- https://polymarket.com/@Rundeep?via=tostitos&tab=activity
- NBC https://www.nbcnews.com/world/israel/israel-charges-reservist-classified-information-bet-polymarket-rcna258709
- reuters https://www.reuters.com/world/middle-east/israel-indicts-reservist-civilian-over-betting-military-operations-2026-02-12/
- Feb 2026
-
x.com x.com
-
-
github.com github.com
-
creator of https://github.com/tw93/Mole
-
- Oct 2025
-
www.youtube.com www.youtube.com
-
www.youtube.com www.youtube.com
-
- 1021 dex vs cex 13:00
-
-
hyperliquid.gitbook.io hyperliquid.gitbook.io
-
The oracle prices are used to compute funding rates. They are also a component in the mark price which is used for margining, liquidations, and triggering TP/SL orders.
oracle price 只是
mark_price的一个 component,还有什么其他因素呢
-
- Sep 2025
- Aug 2025
-
-
via https://x.com/levelsio/status/1960409975655694546
service monitor
-
- Jun 2023
-
-
Only by unblinding the returned signed blinded data, the signature can be extracted.
only those who can unblind the data can get the sig from coordinator?
nice guaranty, but why?
最简单的,通过公钥加密就能实现这一点,coordinator 将 sig 使用 user 的公钥加密,这样,只有拥有私钥的人才能获得 sig,而这个私钥也用于 data 的 blind 过程
-
submits a to-be-funded address alongside the coordinator's signature and the unblinded ticket.
这一步不会暴露 A 地址么?
根据 blind signature 的原理,不会,因为这一步提交的是信件的内容,而前面提交的是信封✉️,两者在外部人员看来,无法建立联系
-
-
github.com github.com
-
nodejs cmd line
-
-
twitter.com twitter.com
-
```
ethers.utils.RLP.encode(["0xd8dA6BF26964aF9D7eEd9e03E53415D37aA96045", ethers.utils.stripZeros(ethers.utils.arrayify(0x0)) ]) '0xd694d8da6bf26964af9d7eed9e03e53415d37aa9604580'
✗ cast keccak 0xd694d8da6bf26964af9d7eed9e03e53415d37aa9604580 0xabb18b93dff3ee19c50127123e4ea2156166390f880071d94458efb098473311 ```
0xabb18b93dff3ee19c50127123e4ea2156166390f880071d94458efb098473311
Tags
Annotators
URL
-
-
github.com github.com
-
docs.ethers.org docs.ethers.org
-
An Application Binary Interface (ABI) is a collection of Fragments which specify how to interact with various components of a Contract.
difference btw. ABI & Fragments & Interface ?
ABI is a collection of Fragments
and fragment is?<br /> fragment is a piece of definition of function/event/error/constructor
and fragment vs interface?<br /> interface is a collection of Fragments<br /> interface is ABI
``` const ABI = [ // Constructor "constructor(address ens)",
// Constant functions (pure or view) "function balanceOf(address owner) view returns (uint)",
// State-mutating functions (payable or non-payable) "function mint(uint amount) payable", "function transfer(address to, uint amount) returns (bool)",
// Events "event Transfer(address indexed from, address indexed to, uint amount)",
// Errors "error InsufficientFunds(address from, uint balance)", ] ```
-
-
docs.ethers.org docs.ethers.orgAbiCoder2
-
AbiCoder: encode/decode btw. types and binary data
-
Most developers will never need to use this class directly, since the Interface class greatly simplifies these operations.
AbiCoder vs Interface
difference?
-
-
twitter.com twitter.com
-
validium
Tags
Annotators
URL
-
-
era.zksync.io era.zksync.io
-
After the verification passes, the batch of transactions is considered final like any other Ethereum transaction
actually https://hypothes.is/a/DsLSWgmVEe6bEJM6fFGNwA
but showed up here
-
- Apr 2023
-
twitter.com twitter.com
-
入门零知识需要的预备知识
Tags
Annotators
URL
-
-
mp.weixin.qq.com mp.weixin.qq.com
-
zkp 学习班
-
- Jul 2021
-
blog.ethereum.org blog.ethereum.org
-
The state in Ethereum essentially consists of a key-value map, where the keys are addresses and the values are account declarations, listing the balance, nonce, code and storage for each account (where the storage is itself a tree).
state in eth: a k-v map
- key: address
- value: account infos:
- balance
- nonce
- code
- storage (which itself is another tree)
-
- Apr 2021
-
-
via https://stackoverflow.blog/2021/04/23/podcast-332-non-fungible-talking/?cb=1
check if devlop on Ethereum still sucks
-
-
www.youtube.com www.youtube.com
-
www.youtube.com www.youtube.com
-
Fork Uniswap & Create Your Own Sushiswap
-
-
-
evm_mine
await network.provider.send("evm_mine")
-
-
ethereum.stackexchange.com ethereum.stackexchange.com
-
hardhat mining timestamp
-
-
docs.ethers.io docs.ethers.io
-
formatEther
ethers.utils.formatEther(await vault.totalSupply()) '53.670765503837765998'
-
-
github.com github.com
-
IRC client
-
-
-
deposit LP token to Bunny's VaultFlipToCake
-
-
-
add Liquidity to USDT-BUSD pool at PancakeSwap
-
-
github.com github.com
-
uPic upload pic
-
-
itnext.io itnext.io
-
a.addUint(b); meaning a is passed automatically as first argument to the library function.
using count for uint; a.addUint(b) // equal count.addUint(a, b)看起来
using for就是个语法糖🍬 -
The using A for B; directive means we attach library functions( from the library A to any type B). When this happens, these functions will receive the object they are called on as their first parameter
using A for typeB; typeB.fooFunc(1) => A.fooFunc(typeB, 1) -
then the library doesn’t need to be deployed
?
不部署 library 的代码从哪儿来?
-
-
docs.soliditylang.org docs.soliditylang.org
-
Function Types
via https://medium.com/coinmonks/all-you-should-know-about-libraries-in-solidity-dd8bc953eae7
Tags
Annotators
URL
-
-
-
If a smart contract is consuming a library which have only internal functions than EVM simply embeds library into the contract.
? 没看懂
-
-
github.com github.com
-
the famous gas fee problem
still not read yet
-
- Mar 2021
-
kubernetes.io kubernetes.io
-
A records
对于普通的 Service, A 记录对应的形式是
svc-name.namesapce.svc.cluster-domain.example, 指向 service 的 cluster ipheadless service 没有 cluster ip,指向的直接是 service 匡选的 pods 对应的 IPs
svc.cluster-domain.example是什么东西?
这个是 DNS search list
-
-
www.youtube.com www.youtube.com
-
seems a interesting talk on k8s
听了一半,这里的 Builders and Operators 指的是运维而非 k8s controller 里的 operator,以后有机会再看看吧
配合自己用 kubeadm 部署一个 cluster 可能不错
-
-
vitalik.ca vitalik.ca
-
via https://news.ycombinator.com/item?id=25640976
LOL, my tag makes me laugh
Tags
Annotators
URL
-
-
cert-manager.io cert-manager.io
-
isCA: false
certificate as CA?
啥意思,证书可以作为 CA 去签其他证书?
CA 本质上就是一个证书(包含一对公私钥),公钥用来表示自己,私钥用来签名
-
- Jan 2021
-
draveness.me draveness.me
-
a book on Golang
-
-
www.bt.cn www.bt.cn
-
via Aladdin, when talking about Kalm potential user
-
-
redux.js.org redux.js.org
-
Creating a Single Post Page
todo, make this link to single post work
Tags
Annotators
URL
-
-
grafana.com grafana.com
-
serve_from_sub_path
example config: https://grafana.com/tutorials/run-grafana-behind-a-proxy/#1
-
database
grafana data 持久化
-
-
grafana.com grafana.com
-
配置 grafana sub path
参考
-
-
docs.docker.com docs.docker.com
-
Understand how CMD and ENTRYPOINT interact
CMD v.s ENTRYPOINT
-
-
github.com github.com
-
via 磊哥
-
-
-
via Mattermost
-
-
github.com github.com
-
open source slack
via 磊哥
-
-
-
open source slack
-
-
grafana.com grafana.com
-
This will make GitOps more natural as data sources and dashboards can be defined via files that can be version controlled. We hope to extend this system to later add support for users, orgs and alerts as well.
support:
- data source
- dashboards
not support yet:
- users
- orgs
- alerts
-
-
grafana.com grafana.com
-
labelmap: Match regex against all label names. Then copy the values of the matching labels to label names given by replacement with match group references (${1}, ${2}, …) in replacement substituted by their value.
- action: labelmap regex: __meta_kubernetes_service_label_(.+) // all __meta_kubernetes_service_label_(.+) will be changed to the (.+) // e.g. // __meta_kubernetes_service_label_app='armada-api' // to // app='armada-api'from https://gist.github.com/reachlin/a98b90afcbff4604c90c183a0169474f#file-prometheus-yml-L43-L46
-
role types
roles types for
kubernetes_sd_config:- node
- service
- pod
- endpoints
- ingress
-
-
gist.github.com gist.github.com
-
labelmap
nice example on how
labelmapinrelabel_configsworks
-
-
musclewiki.com musclewiki.com
-
nice workout site
-
-
grafana.com grafana.com
-
Auth Proxy Authentication
seems related to Kalm integrating PLG (Promtail Loki Grafana)
-
-
github.com github.com
-
might worth reading for loki multi-tenancy
-
-
www.youtube.com www.youtube.com
-
Grafana Loki
energetic intro to Grafana Loki
-
-
-
a discussion on abandon multi-org in Grafana
-
-
github.com github.com
-
see it again via https://twitter.com/patrickc/status/1351650517869465601
-
-
www.infracloud.io www.infracloud.io
-
multi-tenant log aggregation system
nice!
-
-
-
MARK
-
-
www.thefxck.com www.thefxck.com
-
a story for production Positioning?
-
-
fediverse.party fediverse.party
-
via https://framagit.org/tom79/fedilab
this is a site for what?
-
-
www.ruanyifeng.com www.ruanyifeng.com
-
-
eth
Tags
Annotators
URL
-
-
tjayrush.medium.com tjayrush.medium.com
-
Finally, to jump up to a full blown audit node, we recommend the following specs:A solid state drive (SSD) of 8 TBAt least 32 GB of RAMIntel i7 or equivalent
8TB 的 SSD,有点儿夸张。。。
-
-
www.duneanalytics.com www.duneanalytics.com
-
a interesting service for ETH
-
-
www.ruanyifeng.com www.ruanyifeng.com
-
后半段没看懂,dispatch not only object, but also func
-
下面是它的源码
天书
-
via http://www.ruanyifeng.com/blog/2016/09/redux_tutorial_part_one_basic_usages.html
-
-
duibiao.info duibiao.info
-
不错
-
-
zh.wikipedia.org zh.wikipedia.org
-
好听
-
-
zhuanlan.zhihu.com zhuanlan.zhihu.com
-
这套视频不错啊
肌肉 放松
-
-
www.michaelseibel.com www.michaelseibel.com
-
via david
-
-
mp.weixin.qq.com mp.weixin.qq.com
-
有意思的问题
-
-
startupclass.samaltman.com startupclass.samaltman.com
-
startup class
-
-
redux.js.org redux.js.org
-
www.ruanyifeng.com www.ruanyifeng.com
-
combineReducer的简单实现
不明觉厉
-
dispatch({});
这行调用是干啥的?
-
-
legacy.reactjs.org legacy.reactjs.org
-
完成了 MAIN CONCEPTS
-
-
github.com github.com
-
via our kalm SaaS project
-
-
coolshell.cn coolshell.cn
-
好文章
-
-
github.com github.com
-
www.youtube.com www.youtube.com
-
Tim Roughgarden 对 EIP-1559 的经济分析视频
-
-
github.com github.com
-
surprising PDF
-
-
www.youtube.com www.youtube.com
-
MARK 19:21
MARK 19:21
-
MARK
-
-
weibo.com weibo.com
-
精准扶贫
-
- Dec 2020
-
weibo.com weibo.com
-
陈文非
-
-
www.facebook.com www.facebook.com
-
-
via B站 2020 跨年晚会
-
-
mp.weixin.qq.com mp.weixin.qq.com
-
kubevela, ali, kalm
-
-
zhuanlan.zhihu.com zhuanlan.zhihu.com
-
kubevela, ali, kalm
-
-
zhuanlan.zhihu.com zhuanlan.zhihu.com
-
kubevela, ali, kalm
-
-
swimlanes.io swimlanes.io
-
这个时序图的工具貌似也不错
-
-
github.com github.com
-
docs.kubesail.com docs.kubesail.com
-
KubeSail.com can also forward kube-api and Ingress traffic to your cluster! This allows you to host internet-facing applications on your cluster, even if it does not have a reliable static IP address, and without having to forward ports. HTTPS traffic is kept secure and encrypted from the internet all the way to your cluster's applications - it's never decrypted by KubeSail (or the KubeSail agent).
怎么做到的
-
-
movie.douban.com movie.douban.com
-
哈哈哈,就从评价和标记都没了这点,就知道这部电影可以一看
-
-
github.com github.com
-
牛逼 airdrop
-
-
francescodilorenzo.com francescodilorenzo.com
-
被人开心使用的 SaaS
Tags
Annotators
URL
-
-
www.youtube.com www.youtube.com
-
不错的自由泳总述
-
-
github.com github.com
-
-
有意思 老照片修复
-
-
github.com github.com
-
via bfd-engine
-
-
snapdrop.net snapdrop.netSnapdrop1
-
牛逼 有意思
-
-
casbin.org casbin.org
-
p.eft is the effect for a policy, it can be allow or deny
eft == effect
骚气的简写,给跪
-
-
www.youtube.com www.youtube.com
-
粗略过了一遍,基本没懂,还得再学习...
-
-
xinpure.com xinpure.com
-
设置 networkservice DHCP
DHCP
sudo networksetup -setdhcp Wi-Fi networksetup -setdnsservers Wi-Fi 192.168.1.1Koolshare
networksetup -setmanual Wi-Fi 192.168.1.234 255.255 .255.0 192.168.1.233 networksetup -setdnsservers Wi-Fi 192.168.1.233
-
-
www.postgresql.org www.postgresql.org
-
You can change default privileges only for objects that will be created by yourself or by roles that you are a member of.
没看懂但是和我们这个错误貌似相关
ALTER DEFAULT PRIVILEGES FOR ROLE bfd IN SCHEMA public REVOKE ALL ON TABLES FROM bfd; # ERROR: must be member of role "bfd"
-
-
github.com github.com
-
via PGraham
-
-
www.nytimes.com www.nytimes.com
-
有点儿意思
蠢驴不蠢,精明得很
-
-
twitter.com twitter.com
-
cloud.google.com cloud.google.com
-
gsutil cp gs://ddex-db-export/bfd.sql /mnt/disks/tmp-for-bucket/
-
-
cloud.google.com cloud.google.com
-
deal with google bucket using: gsutil
-
-
github.com github.com
-
cloud.google.com cloud.google.com
-
Cloud Storage FUSE
mount bucket to vm
-
-
www.youtube.com www.youtube.com
-
www.youtube.com www.youtube.com
-
www.youtube.com www.youtube.com
-
via https://www.youtube.com/watch?v=rI7GRUhWtuI&t=62s
A Promised Land
-
-
wizardforcel.gitbooks.io wizardforcel.gitbooks.io
-
生财有术
生财有术
-
-
wizardforcel.gitbooks.io wizardforcel.gitbooks.io
-
思路不错
-
-
wizardforcel.gitbooks.io wizardforcel.gitbooks.io
-
www.indiehackers.com www.indiehackers.com
-
mp.weixin.qq.com mp.weixin.qq.com
-
kubernetes.io kubernetes.io
-
Sometimes, applications are temporarily unable to serve traffic. For example, an application might need to load large data or configuration files during startup, or depend on external services after startup. In such cases, you don't want to kill the application, but you don't want to send it requests either. Kubernetes provides readiness probes to detect and mitigate these situations. A pod with containers reporting that they are not ready does not receive traffic through Kubernetes Services.
alive but not ready for requests
-
-
www.cloudflare.com www.cloudflare.com
-
All DNS servers fall into one of four categories: Recursive resolvers, root nameservers, TLD nameservers, and authoritative nameservers.
4 types of DNS Server:
- Recursive Solver
- root NS
- TLD NS
- authoritative nameservers
-
-
www.cloudflare.com www.cloudflare.com
-
start of authority
SOA = Start Of Authority
-
-
ns1.com ns1.com
-
Domain Information Groper
DIG: Domain Info Groper
-
-
-
time-to-live (TTL)
TTL for cache
-
the .com Top-Level Domain (TLD)
TLD: Top Level Domain
-
recursive resolver
recursive resolver, 这是个什么鬼?
-
-
www.iana.org www.iana.org
-
The authoritative name servers that serve the DNS root zone, commonly known as the “root servers”, are a network of hundreds of servers in many countries around the world. They are configured in the DNS root zone as 13 named authorities
13 个 root servers
-
-
github.com github.com
-
competitor of Istio?
-
-
github.com github.com
-
DeferredDiscoveryRESTMapper
There are multiple different implementations of the RESTMapper interface. The most important one for client applications is the discovery-based DeferredDiscoveryRESTMapper in the package k8s.io/client-go/restmapper: it uses discovery information from the Kubernetes API server to dynamically build up the REST mapping. It will also work with non-core resources like custom resources.
From: programming kubernetes
-
-
youke.co youke.co
-
有点儿意思
-
-
github.com github.com
-
anandzhang.com anandzhang.com
-
v2ray config
主要是其中分别检查各个部分是否正确,给了我debug的思路。。。
-
-
finance.sina.com.cn finance.sina.com.cn
-
这个牛逼,有科幻的意思了
-
-
-
cool coding site
-
-
github.com github.com
-
probers point to a new endpoint at port 15020, this is expected. As the name indicates, "prober rewrites" means the actual podspec container prober configuration is configured to different path and port.
Istio re-write probe port to 15020
-
-
moderncto.io moderncto.io
-
doorDash CTO
Tags
Annotators
URL
-
-
zapier.com zapier.com
-
Why Zapier has always been 100% remote
Tags
Annotators
URL
-
-
medium.com medium.com
-
gcloud config set xxx yyy
-
-
-
controller-runtime is doing this
not sure how this works but yes, it works
-
-
samczsun.com samczsun.com
-
price oracle
-
-
www.youtube.com www.youtube.com
-
consensys.net consensys.net
-
intro of PoS
-
and may not even exist.
?
-
-
-
intro of ETH2
-
-
ethereum.org ethereum.org
-
Sharding the network in a proof-of-work system would simply lower the power needed to compromise a portion of the network
如果是挖矿的模式下(PoW),多条链的 sharding 模式意味着算力的分散,51% 攻击某条链的成本更低了
-
and more nodes doesn't mean increased % returns
?
-
Crosslinks
?
-
After each epoch, the committee is disbanded and reformed with different, random participants.
?
-
seems a good place to start learning of PoS
-
-
ethereum.org ethereum.org
-
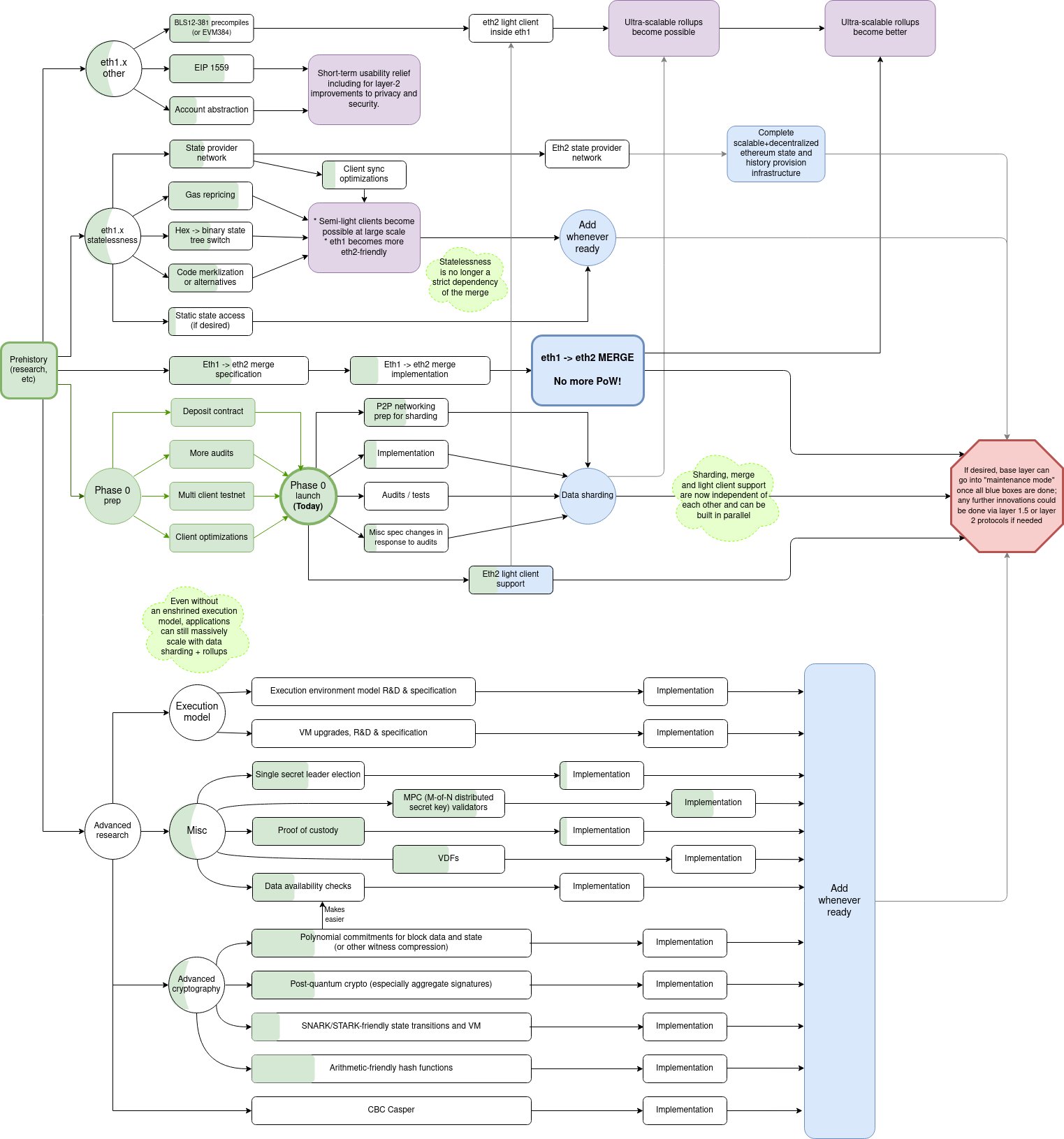
The Eth2 upgrades
三步走:
- The Beacon Chain (live)
- Shard chains
- The docking
-
How the upgrades fit together
这个图不错啊
beacon chain 和 mainnet 现在以及将来的关系非常直观
-
ETH2 home page
-
-
www.youtube.com www.youtube.com
-
不错的一个 eth2 扫盲科普
-
-
ethereum.org ethereum.org
-
sharding
-
-
ethereum.org ethereum.org
-
But it won't be like the Ethereum mainnet of today. It can't handle accounts or smart contracts.
?
-
-
ethfans.org ethfans.org
-
原文: A Proof of Stake Design Philosophy
https://medium.com/@VitalikButerin/a-proof-of-stake-design-philosophy-506585978d51
-
-
-
Vitalik on PoS
-
-
github.com github.com
-
github.com github.com
-
科学上网
-
-
tylertringas.com tylertringas.com
-
不错的思路,点子💡 绞肉机,meat grinder
-
-
blog.rchase.com blog.rchase.com
-
一个胶水项目,为 UnifFi 自动部署 Cloud 版本
部署的这个程序是官方提供的,这个项目其实就是将起VPS,和安装自动化了
还是非常有启发的
-
-
blog.rchase.com blog.rchase.com
-
No Surprise, SNS
-
-
-
lsof -i :80
lsofrocks
-
-
number-none.com number-none.com
-
coding style
John Carmack on coding style
-
-
github.com github.com
-
www.youtube.com www.youtube.com
-
seems interesting
-
-
www.youtube.com www.youtube.com
-
API Machinery SIG
-
-
github.com github.com
-
nice talks, especially from Daniel Smith
Tags
Annotators
URL
-
-
istio.io istio.io
-
The Envoy proxy uses 0.35 vCPU and 40 MB memory per 1000 requests per second going through the proxy.
too good to be true?
-
In a large namespace, the proxy consumes approximately 50 MB of memory.
in our setup, istio memory limit 64Mi will cause:
command 'pilot-agent wait' exited with 137
seems SIGKILLED by out of ram?
-
- Nov 2020
-
legacy.reactjs.org legacy.reactjs.org
-
todo 20201130
-