribute you can specify exactly how the new content is swapped in do you want it to be the inner HTML do you want to Target the outer HTML do you want to append it and so forth HX indicator is an attribute that allows you to show an indicator when a request is in flight so that users add feedback to Something's occurring that's often very good to do from usability standpoint HX include allows you to include inputs by default if there's a form wrapping around an element it'll include it but HX include lets you do that a little bit more dynamically HX select allows you to select a chunk from the return earned HTML so if you only want some you know bit from within a larger document we can select just that out to be swapped into the Dom um so roughly I'd say there's about a dozen or so core attributes to the library you can check out htmx.org reference if you want to see them all
HX Target it has a CSS selector
CSS selector
allow you to Target whatever thing you want on the page using a CSS selector
and so this says it's not essentially issue a put requests to like when a click occurs and then whatever HTML comes back I want you to put that into the thing with the ID output which is this output element down below so it's going to take the HTML that comes back from that and stick it into the inner HTML of this output
that's 00:24:46 what turns this into a hyper media control
turn into a hypermedia control
.png)
tries to be 00:24:11 attribute driven just like an anchor has an ahref a hypermedia reference
the four potential these are the four generalizations of hdmax make

HTMx: Building modern web applications without JS (with Carson Gross)

Sortable In this example we show how to integrate the Sortable javascript library with htmx. To begin we initialize the .sortable class with the Sortable javascript library:
best thing since slice bread!
UI Examples Below are a set of UX patterns implemented in htmx with minimal HTML and styling. You can copy and paste them and then adjust them for your needs.
from: https://hyp.is/5wzE2C_HEe6kHedsL7O_1A/docdrop.org/video/Jodkvyo5DbA/
don't have to distract myself with remembering this goes in this folder and this one goes 00:25:57 there
Do not have files write whatever comes to mind where u r
want to be able to work at the speed that you can think I want to even be able to and we'll show sample in a minute I want to be able to just put put controllers that call services that call mediators I want to put it in 00:25:45 the same file
To be able to work at the speed of thought
Software development requires networked tools for thought conversations
Not same file but self explicating intertwingled high resolution intent meaningfully addressable intentionsl info infra structures storage communication and compute syructures composed freely in a universal medium of effective ellaboration
explaining why are we doing things understanding trying to explain the rationale and always give 00:24:33 the other developers space to challenge what what we're doing
keep very closely related code together
Just create the associations be articulate about the why the intent the how connecting whats needed in meaningful articulate way. Do not be forced to create textusl order let the connections do the work
there's a balance here we do these prescriptive approaches so developers don't have to think
Prescriptive
Don't have to think
creating a decision tree of when does this not work
X
explain the why why
Yes
Why first then how to let the IT right at last in
You can only get it right first time
If u get the IT right
Which emerges eventually if you get your symmathetic processes right through engaged aytention care and the power of imaginative thought through criticsl elsaboration. Exploration to arrive where we have started but have our ontent articulated do ee can see it for the first time in action
Vertical Slices in practice

youtube - CQRS is simpler then u think ...

Last week I wrote a blog post ostensibly about Marten’s compiled query feature that also included this code sample that I adapted from Oskar’s excellent post on vertical slices:
to : vertifcal slices
The Shade Tree Developer Still having fun writing code
About A front-controller style MVC framework for .NET


FubuMVC was conceived as an addon to the nascent ASP.Net MVC framework during a large web application project in 2008-9
2008
FubuMVC

way back in 2015 as an intended reboot of an even older project named FubuMVC / FubuTransportation that was a combination web api framework and asynchronous message bus
web api framework
asynchronous message bus
Wolverine is a Next Generation .NET Mediator and Message Bus.


WolverineNext Generation .NET Mediator and Message BusA batteries included modern and opinionated library!
modern and opinionated

Next generation application development framework for .Net
next gen applicaiton framework
Asynchronous Processing
Use Jasper as an - in memory command bus - to easily leverage - asynchronous and - parallel processing within a single process
Jasper has a unique approach to command processing
Messaging
Everything you need for - robust messaging solutions between services - including support for many popular - transports, - message failure policies, and - persistent inbox/outbox messaging
JasperNext Generation Command and Message Bus for .NET

Content addressability means
that the Network is the Database, and in fact is the InterNet of Autonomous Ambient InterPersonal Intentional Software (as a conversation: Symmathesy Mutual Learning) nora bateson @jessitron
https://hypothes.is/a/LfiLpprEEeykWV8a3Q47lg
not a question of Semantics
it is a matter of communicating Intent. Android popularized the term.Charles Simonyi created Intentional Software. Bought by Microsoft and folded.
I'm still only collating, although been following the rise and fall of Intentional software for the past decade.
Not only as a fellow Hungarian, but someone who had been thinking about the same problem for the past 40 years!
I thought too that language-oriented programming is the way. 20 years ago I realised that
software is a conversation (mainly about intents, purposes and means, but lately I learned that it is symmathesy mutual learning.
I also believe, inspired by Haugland's Mind Design that

That is the case, as I learning from experiments.
https://indylab-2022.fission.app/hyp?intentional&user=gyuri https://indylab-2022.fission.app/hyp?symmathesy&user=gyuri
APIs are like waiters - or are they?
Nov 24, 2022 — You, in this analogy, are the “client”; the person you talk to is quite ... the rise and fall of Intentional software for the past decade
alan morrison - Dcaf transformation & kg adoption 2022
we need to deliver meaningful, purposeful, actionable data to the point of ... Ambient InterPersonal Intentional Software (as a conversation: Symmathesy ..
search : software conversation intentional symmathesy
from - search : hci qizard pattern
testing before development has even begun
test before development
What is Wizard of Oz testing and how can it be used?
search - hci wizard pattern
In hypertext writing, the narrative is emergent and the ideas are associative. It is like a book where the pages rearrange themselves for you based on your current curiosity each time you revisit.
!- big idea : documents become virtual with MindGraph

an emerging, situated, Meta Knowledge Graph.
span an emergent, situated,Personal Meta Virtual HyperDocument Space where trailmarks are but thought vectors in concept space and intent marks forming associative complex 'shapes; as span are info-structure-communication-computational Spaces or Autmented Transitions Network generating Morphic Presentation complexes Lively Hyperdocuments (Lively as in ively Kernel)

IPFS Lite IPFS Lite node with modern UI to support standard use cases of IPFS
Cross-platform IPFS Lite: JS, Android, iOS, and gRPC

❋ (HEAVY EIGHT TEARDROP-SPOKED PROPELLER ASTERISK) utf-8 character icon
❋
⊛ CIRCLED ASTERISK OPERATOR
for IndyLab
❉ BALLOON-SPOKED ASTERISK
for - IndyHub
❉ (BALLOON-SPOKED ASTERISK) utf-8 character icon
for : concept, plex
indyHub
Search results for "asterisk"
![]()
4 - PLeXplore - PlexScape
from - https://twitter.com/imcalshort/status/1681603218311184384 - https://hyp.is/sjdSQCnxEe6VzmcV8j5Nwg/twitter.com/imcalshort/status/1681603218311184384
Stop using ChatGPT, Jasper or any generic AI to write articles.
Cal @imcalshort Stop using ChatGPT, Jasper or any generic AI to write articles.
I built an AI editor that trains itself on your published articles.
The result? An immediate upgrade over these generic tools.
Don't believe me? Try it for free...
I think it's very 00:07:49 very dangerous because it doesn't understand us and AI at present is mostly digesting the products of human culture 00:08:00 everything we've produced over thousands of years it eats all of these cultural products digests it and starts producing its own new stuff
AI doers not understand us
the earliest human-computer 00:05:45 interaction are close to the earliest you might say was was turning the crank
earliest comuter human interation babbage turning the crank
try to intersperse some references to show that this progression of concerns that has 00:04:31 led to looking at how the human fits into the computer human interaction
HCI
the Association for Computing Machinery it's the biggest computer professional organization and it seems like it's for the machines not for us
Association of Computing Machinery for the Marchines not for US
CH I always thought it was HCI I thought it was human
HCI Human Cmputer Interaction
I thought it was Human first
Terry Winograd: Filling in the "H" in CHI
failing to acknowledge the complexity of reality
failing to "honor the complexity of the situtation"
https://hyp.is/r908WijSEe6h7X9ocYCu3g/the-santiago-boys.com/context
Fernando Flores and Terry Winograd released their paradigm-shifting text, "Understanding Computers and Cognition."
This work was a direct challenge - to many of the existing paradigms in artificial intelligence.
They contested the idea that - reality could be fully represented through a series of rules and descriptions, - then formalized into a computer system - that could act upon that reality.
They asserted that such projects were guided by a false pursuit of - omniscience, - omnipotence, and - control,
failing to acknowledge - the complexity of reality.
// or as Terence McKenna put it: - "honouring the complexity of the situation"
from 
honor the complexity of the situation.
honor the complexity of the situation
instead of
"failing to acknowledge the complexity of reality." https://hyp.is/r908WijSEe6h7X9ocYCu3g/the-santiago-boys.com/context
Current computing embodiesan epistemology
Current computing embodies an epistemology which - claims to know more than we can know, and - it denies what we do know but cannot explicitly justify.
It is wedded to - a hierarchy based Cosmology for the Computer Universe, that is - fixated on centralised control; - with a Transhumanist promised land at the end of history
replacing any - belief in human potential.
This approach not only - damages the freedom of the individual to make new discoveries, it also - generates a spiritual (or as Polanyi puts it - moral inversion in our understanding of - what it is to be a human being.
The current hype around AI promotes the idea that - the humanmind can be reduced to processes that can be replicated and run - in ways that are akin to advanced deep learning algorithms in the cloud.
to situate Concepts like next to or near or almost or approximately or sort of as being ontologically fundamental more fundamental than the apparent options 00:09:05 that they mediate between and this has
metaphors we live by sort of ontologicaly fundamental
the affordances provided by intercontextual proximity to be a pluralist or a post pluralist or even a non-dualist you have to have this
spirituality as something you enact rather than something you have to believe
enacted not believed
ot bound by any singular overriding self-consistent sense of a totalized one
self consistent toralized
have in common is an appreciation of incompleteness as a coherent structural feature of the relationship between apparent Alternatives and the use of that to rebuild philosophy and Society
rebuid
HEGEL'S SCIENCE OF LOGIC: Formative Moments 1801-1807
science of logic
How to make the world-wide information superhighway work for you...
Forget the Cloud... Go Direct!
SSuite Grabby Screen RecorderDiscover our latest screen, webcam, and microphone recorder called Grabby...

Pro It is an online and offline office suite that is also a Progressive Web Application
Not cloud-based and completely server-less (it can be run online or offline).
x
SSuite Office Online Review
What is the best alternative to Cryptpad?
Deep Cache
with IPFS
where documents as permanent interpersonal emergent networked pages form a global giant single documents eventually connecting everything
knowledge grails
everyone can re-use all contents
reuse remix
make content available with certain permissions; then distribute and maintain documents simply as lists of these contents
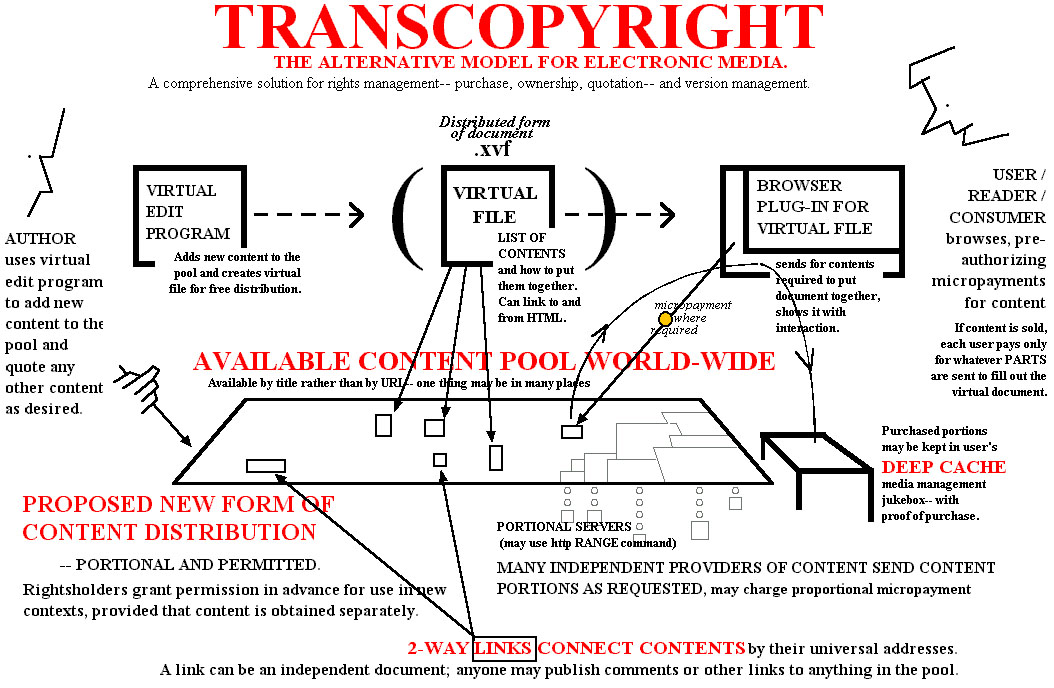
TRANSCOPYRIGHT FOR THE WEB A clean legal and technical system for re-using on-line content
reshape for IndyWeb
The Xanadu copyright model-- now called "transcopyright"-- takes a little more explaining.
transcopyright
VLIT, Virtual Literary Format
Virtual Literary format
THE NEW XANADU® STRUCTURE FOR THE WEB
DEEP HYPERTEXT: THE XANADU® MODEL
deep hypertext
the Xanadu model
promises of faceted search in discovering salient patterns of meaning that connect in the growing body of conversations and literature about transition/emergence into a post-pandemic future
that ate continuous, permanent, evergreen, built from trust for trust without being synchronous
scaling reach emergent self rating
What Went Wrong? The Backstory
// my thought What Korzibski calls essentialism
the constructive subliminal contsraining influence of languages with the copula
Context Changes EverythingHow Constraints Create CoherenceAlicia Juarrero


Context Changes EverythingDownloaded from http://direct.mit.edu/books/book-pdf/2133506/book_9780262374774.pdf by guest on 13 July 2023

Why Pull Requests Are A BAD IDEA

Open source toolkit for digital spaces Customisable, Decentralised, Self-governed. Welcome to the digital space of the future.
space
FOSDEM 2023: Whom Do You Trust? - Privacy and Collaboration in CryptPad
![]()

intended way.
text- search : inten
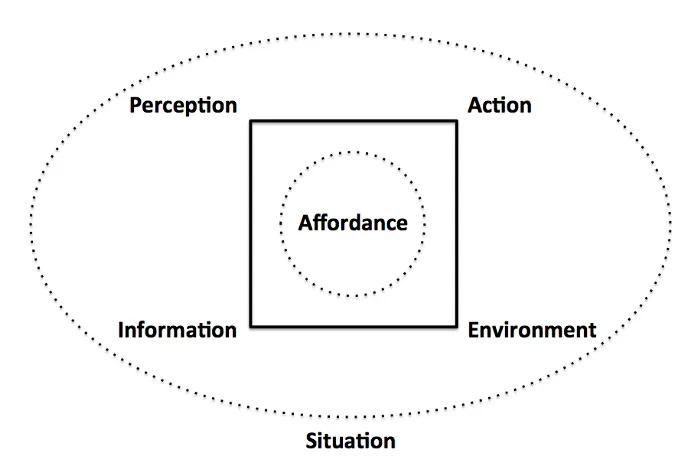
These obvious properties - prompt users to use - the affordance
in an intended way. -
An affordance is, in essence
An affordance is, in essence, - an action possibility - in the relation between - user and an object. - that determine just - how the object could possibly be used
in terns of intents -
🔎 (RIGHT-POINTING MAGNIFYING GLASS) utf-8 character icon
🔎
🔍 (LEFT-POINTING MAGNIFYING GLASS) utf-8 character icon
🔍
search : meaning affordances

Lifesystem: The Notion of Affordance Analysis | by Oliver Ding | CALL4 | Medium
aha


Lifesystem: The Notion of Affordance Analysis

CryptPad Documentation
This means we get a two-way conversation flowing between our web locations
"locations" should be people doing it for themesleves
ReImagining the Web as the : People-Centered Internet
"An Interment That works For People"
bulltby people, for the people, literally "of the people"
a web that is woven using un-enclose-able carriers
so the human autonomy and dignity is not just an alienable birth right but is guaranteed by design/constitutions

the mono-directional link
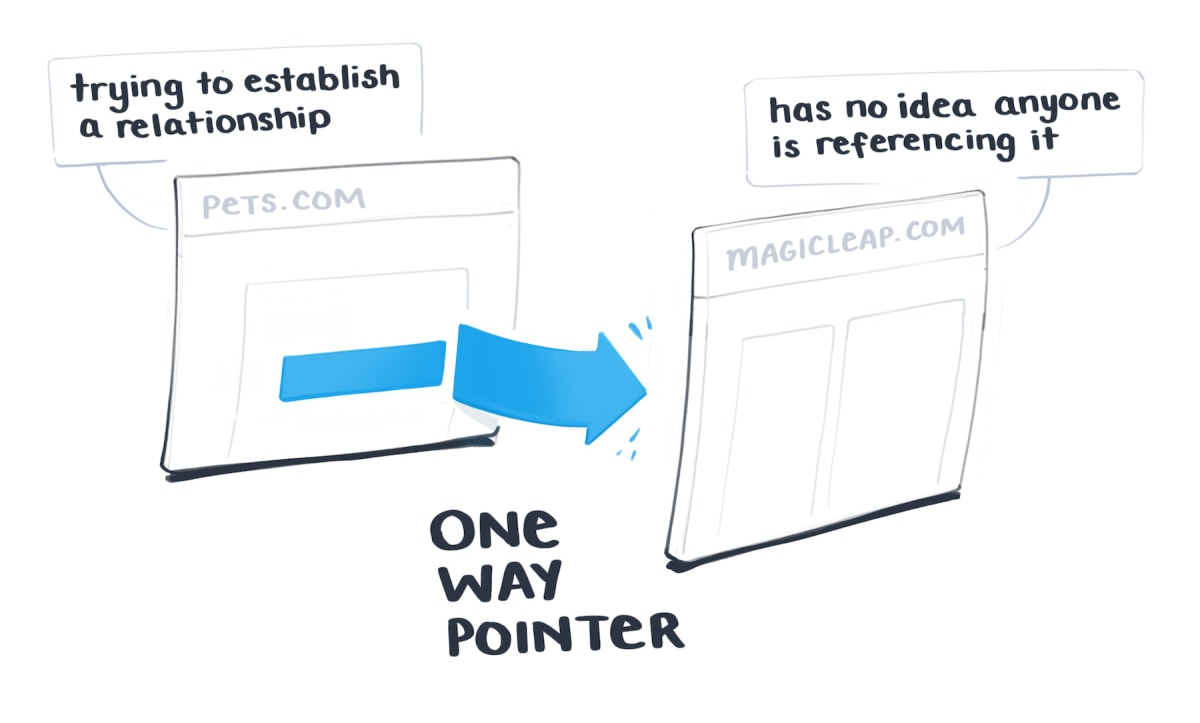
the principle of "Parallel Documents, Visibly Linked"
the principle of "Parallel Documents, Visibly Linked" – - the proposed interface presented documents side-by-side,and included features like - version control and - Bi-Directional Links.
Personal ways of knowledge acquisition
Personal ways of knowledge acquisition and its cooperatively manageable organization represent meta-information concerning the problem situation that determines the conceptual structure of the problem space. Representation of the search for information and its conceptual organization provide keys to problem definition and consequently to its solution. We reconsider concept organization and visual knowledge representation tools that augment human problem solving. By “augmented knowledge architectures” we refer to Douglas C. Engelbart’s (1962) conceptual framework for augmenting human intellect. Reconsidering his vision we argue, that in order to realize the potential of human-computer interactions for building augmented knowledge architectures we need to develop platforms for cooperative problem solvers along the lines of a ‘Wikipedia of Concepts’. Analyzing next generation techniques such as Google’s Knowledge Graph and existing relational representations and visualizations of knowledge structures we make explicit proactive requirements for next generation platforms, called “Conceptipedia”, in the spirit of Engelbart’s original approach
Computer enhanced technology gives us
Computer enhanced technology gives us - access to collective knowledge that - needs to be - contextualized, - personalized, and - reorganized.
This : knowledge work is a major task for - next generation learners and - knowledge workers
for whom - searching, - gathering, - digesting, - producing, and - presenting information
makes sense - in personal problem solving contexts
you've written you've read stuff that was not written in the way you are seeking to read it
not written in a way that u r seeking to read it
best

so you are interfering with their reading process when you're writing I

About RetroShare is a Free and Open Source cross-platform, Friend-2-Friend and secure decentralised communication platform.
SSL would be overkill.
SSL would be overkill
The computer Arts imitate creation itself
@gyurilajos7220 1 minute ago (edited) Kay said at the end of his talk just before Engelbart was to give a talk: The Greeks held that the Arts imitate Life. The computer Arts imitate creation itself. https://twitter.com/search?q=arts%20imitate(from%3ATrailMarks%20OR%20from%3ATrailHub1)&src=typed_query&f=top
That is our responsibility: Dreaming awake at the end of times. Honoring the complexity of our situations
Reply
Alan Kay on stronger and weaker conceptions of computing--and life

source : https://www.youtube.com/clip/UgkxYXAyOGZUmPskB_N3GT2P2tenpwvMjaAQ

computer science is an oxymoron software engineering of an oxymoron
= computer science = software engineering - is a = pop culture - because = it - is - not - curious - about = the past - or = the future - only - curious about = establishing - it's - own = identity - xx - - is an = oximoron - - not : curious about the past
https://twitter.com/TrailMarks/status/1591137991158005762

Yonatan@founderYonzFollows you@getallspark http://lofi.software @HarvardHBS Previously worked as a dev at @LinkedIn @Qulacomm. Passionate about user-owned auth, storage, and personalization.Entrepreneuryonz.devJoined September 2009

= computer science = software engineering
https://lnkd.in/d85dMwDP https://docdrop.org/video/OcZSnLYguHU/#annotations:lIBaSmHrEe276gez4Ts2ng = computer science = software engineering is an OXYMORON
is a = pop culture because = it is - - not - curious about = the past or - = the future
only - curious about = - establishing - it's - own = identity - is an = oximoron
in real science like physics you would be thrown out if you did not know what Newton or Galileo did busy reinventing the flat tire
https://lnkd.in/d7PX57_n https://lnkd.in/dWwfwPq7
Stanford Seminar: I forgot, I invented hypertext - @TheTedNelson https://lnkd.in/dTCAZ4Tf via @YouTube Xanadu vision lives onSystems of indexingVirtual Documents with two way meaning/intentful links & transclusionassigning permanent high resolution to all trailmarked clues

Mere Simulacrity

she said in these apps I can see and do full WYSIWYG opera authoring and the web browser has all these modes and I 00:16:55 have to type through a keyhole and I have to wait to see whether what I did was ok and all these stuff and and why is that she asked me and I said well it's because the stuff you like was 00:17:09 invented in the 70s and the stuff you don't like was invented 20 years late
https://youtube.com/clip/UgkxRRX5VfyBdxG40LiDy0pe9qvQpPU93Vra

for : Broken Wheel
John Vervaeke@vervaeke_johnPsychology and Cognitive Science Professor | Integrating science and spirituality to solve the #MeaningCrisis

Structuring thoughts and actions into trails
TrailMarks goes universal - as HyperMarks
opens up the possibility for - blazing trails of actions weaving personal workflows
composing workflows - accross web services indyweb capabailities
describe in - intellectually manageable, - resusable, - extensible, - tinkerable form
integrates/articulates - info structures and - description of intents
can be interpreted to accompish the desired - info transfor mation and - present the result in a form
that not only is amenable to - morphic interaction - but is also a permanent record of a state of a broader space
Personal data
data concerning people is but people in disguise
design for Humans HX not UX
.jpg)
identity should be
dystopia of SSI identity should be - portable and - secure across the internet
as with hyperdocuments themselves
we need to go meta and virtual with identities
location independence of all capabilities combined with the interpersonal communication layer provided on the IndyWeb identities and peoples own emergent trust based social networks remains under personal control and share on terms that people control themselves
Human social networks are NOT transactional networks but networks build from trust for trust and deep collaboration
]real identity](https://hypothes.is/a/st49PMMLEe2IYWM0LNu6EQ)
need privacy and security
understand.

re-purpose pre-existing tools
IndyLab allows - based on location independence of IPFS - so that they can provide services for people - on their own(ed) devices, off line first - and allow them to create their own(ed) - autonomous workflows across pre-existing tools
withoutcompromising our focus
The prevailing internet architecture is not the answer
// IndyWeb is about Flipping the Web // Not enought to Shifft the paradigm - from centralized to decentralized (just to be decent) - need to Flip it completely
This presentation identifies and articulates in a clear way the same problems that we address with the IndyWeb
Problems seem to define their own solutions the annotations highlight the most important points of convergence
Memetic Activation Platform discussed here
from : - App-Centric / Prover centric
Tight coupling of - identity, - data, - user interface & app functionality - echoes EA Business Silos – era of Function Automation
self perma link with hypothesis annotation pdf viewer preloaded
source : https://www.hylo.com/groups/collaborative-technology-alliance/topics/general/post/59258
= Memetic activation Platform
= MAP
= Enterprise
[docdrop]

Founding Director, Artificial Intelligence Institute and Professor, Computer Science & Engineering

Knowledge Graphs Interest Group at the Alan Turing Institute This interest group will facilitate research and innovation in a critical area of data science and AI.
providing a free service does not havemuch running cost
One up on that. The cheapest service provision of all is the one you do not need to provide.
Custody of information and even communication and computation is the key to Autnomy
Google Sign In
ditched that, aor any other's like it.
Google account is required
IndyWeb, The Flipped web insits in no accojnt needed ever. Not even Just one Login, on the new Web services authenticate with you, then one links one's Virtual Identities on one owned device will all the others.
Google Drive
Inteded as a spring board for a srotrage provider independent solution, preferably Personal First Off line First.
IPFS Desktopm Fossil, Perkeep, Peergos Web3Storage, Pinata, Fission are the alternatives we areconsidering.
Trapped in their “walled gardens” users lack anend to end workflow.
workflows are important. Because "Knowledge Work" is in a sense all encompassing. If you are in IT, then 90% of all your work is Knowledge work. If you are in a business, the higher level you are the more all your work is essentiallly Knowledge work, knowledge of People mainly and your sector.
Business Idea
We see a gap in the market of knowledge management solutions which support personal knowledge work end to end. That is, from the first note you make on a topic of interest, through the detailed research and presentation of your findings and ideas, which create re-usable, re-purposable, reproducible, and re-enactable dynamic Research and Knowledge Objects, which together eventually constitute a self-organizing Lifelong Personal Digital Archive of all your work. It provides a place where you can keep and have the tools that help you to ‘bring to mind what you have in mind’. Our holistic solution fills the gap in personal knowledge management tools, and is not only available for desktops, but also for mobile devices
he power of semantic search, turning strings to things
semantic search (wince, wince)
In MindPlex (hyperdocument space spanned my hypermark compositions into shapes)
Plex Pages have composite names shapes plus
Thery are treated as indeces to high resolution meaningfully linked contexts
Not forrests of propositional trails but
releavant content snippets
as search results are bnut dynamic hyperdocuments they are amenabe to be treated as any other hyperdocfument, ie.e. highresolution annotated , associated in meaningful ways with any hisgh resolution relevant snippets etc
gap in the market
Yeh but is there a market in that Gap.
Now Roam Research created it. They paid the price what I was not prepared to do, In any case Woud have little chance without VC funding which is not the way I ever wanted it to go.
Now there is an awareness of it
From the word go the personal was envisaged to be interpersonal, and that required the kind of communication and storage and computation infrastructure that was not there.
t exploits its “soft” (non formal)semantic capabilities
non formal symmathetic capabilities
where everything is a conversation between oneself through time and with the Others
so is the Software needed to conduct therser conversations
meta-reflective meta-design capabilitie
see Inmdyweb Virtual Document Spaces are virtual in two sense of the world
MEMplEX spaces are Named Everything Networks, permanent Hypermedia powered by IPFS
so documents are not enclosures of complete and consistent information, but the meterailize for the reader as the attention of focus is shifted on reading/writing
where intertwingularity reigns supreme,
while at the same time avery document Plex Page is verifiably attributed to the creator, and even the access to it is controlled by the author, all participants maintain their own verifiable record of all the interaction information flows they engage in.
HyperDocuments are Virtual in the sense that The IndyPlex HyperDocument Kernel is a Virtual Machine for HyperDocuments, in this sense that HyperDocuments are Universal as UniversalMachines
(With this we go beyond turing Equivalence because these documents are created for Human comnsumption first, so their expressive power goes way byond what mahines can handle, as they require completeness and consitency) Not true for LISP as it is homoiconic, and the computational model allows incomplete descriptions )
but when it comes to human articulation the more we write the more incomplete our account becomes as each page introduces futher pages et
We can converge because there will be cycles,
but not turing rwuivbslenty vbirtyual machine can accommote the level of divergence an incompleteness with which the mind can be comfortable with, It is a fact of life that must be comfortable with the inknown even with unkonw unkown, while computational ystems are restricted to known unkonws
Intentional Trails in Pages are self-hosting articulation of info-strucure-communication-computation patterns and when fully elaborated can be used as software artifact
offers collaboration via Google Docs
With a complete round trip between personal knowledge works captured as HTML and Google Docs
Wtih the Indyweb collaboration between people is supported with the same way that the Individual is able to search explore, synthesize, annotate, comment on and revise past work in the process of creating new synthesis from this through time collaboration and conversations.
knowledge about Things of interest.
Instead of curating Knowledge of Interest
the emphasis is on articulation, discovery and organizing web resources for scaling synthesis and symmathesy mutual learning trails and associateve complexes constituting a MEMEpleX
a graph
graph is a very limiting concept and it is a concept fo Representation
whereas what we care about is presentation for human consumption which maximizes comprehension and articulation yet amenable to interpretative processes
assigned types and properties on the fly
it is not the notes that are assighe types and properties
but thanks to TrailMark Symmathetic In-Notation
Clues (structured tet/information interpersed with plain-text innotations and property defitintions
Clues are a comnbination of trails of Trail/Hypermarks and Targets, whcih themselves can be named Plex Pages with their own self-organizing info-structure structured with TrailMakrs Clues and Cluetrails
atomic notes
seemed a good idea at the time
today the basic unit is a MEMEpleX
associative complexes all laid out in a plan on a page using transclusion and dynamic zooming for reading and writing
Instead of two way linking between atomic notes
use high resolution meaningful bidirectional links the meaning/intent of the link is made explicit as a TrailMark with its onw meta level Space
WikiNizer™ Research
Networked Thinking/Learning tool
Roam Research like but local first, Personal First
making it interpersonal on the IndyWeb
It supports a connectivist learning mode
It supports a connectivist learning model and as a - “self-curating” semantic knowledge management tool
it can be used in - problem and project based learning to - explore resources and - conceptual relationships,
helping us to - define learning paths and workflows, or - design meta-level didactic object structures and activities.
It is a tool which helps us - track meaning construction in a - situated, - intent dependent and - dynamic manner.
It is a holistic solution which integrates - web research, - linked data, - annotation, - note-taking and knowledge organization - into a Lifelong Personal Digital Archive of - “born reproducible”, - ab initio - re-purposable, and - re-enactable, - Research Objects
Using Freebase as a
Using Freebase as a linked data source it - harvests and contextualizes semantically structured information, - empowering us to curate a private Knowledge Graph of Things, with a view also - to enhancing collaborative knowledge work.
Its users - integrate open web data within the - content driven graph architectures of their personal learning environments.
It enables us to - elaborate upon the emergent dynamic graphs which - articulate the typed connections that exist between ‘Things’ of interest, - facilitating the emergence of novel concepts in the - associated complexes of content which are organized into node based structures
visual Wiki-likeknowledge orgaNizer
WikiNizeR
physical style ofhuman augmentation
physical bionic augmentation
bionic, hardware-augmented future in which humans andmachines merge to form powerful new entities
merge with the machine## bionic augmentation
personal intelligence augmentation (IA)
degrading augmenting intellect to ontelligence
The Design of Artifacts for Augmenting Intellect
The title refers to Autmenting Intellect
Yet it talks about IA as Intelligence Augmentation
degraded and brought closer to Artificial Intelligence
not Symbioitic Human-Software Individual Intellect eternalized into a form that can be explored, angaged with and synthesized thorugh inter personal collabnoration
improving what Doug Called our Collective IQ
Not intelligencer but our capacity to to comprehend and engage and make intelligent choices togehter that makximize future choices and thrivabiity
goals - annote - my goal here is to highlight points of overlap and divergence from the one articulated in this paper and my current views as we are creating a lunch community of our own
AUGMENTING HUMAN INTELLECT: EXPERIMENTS, CONCEPTS, AND POSSIBILITIES.DC Engelbart - 1965 - apps.dtic.milEarly stages of research on augmenting human intellect are reported. An experimental system comprising a tapewriter tape-punching typewriter, a computer-programmed Translator, …
google scholar - search augmenting human intellect
a "learning community" as we are a "launch community."
OHS Launch Community

A HUMAN RIGHTS-BASEDAPPROACH TO DATALEAVING NO ONE BEHIND IN THE 2030AGENDA FOR SUSTAINABLE DEVELOPMENT


ENGAGE 2023 - NETSCOUT Technology & User SummitNetscouthttps://www.netscout.com › engageNetscouthttps://www.netscout.com › engageLink to Engage homepage. Netscout Technology & User Summit. Register now. Attend. Agenda overview · Events · Plan your trip. Learn. Hands-on Workshops.Oct 2 - Oct 5NETSCOUT ENGAGE 2023 ...
☎️ Wire for Android
designing information infrastructure in ways that favour de-centralisation
designing constellation for information creation/curation/conversational collaboration harnessing decen(tralized) protocols
decentralization shifts the parading from centralized silos to a decent/distributed modes, at the edges, where we, the people operate, with increase in autonomy.
But what is needed is to flip the centralized paradigm and put people at the center.
Interpersonal trust networks build for trust from trust,
Empowering individuals and communities to create their own - autonomous digital spaces of their own
that are born interoperable with anything in that - space of permanent hypermedia - HyperDocuments,
that are - local first, - offline first for all participants
yet supports interpersonal collaboration in all collaborative modalities, - real-(time, - eventually consistent async messaging, - continuous without being synchronous,
while maintaining - full contiguity of their own personal/community work and digital engagements
independent of the tools they use for that purpose.
As the IndyVerse/Web/Net/Lab/Learning Commons is piloted at the moment
it also offers deep integration with - web annotation services like Hypothesis and Memex, but any other system can readily be bi integrated (two ways) as plug-outs ready to be integrated into individuals' own(ed) workflows
the IndyWeb also makes use of TrailMarks (generalized into HyperMarks in the IndyVerse of Intentional Morphic HyperDocuments
that itself has 'Universality' in the sense of "Universal Machines'
providing a universal way of designating info structures on the fly, as one writes, and intended interpretation across hypermedia content decouple from the means that were used to create them Where documents are not considered enclosures but dynamic views in a global giant emergent permanent digital spaces
in the first place. Think of TrailMarks as a plain text Symmathetic Mark-In notation that can be added to any content unobtrusively along with the machinery needed to play this intentional/semanttic/symmathetic game
That's what the indyWeb/Net/Hub/Lab pilots
It aims to complete existing systems, including centralized ones.
Centralized system offer global reach, at the risk of censorship, decentralized systems are uncensorable but very limited in reach as they represent technical and other barriers to on-boarding.
On the IndyWeb that Flips the web from server/provider centric to People-centric
IndyNet offers zero friction on-boarding and proogressiver trust networks with potential eventually global reach where servi
for - flipped web - offline first
The Kubo config file
kubo
understand understood popova

When statements in documents become addressable resources on the web, we can weave them together in the way Vannevar Bush imagined.
Yes, that's Trailmarks on the Indyweb
Open HyperDocument System on the interpersonal interplanetary web
the IndyWeb
the flipped web
(inter)personal net dashboard

There’s a tool of his trade called a claim chart. It’s a two-column table. In column one you list claims that a patent is making, which are selections of text from the claims section of the patent.
claim chart

So let’s stare in amazement at another interesting URL

It’s a nice example of how open source components can enable an ecosystem of interoperable annotation services.
open source components enable annotation systems

Weaving the annotated web
for Open Hyperdocument System
back to the future project IndyWeb
Existence. Users must have an independent existence.Any self-sovereign identity can never exist wholly in digital form. It simply makes some real-life aspects of a person public and accessible
 Need to explore the space that opens up
when we affirm the opposite.
Need to explore the space that opens up
when we affirm the opposite.
I interact - here in this space Therefore I AM exists virtually in this virtual space!
All we need is verifiable provenance - audit trail - of all engagements mutually held - privately, - securely, - full custody and control exercised by the Human Actor!
by participants in virtual Networked Interactions
flipped web
IndyWeb
Back to the Future project of realizing Engelbart's Vision of Open Hyperdocument System
Open Hyperdocument System
For individuals, legal entities and devices alike, a verifiableand trusted identity is necessary to interact and transactwith others
transact yes but not for forming autononomnous trust networks
perma-an-note // inspired to write
Complete the Web with - commons based - peer bootstrapped - constellations for - Evergreen - eventually global, nay interplanetary - Networked interpersonal Social Media - around which - interest/mission focused social networks can grow - connecting creators with their audiences, problems with solutions, directly - weaving the Autonomous Open Mutual (l)earning Commons into a virtual co-evolving Open (to change) HyperDocument System as a co-evolving engine for cultural co-evolution

Launch Community
fascinated by the idea of a Launch Community
We are about to create our own
on the IndyWeb

https://hypothes.is/a/wdePFg7HEe61SI_D3OfrAg
Back to the future of Open Hyperdocument System
come back where we have sgtarted and see it for the first time
Doug Engelbart (03) no bio (015) Projects: Hyperscope, Open Hyperdocument System (
OHS
Launch Community

Need to create one for the IndyWeb especially because
it is based on the idea of a Universal HyperDocument
and that Computer Supported Personal Work
and Computer Supported Collaborative Work
requires one that is Personal First with full provenance and recapitulable history
evergreen forward compatible
what that means is Personal Work is
interpersonal with past versions of the OHS
So we need only to Bootstrap one Integral Intentional Evergreen extensible self-hosting HyperDocument System that is based on the notion of a Universal Hyperdocument System
https://dev-indy0.fission.app/hyp/facet/aiframe.html?params=%7B%22user%22%3A%22indyweb%22%2C%22group%22%3A%22all%22%2C%22url%22%3A%22%22%2C%22wildcard_uri%22%3A%22%22%2C%22tag%22%3A%22%22%2C%22any%22%3A%22launch%20community%22%2C%22max%22%3A%22100%22%2C%22service%22%3A%22https%3A%2F%2Fhypothes.is%22%2C%22exactTagSearch%22%3A%22false%22%2C%22expanded%22%3A%22true%22%2C%22addQuoteContext%22%3A%22true%22%2C%22format%22%3A%22html%22%2C%22_separate_replies%22%3A%22false%22%2C%22groupName%22%3A%22All%22%2C%22sortBy%22%3A%22recency%22%7D
Or clone and rehost elsewhere
clo0ne and rehost