While the increasing importance of interconnection with technologies,
redacción
While the increasing importance of interconnection with technologies,
redacción
Self-efficacy has proven to be particularly relevant when it comes to digital technologies learning achievements. A whole thematic research agenda has opened up around self-efficacy role on the adoption of new technologies and the develop of competences on digital environments, although there are scattered efforts when it comes to measuring this construct.
párrafo volando
i) plays a central role in the self-regulation of motivation through goal challenges and outcome expectations. ii) determines the challenge to undertake, how much effort to expend in the endeavor, how long to persevere in the face of obstacles and failure, and whether failures are motivating or demoralizing. iii) Efficacy beliefs also play a key role in shaping the course of life by influencing the types of activities and environments people choose to get into.
mejorar estructura de como se cuenta esto, mucha información
Are you a developer, product manager, or business leader in the HealthTech sector? Are you looking to bring your digital health app to the UK healthcare market? Is your team struggling to understand or comply with the complex and evolving UK regulatory landscape, such as the NHS and MHRA app compliance checklist? You’re not alone, and this guide on building compliant HealthTech apps in the UK is designed to help you through the entire process.
Learn how to build healthcare apps in the UK that comply with NHS digital standards and MHRA medical-device regulations. This CMARIX guide covers UK-specific regulatory requirements, UKCA marking, DTAC framework, GDPR, risk management, clinical evaluation, and post-market surveillance.
Note: This response was posted by the corresponding author to Review Commons. The content has not been altered except for formatting.
Learn more at Review Commons
Reviewer #1
Evidence, reproducibility and clarity
This paper addresses a very interesting problem of non-centrosomal microtubule organization in developing Drosophila oocytes. Using genetics and imaging experiments, the authors reveal an interplay between the activity of kinesin-1, together with its essential cofactor Ensconsin, and microtubule organization at the cell cortex by the spectraplakin Shot, minus-end binding protein Patronin and Ninein, a protein implicated in microtubule minus end anchoring. The authors demonstrate that the loss of Ensconsin affects the cortical accumulation non-centrosomal microtubule organizing center (ncMTOC) proteins, microtubule length and vesicle motility in the oocyte, and show that this phenotype can be rescued by constitutively active kinesin-1 mutant, but not by Ensconsin mutants deficient in microtubule or kinesin binding. The functional connection between Ensconsin, kinesin-1 and ncMTOCs is further supported by a rescue experiment with Shot overexpression. Genetics and imaging experiments further implicate Ninein in the same pathway. These data are a clear strength of the paper; they represent a very interesting and useful addition to the field.
The weaknesses of the study are two-fold. First, the paper seems to lack a clear molecular model, uniting the observed phenomenology with the molecular functions of the studied proteins. Most importantly, it is not clear how kinesin-based plus-end directed transport contributes to cortical localization of ncMTOCs and regulation of microtubule length.
Second, not all conclusions and interpretations in the paper are supported by the presented data.
We thank the reviewer for recognizing the impact of this work. In response to the insightful suggestions, we performed extensive new experiments that establish a well-supported cellular and molecular model (Figure 7). The discussion has been restructured to directly link each conclusion to its corresponding experimental evidence, significantly strengthening the manuscript.
Below is a list of specific comments, outlining the concerns, in the order of appearance in the paper/figures.
Figure 1. The statement: "Ens loading on MTs in NCs and their subsequent transport by Dynein toward ring canals promotes the spatial enrichment of the Khc activator Ens in the oocyte" is not supported by data. The authors do not demonstrate that Ens is actually transported from the nurse cells to the oocyte while being attached to microtubules. They do show that the intensity of Ensconsin correlates with the intensity of microtubules, that the distribution of Ensconsin depends on its affinity to microtubules and that an Ensconsin pool locally photoactivated in a nurse cell can redistribute to the oocyte (and throughout the nurse cell) by what seems to be diffusion. The provided images suggest that Ensconsin passively diffuses into the oocyte and accumulates there because of higher microtubule density, which depends on dynein. To prove that Ensconsin is indeed transported by dynein in the microtubule-bound form, one would need to measure the residence time of Ensconsin on microtubules and demonstrate that it is longer than the time needed to transport microtubules by dynein into the oocyte; ideally, one would like to see movement of individual microtubules labelled with photoconverted Ensconsin from a nurse cell into the oocyte. Since microtubules are not enriched in the oocyte of the dynein mutant, analysis of Ensconsin intensity in this mutant is not informative and does not reveal the mechanism of Ensconsin accumulation.
As noted by Reviewer 3, the directional movement of microtubules traveling at ~140 nm/s from nurse cells toward the oocyte through Ring Canals was previously reported using a tagged Ens-MT binding domain reporter line by Lu et al. (2022). We have therefore added the citation of this crucial work in the novel version of the manuscript (lane 155-157) and removed the photo-conversion panel.
Critically, however, our study provides mechanistic insight that was missing from this earlier work: this mechanism is also crucial to enrich MAPs in the oocyte. The fact that Dynein mutants fail to enrich Ensconsin is a crucial piece of evidence: it supports a model of Ensconsin-loaded MT transport (Figure 1D-1F).
Figure 2. According to the abstract, this figure shows that Ensconsin is "maintained at the oocyte cortex by Ninein". However, the figure doesn't seem to prove it - it shows that oocyte enrichment of Ensonsin is partially dependent on Ninein, but this applies to the whole cell and not just to the cell cortex. Furthermore, it is not clear whether Ninein mutation affects microtubule density, which in turn would affect Ensconsin enrichment, and therefore, it is not clear whether the effect of Ninein loss on Ensconsin distribution is direct or indirect.
Ninein plays a critical role in Ensconsin enrichment and microtubule organization in the oocyte (new Figure 2, Figure 3, Figure S3). Quantification of total Tubulin signal shows no difference between control and Nin mutant oocytes (new Figure S3 panels A, B). We found decreased Ens enrichment in the oocyte, and Ens localization on MTs and to the cell cortex (Figure 2E, 2F, and Figure S3C and S3D).
Novel quantitative analyses of microtubule orientation at the anterior cortex, where MTs are normally preferentially oriented toward the posterior pole (Parton et al. 2011), demonstrate that Nin mutants exhibit randomized MT orientation compared to wild-type oocytes (new Figure 3C-3E).These findings establish that Ninein (although not essential) favors Ensconsin localization on MTs, Ens enrichment in the oocyte, ncMTOC cortical localization, and more robust MT orientation toward the posterior cortex. It also suggests that Ens levels in the oocyte acts as a rheostat to control Khc activation.
The observation that the aggregates formed by overexpressed Ninein accumulate other proteins, including Ensconsin, supports, though does not prove their interactions. Furthermore, there is absolutely no proof that Ninein aggregates are "ncMTOCs". Unless the authors demonstrate that these aggregates nucleate or anchor microtubules (for example, by detailed imaging of microtubules and EB1 comets), the text and labels in the figure would need to be altered.
We have modified the manuscript, we now refer to an accumulation of these components in large puncta, rather than aggregates, consistent with previous observations (Rosen et al., 2000). We acknowledge in the revised version that these puncta recruit Shot, Patronin and Ens without mentioning direct interaction (lane 218).
Importantly, we conducted a more detailed characterization of these Ninein/Shot/Patronin/Ens-containing puncta in a novel Figure S4. To rigorously assess their nucleation capacity, we analyzed Eb1-GFP-labeled MT comets, a robust readout of MT nucleation (Parton et al., 2011, Nashchekin et al., 2016). While few Eb1-positive comets occasionally emanate from these structures, confirming their identity as putative ncMTOCs, these puncta function as surprisingly weak nucleation centers (new Figure S4 E, Video S1) and, their presence does not alter overall MT architecture (new Figure S4 F). Moreover, these puncta disappear over time, are barely visible at stage 10B, they do not impair oocyte development or fertility (Figure S4 G and Table 1).
Minor comment: Note that a "ratio" (Figure 2C) is just a ratio, and should not be expressed in arbitrary units.
We have amended this point in all the figures.
Figure 3B: immunoprecipitation results cannot be interpreted because the immunoprecipitated proteins (GFP, Ens-GFP, Shot-YFP) are not shown. It is also not clear that this biochemical experiment is useful. If the authors would like to suggest that Ensconsin directly binds to Patronin, the interaction would need to be properly mapped at the protein domain level.
This is a good point: the GFP and Ens-GFP immunoprecipitated proteins are now much clearly identified on the blots and in the figure legend (new Figure 4G). Shot-YFP IP, was used as a positive control but is difficult to be detected by Western blot due to its large size (>106 Da) using conventional acrylamide gels (Nashchekin et al., 2016).
We now explicitly state that immunoprecipitations were performed at 4°C, where microtubules are fully depolymerized, thereby excluding undirect microtubule-mediated interactions. We agree with this reviewer: we cannot formally rule out interactions through bridging by other protein components. This is stated in the revised manuscript (lane 238-239).
One of the major phenotypes observed by the authors in Ens mutant is the loss of long microtubules. The authors make strong conclusions about the independence of this phenotype from the parameters of microtubule plus-end growth, but in fact, the quality of their data does not allow to make such a conclusion, because they only measured the number of EB1 comets and their growth rate but not the catastrophe, rescue or pausing frequency."Note that kinesin-1 has been implicated in promoting microtubule damage and rescue (doi: 10.1016/j.devcel.2021).In the absence of such measurements, one cannot conclude whether short microtubules arise through defects in the minus-end, plus-end or microtubule shaft regulation pathways.
We thank the reviewer for raising this important point. Our data demonstrate that microtubule (MT) nucleation and polymerization rates remain unaffected under Khc RNAi and ens mutant conditions, indicating that MT dynamics alterations must arise through alternative mechanisms.
As the reviewer suggested, recent studies on Kinesin activity and MT network regulation are indeed highly relevant. Two key studies from the Verhey and Aumeier laboratories examined Kinesin-1 gain-of-function conditions and revealed that constitutively active Kinesin-1 induces MT lattice damage (Budaitis et al., 2022). While damaged MTs can undergo self-repair, Aumeier and colleagues demonstrated that GTP-tubulin incorporation generates "rescue shafts" that promote MT rescue events (Andreu-Carbo et al., 2022). Extrapolating from these findings, loss of Kinesin-1 activity could plausibly reduce rescue shaft formation, thereby decreasing MT rescue frequency and stability. Although this hypothesis is challenging to test directly in our system, it provides a mechanistic framework for the observed reduction in MT number and stability.
Additionally, the reviewer highlighted the role of Khc in transporting the dynactin complex, an anti-catastrophe factor, to MT plus ends (Nieuwburg et al., 2017), which could further contribute to MT stabilization. This crucial reference is now incorporated into the revised Discussion.
Importantly, our work also demonstrates the contribution of Ens/Khc to ncMTOC targeting to the cell cortex. Our new quantitative analyses of MT organization (new Figure 5 B) reveal a defective anteroposterior orientation of cortical MTs in mutant conditions, pointing to a critical role for cortical ncMTOCs in organizing the MT network.
Taken together, we propose that the observed MT reduction and disorganization result from multiple interconnected mechanisms: (1) reduced rescue shaft formation affecting MT stability; (2) impaired transport of anti-catastrophe factors to MT plus ends; and (3) loss of cortical ncMTOCs, which are essential for minus-end MT stabilization and network organization. The Discussion has been revised to reflect this integrated model in a dedicated paragraph (“A possible regulation of MT dynamics in the oocyte at both plus end minus MT ends by Ens and Khc” lane 415-432).
It is important to note in that a spectraplakin, like Shot, can potentially affect different pathways, particularly when overexpressed.
We agree that Shot harbors multiple functional domains and acts as a key organizer of both actin and microtubule cytoskeletons. Overexpression of such a cytoskeletal cross-linker could indeed perturb both networks, making interpretation of Ens phenotype rescue challenging due to potential indirect effects.
To address this concern, we selected an appropriate Shot isoform for our rescue experiments that displayed similar localization to “endogenous” Shot-YFP (a genomic construct harboring shot regulatory sequences) and importantly that was not overexpressed.
Elevated expression of the Shot.L(A) isoform (see Western Blot Figure S8 A), considered as the wild-type form with two CH1 and CH2 actin-binding motifs (Lee and Kolodziej, 2002), showed abnormal localization such as strong binding to the microtubules in nurse cells and oocyte confirming the risk of gain-of-function artifacts and inappropriate conclusions (Figure S8 B, arrows).
By contrast, our rescue experiments using the Shot.L(C) isoform (that only harbors the CH2 motif) provide strong evidence against such artifacts for three reasons. First, Shot-L(C) is expressed at slightly lower levels than a Shot-YFP genomic construct (not overexpressed), and at much lower levels than Shot-L(A), despite using the same driver (Figure S8 A). Second, Shot-L(C) localization in the oocyte is similar to that of endogenous Shot-YFP, concentrating at the cell cortex (Figure S8 B, compare lower and top panels). Taken together, these controls rather suggest our rescue with the Shot-L(C) is specific.
Note that this Shot-L(C) isoform is sufficient to complement the absence of the shot gene in other cell contexts (Lee and Kolodziej, 2002).
Unjustified conclusions should be removed: the authors do not provide sufficient data to conclude that "ens and Khc oocytes MT organizational defects are caused by decreased ncMTOC cortical anchoring", because the actual cortical microtubule anchoring was not measured.
This is a valid point. We acknowledge that we did not directly measure microtubule anchoring in this study. In response, we have revised the discussion to more accurately reflect our observations. Throughout the manuscript, we now refer to "cortical microtubule organization" rather than "cortical microtubule anchoring," which better aligns with the data presented.
Minor comment: Microtubule growth velocity must be expressed in units of length per time, to enable evaluating the quality of the data, and not as a normalized value.
This is now amended in the revised version (modified Figure S7).
A significant part of the Discussion is dedicated to the potential role of Ensconsin in cortical microtubule anchoring and potential transport of ncMTOCs by kinesin. It is obviously fine that the authors discuss different theories, but it would be very helpful if the authors would first state what has been directly measured and established by their data, and what are the putative, currently speculative explanations of these data.
We have carefully considered the reviewer's constructive comments and are confident that this revised version fully addresses their concerns.
First, we have substantially strengthened the connection between the Results and Discussion sections, ensuring that our interpretations are more directly anchored in the experimental data. This restructuring significantly improves the overall clarity and logical flow of the manuscript.
Second, we have added a new comprehensive figure presenting a molecular-scale model of Kinesin-1 activation upon release of autoinhibition by Ensconsin (new Figure 7D). Critically, this figure also illustrates our proposed positive feedback loop mechanism: Khc-dependent cytoplasmic advection promotes cortical recruitment of additional ncMTOCs, which generates new cortical microtubules and further accelerates cytoplasmic transport (Figure 7 A-C). This self-amplifying cycle provides a mechanistic framework consistent with emerging evidence that cytoplasmic flows are essential for efficient intracellular transport in both insect and mammalian oocytes.
Minor comment: The writing and particularly the grammar need to be significantly improved throughout, which should be very easy with current language tools. Examples: "ncMTOCs recruitment" should be "ncMTOC recruitment"; "Vesicles speed" should be "Vesicle speed", "Nin oocytes harbored a WT growth,"- unclear what this means, etc. Many paragraphs are very long and difficult to read. Making shorter paragraphs would make the authors' line of thought more accessible to the reader.
We have amended and shortened the manuscript according to this reviewer feed-back. We have specifically built more focused paragraphs to facilitates the reading.
Significance
This paper represents significant advance in understanding non-centrosomal microtubule organization in general and in developing Drosophila oocytes in particular by connecting the microtubule minus-end regulation pathway to the Kinesin-1 and Ensconsin/MAP7-dependent transport. The genetics and imaging data are of good quality, are appropriately presented and quantified. These are clear strengths of the study which will make it interesting to researchers studying the cytoskeleton, microtubule-associated proteins and motors, and fly development.
The weaknesses of this study are due to the lack of clarity of the overall molecular model, which would limit the impact of the study on the field. Some interpretations are not sufficiently supported by data, but this can be solved by more precise and careful writing, without extensive additional experimentation.
We thank the reviewer for raising these important concerns regarding clarity and data interpretation. We have thoroughly revised the manuscript to address these issues on multiple fronts. First, we have substantially rewritten key sections to ensure that our conclusions are clearly articulated and directly supported by the data. Second, we have performed several new experiments that now allow us to propose a robust mechanistic model, presented in new figures. These additions significantly strengthen the manuscript and directly address the reviewer's concerns.
My expertise is cell biology and biochemistry of the microtubule cytoskeleton, including both microtubule-associated proteins and microtubule motors.
Reviewer #2
Evidence, reproducibility and clarity
In this manuscript, Berisha et al. investigate how microtubule (MT) organization is spatially regulated during Drosophila oogenesis. The authors identify a mechanism in which the Kinesin-1 activator Ensconsin/MAP7 is transported by dynein and anchored at the oocyte cortex via Ninein, enabling localized activation of Kinesin-1. Disruption of this pathway impairs ncMTOC recruitment and MT anchoring at the cortex. The authors combine genetic manipulation with high-resolution microscopy and use three key readouts to assess MT organization during mid-to-late oogenesis: cortical MT formation, localization of posterior determinants, and ooplasmic streaming. Notably, Kinesin-1, in concert with its activator Ens/MAP7, contributes to organizing the microtubule network it travels along. Overall, the study presents interesting findings, though we have several concerns we would like the authors to address. Ensconsin enrichment in the oocyte 1. Enrichment in the oocyte • Ensconsin is a MAP that binds MTs. Given that microtubule density in the oocyte significantly exceeds that in the nurse cells, its enrichment may passively reflect this difference. To assess whether the enrichment is specific, could the authors express a non-Drosophila MAP (e.g., mammalian MAP1B) to determine whether it also preferentially localizes to the oocyte?
To address this point, we performed a new series of experiments analyzing the enrichment of other Drosophila and non-Drosophila MAPs, including Jupiter-GFP, Eb1-GFP, and bovine Tau-GFP, all widely used markers of the microtubule cytoskeleton in flies (see new Figure S2). Our results reveal that Jupiter-GFP, Eb1-GFP, and bovine Tau-GFP all exhibit significantly weaker enrichment in the oocyte compared to Ens-GFP. Khc-GFP also shows lower enrichment. These findings indicate that MAP enrichment in the oocyte is MAP-dependent, rather than solely reflecting microtubule density or organization. Of note, we cannot exclude that microtubule post-translational modifications contribute to differential MAP binding between nurse cells and the oocyte, but this remains a question for future investigation.
The ability of ens-wt and ens-LowMT to induce tubulin polymerization according to the light scattering data (Fig. S1J) is minimal and does not reflect dramatic differences in localization. The authors should verify that, in all cases, the polymerization product in their in vitro assays is microtubules rather than other light-scattering aggregates. What is the control in these experiments? If it is just purified tubulin, it should not form polymers at physiological concentrations.
The critical concentration Cr for microtubule self-assembly in classical BRB80 buffer found by us and others is around 20 µM (see Fig. 2c in Weiss et al., 2010). Here, microtubules were assembled at 40 µM tubulin concentration, i.e., largely above the Cr. As stated in the materials and methods section, we systematically induced cooling at 4°C after assembly to assess the presence of aggregates, since those do not fall apart upon cooling. The decrease in optical density upon cooling is a direct control that the initial increase in DO is due to the formation of microtubules. Finally, aggregation and polymerization curves are widely different, the former displaying an exponential shape and the latter a sigmoid assembly phase (see Fig. 3A and 3B in Weiss et al., 2010).
Photoconversion caveatsMAPs are known to dynamically associate and dissociate from microtubules. Therefore, interpretation of the Ens photoconversion data should be made with caution. The expanding red signal from the nurse cells to the oocyte may reflect a any combination of dynein-mediated MT transport and passive diffusion of unbound Ensconsin. Notably, photoconversion of a soluble protein in the nurse cells would also result in a gradual increase in red signal in the oocyte, independent of active transport. We encourage the authors to more thoroughly discuss these caveats. It may also help to present the green and red channels side by side rather than as merged images, to allow readers to assess signal movement and spatial patterns better.
This is a valid point that mirrors the comment of Reviewers 1 and 3. The directional movement of microtubules traveling at ~140 nm/s from nurse cells toward the oocyte via the ring canals was previously reported by Lu et al. (2022) with excellent spatial resolution. Notably, this MT transport was measured using a fusion protein containing the Ens MT-binding domain. We now cite this relevant study in our revised manuscript and have removed this redundant panel in Figure 1.
Reduction of Shot at the anterior cortex• Shot is known to bind strongly to F-actin, and in the Drosophila ovary, its localization typically correlates more closely with F-actin structures than with microtubules, despite being an MT-actin crosslinker. Therefore, the observed reduction of cortical Shot in ens, nin mutants, and Khc-RNAi oocytes is unexpected. It would be important to determine whether cortical F-actin is also disrupted in these conditions, which should be straightforward to assess via phalloidin staining.
As requested by the reviewer, we performed actin staining experiments, which are now presented in a new Figure S5. These data demonstrate that the cortical actin network remains intact in all mutant backgrounds analyzed, ruling out any indirect effect of actin cytoskeleton disruption on the observed phenotypes.
MTs are barely visible in Fig. 3A, which is meant to demonstrate Ens-GFP colocalization with tubulin. Higher-quality images are needed.
The revised version now provides significantly improved images to show the different components examined. Our data show that Ens and Ninein localize at the cell cortex where they co-localize with Shot and Patronin (Figure 2 A-C). In addition, novel images show that Ens extends along microtubules (new Figure 4 A).
MT gradient in stage 9 oocytesIn ens-/-, nin-/-, and Khc-RNAi oocytes, is there any global defect in the stage 9 microtubule gradient? This information would help clarify the extent to which cortical localization defects reflect broader disruptions in microtubule polarity.
We now provide quantitative analysis of microtubule (MT) array organization in novel figures (Figure 3D and Figure 5B). Our data reveal that both Khc RNAi and ens mutant oocytes exhibit severe disruption of MT orientation toward the posterior (new Figure 5B). Importantly, this defect is significantly less pronounced in Nin-/- oocytes, which retain residual ncMTOCs at the cortex (new Figure 3D). This differential phenotype supports our model that cortical ncMTOCs are critical for maintaining proper MT orientation toward the posterior side of the oocyte.
Role of Ninein in cortical anchoringThe requirement for Ninein in cortical anchorage is the least convincing aspect of the manuscript and somewhat disrupts the narrative flow. First, it is unclear whether Ninein exhibits the same oocyte-enriched localization pattern as Ensconsin. Is Ninein detectable in nurse cells? Second, the Ninein antibody signal appears concentrated in a small area of the anterior-lateral oocyte cortex (Fig. 2A), yet Ninein loss leads to reduced Shot signal along a much larger portion of the anterior cortex (Fig. 2F)-a spatial mismatch that weakens the proposed functional relationship. Third, Ninein overexpression results in cortical aggregates that co-localize with Shot, Patronin, and Ensconsin. Are these aggregates functional ncMTOCs? Do microtubules emanate from these foci?
We now provide a more comprehensive analysis of Ninein localization. Similar to Ensconsin (Ens), endogenous Ninein is enriched in the oocyte during the early stages of oocyte development but is also detected in NCs (see modified Figure 2 A and Lasko et al., 2016). Improved imaging of Ninein further shows that the protein partially co-localizes with Ens, and ncMTOCs at the anterior cortex and with Ens-bound MTs (Figure 2B, 2C).
Importantly, loss of Ninein (Nin) only partially reduces the enrichment of Ens in the oocyte (Figure 2E). Both Ens and Kinesin heavy chain (Khc) remain partially functional and continue to target non-centrosomal microtubule-organizing centers (ncMTOCs) to the cortex (Figure 3A). In Nin-/- mutants, a subset of long cortical microtubules (MTs) is present, thereby generating cytoplasmic streaming, although less efficiently than under wild-type (WT) conditions (Figure 3F and 3G). As a non-essential gene, we envisage Ninein as a facilitator of MT organization during oocyte development.
Finally, our new analyses demonstrate that large puncta containing Ninein, Shot, Patronin, and despite their size, appear to be relatively weak nucleation centers (revised Figure S4 E and Video 1). In addition, their presence does not bias overall MT architecture (Figure S4 F) nor impair oocyte development and fertility (Figure S4 G and Table 1).
Inconsistency of Khc^MutEns rescueThe Khc^MutEns variant partially rescues cortical MT formation and restores a slow but measurable cytoplasmic flow yet it fails to rescue Staufen localization (Fig. 5). This raises questions about the consistency and completeness of the rescue. Could the authors clarify this discrepancy or propose a mechanistic rationale?
This is a good point. The cytoplasmic flows (the consequence of cargo transport by Khc on MTs) generated by a constitutively active KhcMutEns in an ens mutant condition, are less efficient than those driven by Khc activated by Ens in a control condition (Figure 6C). The rescued flow is probably not efficient enough to completely rescue the Staufen localization at stage 10.
Additionally, this KhcMutEns variant rescues the viability of embryos from Khc27 mutant germline clones oocytes but not from ens mutants (Table1). One hypothesis is that Ens harbors additional functions beyond Khc activation.
This incomplete rescue of Ens by an active Khc variant could also be the consequence of the “paradox of co-dependence”: Kinesin-1 also transport the antagonizing motor Dynein that promotes cargo transport in opposite directions (Hancock et al., 2016). The phenotype of a gain of function variant is therefore complex to interpret. Consistent with this, both KhcMutEns-GFP and KhcDhinge2 two active Khc only rescues partially centrosome transport in ens mutant Neural Stem Cells (Figure S10).
Minor points: 1. The pUbi-attB-Khc-GFP vector was used to generate the Khc^MutEns transgenic line, presumably under control of the ubiquitous ubi promoter. Could the authors specify which attP landing site was used? Additionally, are the transgenic flies viable and fertile, given that Kinesin-1 is hyperactive in this construct?
All transgenic constructs were integrated at defined genomic landing sites to ensure controlled expression levels. Specifically, both GFP-tagged KhcWT and KhcMutEns were inserted at the VK05 (attP9A) site using PhiC31-mediated integration. Full details of the landing sites are provided in the Materials and Methods section. Both transgenic flies are homozygous lethal and the transgenes are maintained over TM6B balancers.
On page 11 (Discussion, section titled "A dual Ensconsin oocyte enrichment mechanism achieves spatial relief of Khc inhibition"), the statement "many mutations in Kif5A are causal of human diseases" would benefit from a brief clarification. Since not all readers may be familiar with kinesin gene nomenclature, please indicate that KIF5A is one of the three human homologs of Kinesin heavy chain.
We clarified this point in the revised version (lane 465-466).
On page 16 (Materials and Methods, "Immunofluorescence in fly ovaries"), the sentence "Ovaries were mounted on a slide with ProlonGold medium with DAPI (Invitrogen)" should be corrected to "ProLong Gold."
This is corrected.
Significance
This study shows that enrichment of MAP7/ensconsin in the oocyte is the mechanism of kinesin-1 activation there and is important for cytoplasmic streaming and localization non-centrosomal microtubule-organizing centers to the oocyte cortex
We thank the reviewers for the accurate review of our manuscript and their positive feed-back.
Reviewer #3
Evidence, reproducibility and clarity
The manuscript of Berisha et al., investigates the role of Ensconsin (Ens), Kinesin-1 and Ninein in organisation of microtubules (MT) in Drosophila oocyte. At stage 9 oocytes Kinesin-1 transports oskar mRNA, a posterior determinant, along MT that are organised by ncMTOCs. At stage 10b, Kinesin-1 induces cytoplasmic advection to mix the contents of the oocyte. Ensconsin/Map7 is a MT associated protein (MAP) that uses its MT-binding domain (MBD) and kinesin binding domain (KBD) to recruit Kinesin-1 to the microtubules and to stimulate the motility of MT-bound Kinesin-1. Using various new Ens transgenes, the authors demonstrate the requirement of Ens MBD and Ninein in Ens localisation to the oocyte where Ens activates Kinesin-1 using its KBD. The authors also claim that Ens, Kinesin-1 and Ninein are required for the accumulation of ncMTOCs at the oocyte cortex and argue that the detachment of the ncMTOCs from the cortex accounts for the reduced localisation of oskar mRNA at stage 9 and the lack of cytoplasmic streaming at stage 10b. Although the manuscript contains several interesting observations, the authors' conclusions are not sufficiently supported by their data. The structure function analysis of Ensconsin (Ens) is potentially publishable, but the conclusions on ncMTOC anchoring and cytoplasmic streaming not convincing.
We are grateful that the regulation of Khc activity by MAP7 was well received by all reviewers. While our study focuses on Drosophila oogenesis, we believe this mechanism may have broader implications for understanding kinesin regulation across biological systems.
For the novel function of the MAP7/Khc complex in organizing its own microtubule networks through ncMTOC recruitment, we have carefully considered the reviewers' constructive recommendations. We now provide additional experimental evidence supporting a model of flux self-amplification in which ncMTOC recruitment plays a key role. It is well established that cytoplasmic flows are essential for posterior localization of cell fate determinants at stage 10B. Slow flows have also been described at earlier oogenesis stages by the groups of Saxton and St Johnston. Building on these early publications and our new experiments, we propose that these flows are essential to promote a positive feedback loop that reinforces ncMTOC recruitment and MT organization (Figure 7).
1) The main conclusion of the manuscript is that "MT advection failure in Khc and ens in late oogenesis stems from defective cortical ncMTOCs recruitment". This completely overlooks the abundant evidence that Kinesin-1 directly drives cytoplasmic streaming by transporting vesicles and microtubules along microtubules, which then move the cytoplasm by advection (Palacios et al., 2002; Serbus et al, 2005; Lu et al, 2016). Since Kinesin-1 generates the flows, one cannot conclude that the effect of khc and ens mutants on cortical ncMTOC positioning has any direct effect on these flows, which do not occur in these mutants.
We regret the lack of clarity of the first version of the manuscript and some missing references. We propose a model in which the Kinesin-1- dependent slow flows (described by Serbus/Saxton and Palacios/StJohnston) play a central role in amplifying ncMTOC anchoring and cortical MT network formation (see model in the new Figure 7).
2) The authors claim that streaming phenotypes of ens and khs mutants are due to a decrease in microtubule length caused by the defective localisation of ncMTOCs. In addition to the problem raised above, However, I am not convinced that they can make accurate measurements of microtubule length from confocal images like those shown in Figure 4. Firstly, they are measuring the length of bundles of microtubules and cannot resolve individual microtubules. This problem is compounded by the fact that the microtubules do not align into parallel bundles in the mutants. This will make the "microtubules" appear shorter in the mutants. In addition, the alignment of the microtubules in wild-type allows one to choose images in which the microtubule lie in the imaging plane, whereas the more disorganized arrangement of the microtubules in the mutants means that most microtubules will cross the imaging plane, which precludes accurate measurements of their length.
As mentioned by Reviewer 4, we have been transparent with the methodology, and the limitations that were fully described in the material and methods section.
Cortical microtubules in oocytes are highly dynamic and move rapidly, making it technically impossible to capture their entire length using standard Z-stack acquisitions. We therefore adopted a compromise approach: measuring microtubules within a single focal plane positioned just below the oocyte cortex. This strategy is consistent with established methods in the field, such as those used by Parton et al. (2011) to track microtubule plus-end directionality. To avoid overinterpretation, we explicitly refer to these measurements as "minimum detectable MT length," acknowledging that microtubules may extend beyond the focal plane, particularly at stage 10, where long, tortuous bundles frequently exit the plane of focus. These methodological considerations and potential biases are clearly described in the Materials and Methods section and the text now mentions the possible disorganization of the MT network in the mutant conditions (lane 272-273).
In this revised version, we now provide complementary analyses of MT network organization.Beyond length measurements (and the mentioned limitations), we also quantified microtubule network orientation at stage 9, assessing whether cortical microtubules are preferentially oriented toward the posterior axis as observed in controls (revised Figure 3D and Figure 5B). While this analysis is also subject to the same technical limitations, it reveals a clear biological difference: microtubules exhibit posterior-biased orientation in control oocytes similar to a previous study (Parton et al., 2011) but adopt a randomized orientation in Nin-/-, ens, and Khc RNAi-depleted oocytes (revised Figure 3D and Figure 5B).
Taken together, these complementary approaches, despite their technical constraints, provide convergent evidence for the role of the Khc/Ens complex in organizing cortical microtubule networks during oogenesis.
3) "To investigate whether the presence of these short microtubules in ens and Khc RNAi oocytes is due to defects in microtubule anchoring or is also associated with a decrease in microtubule polymerization at their plus ends, we quantified the velocity and number of EB1comets, which label growing microtubule plus ends (Figure S3)." I do not understand how the anchoring or not of microtubule minus ends to the cortex determines how far their plus ends grow, and these measurements fall short of showing that plus end growth is unaffected. It has already been shown that the Kinesin-1-dependent transport of Dynactin to growing microtubule plus ends increases the length of microtubules in the oocyte because Dynactin acts as an anti-catastrophe factor at the plus ends. Thus, khc mutants should have shorter microtubules independently of any effects on ncMTOC anchoring. The measurements of EB1 comet speed and frequency in FigS2 will not detect this change and are not relevant for their claims about microtubule length. Furthermore, the authors measured EB1 comets at stage 9 (where they did not observe short MT) rather than at stage 10b. The authors' argument would be better supported if they performed the measurements at stage 10b.
We thank the reviewer for raising this important point. The short microtubule (MT) length observed at stage 10B could indeed result from limited plus-end growth. Unfortunately, we were unable to test this hypothesis directly: strong endogenous yolk autofluorescence at this stage prevented reliable detection of Eb1-GFP comets, precluding velocity measurements.
At least during stage 9, our data demonstrate that MT nucleation and polymerization rates are not reduced in both KhcRNAi and ens mutant conditions, indicating that the observed MT alterations must arise through alternative mechanisms.
In the discussion, we propose the following interconnected explanations, supported by recent literature and the reviewers’ suggestions:
1- Reduced MT rescue events. Two seminal studies from the Verhey and Aumeier laboratories have shown that constitutively active Kinesin-1 induces MT lattice damage (Budaitis et al., 2022), which can be repaired through GTP-tubulin incorporation into "rescue shafts" that promote MT rescue (Andreu-Carbo et al., 2022). Extrapolating from these findings, loss of Kinesin-1 activity could plausibly reduce rescue shaft formation, thereby decreasing MT stability. While challenging to test directly in our system, this mechanism provides a plausible framework for the observed phenotype.
2- Impaired transport of stabilizing factors. As that reviewer astutely points out, Khc transports the dynactin complex, an anti-catastrophe factor, to MT plus ends (Nieuwburg et al., 2017). Loss of this transport could further compromise MT plus end stability. We now discuss this important mechanism in the revised manuscript.
3- Loss of cortical ncMTOCs. Critically, our new quantitative analyses (revised Figure 3 and Figure 5) also reveal defective anteroposterior orientation of cortical MTs in mutant conditions. These experiments suggest that Ens/Khc-mediated localization of ncMTOCs to the cortex is essential for proper MT network organization, and possibly minus-end stabilization as suggested in several studies (Feng et al., 2019, Goodwin and Vale, 2011, Nashchekin et al., 2016).
Altogether, we now propose an integrated model in which MT reduction and disorganization may result from multiple complementary mechanisms operating downstream of Kinesin-1/Ensconsin loss. While some aspects remain difficult to test directly in our in vivo system, the convergence of our data with recent mechanistic studies provides an interesting conceptual framework. The Discussion has been revised to reflect this comprehensive view in a dedicated paragraph (“A possible regulation of MT dynamics in the oocyte at both plus end minus MT ends by Ens and Khc” lane 415-432).
4) The Shot overexpression experiments presented in Fig.3 E-F, Fig.4D and TableS1 are very confusing. Originally , the authors used Shot-GFP overexpression at stage 9 to show that there is a decrease of ncMTOCs at the cortex in ens mutants (Fig.3 E-F) and speculated that this caused the defects in MT length and cytoplasmic advection at stage 10B. However the authors later state on page 8 that : "Shot overexpression (Shot OE) was sufficient to rescue the presence of long cortical MTs and ooplasmic advection in most ens oocytes (9/14), resembling the patterns observed in controls (Figures 4B right panel and 4D). Moreover, while ens females were fully sterile, overexpression of Shot was sufficient to restore that loss of fertility (Table S1)". Is this the same UAS Shot-GFP and VP16 Gal4 used in both experiments? If so, this contradictions puts the authors conclusions in question.
This is an important point that requires clarification regarding our experimental design.
The Shot-YFP construct is a genomic insertion on chromosome 3. The ens mutation is also located on chromosome 3 and we were unable to recombine this transgene with the ens mutant for live quantification of cortical Shot. To circumvent this technical limitation, we used a UAS-Shot.L(C)-GFP transgenic construct driven by a maternal driver, expressed in both wild-type (control) and ens mutant oocytes. We validated that the expression level and subcellular localization of UAS-Shot.L(C)-GFP were comparable to those of the genomic Shot-YFP (new Figure S8 A and B).
From these experiments, we drew two key conclusions. First, cortical Shot.L(C)-GFP is less abundant in ens mutant oocytes compared to wild-type (the quantification has been removed from this version). Second, despite this reduced cortical accumulation, Shot.L(C)-GFP expression partially rescues ooplasmic flows and microtubule streaming in stage 10B ens mutant oocytes, and restores fertility to ens mutant females.
5) The authors based they conclusions about the involvement of Ens, Kinesin-1 and Ninein in ncMTOC anchoring on the decrease in cortical fluorescence intensity of Shot-YFP and Patronin-YFP in the corresponding mutant backgrounds. However, there is a large variation in average Shot-YFP intensity between control oocytes in different experiments. In Fig. 2F-G the average level of Shot-YFP in the control sis 130 AU while in Fig.3 G-H it is only 55 AU. This makes me worry about reliability of such measurements and the conclusions drawn from them.
To clarify this point, we have harmonized the method used to quantify the Shot-YFP signals in Figure 4E with the methodology used in Figure 3B, based on the original images. The levels are not strictly identical (Control Figure 2 B: 132.7+/-36.2 versus Control Figure 4 E: 164.0+/- 37.7). These differences are usual when experiments are performed at several-month intervals and by different users.
6) The decrease in the intensity of Shot-YFP and Patronin-YFP cortical fluorescence in ens mutant oocytes could be because of problems with ncMTOC anchoring or with ncMTOCs formation. The authors should find a way to distinguish between these two possibilities. The authors could express Ens-Mut (described in Sung et al 2008), which localises at the oocyte posterior and test whether it recruits Shot/Patronin ncMTOCs to the posterior.
We tried to obtain the fly stocks described in the 2008 paper by contacting former members of Pernille Rørth's laboratory. Unfortunately, we learned that the lab no longer exists and that all reagents, including the requested stocks, were either discarded or lost over time. To our knowledge, these materials are no longer available from any source. We regret that this limitation prevented us from performing the straightforward experiments suggested by the reviewer using these specific tools.
7) According to the Materials and Methods, the Shot-GFP used in Fig.3 E-F and Fig.4 was the BDSC line 29042. This is Shot L(C), a full-length version of Shot missing the CH1 actin-binding domain that is crucial for Shot anchoring to the cortex. If the authors indeed used this version of Shot-GFP, the interpretation of the above experiments is very difficult.
The Shot.L(C) isoform lacks the CH1 domain but retains the CH2 actin-binding motif. Truncated proteins with this domain and fused to GST retains a weak ability to bind actin in vitro. Importantly, the function of this isoform is context-dependent: it cannot rescue shot loss-of-function in neuron morphogenesis but fully restores Shot-dependent tracheal cell remodeling (Lee and Kolodziej, 2002).
In our experiments, when the Shot.L(C) isoform was expressed under the control of a maternal driver, its localization to the oocyte cortex was comparable to that of the genomic Shot-YFP construct (new Figure S8). This demonstrates unambiguously that the CH1 domain is dispensable for Shot cortical localization in oocytes, and that CH2-mediated actin binding is sufficient for this localization. Of note, a recent study showed that actin network are not equivalent highlighting the need for specific Shot isoforms harboring specialized actin-binding domain (Nashchekin et al., 2024).
We note that the expression level of Shot.L(C)-GFP in the oocyte appeared slightly lower than that of Shot-YFP (expressed under endogenous Shot regulatory sequences), as assessed by Western blot (Figure S8 A).
Critically, Shot.L(C)-GFP expression was substantially lower than that of Shot.L(A)-GFP (that harbored both the CH1 and CH2 domain). Shot.L(A)-GFP was overexpressed (Figure 8 A) and ectopically localized on MTs in both nurse cells and the ooplasm (Figure S8 B middle panel and arrow). These observations are in agreement that the Shot.L(C)-GFP rescue experiment was performed at near-physiological expression levels, strengthening the validity of our conclusions.
8) Page 6 "converted in NCs, in a region adjacent to the ring canals, Dendra-Ens-labeled MTs were found in the oocyte compartment indicating they are able to travel from NC toward the oocyte through ring canals". I have difficulty seeing the translocation of MT through the ring canals. Perhaps it would be more obvious with a movie/picture showing only one channel. Considering that f Dendra-Ens appears in the oocyte much faster than MT transport through ring canals (140nm/s, Lu et al 2022), the authors are most probably observing the translocation of free Ens rather than Ens bound to MT. The authors should also mention that Ens movement from the NC to the oocyte has been shown before with Ens MBD in Lu et al 2022 with better resolution.
We fully agree on the caveat mentioned by this reviewer: we may observe the translocation of free Dendra-Ensconsin. The experiment, was removed and replaced by referring to the work of the Gelfand lab. The movement of MTs that travel at ~140 nm/s between nurse cells toward the oocyte through the Ring Canals was reported before by Lu et al. (2022) with a very good resolution. Notably, this directional directed movement of MTs was measured using a fusion protein encompassing Ens MT-binding domain. We decided to remove this inclusive experiment and rather refer to this relevant study.
9) Page 6: The co-localization of Ninein with Ens and Shot at the oocyte cortex (Figure 2A). I have difficulty seeing this co-localisation. Perhaps it would be more obvious in merged images of only two channels and with higher resolution images
10) "a pool of the Ens-GFP co-localized with Ch-Patronin at cortical ncMTOCs at the anterior cortex (Figure 3A)". I also have difficulty seeing this.
We have performed new high-resolution acquisitions that provide clearer and more convincing evidence for the localization cortical distribution of these proteins (revised Figure 2A-2C and Figure 4A). These improved images demonstrate that Ens, Ninein, Shot, and Patronin partially colocalize at cortical ncMTOCs, as initially proposed. Importantly, the new data also reveal a spatial distinction: while Ens localizes along microtubules extending from these cortical sites, Ninein appears confined to small cytoplasmic puncta adjacent but also present on cortical microtubules.
11) "Ninein co-localizes with Ens at the oocyte cortex and partially along cortical microtubules, contributing to the maintenance of high Ens protein levels in the oocyte and its proper cortical targeting". I could not find any data showing the involvement of Ninein in the cortical targeting of Ens.
We found decreased Ens localization to MTs and to the cell cortex region (new Figure S3 A-B).
12) "our MT network analyses reveal the presence of numerous short MTs cytoplasmic clustered in an anterior pattern." "This low cortical recruitment of ncMTOCs is consistent with poor MT anchoring and their cytoplasmic accumulation." I could not find any data showing that short cortical MT observed at stage 10b in ens mutant and Khc RNAi were cytoplasmic and poorly anchored.
The sentence was removed from the revised manuscript.
13) "The egg chamber consists of interconnected cells where Dynein and Khc activities are spatially separated. Dynein facilitates transport from NCs to the oocyte, while Khc mediates both transport and advection within the oocyte." Dynein is involved in various activities in the oocyte. It anchors the oocyte nucleus and transports bcd and grk mRNA to mention a few.
The text was amended to reflect Dynein involvement in transport activities in the oocyte, with the appropriate references (lane 105-107).
14) The cartoons in Fig.2H and 3I exaggerate the effect of Ninein and Ens on cortical ncMTOCs. According to the corresponding graphs, there is a 20 and 50% decrease in each case.
New cartoons (now revised Figure 3E and 4F), are amended to reflect the ncMTOC values but also MT orientation (Figure 3E).
Significance
Given the important concerns raised, the significance of the findings is difficult to assess at this stage.
We sincerely thank the reviewer for their thorough evaluation of our manuscript. We have carefully addressed their concerns through substantial new experiments and analyses. We hope that the revised manuscript, in its current form, now provides the clarifications and additional evidence requested, and that our responses demonstrate the significance of our findings.
Reviewer #4 (Evidence, reproducibility and clarity (Required)):
Summary: This manuscript presents an investigation into the molecular mechanisms governing spatial activation of Kinesin-1 motor protein during Drosophila oogenesis, revealing a regulatory network that controls microtubule organization and cytoplasmic transport. The authors demonstrate that Ensconsin, a MAP7 family protein and Kinesin-1 activator, is spatially enriched in the oocyte through a dual mechanism involving Dynein-mediated transport from nurse cells and cortical maintenance by Ninein. This spatial enrichment of Ens is crucial for locally relieving Kinesin-1 auto-inhibition. The Ens/Khc complex promotes cortical recruitment of non-centrosomal microtubule organizing centers (ncMTOCs), which are essential for anchoring microtubules at the cortex, enabling the formation of long, parallel microtubule streams or "twisters" that drive cytoplasmic advection during late oogenesis. This work establishes a paradigm where motor protein activation is spatially controlled through targeted localization of regulatory cofactors, with the activated motor then participating in building its own transport infrastructure through ncMTOC recruitment and microtubule network organization.
There's a lot to like about this paper! The data are generally lovely and nicely presented. The authors also use a combination of experimental approaches, combining genetics, live and fixed imaging, and protein biochemistry.
We thank the reviewer for this enthusiastic and supportive review, which helped us further strengthen the manuscript.
Concerns: Page 6: "to assay if elevation of Ninein levels was able to mis-regulate Ens localization, we overexpressed a tagged Ninein-RFP protein in the oocyte. At stage 9 the overexpressed Ninein accumulated at the anterior cortex of the oocyte and also generated large cortical aggregates able to recruit high levels of Ens (Figures 2D and 2H)... The examination of Ninein/Ens cortical aggregates obtained after Ninein overexpression showed that these aggregates were also able to recruit high levels of Patronin and Shot (Figures 2E and 2H)." Firstly, I'm not crazy about the use of "overexpressed" here, since there isn't normally any Ninein-RFP in the oocyte. In these experiments it has been therefore expressed, not overexpressed. Secondly, I don't understand what the reader is supposed to make of these data. Expression of a protein carrying a large fluorescent tag leads to large aggregates (they don't look cortical to me) that include multiple proteins - in fact, all the proteins examined. I don't understand this to be evidence of anything in particular, except that Ninein-RFP causes the accumulation of big multi-protein aggregates. While I can understand what the authors were trying to do here, I think that these data are inconclusive and should be de-emphasized.
We have revised the manuscript by replacing overexpressed with expressed (lanes 211 and 212). In addition, we now provide new localization data in both cortical (new Figure S4 A, top) and medial focal planes (new Figure S4 A, bottom), demonstrating that Ninein puncta (the word used in Rosen et al, 2019), rather than aggregates are located cortically. We also show that live IRP-labelled MTs do not colocalize with Ninein-RFP puncta. In light of the new experiments and the comments from the other reviewers, the corresponding text has been revised and de-emphasized accordingly.
Page 7: "Co-immunoprecipitations experiments revealed that Patronin was associated with Shot-YFP, as shown previously (Nashchekin et al., 2016), but also with EnsWT-GFP, indicating that Ens, Shot and Patronin are present in the same complex (Figure 3B)." I do not agree that association between Ens-GFP and Patronin indicates that Ens is in the same complex as Shot and Patronin. It is also very possible that there are two (or more) distinct protein complexes. This conclusion could therefore be softened. Instead of "indicating" I suggest "suggesting the possibility."
We have toned down this conclusion and indicated “suggesting the possibility” (lane 238-239).
Page 7: "During stage 9, the average subcortical MT length, taken at one focal plane in live oocytes (see methods)..." I appreciate that the authors have been careful to describe how they measured MT length, as this is a major point for interpretation. I think the reader would benefit from an explanation of why they decided to measure in only one focal plane and how that decision could impact the results.
We appreciate this helpful suggestion. Cortical microtubules are indeed highly dynamic and extend in multiple directions, including along the Z-axis. Moreover, their diameter is extremely small (approximately 25 nm), making it technically challenging to accurately measure their full length with high resolution using our Zeiss Airyscan confocal microscope (over several, microns): the acquisition of Z-stacks is relatively slow and therefore not well suited to capturing the rapid dynamics of these microtubules. Consequently, our length measurements represent a compromise and most likely underestimate the actual lengths of microtubules growing outside the focal plane. We note that other groups have encountered similar technical limitations (Parton et al., 2011).
Page 7: "... the MTs exhibited an orthogonal orientation relative to the anterior cortex (Figures 4A left panels, 4C and 4E)." This phenotype might not be obvious to readers. Can it be quantified?
We have now analyzed the orientation of microtubules (MTs) along the dorso-ventral axis. Our analysis shows that ens, Khc RNAi oocytes (new Figure 5B), and, to a lesser extent, Nin mutant oocytes (new Figure 3D), display a more random MT orientation compared to wild-type (WT) oocytes. In WT oocytes, MTs are predominantly oriented toward the posterior pole, consistent with previous findings (Parton et al., 2011).
Page 8: "Altogether, the analyses of Ens and Khc defective oocytes suggested that MT organization defects during late oogenesis (stage 10B) were caused by an initial failure of ncMTOCs to reach the cell cortex. Therefore, we hypothesized that overexpression of the ncMTOC component Shot could restore certain aspects of microtubule cortical organization in ens-deficient oocytes. Indeed, Shot overexpression (Shot OE) was sufficient to rescue the presence of long cortical MTs and ooplasmic advection in most ens oocytes (9/14)..." The data are clear, but the explanation is not. Can the authors please explain why adding in more of an ncMTOC component (Shot) rescues a defect of ncMTOC cortical localization?
We propose that cytoplasmic ncMTOCs can bind the cell cortex via the Shot subunit that is so far the only component that harbors actin-binding motifs. Therefore, we propose that elevating cytoplasmic Shot increase the possibility of Shot to encounter the cortex by diffusion when flows are absent. This is now explained lane 282-285.
I'm grateful to the authors for their inclusion of helpful diagrams, as in Figures 1G and 2H. I think the manuscript might benefit from one more of these at the end, illustrating the ultimate model.
We have carefully considered and followed the reviewer’s suggestions. In response, we have included a new figure illustrating our proposed model: the recruitment of ncMTOCs to the cell cortex through low Khc-mediated flows at stage 9 enhances cortical microtubule density, which in turn promotes self-amplifying flows (new Figure 7, panels A to C). Note that this Figure also depicts activation of Khc by loss of auto-inhibition (Figure 7, panel D).
I'm sorry to say that the language could use quite a bit of polishing. There are missing and extraneous commas. There is also regular confusion between the use of plural and singular nouns. Some early instances include:
- Page 3: thought instead of "thoughted."
- Page 5: "A previous studies have revealed"
- Page 5: "A significantly loss"
- Page 6: "troughs ring canals" should be "through ring canals"
- Page 7: lives stage 9 oocytes
- Page 7: As ens and Khc RNAi oocytes exhibits
- Page 7: we examined in details
- Page 7: This average MT length was similar in Khc RNAi and ens mutant oocyte..
We apologize for errors. We made the appropriate corrections of the manuscript.
Reviewer #4 (Significance (Required)):
This work makes a nice conceptual advance by showing that motor activation controls its own transport infrastructure, a paradigm that could extend to other systems requiring spatially regulated transport.
We thank the reviewers for their evaluation of the manuscript and helpful comments.
Note: This preprint has been reviewed by subject experts for Review Commons. Content has not been altered except for formatting.
Learn more at Review Commons
Summary: This manuscript presents an investigation into the molecular mechanisms governing spatial activation of Kinesin-1 motor protein during Drosophila oogenesis, revealing a regulatory network that controls microtubule organization and cytoplasmic transport. The authors demonstrate that Ensconsin, a MAP7 family protein and Kinesin-1 activator, is spatially enriched in the oocyte through a dual mechanism involving Dynein-mediated transport from nurse cells and cortical maintenance by Ninein. This spatial enrichment of Ens is crucial for locally relieving Kinesin-1 auto-inhibition. The Ens/Khc complex promotes cortical recruitment of non-centrosomal microtubule organizing centers (ncMTOCs), which are essential for anchoring microtubules at the cortex, enabling the formation of long, parallel microtubule streams or "twisters" that drive cytoplasmic advection during late oogenesis. This work establishes a paradigm where motor protein activation is spatially controlled through targeted localization of regulatory cofactors, with the activated motor then participating in building its own transport infrastructure through ncMTOC recruitment and microtubule network organization.
There's a lot to like about this paper! The data are generally lovely and nicely presented. The authors also use a combination of experimental approaches, combining genetics, live and fixed imaging, and protein biochemistry.
Concerns:
Page 6: "to assay if elevation of Ninein levels was able to mis-regulate Ens localization, we overexpressed a tagged Ninein-RFP protein in the oocyte. At stage 9 the overexpressed Ninein accumulated at the anterior cortex of the oocyte and also generated large cortical aggregates able to recruit high levels of Ens (Figures 2D and 2H)... The examination of Ninein/Ens cortical aggregates obtained after Ninein overexpression showed that these aggregates were also able to recruit high levels of Patronin and Shot (Figures 2E and 2H)." Firstly, I'm not crazy about the use of "overexpressed" here, since there isn't normally any Ninein-RFP in the oocyte. In these experiments it has been therefore expressed, not overexpressed. Secondly, I don't understand what the reader is supposed to make of these data. Expression of a protein carrying a large fluorescent tag leads to large aggregates (they don't look cortical to me) that include multiple proteins - in fact, all the proteins examined. I don't understand this to be evidence of anything in particular, except that Ninein-RFP causes the accumulation of big multi-protein aggregates. While I can understand what the authors were trying to do here, I think that these data are inconclusive and should be de-emphasized.
Page 7: "Co-immunoprecipitations experiments revealed that Patronin was associated with Shot-YFP, as shown previously (Nashchekin et al., 2016), but also with EnsWT-GFP, indicating that Ens, Shot and Patronin are present in the same complex (Figure 3B)." I do not agree that association between Ens-GFP and Patronin indicates that Ens is in the same complex as Shot and Patronin. It is also very possible that there are two (or more) distinct protein complexes. This conclusion could therefore be softened. Instead of "indicating" I suggest "suggesting the possibility."
Page 7: "During stage 9, the average subcortical MT length, taken at one focal plane in live oocytes (see methods)..." I appreciate that the authors have been careful to describe how they measured MT length, as this is a major point for interpretation. I think the reader would benefit from an explanation of why they decided to measure in only one focal plane and how that decision could impact the results.
Page 7: "... the MTs exhibited an orthogonal orientation relative to the anterior cortex (Figures 4A left panels, 4C and 4E)." This phenotype might not be obvious to readers. Can it be quantified?
Page 8: "Altogether, the analyses of Ens and Khc defective oocytes suggested that MT organization defects during late oogenesis (stage 10B) were caused by an initial failure of ncMTOCs to reach the cell cortex. Therefore, we hypothesized that overexpression of the ncMTOC component Shot could restore certain aspects of microtubule cortical organization in ens-deficient oocytes. Indeed, Shot overexpression (Shot OE) was sufficient to rescue the presence of long cortical MTs and ooplasmic advection in most ens oocytes (9/14)..." The data are clear, but the explanation is not. Can the authors please explain why adding in more of an ncMTOC component (Shot) rescues a defect of ncMTOC cortical localization?
I'm grateful to the authors for their inclusion of helpful diagrams, as in Figures 1G and 2H. I think the manuscript might benefit from one more of these at the end, illustrating the ultimate model.
I'm sorry to say that the language could use quite a bit of polishing. There are missing and extraneous commas. There is also regular confusion between the use of plural and singular nouns. Some early instances include:
This work makes a nice conceptual advance by showing that motor activation controls its own transport infrastructure, a paradigm that could extend to other systems requiring spatially regulated transport.
Note: This preprint has been reviewed by subject experts for Review Commons. Content has not been altered except for formatting.
Learn more at Review Commons
The manuscript of Berisha et al., investigates the role of Esconsin (Ens), Kinesin-1 and Ninein in organisation of microtubules (MT) in Drosophila oocyte. At stage 9 oocytes Kinesin-1 transports oskar mRNA, a posterior determinant, along MT that are organised by ncMTOCs. At stage 10b, Kinesin-1 induces cytoplasmic advection to mix the contents of the oocyte. Ensconsin/Map7 is a MT associated protein (MAP) that uses its MT-binding domain (MBD) and kinesin binding domain (KBD) to recruit Kinesin-1 to the microtubules and to stimulate the motility of MT-bound Kinesin-1. Using various new Ens transgenes, the authors demonstrate the requirement of Ens MBD and Ninein in Ens localisation to the oocyte where Ens activates Kinesin-1 using its KBD. The authors also claim that Ens, Kinesin-1 and Ninein are required for the accumulation of ncMTOCs at the oocyte cortex and argue that the detachment of the ncMTOCs from the cortex accounts for the reduced localisation of oskar mRNA at stage 9 and the lack of cytoplasmic streaming at stage 10b.
Although the manuscript contains several interesting observations, the authors' conclusions are not sufficiently supported by their data. The structure function analysis of Ensconsin (Ens) is potentially publishable, but the conclusions on ncMTOC anchoring and cytoplasmic streaming not convincing
Given the important concerns raised, the significance of the findings is difficult to assess at this stage.
Note: This preprint has been reviewed by subject experts for Review Commons. Content has not been altered except for formatting.
Learn more at Review Commons
In this manuscript, Berisha et al. investigate how microtubule (MT) organization is spatially regulated during Drosophila oogenesis. The authors identify a mechanism in which the Kinesin-1 activator Ensconsin/MAP7 is transported by dynein and anchored at the oocyte cortex via Ninein, enabling localized activation of Kinesin-1. Disruption of this pathway impairs ncMTOC recruitment and MT anchoring at the cortex. The authors combine genetic manipulation with high-resolution microscopy and use three key readouts to assess MT organization during mid-to-late oogenesis: cortical MT formation, localization of posterior determinants, and ooplasmic streaming. Notably, Kinesin-1, in concert with its activator Ens/MAP7, contributes to organizing the microtubule network it travels along. Overall, the study presents interesting findings, though we have several concerns we would like the authors to address.
Ensconsin enrichment in the oocyte
Minor points:
This study shows that enrichment of MAP7/ensconsin in the oocyte is the mechanism of kinesin-1 activation there and is important for cytoplasmic streaming and localization non-centrosomal microtubule-organizing centers to the oocyte cortex
Note: This preprint has been reviewed by subject experts for Review Commons. Content has not been altered except for formatting.
Learn more at Review Commons
This paper addresses a very interesting problem of non-centrosomal microtubule organization in developing Drosophila oocytes. Using genetics and imaging experiments, the authors reveal an interplay between the activity of kinesin-1, together with its essential cofactor Ensconsin, and microtubule organization at the cell cortex by the spectraplakin Shot, minus-end binding protein Patronin and Ninein, a protein implicated in microtubule minus end anchoring. The authors demonstrate that the loss of Ensconsin affects the cortical accumulation non-centrosomal microtubule organizing center (ncMTOC) proteins, microtubule length and vesicle motility in the oocyte, and show that this phenotype can be rescued by constitutively active kinesin-1 mutant, but not by Ensconsin mutants deficient in microtubule or kinesin binding. The functional connection between Ensconsin, kinesin-1 and ncMTOCs is further supported by a rescue experiment with Shot overexpression. Genetics and imaging experiments further implicate Ninein in the same pathway. These data are a clear strength of the paper; they represent a very interesting and useful addition to the field.
The weaknesses of the study are two-fold. First, the paper seems to lack a clear molecular model, uniting the observed phenomenology with the molecular functions of the studied proteins. Most importantly, it is not clear how kinesin-based plus-end directed transport contributes to cortical localization of ncMTOCs and regulation of microtubule length.
Second, not all conclusions and interpretations in the paper are supported by the presented data. Below is a list of specific comments, outlining the concerns, in the order of appearance in the paper/figures.
Minor comment: Note that a "ratio" (Figure 2C) is just a ratio, and should not be expressed in arbitrary units. 3. Figure 3B: immunoprecipitation results cannot be interpreted because the immunoprecipitated proteins (GFP, Ens-GFP, Shot-YFP) are not shown. It is also not clear that this biochemical experiment is useful. If the authors would like to suggest that Ensconsin directly binds to Patronin, the interaction would need to be properly mapped at the protein domain level. 4. One of the major phenotypes observed by the authors in Ens mutant is the loss of long microtubules. The authors make strong conclusions about the independence of this phenotype from the parameters of microtubule plus-end growth, but in fact, the quality of their data does not allow to make such a conclusion, because they only measured the number of EB1 comets and their growth rate but not the catastrophe, rescue or pausing frequency. Note that kinesin-1 has been implicated in promoting microtubule damage and rescue (doi: 10.1016/j.devcel.2021). In the absence of such measurements, one cannot conclude whether short microtubules arise through defects in the minus-end, plus-end or microtubule shaft regulation pathways. It is important to note in that a spectraplakin, like Shot, can potentially affect different pathways, particularly when overexpressed. Unjustified conclusions should be removed: the authors do not provide sufficient data to conclude that "ens and Khc oocytes MT organizational defects are caused by decreased ncMTOC cortical anchoring", because the actual cortical microtubule anchoring was not measured.
Minor comment: Microtubule growth velocity must be expressed in units of length per time, to enable evaluating the quality of the data, and not as a normalized value. 5. A significant part of the Discussion is dedicated to the potential role of Ensconsin in cortical microtubule anchoring and potential transport of ncMTOCs by kinesin. It is obviously fine that the authors discuss different theories, but it would be very helpful if the authors would first state what has been directly measured and established by their data, and what are the putative, currently speculative explanations of these data.
Minor comment: The writing and particularly the grammar need to be significantly improved throughout, which should be very easy with current language tools. Examples: "ncMTOCs recruitment" should be "ncMTOC recruitment"; "Vesicles speed" should be "Vesicle speed", "Nin oocytes harbored a WT growth,"- unclear what this means, etc. Many paragraphs are very long and difficult to read. Making shorter paragraphs would make the authors' line of thought more accessible to the reader.
This paper represents significant advance in understanding non-centrosomal microtubule organization in general and in developing Drosophila oocytes in particular by connecting the microtubule minus-end regulation pathway to the Kinesin-1 and Ensconsin/MAP7-dependent transport. The genetics and imaging data are of good quality, are appropriately presented and quantified. These are clear strengths of the study which will make it interesting to researchers studying the cytoskeleton, microtubule-associated proteins and motors, and fly development.
The weaknesses of this study are due to the lack of clarity of the overall molecular model, which would limit the impact of the study on the field. Some interpretations are not sufficiently supported by data, but this can be solved by more precise and careful writing, without extensive additional experimentation.
My expertise is cell biology and biochemistry of the microtubule cytoskeleton, including both microtubule-associated proteins and microtubule motors.
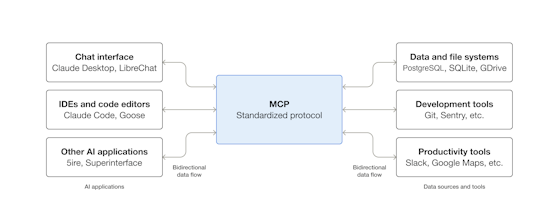
What is the Model Context Protocol (MCP)?
By pairing the book with the film, we wanted the students to have a sense both of the harsh realities of urban schools and of the possibilities to transform and transcend those realities.
By pairing the book Savage Inequalities with the film Stand and Deliver, the authors wanted students to face both the harsh reality of scarce resources and unfair opportunities in urban schools, and see the possibility of breaking through structural dilemmas.
We took this idea of a dialogic or problem-posing pedagogy to heart when designing activities within our various units.
This design not only cultivates students' expression and collaboration abilities, but also conforms to the core goal of critical pedagogy of empowering students to become knowledge creators.
We sought to counter these traditions in our curriculum development and our pedagogies, and we sought to situate our work conceptually and em-pirically.
This strategy echoes Vygotsky's idea of using children's known world to carry out teaching, and also solves the problem of alienation between urban teenagers and canonical texts, rooting academic learning in students' daily cultural experiences.
By the same token, we were wary of those educators and literary theorists who equated multiculturalism with simply offering texts written by people of color or featuring people of color as protagonists
True multiculturalism is not the accumulation of textual forms, but the interpretation of all texts from an equal and critical perspective, avoiding oppressive interpretations of texts by ethnic minorities.
Studying canonical texts is an important strategy for under-standing the values and ideologies of dominant groups at various points in history.
This sentence reflects the authors' dialectical attitude towards canonical texts: classics are not unquestionable authorities, but windows to understand the values and ideologies of dominant groups.
Though critical literacy remained a goal of our pedagogy, we understood that critical literacy also demands a knowledge of and facility with the language of power. It is impossible to critique or refute texts that one does not understand; com-prehension is an important prerequisite for critique
Here the authors clarify the core relationship between critical literacy and mastery of the language of power. Critique is not groundless negation, but based on the understanding and application of the language of power.
Critical pedagogy is hotly discussed and highly debated in the academy. Its proponents draw upon important scholars (Freire, 1970; McLaren, 1994, 2003b; Giroux, 2001; hooks, 1994; Darder, 1991; Kincheloe, 2004; Shor, 1992) to argue for an approach to education that is rooted in the existential experiences of marginalized peoples; that is centered in a critique of struc-tural, economic, and racial oppression; that is focused on dialogue instead of a one-way transmission of knowledge; and that is structured to empower in-dividuals and collectives as agents of social change.
This sentence defines the core theoretical foundation and propositions of critical pedagogy. It is not an abstract educational concept, but anchored in the existential experiences of marginalized groups and focused on critiquing structural, economic, and racial oppression. This provides a theoretical framework for the authors to apply critical pedagogy to the English classroom of an urban high school in Oakland later, and also reflects the core characteristic of critical pedagogy of connecting theory with reality.
Teachers need to be prepared for the emotions that will be evoked by the visual text. They also need to be ready to communicate with other teachers, with administrators, with parents, and with students about the importance of utilizing this medium to teach about issues related to diversity
Film can do powerful work and it also brings strong emotions, so the plan has to match the medium. Set clear learning goals tied to standards, give content notes in advance, and offer a real alternative path for any student who needs it without penalty. Co create discussion norms, use short scenes with frequent pauses to analyze choices, and build in prepare before and debrief after so students can process what they see.
They can also use cultural studies to make sense of how society creates categories of self and other around a host of identifiers such as race, class, gender, sexuality, home language, and religion.
Because the topics are heavy, set clear discussion norms, offer content notes, and give alternative scene choices so students can opt into material at a level that feels safe. Tie everything back to core ELA skills like citing evidence, analyzing author director choices, and writing for a real audience. Done this way, the unit uses film to build empathy and sharpen critique while giving students practice naming how race, class, gender, language, and religion get represented in everyday media.
Their willingness to identify with this text enables them to bridge their worlds and the film text and to embrace the text at a critical level. Rather than looking at Carl Lee and the others as fic-tional characters, they are looking at what they represent to their own lives in creating that universal plane of knowledge.
I like how the students’ identification opens a door to deeper critique, because it ties the film to lived experience and makes power visible. It is also a good place to press on complexity. If torching the Klan wizard reads as justice, what does that say about how the film frames law, vengeance, and protection when institutions fail. Who gets legitimacy and who is denied it. Does celebrating Carl Lee’s exoneration address structural racism or resolve it through a single exceptional case. You can keep the empowering lens while adding others by asking how the courtroom, the press, and missing community voices shape what counts as justice, and whether the film invites empathy at the cost of flattening the risks of extrajudicial violence.
Critical Pedagogy in an Urban High School English Classroom 59 also drew upon photographs, video footage, and other artifacts to exemplify the conditions of the various schools.
This is a strong move from discussion to civic action. Putting students in the role of policymakers, sending them to interview administrators and peers in both a wealthy school and their own, and asking them to marshal photos and video turns equity into something visible and arguable. It is authentic assessment, and it teaches research, audience awareness, and evidence use all at once.
Anthropologist Clifford Geertz claims that the more we study the cul-tural practices of others, the more these practices seem logical to us (2000, 16) and the more they help us to understand our own practices as equally unique and equally meaningful
As a university international student, I like this because it treats literature as a bridge, not just something to tear down. Pairing Shakespeare or Donne with the Fugees, and reading the Odyssey and Beowulf through themes like heroism, sexism, and violence, makes the classics feel present and tied to our lives. As Geertz says, studying other practices helps us see our own as one meaningful way among many. This builds empathy and strong close reading at the same time.
Through our reading of critical theory and our work with urban adolescents we came to understand the importance of studying dominant texts to the development and mainte-nance of a revolutionary consciousness for both teachers and the students in their classroom
This passage makes a clear and honest point. If we want students to argue back to power, they need fluency in the language of power and the literacy habits that go with it. I also hear a risk that many of us have seen. Teaching Standard English can slide into subtractive English only. The way through is an additive stance. Treat home languages and dialects as assets while building LWC as another register for school, work, and civic life. In practice that looks like code meshing in drafts with audience aware editing for finals, side by side reading of dominant texts and community texts, and explicit lessons on how authors in power make meaning. That way comprehension feeds critique, and critique does not require students to leave parts of themselves at the door.
gain, educators and researchers look to critical pedagogy as they con-sider ways to motivate students, to develop literacies and numeracies of power, and to engage students and their communities in the struggle for edu-cational justice.
As a university international student, this reads like a plan that starts with big ideas and then tests them in real classrooms. They try critical pedagogy in an Oakland English class and in teams and summer programs, then learn from what actually happens. I like that they refuse the usual tradeoff between rigor and freedom. My best classes challenge me on close reading and writing while also letting us connect literature to our lives and communities. I want to see the concrete moves, like how they run discussions, what texts they pair, and how they grade so civic voice counts along with standards. I do still wonder how much time this takes and how it works when the teacher is new. Even so, it feels promising because the theory grows out of students and daily practice, not just a lecture.
eLife Assessment
The authors present valuable empirical and modelling evidence that statistical learning in speech perception may contain sub-processes. While the evidence for statistical learning effects is solid, the link between the pattern of effects (both empirical and simulated) and the theoretical concepts of the sub-processes (e.g., segmentation, anticipation) could be further developed. This work is of broad interest to researchers working on, or with, statistical learning, and to any researcher interested in the challenges of how data and models adjudicate between competing theoretical constructs.
Reviewer #1 (Public review):
Summary:
This paper presents three experiments. Experiments 1 and 3 use a target detection paradigm to investigate the speed of statistical learning. The first experiment is a replication of Batterink, 2017, in which participants are presented with streams of uniform-length, trisyllabic nonsense words and asked to detect a target syllable. The results replicate previous findings, showing that learning (in the form of response time facilitation to later-occurring syllables within a nonsense word) occurs after a single exposure to a word. In the second experiment, participants are presented with streams of variable length nonsense words (two trisyllabic words and two disyllabic words), and perform the same task. A similar facilitation effect was observed as in Experiment 1. In Experiment 3 (newly added in the Revised manuscript), an adult version of the study by Johnson and Tyler is included. Participants were exposed to streams of words of either uniform length (all disyllabic) or mixed length (two disyllabic, two trisyllabic) and then asked to perform a familiarity judgment on a 1-5 scale on two words from the stream and two part-words. Performance was better in the uniform length condition.
The authors interpret these findings as evidence that target detection requires mechanisms different from segmentation. They present results of a computational model to simulate results from the target detection task, and find that a bigram model can produce facilitation effects similar to the ones observed by human participants in Experiments 1 and 2 (though this model was not directly applied to test whether human-like effects were also produced to account for the data in Experiment 3). PARSER was also tested and produced differing results from those observed by humans across all three experiments. The authors conclude that the mechanisms involved in the target detection task are different from those involved in the word segmentation task.
Strengths:
The paper presents multiple experiments that provide internal replication of a key experimental finding, in which response times are facilitated after a single exposure to an embedded pseudoword. Both experimental data and results from a computational model are presented, providing converging approaches for understanding and interpreting the main results. The data are analyzed very thoroughly using mixed effects models with multiple explanatory factors. The addition of Experiment 3 provides direct evidence that the profile of performance for familiarity ratings and target detection differ as a function of word length variability.
Weaknesses:
(1) The concept of segmentation is still not quite clear. The authors seem to treat the testing procedure of Experiment 3 as synonymous with segmentation. But the ability to more strongly endorse words from the stream versus part-words as familiar does not necessarily mean that they have been successfully "segmented", as I elaborated on in my earlier review. In my view, it would be clearer to refer to segmentation as the mechanism or conceptual construct of segmenting continuous speech into discrete words. This ability to accurately segment component words could support familiarity judgments but is not necessary for above-chance familiarity or recognition judgments, which could be supported by more general memory signals. In other words, segmentation as an underlying ability is sufficient but not necessary for above-chance performance on familiarity-driven measures such as the one used in experiment 3.
(2) The addition of experiment 3 is an added strength of the revised paper and provides more direct evidence of dissociations as a function of word length on the two tasks (target detection and familiarity ratings), compared to the prior strategy of just relying on previous work for this claim. However, it is not clear why the authors chose not to use the same stimuli as used in experiment 1 and 2, which would have allowed for more direct comparisons to be made. It should also be specified whether test items in the UWL and MWL were matched for overall frequency during exposure. Currently, the text does not specify whether test words in the UWL condition were taken from the high frequency or low frequency group; if they were taken from the high frequency group this would of course be a confound when comparing to the MWL condition. Finally, the definition of part-words should also be clarified,
(3) The framing and argument for a prediction/anticipation mechanism was dropped in the Revised manuscript, but there are still a few instances where this framing and interpretation remain. E.g. Abstract - "we found that a prediction mechanism, rather than clustering, could explain the data from target detection." Discussion page 43 "Together, these results suggest that a simple prediction-based mechanism can explain the results from the target detection task, and clustering-based approaches such as PARSER cannot, contrary to previous claims."
Minor (4) It was a bit unclear as to why a conceptual replication of Batterink 2017 was conducted, given that the target syllables at the beginning and end of the streams were immediately dropped from further analysis. Why include syllable targets within these positions in the design if they are not analyzed?
(5) Figures 3 and 4 are plotted on different scales, which makes it difficult to visually compare the effects between word length conditions.
Reviewer #2 (Public review):
Summary:
The valuable study investigates how statistical learning may facilitate a target detection task and whether the facilitation effect is related to statistical learning of word boundaries. Solid evidence is provided that target detection and word segmentation rely on different statistical learning mechanisms.
Strengths:
The study is well designed, using the contrast between the learning of words of uniform length and words of variable length to dissociate general statistical learning effects and effects related to word segmentation.
Weaknesses:
The study relies on the contrast between word length effects on target detection and word learning. However, the study only tested the target detection condition and did not attempt to replicate the word segmentation effect. It is true that the word segmentation effect has been replicated before but it is still worth reviewing the effect size of previous studies.
The paper seems to distinguish prediction, anticipation, and statistical learning, but it is not entirely clear what each terms refers to.
Comments on revisions:
The authors did not address my concerns...they only replied to reviewer 1.
Author response:
The following is the authors’ response to the original reviews.
Reviewer #1 (Public review):
Summary:
This paper presents two experiments, both of which use a target detection paradigm to investigate the speed of statistical learning. The first experiment is a replication of Batterink, 2017, in which participants are presented with streams of uniform-length, trisyllabic nonsense words and asked to detect a target syllable. The results replicate previous findings, showing that learning (in the form of response time facilitation to later-occurring syllables within a nonsense word) occurs after a single exposure to a word. In the second experiment, participants are presented with streams of variable-length nonsense words (two trisyllabic words and two disyllabic words) and perform the same task. A similar facilitation effect was observed as in Experiment 1. The authors interpret these findings as evidence that target detection requires mechanisms different from segmentation. They present results of a computational model to simulate results from the target detection task and find that an "anticipation mechanism" can produce facilitation effects, without performing segmentation. The authors conclude that the mechanisms involved in the target detection task are different from those involved in the word segmentation task.
Strengths:
The paper presents multiple experiments that provide internal replication of a key experimental finding, in which response times are facilitated after a single exposure to an embedded pseudoword. Both experimental data and results from a computational model are presented, providing converging approaches for understanding and interpreting the main results. The data are analyzed very thoroughly using mixed effects models with multiple explanatory factors.
Weaknesses:
In my view, the main weaknesses of this study relate to the theoretical interpretation of the results.
(1) The key conclusion from these findings is that the facilitation effect observed in the target detection paradigm is driven by a different mechanism (or mechanisms) than those involved in word segmentation. The argument here I think is somewhat unclear and weak, for several reasons:
First, there appears to be some blurring in what exactly is meant by the term "segmentation" with some confusion between segmentation as a concept and segmentation as a paradigm.
Conceptually, segmentation refers to the segmenting of continuous speech into words. However, this conceptual understanding of segmentation (as a theoretical mechanism) is not necessarily what is directly measured by "traditional" studies of statistical learning, which typically (at least in adults) involve exposure to a continuous speech stream followed by a forced-choice recognition task of words versus recombined foil items (part-words or nonwords). To take the example provided by the authors, a participant presented with the sequence GHIABCDEFABCGHI may endorse ABC as being more familiar than BCG, because ABC is presented more frequently together and the learned association between A and B is stronger than between C and G. However, endorsement of ABC over BCG does not necessarily mean that the participant has "segmented" ABC from the speech stream, just as faster reaction times in responding to syllable C versus A do not necessarily indicate successful segmentation. As the authors argue on page 7, "an encounter to a sequence in which two elements co-occur (say, AB) would theoretically allow the learner to use the predictive relationship during a subsequent encounter (that A predicts B)." By the same logic, encoding the relationship between A and B could also allow for the above-chance endorsement of items that contain AB over items containing a weaker relationship.
Both recognition performance and facilitation through target detection reflect different outcomes of statistical learning. While they may reflect different aspects of the learning process and/or dissociable forms of memory, they may best be viewed as measures of statistical learning, rather than mechanisms in and of themselves.
Thanks for this nuanced discussion, and this is an important point that R2 also raised. We agree that segmentation can refer to both an experimental paradigm and a mechanism that accounts for learning in the experimental paradigm. In the experimental paradigm, participants are asked to identify which words they believe to be (whole) words from the continuous syllable stream. In the target-detection experimental paradigm, participants are not asked to identify words from continuous streams, and instead, they respond to the occurrences of a certain syllable. It’s possible that learners employ one mechanism in these two tasks, or that they employ separate mechanisms. It’s also the case that, if all we have is positive evidence for both experimental paradigms, i.e., learners can succeed in segmentation tasks as well as in target detection tasks with different types of sequences, we would have no way of talking about different mechanisms, as you correctly suggested that evidence for segmenting AB and processing B faster following A, is not evidence for different mechanisms.
However, that is not the case. When the syllable sequences contain same-length subsequences (i.e., words), learning is indeed successful in both segmentation and target detection tasks. However, in studies such as Hoch et al. (2013), findings suggest that words from mixed-length sequences are harder to segment than words from uniform-length sequences. This finding exists in adult work (e.g., Hoch et al. 2013) as well as infant work (Johnson & Tyler, 2010), and replicated here in the newly included Experiment 3, which stands in contrast to the positive findings of the facilitation effect with mixed-length sequences in the target detection paradigm (one of our main findings in the paper). Thus, it seems to be difficult to explain, if the learning mechanisms were to be the same, why humans can succeed in mixed-length sequences in target detection (as shown in Experiment 2) but fail in uniform-length sequences (as shown in Hoch et al. and Experiment 3).
In our paper, we have clarified these points describe the separate mechanisms in more detail, in both the Introduction and General Discussion sections.
(2) The key manipulation between experiments 1 and 2 is the length of the words in the syllable sequences, with words either constant in length (experiment 1) or mixed in length (experiment 2). The authors show that similar facilitation levels are observed across this manipulation in the current experiments. By contrast, they argue that previous findings have found that performance is impaired for mixed-length conditions compared to fixed-length conditions. Thus, a central aspect of the theoretical interpretation of the results rests on prior evidence suggesting that statistical learning is impaired in mixed-length conditions. However, it is not clear how strong this prior evidence is. There is only one published paper cited by the authors - the paper by Hoch and colleagues - that supports this conclusion in adults (other mentioned studies are all in infants, which use very different measures of learning). Other papers not cited by the authors do suggest that statistical learning can occur to stimuli of mixed lengths (Thiessen et al., 2005, using infant-directed speech; Frank et al., 2010 in adults). I think this theoretical argument would be much stronger if the dissociation between recognition and facilitation through RTs as a function of word length variability was demonstrated within the same experiment and ideally within the same group of participants.
To summarize the evidence of learning uniform-length and mixed-length sequences (which we discussed in the Introduction section), “even though infants and adults alike have shown success segmenting syllable sequences consisting of words that were uniform in length (i.e., all words were either disyllabic; Graf Estes et al., 2007; or trisyllabic, Aslin et al., 1998), both infants and adults have shown difficulty with syllable sequences consisting of words of mixed length (Johnson & Tyler, 2010; Johnson & Jusczyk, 2003a; 2003b; Hoch et al., 2013).” The newly added Experiment 3 also provided evidence for the difference in uniform-length and mixed-length sequences. Notably, we do not agree with the idea that infant work should be disregarded as evidence just because infants were tested with habituation methods; not only were the original findings (Saffran et al. 1996) based on infant work, so were many other studies on statistical learning.
There are other segmentation studies in the literature that have used mixed-length sequences, which are worth discussing. In short, these studies differ from the Saffran et al. (1996) studies in many important ways, and in our view, these differences explain why the learning was successful. Of interest, Thiessen et al. (2005) that you mentioned was based on infant work with infant methods, and demonstrated the very point we argued for: In their study, infants failed to learn when mixed-length sequences were pronounced as adult-directed speech, and succeeded in learning given infant-directed speech, which contained prosodic cues that were much more pronounced. The fact that infants failed to segment mixed-length sequences without certain prosodic cues is consistent with our claim that mixed-length sequences are difficult to segment in a segmentation paradigm. Another such study is Frank et al. (2010), where continuous sequences were presented in “sentences”. Different numbers of words were concatenated into sentences where a 500ms break was present between each sentence in the training sequence. One sentence contained only one word, or two words, and in the longest sentence, there were 24 words. The results showed that participants are sensitive to the effect of sentence boundaries, which coincide with word boundaries. In the extreme, the one-word-per-sentence condition simply presents learners with segmented word forms. In the 24-word-per-sentence condition, there are nevertheless sentence boundaries that are word boundaries, and knowing these word boundaries alone should allow learners to perform above chance in the test phase. Thus, in our view, this demonstrates that learners can use sentence boundaries to infer word boundaries, which is an interesting finding in its own right, but this does not show that a continuous syllable sequence with mixed word lengths is learnable without additional information. In summary, to our knowledge, syllable sequences containing mixed word lengths are better learned when additional cues to word boundaries are present, and there is strong evidence that syllable sequences containing uniform-word lengths are learned better than mixed-length ones.
Frank, M. C., Goldwater, S., Griffiths, T. L., & Tenenbaum, J. B. (2010). Modeling human performance in statistical word segmentation. Cognition, 117(2), 107-125.
To address your proposal of running more experiments to provide stronger evidence for our theory, we were planning to run another study to have the same group of participants do both the segmentation and target detection paradigm as suggested, but we were unable to do so as we encountered difficulties to run English-speaking participants. Instead, we have included an experiment (now Experiment 3), showing the difference between the learning of uniform-length and mixed-length sequences with the segmentation paradigm that we have never published previously. This experiment provides further evidence for adults’ difficulties in segmenting mixed-length sequences.
(3) The authors argue for an "anticipation" mechanism in explaining the facilitation effect observed in the experiments. The term anticipation would generally be understood to imply some kind of active prediction process, related to generating the representation of an upcoming stimulus prior to its occurrence. However, the computational model proposed by the authors (page 24) does not encode anything related to anticipation per se. While it demonstrates facilitation based on prior occurrences of a stimulus, that facilitation does not necessarily depend on active anticipation of the stimulus. It is not clear that it is necessary to invoke the concept of anticipation to explain the results, or indeed that there is any evidence in the current study for anticipation, as opposed to just general facilitation due to associative learning.
Thanks for raising this point. Indeed, the anticipation effect we reported is indistinguishable from the facilitation effect that we reported in the reported experiments. We have dropped this framing.
In addition, related to the model, given that only bigrams are stored in the model, could the authors clarify how the model is able to account for the additional facilitation at the 3rd position of a trigram compared to the 2nd position?
Thanks for the question. We believe it is an empirical question whether there is an additional facilitation at the 3rd position of a trigram compared to the 2nd position. To investigate this issue, we conducted the following analysis with data from Experiment 1. First, we combined the data from two conditions (exact/conceptual) from Experiment 1 so as to have better statistical power. Next, we ran a mixed effect regression with data from syllable positions 2 and 3 only (i.e., data from syllable position 1 were not included). The fixed effect included the two-way interaction between syllable position and presentation, as well as stream position, and the random effect was a by-subject random intercept and stream position as the random slope. This interaction was significant (χ<sup>2</sup>(3) =11.73, p=0.008), suggesting that there is additional facilitation to the 3rd position compared to the 2nd position.
For the model, here is an explanation of why the model assumes an additional facilitation to the 3rd position. In our model, we proposed a simple recursive relation between the RT of a syllable occurring for the nth time and the n+1<sup>th</sup> time, which is:
and
RT(1) = RT0 + stream_pos * stream_inc, where the n in RT(n) represents the RT for the n<sup>th</sup> presentation of the target syllable, stream_pos is the position (3-46) in the stream, and occurrence is the number of occurrences that the syllable has occurred so far in the stream.
What this means is that the model basically provides an RT value for every syllable in the stream. Thus, for a target at syllable position 1, there is a RT value as an unpredictable target, and for targets at syllable position 2, there is a facilitation effect. For targets at syllable position 3, it is facilitated the same amount. As such, there is an additional facilitation effect for syllable position 3 because effects of predication are recursive.
(4) In the discussion of transitional probabilities (page 31), the authors suggest that "a single exposure does provide information about the transitions within the single exposure, and the probability of B given A can indeed be calculated from a single occurrence of AB." Although this may be technically true in that a calculation for a single exposure is possible from this formula, it is not consistent with the conceptual framework for calculating transitional probabilities, as first introduced by Saffran and colleagues. For example, Saffran et al. (1996, Science) describe that "over a corpus of speech there are measurable statistical regularities that distinguish recurring sound sequences that comprise words from the more accidental sound sequences that occur across word boundaries. Within a language, the transitional probability from one sound to the next will generally be highest when the two sounds follow one another within a word, whereas transitional probabilities spanning a word boundary will be relatively low." This makes it clear that the computation of transitional probabilities (i.e., Y | X) is conceptualized to reflect the frequency of XY / frequency of X, over a given language inventory, not just a single pair. Phrased another way, a single exposure to pair AB would not provide a reliable estimate of the raw frequencies with which A and AB occur across a given sample of language.
Thanks for the discussion. We understand your argument, but we respectively disagree that computing transitional probabilities must be conducted under a certain theoretical framework. In our humble opinion, computing transitional probabilities is a mathematical operation, and as such, it is possible to do so with the least amount of data possible that enables the mathematical operation, which concretely is a single exposure during learning. While it is true that a single exposure may not provide a reliable estimate of frequencies or probabilities, it does provide information with which the learner can make decisions.
This is particularly true for topics under discussion regarding the minimal amount of exposure that can enable learning. It is important to distinguish the following two questions: whether learners can learn from a short exposure period (from a single exposure, in fact) and how long of an exposure period does the learner require for it to be considered to produce a reliable estimate of frequencies. Incidentally, given the fact that learners can learn from a single exposure based on Batterink (2017) and the current study, it does not appear that learners require a long exposure period to learn about transitional probabilities.
(5) In experiment 2, the authors argue that there is robust facilitation for trisyllabic and disyllabic words alike. I am not sure about the strength of the evidence for this claim, as it appears that there are some conflicting results relevant to this conclusion. Notably, in the regression model for disyllabic words, the omnibus interaction between word presentation and syllable position did not reach significance (p= 0.089). At face value, this result indicates that there was no significant facilitation for disyllabic words. The additional pairwise comparisons are thus not justified given the lack of omnibus interaction. The finding that there is no significant interaction between word presentation, word position, and word length is taken to support the idea that there is no difference between the two types of words, but could also be due to a lack of power, especially given the p-value (p = 0.010).
Thanks for the comment. Firstly, we believe there is a typo in your comment, where in the last sentence, we believe you were referring to the p-value of 0.103 (source: “The interaction was not significant (χ2(3) = 6.19, p= 0.103”). Yes, a null result with a frequentist approach cannot support a null claim, but Bayesian analyses could potentially provide evidence for the null.
To this end, we conducted a Bayes factor analysis using the approach outlined in Harms and Lakens (2018), which generates a Bayes factor by computing a Bayesian information criterion for a null model and an alternative model. The alternative model contained a three-way interaction of word length, word presentation, and word position, whereas the null model contained a two-way interaction between word presentation and word position as well as a main effect of word length. Thus, the two models only differ in terms of whether there is a three-way interaction. The Bayes factor is then computed as exp[(BICalt − BICnull)/2]. This analysis showed that there is strong evidence for the null, where the Bayes Factor was found to be exp(25.65) which is more than 1011. Thus, there is no power issue here, and there is strong evidence for the null claim that word length did not interact with other factors in Experiment 2.
There is another issue that you mentioned, of whether we should conduct pairwise comparisons if the omnibus interaction did not reach significance. This would be true given the original analysis plan, but we believe that a revised analysis plan makes more sense. In the revised analysis plan for Experiment 2, we start with the three-way interaction (as just described in the last paragraph). The three-way interaction was not significant, and after dropping the third interaction terms, the two-way interaction and the main effect of word length are both significant, and we use this as the overall model. Testing the significance of the omnibus interaction between presentation and syllable position, we found that this was significant (χ<sup>2</sup>(3) =49.77, p<0.001). This represents that, in one model, that the interaction between presentation and syllable position using data from both disyllabic and trisyllabic words. This was in addition to a significant fixed effect of word length (β=0.018, z=6.19, p<0.001). This should motivate the rest of the planned analysis, which regards pairwise comparisons in different word length conditions.
(6) The results plotted in Figure 2 seem to suggest that RTs to the first syllable of a trisyllabic item slow down with additional word presentations, while RTs to the final position speed up. If anything, in this figure, the magnitude of the effect seems to be greater for 1st syllable positions (e.g., the RT difference between presentation 1 and 4 for syllable position 1 seems to be numerically larger than for syllable position 3, Figure 2D). Thus, it was quite surprising to see in the results (p. 16) that RTs for syllable position 1 were not significantly different for presentation 1 vs. the later presentations (but that they were significant for positions 2 and 3 given the same comparison). Is this possibly a power issue? Would there be a significant slowdown to 1st syllables if results from both the exact replication and conceptual replication conditions were combined in the same analysis?
Thanks for the suggestion and your careful visual inspection of the data. After combining the data, the slowdown to 1st syllables is indeed significant. We have reported this in the results of Experiment 1 (with an acknowledgement to this review):
Results showed that later presentations took significantly longer to respond to compared to the first presentation (χ<sup>2</sup>(3) = 10.70, p=0.014), where the effect grew larger with each presentation (second presentation: β=0.011, z=1.82, p=0.069; third presentation: β=0.019, z=2.40, p=0.016; fourth presentation: β=0.034, z=3.23, p=0.001).
(7) It is difficult to evaluate the description of the PARSER simulation on page 36. Perhaps this simulation should be introduced earlier in the methods and results rather than in the discussion only.
Thanks for the suggestions. We have added two separate simulations in the paper, which should describe the PARSER simulations sufficiently, as well as provide further information on the correspondence between the simulations and the experiments. Thanks again for the great review! We believe our paper has improved significantly as a result.
eLife Assessment
This study presents an important finding that ant nest structure and digging behavior depend on ant age demographics for a ground-dwelling ant species (Camponotus fellah). By asking whether ants employ age-polyethism in excavation, the authors address a long-standing question about how individuals in collectives determine the overall state of the task they must perform. The experimental evidence that the age of the ants and the group composition affect the digging of tunnels is convincing, and their model is able to replicate the colony's excavation dynamics qualitatively, results that may prove to be a key consideration for interpreting results from other studies in the field of social insect behavior.
Reviewer #1 (Public review):
This study investigates how ant group demographics influence nest structures and group behaviors of Camponotus fellah ants, a ground-dwelling carpenter ant species (found locally in Israel) that build subterranean nest structures. Using a quasi-2D cell filled with artificial sand, the authors perform two complementary sets of experiments to try to link group behavior and nest structure: first, the authors place a mated queen and several pupae into their cell and observe the structures that emerge both before and after the pupae eclose (i.e., "colony maturation" experiments); second, the authors create small groups (of 5, 10, or 15 ants, each including a queen) within a narrow age range (i.e., "fixed demographic" experiments) to explore the dependence of age on construction. Some of the fixed demographic instantiations included a manually induced catastrophic collapse event; the authors then compared emergency repair behavior to natural nest creation. Finally, the authors introduce a modified logistic growth model to describe the time-dependent nest area. The modification introduced parameters that allow for age-dependent behavior, and the authors use their fixed demographic experiments to set these parameters, and then apply the model to interpret the behavior of the colony maturation experiments. The main results of this paper are that for natural nest construction, nest areas, and morphologies depend on the age demographics of ants in the experiments: younger ants create larger nests and angled tunnels, while older ants tend to dig less and build predominantly vertical tunnels; in contrast, emergency response seems to elicit digging in ants of all ages to repair the nest.
The experimental results are convincing, providing new information and important insights into nest and colony growth in a social insect species. A model, inspired by previous work but modified to capture experimental results, is in reasonable agreement with experiments and is more biologically relevant than previous models.
Reviewer #2 (Public review):
I enjoyed this paper and its examination of the relationship between overall density and age polyethism to reduce the computational complexity required to match nest size with population. I had some questions about the requirement that growth is infinite in such a solution, but these have been addressed by the authors in the responses and updated manuscript. I also enjoyed the discussion of whether collective behaviour is an appropriate framework in systems in which agents (or individuals) differ in the behavioural rules they employ, according to age, location, or information state. This is especially important in a system like social insects, typically held as a classic example of individual-as-subservient to whole, and therefore most likely to employ universal rules of behaviour. The current paper demonstrates a potentially continuous age-related change in target behaviour (excavation), and suggests an elegant and minimal solution to the requirement for building according to need in ants, avoiding the invocation of potentially complex cognitive mechanisms, or information states that all individuals must have access to in order to have an adaptive excavation output.
The authors have addressed questions I had in the review process and the manuscripts is now clear in its communication and conclusions.
The modelling approach is compelling, also allowing extrapolation to other group sizes and even other species. This to me is the main strength of the paper, as the answer to the question of whether it is younger or older ants that primarily excavate nests could have been answered by an individual tracking approach (albeit there are practical limitations to this, especially in the observation nest setup, as the authors point out). The analysis of the tunnel structure is also an important piece of the puzzle, and I really like the overall study.
Author response:
The following is the authors’ response to the previous reviews.
Reviewer #1 (Public review):
This study investigates how ant group demographics influence nest structures and group behaviors of Camponotus fellah ants, a ground-dwelling carpenter ant species (found locally in Israel) that build subterranean nest structures. Using a quasi-2D cell filled with artificial sand, the authors perform two complementary sets of experiments to try to link group behavior and nest structure: first, the authors place a mated queen and several pupae into their cell and observe the structures that emerge both before and after the pupae eclose (i.e., "colony maturation" experiments); second, the authors create small groups (of 5,10, or 15 ants, each including a queen) within a narrow age range (i.e., "fixed demographic" experiments) to explore the dependence of age on construction. Some of the fixed demographic instantiations included a manually induced catastrophic collapse event; the authors then compared emergency repair behavior to natural nest creation. Finally, the authors introduce a modified logistic growth model to describe the time-dependent nest area. The modification introduced parameters that allow for age-dependent behavior, and the authors use their fixed demographic experiments to set these parameters, and then apply the model to interpret the behavior of the colony maturation experiments. The main results of this paper are that for natural nest construction, nest areas, and morphologies depend on the age demographics of ants in the experiments: younger ants create larger nests and angled tunnels, while older ants tend to dig less and build predominantly vertical tunnels; in contrast, emergency response seems to elicit digging in ants of all ages to repair the nest.
The experimental results are solid, providing new information and important insights into nest and colony growth in a social insect species. As presented, I still have some reservations about the model's contribution to a deeper understanding of the system. Additional context and explanation of the model, implications, and limitations would be helpful for readers.
We sincerely thank Reviewer #1 for the time and effort dedicated to our manuscript's detailed review and assessment. The new revision suggestions were constructive, and we have provided a point-by-point response to address them.
Reviewer #2 (Public review):
I enjoyed this paper and its examination of the relationship between overall density and age polyethism to reduce the computational complexity required to match nest size with population. I had some questions about the requirement that growth is infinite in such a solution, but these have been addressed by the authors in the responses and the updated manuscript. I also enjoyed the discussion of whether collective behaviour is an appropriate framework in systems in which agents (or individuals) differ in the behavioural rules they employ, according to age, location, or information state. This is especially important in a system like social insects, typically held as a classic example of individual-as-subservient to whole, and therefore most likely to employ universal rules of behaviour. The current paper demonstrates a potentially continuous age-related change in target behaviour (excavation), and suggests an elegant and minimal solution to the requirement for building according to need in ants, avoiding the invocation of potentially complex cognitive mechanisms, or information states that all individuals must have access to in order to have an adaptive excavation output.
The authors have addressed questions I had in the review process and the manuscript is now clear in its communication and conclusions.
The modelling approach is compelling, also allowing extrapolation to other group sizes and even other species. This to me is the main strength of the paper, as the answer to the question of whether it is younger or older ants that primarily excavate nests could have been answered by an individual tracking approach (albeit there are practical limitations to this, especially in the observation nest setup, as the authors point out). The analysis of the tunnel structure is also an important piece of the puzzle, and I really like the overall study.
We sincerely thank Reviewer #2 for the time and effort dedicated to our manuscript's detailed review and assessment.
Reviewer #1 (Recommendations for the authors):
Thank you for the modifications. I found much of the additional information very helpful. I do still have a few comments, which I will include below.
We thank the reviewer for this comment
The authors provide some additional citations for the model, however, the ODE in refs 24 and 30 is different from what the authors present here, and different from what is presented in ref 29. Specifically, the additional "volume" term that multiplies the entire equation. Can the authors provide some additional context for their model in comparison to these models as well as how their model relates to other work?
We thank the reviewer for this question. The primary difference between the logistic model (reference number: 24,30), and the saturation model (reference number: 29) is rooted in their assumptions on the scaling of the active number of ants that participate in the nest excavation and the nest volume.
The logistic growth model ( 𝑑𝑉/𝑑𝑡 = α𝑉(1-V/Vs) describes the excavation in fixed-sized colonies (50, 100, 200) through a balance of two key processes : (1) positive feedback (α𝑉), where the digging efficiency increases with the nest size, and (2) negative feedback (1-V/Vs), where growth slows as the nest approaches a saturation (Vs). The model assumes that the number of actively excavating ants is linearly proportional to the nest volume (V). This represents a scenario where a large nest contains or can support more workers, which in turn increases the digging rates. While this does not require explicit communication between individuals, ants indirectly sense the global nest volume through stigmergic cues, such as pheromone depositions, encounter rates, while ignoring individual differences in age.
In contrast, the saturation model (𝑑𝑉/𝑑𝑡 = α𝑉(1-V/Vs) assumes a constant number of ants is working throughout the excavation. The digging rate is therefore independent of the nest volume, this model imposes a different cognitive requirement ants must somehow assess the global nest slowing only due to the saturation term (1-V/Vs) as the nest approaches its target size. However, volume (V) and the overall number of ants in the nest. Thus, rather than relying on local cues, ants need more explicit communication or a sophisticated global perception mechanism that allows ants to sense the nest volume and the nest population to adjust the digging rates accordingly. Therefore, this model requires a more complex and less biologically plausible mechanism than the logistic model.
In our age-dependent digging model in the manuscript, we explicitly sum the contribution of each ant towards the nest area expansion based on its age-dependent digging threshold (quantified from fixed demographics experiments) the sum over Thus, the term ‘V’ in the ‘ 𝑉(1-V/Vs) takes the same effect as sum over all ants in the equation (2) of our manuscript; they describe how the total excavation rate scales with the number of individuals. Under the simplifying assumption that the number of ants is proportional to the nest volume ‘V’, and that all ants dig at a constant rate, our equation (2) in the manuscript reduces to the logistic equation ‘𝑉(1-V/Vs)’ This implies that each ant individually assesses the nest volume and then digs at a rate ‘(1-V/Vs)’.
Thus, we adopted the simpler model from the previously published ones, in which ants individually react to the local density cues and regulate their digging. This approach does not require a global assessment of the nest volume or the number of ants; a local perception of density triggers each ant’s decision to dig, likely modulated by the frequency of social contacts or chemical concentration, which serves as an indicator of the global nest area. The ant compares this locally perceived density to an innate, age-specific threshold. If the perceived local density exceeds its threshold (indicating insufficient area), it digs; otherwise, there is no digging. Thus, excavation dynamics in maturing colonies emerge from this collective response to local density cues, without any individual need to directly assess the global nest volume (V) or having explicit knowledge of the colony size (N).
As suggested by the reviewer, we have added these points to the discussion, contrasting the previously published models with our age-dependent excavation models (line numbers: 283-290) “In our study, we adopted the simpler version of previously published age-independent excavation models, where individuals respond to local stigmergic cues such as encounter rates or pheromone concentrations, which serve as a proxy for the global nest volume (24,30). We minimally modified this model to include age-dependent density targets. According to our age-dependent digging model, each ant compares this perceived local density to its own innate age-specific digging threshold as quantified from the fixed demographics experiments. If the perceived local density exceeds its age-dependent area threshold (indicating insufficient area), it digs; otherwise, there is no digging. This mechanism eliminates the need for cognitively demanding global assessment of the total nest volume or the overall colony population, a requirement for the saturation model (29)”.
I still find it a little concerning that the age-independent model, though it cannot be correct, fits the data better than the age-dependent modification. It seems to me the models presented in refs 24, 29, and 30, which served as inspiration for the one presented here, do not have any deep theoretical origin, but were chosen for "being consistent with" the observed overall excavated volumes. Is this correct, and if so, how much can/should be gleaned about behavior from these models? Please provide some discussion of what is reasonable to expect from such a model as well as what the limitations might be.
We thank the reviewer for the comment.
In our study, we make an important assumption, as described in the lines (line number : 161 - 164) of the manuscript, that ants rely on local cues during nest excavation, and individuals cannot distinguish between the fixed demographics and colony maturation conditions. This implies that the age-dependent target area identified in the fixed demographics experiments should also account for the excavation dynamics seen in the colony maturation experiments.
From the fixed demographics young and old experiments, we directly quantified that the younger ants excavate a significantly larger area than the older ants for the same group size. This age-dependent digging propensity is an experimental result, and not a model output.
We agree that the age-independent model fits the colony maturation experiments well, even though it's not a statistically better fit than the age-dependent model. However, the age-independent models in the references (24,29,30) fail to explain the empirically obtained excavation dynamics in the fixed demographics, young and old colonies. If indeed these models were true, then we would have observed similar excavated areas between the colony maturation, fixed demographics, young, and older colonies of the same size. Thus, the inconsistency of these models confirms that age-independent assumptions are biologically inadequate. These details are explicitly mentioned in lines (304 - 309).
We believe that our model’s value is in providing a plausible explanation for the observed excavation dynamics in the colony maturation experiments, and generating testable predictions (Figure 4. C, and 4.D, described in lines 199 - 216) about the percentage contribution of different age cohorts and queens to the excavated area from the colony maturation experiments. This prediction would not be possible with an age-independent model.
Minor comments:
Figure 2A: Please use a color other than white for the model... this curve is still very hard to see
We thank the reviewer for the comment. The colour is changed to yellow.
Figure 4A: Should quoted confidence intervals for slope and intercept be swapped?
Yes, we thank the reviewer for pointing this out. The labels for the slope and intercept were swapped. We corrected this in the current revised version 2.
Figure 5 D-F: Can the authors show data points and confidence intervals instead of bar graphs? The error bars dipping below zero do not clearly represent the data.
We thank the reviewer for the comment. We now show the individual data points from each treatment with the 95% Confidence Interval of the mean.
crimson
As Josephine K. Tarvers discusses in her article, "'The Deep Still Land of Colours': Color Imagery in 'The Defence of Guenevere and Other Poems'", Morris uses color imagery to symbolize meaning. The color red illustrates love and lovers, which is used in this line when Launcelot arrives to Guenevere's rescue. Morris, influenced by the traditional color scheme of the Middle Ages, uses colors such as red, green, white, and blue in his works to evoke an emotional response from his readers. https://www.jstor.org/stable/4174266
eLife Assessment
The present manuscript by Cordeiro et al., shows convincing evidence that α-mangostin, a xanthone obtained from the fruit of the Garcinia mangostana tree, behaves as a strong activator of the large-conductance (BK) potassium channels; macroscopic currents and single-channel experiments show that α-mangostin produces an increase in the probability of opening, without affecting the single-channel conductance. The authors put forward that α-mangostin activation of the BK channel is state-independent, and molecular docking and mutagenesis suggest that α-mangostin binds to a site in the internal cavity. Additionally, the authors show that α-mangostin can relax arteries, further suggesting the plausibility of the proposed effects of this compound. These are valuable findings that should be of interest to channel biophysicists and physiologists alike.
Reviewer #1 (Public review):
In this manuscript, the authors aimed to identify the molecular target and mechanism by which α-Mangostin, a xanthone from Garcinia mangostana, produces vasorelaxation that could explain the antihypertensive effects. Building on prior reports of vascular relaxation and ion channel modulation, the authors convincingly show that large-conductance potassium BK channels are the primary site of action. Using electrophysiological, pharmacological, and computational evidence, the authors achieved their aims and showed that BK channels are the critical molecular determinant of mangostin's vasodilatory effects, even though the vascular studies are quite preliminary in nature.
Strengths:
(1) The broad pharmacological profiling of mangostin across potassium channel families, revealing BK channels - and the vascular BK-alpha/beta1 complex - as the potently activated target in a concentration-dependent manner.
(2) Detailed gating analyses showing large negative shifts in voltage-dependence of activation and altered activation and deactivation kinetics.
(3) High-quality single-channel recordings for open probability and dwell times.
(4) Convincing activation in reconstituted BKα/β1-Caᵥ nanodomains mimicking physiological conditions and functional proof-of-concept validation in mouse aortic rings.
Weaknesses are minor:
(1) Some mutagenesis data (e.g., partial loss at L312A) could benefit from complementary structural validation.
(2) While Cav-BK nanodomains were reconstituted, direct measurement of calcium signals after mangostin application onto native smooth muscle could be valuable.
(3) The work has an impact on ion channel physiology and pharmacology, providing a mechanistic link between a natural product and vasodilation. Datasets include electrophysiology traces, mutagenesis scans, docking analyses, and aortic tension recordings. The latter, however, are preliminary in nature.
Reviewer #2 (Public review):
Summary:
In the present manuscript, Cordeiro et al. show that α-mangostin, a xanthone obtained from the fruit of the Garcinia mangostana tree, behaves as an agonist of the BK channels. The authors arrive at this conclusion through the effect of mangostin on macroscopic and single-channel currents elicited by BK channels formed by the α subunit and α + β1sununits, as well as αβ1 channels coexpressed with voltage-dependent Ca2+ (CaV1,2) channels. The single-channel experiments show that α-mangostin produces a robust increase in the probability of opening without affecting the single-channel conductance. The authors contend that α-mangostin activation of the BK channel is state-independent and molecular docking and mutagenesis suggest that α-mangostin binds to a site in the internal cavity. Importantly, α-mangostin (10 μM) alleviates the contracture promoted by noradrenaline. Mangostin is ineffective if the contracted muscles are pretreated with the BK toxin iberiotoxin.
Strengths:
The set of results combining electrophysiological measurements, mutagenesis, and molecular docking reveals α-mangostin as a potent activator of BK channels and the putative location of the α-mangostin binding site. Moreover, experiments conducted on aortic preparations from mice suggest that α-mangostin can aid in developing drugs to treat a myriad of diverse diseases involving the BK channel.
Weaknesses:
Major:
(1) Although the results indicate that α-mangostin is modifying the closed-open equilibrium, the conclusion that this can be due to a stabilization of the voltage sensor in its active configuration may prove to be wrong. It is more probable that, as has been demonstrated for other activators, the α-mangostin is increasing the equilibrium constant that defines the closed-open reaction (L in the Horrigan, Aldrich allosteric gating model for BK). The paper will gain much if the authors determine the probability of opening in a wide range of voltages, to determine how the drug is affecting (or not), the channel voltage dependence, the coupling between the voltage sensor and the pore, and the closed-open equilibrium (L).
(2) Apparently, the molecular docking was performed using the truncated structure of the human BK channel. However, it is unclear which one, since the PDB ID given in the Methods (6vg3), according to what I could find, corresponds to the unliganded, inactive PTK7 kinase domain. Be as it may, the apo and Ca2+ bound structures show that there is a rotation and a displacement of the S6 transmembrane domain. Therefore, the positions of the residues I308, L312, and A316 in the closed and open configurations of the BK channel are not the same. Hence, it is expected that the strength of binding will be different whether the channel is closed or open. This point needs to be discussed.
Minor:
(1) From Figure 3A, it is apparent that the increase in Po is at the expense of the long periods (seconds) that the channel remains closed. One might suggest that α-mangostin increases the burst periods. It would be beneficial if the authors measured both closed and open dwell times to test whether α-mangostin primarily affects the burst periods.
(2) In several places, the authors make similarities in the mode of action of other BK activators and α-mangostin; however, the work of Gessner et al. PNAS 2012 indicates that NS1619 and Cym04 interact with the S6/RCK linker, and Webb et al. demonstrated that GoSlo-SR-5-6 agonist activity is abolished when residues in the S4/S5 linker and in the S6C region are mutated. These findings indicate that binding of the agonist is not near the selectivity filter, as the authors' results suggest that α-mangostin binds.
(3) The sentence starting in line 452 states that there is a pronounced allosteric coupling between the voltage sensors and Ca2+ binding. If the authors are referring to the coupling factor E in the Horrigan-Aldrich gating model, the references cited, in particular, Sun and Horrigan, concluded that the coupling between those sensors is weak.
Reviewer #3 (Public review):
Summary:
This research shows that a-mangostin, a proposed nutraceutical, with cardiovascular protective properties, could act through the activation of large conductance potassium permeable channels (BK). The authors provide convincing electrophysiological evidence that the compound binds to BK channels and induces a potent activation, increasing the magnitude of potassium currents. Since these channels are important modulators of the membrane potential of smooth muscle in vascular tissue, this activation leads to muscle relaxation, possibly explaining cardiovascular protective effects.
Strengths:
The authors present evidence based on several lines of experiments that a-mangostin is a potent activator of BK channels. The quality of the experiments and the analysis is high and represents an appropriate level of analysis. This research is timely and provides a basis to understand the physiological effects of natural compounds with proposed cardio-protective effects.
Weaknesses:
The identification of the binding site is not the strongest point of the manuscript. The authors show that the binding site is probably located in the hydrophobic cavity of the pore and show that point mutations reduce the magnitude of the negative voltage shift of activation produced by a-mangostin. However, these experiments do not demonstrate binding to these sites, and could be explained by allosteric effects on gating induced by the mutations themselves.
Author response:
We sincerely thank the reviewers and editors for their thoughtful evaluations of our work. We are grateful for the careful reading, constructive critiques, and encouraging comments regarding the electrophysiological analyses, mutagenesis, and vascular experiments. The suggestions provided have been very helpful, and we are working to address these points in our revision to strengthen the manuscript and improve its clarity.
In revising the manuscript, we plan to clarify several text passages as recommended by the reviewers, and review and refine the discussion for improved precision. Following the suggestions of the reviewers, we plan to perform a number of additional experiments to provide more data for the binding region and for further mechanistic and physiological insight. We will prepare a point-by-point response addressing all issues raised in a detailed rebuttal. Additionally, we will include improvements in the Methods section as suggested by the SciScore core report.
We appreciate the opportunity to revise our work and thank the reviewers again for their valuable feedback.
eLife Assessment
The one-carbon tetrahydrofolate metabolism plays a crucial role in producing essential metabolic intermediates. In this study, the authors employ a genetics-based approach to demonstrate that three different metabolic pathways are essential for synthesizing 1C-tetrahydrofolates (1C-THF). Disrupting any of these pathways impairs both growth and virulence. Although the work presented is valuable, the experimental evidence remains incomplete without direct quantification of folate intermediates.
Reviewer #1 (Public review):
Summary:
This study identifies three redundant pathways-glycine cleavage system (GCS), serine hydroxymethyltransferase (GlyA), and formate-tetrahydrofolate ligase/FolD-that feed the one-carbon tetrahydrofolate (1C-THF) pool essential for Listeria monocytogenes growth and virulence. Reactivation of the normally inactive fhs gene rescues 1C-THF deficiency, revealing metabolic plasticity and vulnerability for potential antimicrobial targeting
Strengths:
(1) Novel evolutionary insight - reversible reactivation of a pseudogene (fhs) shows adaptive metabolic plasticity, relevant for pathogen evolution.
(2) They systematically combine targeted gene deletions with suppressor screening to dissect the folate/one-carbon network (GCS, GlyA, Fhs/FolD).
Weaknesses:
(1) The study infers 1C-THF depletion mostly genetically and indirectly (growth rescue with adenine) without direct quantification of folate intermediates or fluxes. Biochemical confirmation, LC-MS-based metabolomics of folates/1C donors, or isotopic tracing would strengthen mechanistic claims.
(2) In multiple result sections, the authors report data from technical triplicates but do not mention independent biological replicates (e.g., Figure 2C, Figure 4A-B, Figure 6D). In addition, some results mention statistical significance but without a detailed description of the specific statistical tests used or replicates, such as Figure 2A-C, Figure 2E, and Figure 2G-I.
Reviewer #2 (Public review):
Summary:
The manuscript by Freier et al examines the impact of deletion of the glycine cleavage system (GCS) GcvPAB enzyme complex in the facultative intracellular bacterial pathogen Listeria monocytogenes. GcvPAB mediates the oxidative decarboxylation of glycine as a first step in a pathway that leads to the generation of N5, N10-methylene-Tetrahydrofolate (THF) to replenish the 1-carbon THF (1C-THF) pool. 1C-THF species are important for the biosynthesis of purines and pyrimidines as well as for the formation of serine, methionine, and N-formylmethionine, and the authors have previously demonstrated that gcvPAB is important for bacterial replication within macrophages. A significant defect for growth is observed for the gcvPAB deletion mutant in defined media, and this growth defect appears to stem from the sensitivity of the mutant strain to excess glycine, which is hypothesized to further deplete the 1C-THF pool. Selection of suppressor mutations that restored growth of gcvPAB deletion mutants in synthetic media with high glycine yielded mutants that reversed stop codon inactivation of the formate-tetrahydrofolate ligase (fhs) gene, supporting the premise that generation of N10-formyl-THF can restore growth. Mutations within the folk, codY, and glyA genes, encoding serine hydroxymethyltransferase, were also identified, although the functional impact of these mutations is somewhat less clear. Overall, the authors report that their work identifies three pathways that feed the 1C-THF pool to support the growth and virulence of L. monocytogenes and that this work represents the first example of the spontaneous reactivation of a L. monocytogenes gene that is inactivated by a premature stop codon.
Strengths:
This is an interesting study that takes advantage of a naturally existing fhs mutant Listeria strain to reveal the contributions of different pathways leading to 1C-THF synthesis. The defects observed for the gcvPAB mutant in terms of intracellular growth and virulence are somewhat subtle, indicating that bacteria must be able to access host sources (such as adenine?) to compensate for the loss of purine and fMet synthesis. Overall, the authors do a nice job of assessing the importance of the pathways identified for 1C-THF synthesis.
Weaknesses:
(1) Line 114 and Figure 1: The authors indicate that the gcvPAB deletion forms significantly fewer plaques in addition to forming smaller plaques (although this is a bit hard to see in the plaque images). A reduction in the overall number of plaques sounds like a bacterial invasion defect - has this been carefully assessed? The smaller plaque size makes sense with reduced bacterial replication, but I'm not sure I understand the reduction in plaque number.
(2) Do other Listeria strains contain the stop codon in fhs? How common is this mutation? That would be interesting to know.
(3) Based on the observation that fhs+ ΔgcvPAB ΔglyA mutant is only possible to isolate in complex media, and fhs is responsible for converting formate to 1C-THF with the addition of FolD, have the authors thought of supplementing synthetic media with formate and assessing mutant growth?
Reviewer #3 (Public review):
Summary:
In this study, Freier et al. demonstrate that 3 distinct metabolic pathways are critical for the synthesis of 1C-THF, a metabolite that is crucial for the growth and virulence of Listeria monocytogenes. Using an elegant suppressor screen, they also demonstrate the hierarchical importance of these metabolic pathways with respect to the biosynthesis of 1C-THF.
Strengths:
This study uses elegant bacterial genetics to confirm that 3 distinct metabolic pathways are critical for 1C-THF synthesis in L. monocytogenes, and the lack of either one of these pathways compromises bacterial growth and virulence. The study uses a combination of in vitro growth assays, macrophage-CFU assays, and murine infection models to demonstrate this.
Weaknesses:
(1) The primary finding of the study is that the perturbation of any of the 3 metabolic pathways important for the synthesis of 1C-THF results in reduced growth and virulence of L. monocytogenes. However, there is no evidence demonstrating the levels of 1C-THF in the various knockouts and suppressor mutants used in this study. It is important to measure the levels of this metabolite (ideally using mass spectrometry) in the various knockouts and suppressor mutants, to provide strong causality.
(2) The story becomes a little hard to follow since macrophage-CFU assays and murine infection model data precede the in vitro growth assays. The manuscript would benefit from a reorganization of Figures 2,3, and 4 for better readability and flow of data.
eLife Assessment
The study highlights development of a multiplex coregulator TR-FRET (CRT) assay that detects ligands with theoretical full agonist, partial agonist, antagonist, and inverse agonist signatures within the same chemical series. The findings are valuable and will have theoretical and practical implications in the subfield, with respect to guiding the design of non-lipogenic liver X receptor (LXR) agonists. The strength of the evidence is solid, whereby the methods, data, and analyses broadly support the claims with only minor weaknesses that can be dealt with through improvements in the data analysis and the discussion. This study will be of interest to experts working in the areas of pharmacology, medicinal chemistry, and drug discovery in Alzheimer's diseases and dementias.
Reviewer #1 (Public review):
Summary:
This important study functionally profiled ligands targeting the LXR nuclear receptors using biochemical assays in order to classify ligands according to pharmacological functions. Overall, the evidence is solid, but nuances in the reconstituted biochemical assays and cellular studies and terminology of ligand pharmacology limit the potential impact of the study. This work will be of interest to scientists interested in nuclear receptor pharmacology.
Strengths:
(1) The authors rigorously tested their ligand set in CRTs for several nuclear receptors that could display ligand-dependent cross-talk with LXR cellular signaling and found that all compounds display LXR selectivity when used at ~1 µM.
(2) The authors tested the ligand set for selectivity against two LXR isoforms (alpha and beta). Most compounds were found to be LXRbeta-specific.
(3) The authors performed extensive LXR CRTs, performed correlation analysis to cellular transcription and gene expression, and classification profiling using heatmap analysis-seeking to use relatively easy-to-collect biochemical assays with purified ligand-binding domain (LBD) protein to explain the complex activity of full-length LXR-mediated transcription.
Weaknesses:
(1) The descriptions of some observations lack detail, which limits understanding of some key concepts.
(2) The presence of endogenous NR ligands within cells may confound the correlation of ligand activity of cellular assays to biochemical assay data.
(3) The normalization of biochemical assay data could confound the classification of graded activity ligands.
(4) The presence of >1 coregulator peptide in the biplex (n=2 peptides) CRT (pCRT) format will bias the LBD conformation towards the peptide-bound form with the highest binding affinity, which will impact potency and interpretation of TR-FRET data.
(5) Correlation graphical plots lack sufficient statistical testing.
(6) Some of the proposed ligand pharmacology nomenclature is not clear and deviates from classifications used currently in the field (e.g., hard and soft antagonist; weak vs. partial agonist, definition of an inverse agonist that is not the opposite function to an agonist).
Reviewer #2 (Public review):
Summary:
In this manuscript by Laham and co-workers, the authors profiled structurally diverse LXR ligands via a coregulator TR-FRET (CRT) assay for their ability to recruit coactivators and kick off corepressors, while identifying coregulator preference and LXR isoform selectivity.
The relative ligand potencies measured via CRT for the two LXR isoforms were correlated with ABCA1 induction or lipogenic activation of SRE, depending on cellular contexts (i.e, astrocytoma or hepatocarcinoma cells). While these correlations are interesting, there is some leeway to improve the quantitative presentation of these correlations. Finally, the CRT signatures were correlated with the structural stabilization of the LXR: coregulator complexes. In aggregate, this study curated a set of LXR ligands with disparate agonism signatures that may guide the design of future nonlipogenic LXR agonists with potential therapeutic applications for cardiovascular disease, Alzheimer's, and type 2 diabetes, without inducing mechanisms that promote fat/lipid production.
Strengths:
This study has many strengths, from curating an excellent LXR compound set to the thoughtful design of the CRT and cellular assays. The design of a multiplexed precision CRT (pCRT) assay that detects corepressor displacement as a function of ligand-induced coactivator recruitment is quite impressive, as it allows measurement of ligand potencies to displace corepressors in the presence of coactivators, which cannot be achieved in a regular CRT assay that looks at coactivator recruitment and corepressor dissociation in separate experiments.
Weaknesses:
I did not identify any major weaknesses.
eLife Assessment
This manuscript describes a valuable screening approach to identifying nanobodies with the potential to modulate gene expression via epigenetic regulators. While the concept is of interest and the screening strategy is well designed, the current evidence supporting mechanistic specificity remains incomplete.
Reviewer #1 (Public review):
Summary:
This study presents a high-throughput screening platform to identify nanobodies capable of recruiting chromatin regulators and modulating gene expression. The authors utilize a yeast display system paired with mammalian reporter assays to validate candidate nanobodies, aiming to create a modular resource for synthetic epigenetic control.
Strengths:
(1) The overall screening design combining yeast display with mammalian functional assays is innovative and scalable.
(2) The authors demonstrate proof-of-concept that nanobody-based recruitment can repress or activate reporter expression.
(3) The manuscript contributes to the growing toolkit for epigenome engineering.
Weaknesses:
(1) The manuscript does not investigate which endogenous factors are recruited by the nanobodies. While repression activity is demonstrated at the reporter level, there is no mechanistic insight into what proteins are being brought to the target site by each nanobody. This limits the interpretability and generalizability of the findings. Related to this, Figure S1B reports sequence similarity among complementarity-determining regions (CDRs) of nanobodies that scored highly in the DNMT3A screen. However, it remains unclear whether this similarity reflects convergence on a common molecular target or is coincidental. Without functional or proteomic validation, the relationship between sequence motifs and effector recruitment remains speculative.
(2) The epigenetic consequences of nanobody recruitment are also left unexplored. Despite targeting epigenetic regulators, the study does not assess changes such as DNA methylation or histone modifications. This makes it difficult to interpret whether the observed reporter repression is due to true chromatin remodeling or secondary effects.
Reviewer #2 (Public review):
Summary:
Wan, Thurm et al. use a yeast nanobody library that is thought to have diverse binders to isolate those that specifically bind to proteins of their interest. The yeast nanobody library collection in general carries enormous potential, but the challenge is to isolate binders that have specific activity. The authors posit that one reason for this isolation challenge is that the negative binders, in general, dampen the signal from the positive binders. This is a classic screening problem (one that geneticists have faced over decades) and, in general, underscores the value of developing a good secondary screen. Over many years, the authors have developed an elegant platform to carry out high-throughput silencing-based assays, thus creating the perfect secondary screen platform to isolate nanobodies that bind to chromatin regulators.
Strengths:
Highlights the enormous value of a strong secondary screen when identifying binders that can be isolated from the yeast nanobody library. This insight is generalizable, and I expect that this manuscript should help inspire many others to design such approaches.
Provides new cell-based reagents that can be used to recruit epigenetic activators or repressors to modulate gene expression at target loci.
Weaknesses:
The authors isolate DNMT3A and TET1/2 enzymes directly from cell lysates and bind these proteins to beads. It is not clear what proteins are, in fact, bound to beads at the end of the IP. Epigenetic repressors are part of complexes, and it would be helpful to know if the IP is specific and whether the IP pulls down only DNMT3A or other factors. While this does not change the underlying assumptions about the screen, it does alter the authors' conclusions about whether the nanobody exclusively recruits DNMT3A or potentially binds to other co-factors.
Using IP-MS to validate the pull-down would be a helpful addition to the manuscript, although one could very reasonably make the case that other co-factors get washed away during the course of the selection assay. Nevertheless, if there are co-factors that are structural and remain bound, these are likely to show up in the MS experiment.
eLife Assessment
This important study presents convincing evidence that uncovers a novel signaling axis impacting the post-mating response in females of the brown planthopper. The findings open several avenues for testing the molecular and neurobiological mechanisms of mating behavior in insects, although broad concerns remain about the relevance of some claims.
Reviewer #1 (Public review):
In this work, Zhang et al, through a series of well-designed experiments, present a comprehensive study exploring the roles of the neuropeptide Corazonin (CRZ) and its receptor in controlling the female post-mating response (PMR) in the brown planthopper (BPH) Nilaparvata lugen and Drosophila melanogaster. Through a series of behavioural assays, micro-injections, gene knockdowns, Crispr/Cas gene editing, and immunostaining, the authors show that both CRZ and CrzR play a vital role in the female post-mating response, with impaired expression of either leading to quicker female remating and reduced ovulation in BPH. Notably, the authors find that this signaling is entirely endogenous in BPH females, with immunostaining of male accessory glands (MAGs) showing no evidence of CRZ expression. Further, the authors demonstrate that while CRZ is not expressed in the MAGs, BPH males with Crz knocked out show transcriptional dysregulation of several seminal fluid proteins and functionally link this dysregulation to an impaired PMR in BPH. In relation, the authors also find that in CrzR mutants, the injection of neither MAG extracts nor maccessin peptide triggered the PMR in BPH females. Finally, the authors extend this study to D. melanogaster, albeit on a more limited scale, and show that CRZ plays a vital role in maintaining PMR in D. melanogaster females with impaired CRZ signaling, once again leading to quicker female remating and reduced ovulation. The authors must be commended for their expansive set of complementary experiments. The manuscript is also generally well written. Given the seemingly conserved nature of CRZ, this work is a significant addition to the literature, opening several avenues for testing the molecular and neurobiological mechanisms in which CRZ triggers the PMR.
However, there are some broad concerns/comments I had with this manuscript. The authors provide clear evidence that CRZ signaling plays a major role in the PMR of D. melanogaster, however, they provide no evidence that CRZ signaling is endogenous, as they did not check for expression in the MAGs of D. melanogaster males. Additionally, while the authors show that manipulating Crz in males leads to dysregulated seminal fluid expression and impaired PMR in BPH, the authors also find that CRZ injection in males in and of itself impairs PMR in BPH. The authors do not really address what this seemingly contradictory result could mean. While a lot of the figures have replicate numbers, the authors do not factor in replicate as an effect into their models, which they ideally should do.
Finally, while the discussion is generally well-written, it lacks a broader conclusion about the wider implications of this study and what future work building on this could look like.
Reviewer #2 (Public review):
Summary:
The work presented by Zhang and coauthors in this manuscript presents the study of the neuropeptide corazonin in modulating the post-mating response of the brown planthopper, with further validation in Drosophila melanogaster. To obtain their results, the authors used several different techniques that orthogonally demonstrate the involvement of corazonin signalling in regulating the female post-mating response in these species.
They first injected synthetic corazonin peptide into female brown planthoppers, showing altered mating receptivity in virgin females and a higher number of eggs laid after mating. The role of corazonin in controlling these post-mating traits has been further validated by knocking down the expression of the corazonin gene by RNA interference and through CRISPR-Cas9 mutagenesis of the gene. Further proof of the importance of corazonin signalling in regulating the female post-mating response has been achieved by knocking down the expression or mutagenizing the gene coding for the corazonin receptor.
Similar results have been obtained in the fruit fly Drosophila melanogaster, suggesting that corazonin signalling is involved in controlling the female post-mating response in multiple insect species.<br /> Notably, the authors also show that corazonin controls gene expression in the male accessory glands and that disruption of this pathway in males compromises their ability to elicit normal post-mating responses in their mates.
Strengths:
The study of the signalling pathways controlling the female post-mating response in insects other than Drosophila is scarce, and this limits the ability of biologists to draw conclusions about the evolution of the post-mating response in female insects. This is particularly relevant in the context of understanding how sexual conflict might work at the molecular and genetic levels, and how, ultimately, speciation might occur at this level. Furthermore, the study of the post-mating response could have practical implications, as it can lead to the development of control techniques, such as sterilization agents.
The study, therefore, expands the knowledge of one of the signalling pathways that control the female post-mating response, the corazonin neuropeptide. This pathway is involved in controlling the post-mating response in both Nilaparvata lugens (the brown planthopper) and Drosophila melanogaster, suggesting its involvement in multiple insect species.
The study uses multiple molecular approaches to convincingly demonstrate that corazonin controls the female post-mating response.
Weaknesses:
The data supporting the main claims of the manuscript are solid and convincing. The statistical analysis of some of the data might be improved, particularly by tailoring the analysis to the type of data that has been collected.
In the case of the corazonin effect in females, all the data are coherent; in the case of CRISPR-Cas9-induced mutagenesis, the analysis of the behavioural trait in heterozygotes might have helped in understanding the haplosufficiency of the gene and would have further proved the authors' point.
Less consistency was achieved in males (Figure 5): the authors show that injection of CRZ and RNAi of crz, or mutant crz, has the same effect on male fitness. However, the CRZ injection should activate the pathway, and crz RNAi and mutant crz should inhibit the pathway, yet they have the same effect. A comment about this discrepancy would have improved the clarity of the manuscript, pointing to new points that need to be clarified and opening new scientific discussion.
eLife Assessment
This valuable study addresses a critical and timely question regarding the role of a subpopulation of cortical interneurons (Chrna2-expressing Martinotti cells) in motor learning and cortical dynamics. However, while some of the behavior and imaging data are impressive, the small sample sizes and incomplete behavioral and activity analyses make interpretation difficult; therefore, they are insufficient to support the central conclusions. The study may be of interest to neuroscientists studying cortical neural circuits, motor learning, and motor control.
Reviewer #1 (Public review):
In this study, the authors investigated a specific subtype of SST-INs (layer 5 Chrna2-expressing Martinotti cells) and examined its functional role in motor learning. Using endoscopic calcium imaging combined with chemogenetics, they showed that activation of Chrna2 cells reduces the plasticity of pyramidal neuron (PyrN) assemblies but does not affect the animals' performance. However, activating Chrna2 cells during re-training improved performance. The authors claim that activating Chrna2 cells likely reduces PyrN assembly plasticity during learning and possibly facilitates the expression of already acquired motor skills.
There are many major issues with the study. The findings across experiments are inconsistent, and it is unclear how the authors performed their analyses or why specific time points and comparisons were chosen. The study requires major re-analysis and additional experiments to substantiate its conclusions.
Major Points:
(1a) Behavior task - the pellet-reaching task is a well-established paradigm in the motor learning field. Why did the authors choose to quantify performance using "success pellets per minute" instead of the more conventional "success rate" (see PMID 19946267, 31901303, 34437845, 24805237)? It is also confusing that the authors describe sessions 1-5 as being performed on a spoon, while from session 6 onward, the pellets are presented on a plate. However, in lines 710-713, the authors define session 1 as "naïve," session 2 as "learning," session 5 as "training," and "retraining" as a condition in which a more challenging pellet presentation was introduced. Does "naïve session 1" refer to the first spoon session or to session 6 (when the food is presented on a plate)? The same ambiguity applies to "learning session 2," "training session 5," and so on. Furthermore, what criteria did the authors use to designate specific sessions as "learning" versus "training"? Are these definitions based on behavioral performance thresholds or some biological mechanisms? Clarifying these distinctions is essential for interpreting the behavioral results.
(1b) Judging from Figures 1F and 4B, even in WT mice, it is not convincing that the animals have actually learned the task. In all figures, the mice generally achieve ~10-20 pellets per minute across sessions. The only sessions showing slightly higher performance are session 5 in Figure 1F ("train") and sessions 12 and 13 in Figure 4B ("CLZ"). In the classical pellet-reaching task, animals are typically trained for 10-12 sessions (approximately 60 trials per session, one session per day), and a clear performance improvement is observed over time. The authors should therefore present performance data for each individual session to determine whether there is any consistent improvement across days. As currently shown, performance appears largely unchanged across sessions, raising doubts about whether motor learning actually occurred.
(1c) The authors also appear to neglect existing literature on the role of SST-INs in motor learning and local circuit plasticity (e.g., PMID 26098758, 36099920). Although the current study focuses on a specific subpopulation of SST-INs, the results reported here are entirely opposite to those of previous studies. The authors should, at a minimum, acknowledge these discrepancies and discuss potential reasons for the differing outcomes in the Discussion section.
(2a) Calcium imaging - The methodology for quantifying fluorescence changes is confusing and insufficiently described. The use of absolute ΔF values ("detrended by baseline subtraction," lines 565-567) for analyses that compare activity across cells and animals (e.g., Figure 1H) is highly unconventional and problematic. Calcium imaging is typically reported as ΔF/F₀ or z-scores to account for large variations in baseline fluorescence (F₀) due to differences in GCaMP expression, cell size, and imaging quality. Absolute ΔF values are uninterpretable without reference to baseline intensity - for example, a ΔF of 5 corresponds to a 100% change in a dim cell (F₀ = 5) but only a 1% change in a bright cell (F₀ = 500). This issue could confound all subsequent population-level analyses (e.g., mean or median activity) and across-group comparisons. Moreover, while some figures indicate that normalization was performed, the Methods section lacks any detailed description of how this normalization was implemented. The critical parameters used to define the baseline are also omitted. The authors should reprocess the imaging data using a standardized ΔF/F₀ or z-score approach, explicitly define the baseline calculation procedure, and revise all related figures and statistical analyses accordingly.
(2b) Figure 1G - It is unclear why neural activity during successful trials is already lower one second before movement onset. Full traces with longer duration before and after movement onset should also be shown. Additionally, only data from "session 2 (learning)" and a single neuron are presented. The authors should present data across all sessions and multiple neurons to determine whether this observation is consistent and whether it depends on the stage of learning.
(2c) Figure 1H - The authors report that chemogenetic activation of Chrna2 cells induces differential changes in PyrN activity between successful and failed trials. However, one would expect that activating all Chrna2 cells would strongly suppress PyrN activity rather than amplifying the activity differences between trials. The authors should clarify the mechanism by which Chrna2 cell activation could exaggerate the divergence in PyrN responses between successful and failed trials. Perhaps, performing calcium imaging of Chrna2 cells themselves during successful versus failed trials would provide insight into their endogenous activity patterns and help interpret how their activation influences PyrN activity during successful and failed trials.
(2d) Figure 1H - Also, in general, the Cre⁺ (red) data points appear consistently higher in activity than the Cre⁻ (black) points. This is counterintuitive, as activating Chrna2 cells should enhance inhibition and thereby reduce PyrN activity. The authors should clarify how Cre⁺ animals exhibit higher overall PyrN activity under a manipulation expected to suppress it. This discrepancy raises concerns about the interpretation of the chemogenetic activation effects and the underlying circuit logic.
(3) The statistical comparisons throughout the manuscript are confusing. In many cases, the authors appear to perform multiple comparisons only among the N, L, T, and R conditions within the WT group. However, the central goal of this study should be to assess differences between the WT and hM3D groups. In fact, it is unclear why the authors only provide p-values for some comparisons but not for the majority of the groups.
(4a) Figure 4 - It is hard to understand why the authors introduce LFP experiments here, and the results are difficult to interpret in isolation. The authors should consider combining LFP recordings with calcium imaging (as in Figure 1) or, alternatively, repeating calcium imaging throughout the entire re-training period. This would provide a clearer link between circuit activity and behavior and strengthen the conclusions regarding Chrna2 cell function during re-training.
(4b) It is unclear why CLZ has no apparent effect in session 11, yet induces a large performance increase in sessions 12 and 13. Even then, the performance in sessions 12 and 13 (~30 successful pellets) is roughly comparable to Session 5 in Figure 1F. Given this, it is questionable whether the authors can conclude that Chrna2 cell activation truly facilitates previously acquired motor skills?
(5) Figure 5 - The authors report decreased performance in the pasta-handling task (presumably representing a newly learned skill) but observe no difference in the pellet-reaching task (presumably an already acquired skill). This appears to contradict the authors' main claim that Chrna2 cell activation facilitates previously acquired motor skills.
(6) Supplementary Figure 1 - The c-fos staining appears unusually clean. Previous studies have shown that even in home-cage mice, there are substantial numbers of c-fos⁺ cells in M1 under basal conditions (PMID 31901303, 31901303). Additionally, the authors should present Chrna2 cell labeling and c-fos staining in separate channels. As currently shown, it is difficult to determine whether the c-fos⁺ cells are truly Chrna2 cells⁺.
Overall, the authors selectively report statistical comparisons only for findings that support their claims, while most other potentially informative comparisons are omitted. Complete and transparent reporting is necessary for proper interpretation of the data.
Reviewer #2 (Public review):
Summary:
In this manuscript, Malfatti et al. study the role of Chrna2 Martinotti cells (Mα2 cells), a subset of SST interneurons, for motor learning and motor cortex activity. The authors trained mice on a forelimb prehension task while recording neuronal activity of pyramidal cells using calcium imaging with a head-mounted miniscope. While chemogenetically increasing Mα2 cell activity did not affect motor learning, it changed pyramidal cell activity such that activity peaks became sharper and differently timed than in control mice. Moreover, co-active neuronal assemblies become more stable with a smaller spatial distribution. Increasing Mα2 cell activity in previously trained mice did increase performance on the prehension task and led to increased theta and gamma band activity in the motor cortex. On the other hand, genetic ablation of Mα2 cells affected fine motor movements on a pasta handling task while not affecting the prehension task.
Strengths:
The proposed question of how Chrna2-expressing SST interneurons affect motor learning and motor cortex activity is important and timely. The study employs sophisticated approaches to record neuronal activity and manipulate the activity of a specific neuronal population in behaving mice over the course of motor learning. The authors analyze a variety of neuronal activity parameters, comparing different behavior trials, stages of learning, and the effects of Mα2 cell activation. The analysis of neuronal assembly activity and stability over the course of learning by tracking individual neurons throughout the imaging sessions is notable, since technically challenging, and yielded the interesting result that neuronal assemblies are more stable when activating Mα2 cells.
Overall, the study provides compelling evidence that Mα2 cells regulate certain aspects of motor behaviors, likely by shaping circuit activity in the motor cortex.
Weaknesses:
The main limitation of the study lies in its small sample sizes and the absence of key control experiments, which substantially weaken the strength of the conclusions.
Core findings of this paper, such as the lack of effect of Mα2 cell activation on motor learning, as well as the altered neuronal activity, rely ona sample size of n=3 mice per condition, which is likely underpowered to detect differences in behavior and contributes to the somewhat disconnected results on calcium activity, activity timing, and neuronal assembly activity.
More comprehensive analyses and data presentation are also needed to substantiate the results. For example, examining calcium activity and behavioral performance on a trial-by-trial basis could clarify whether closely spaced reaching attempts influence baseline signals and skew interpretation.
The study uses cre-negative mice as controls for hM3Dq-mediated activation, which does not account for potential effects of Cre-dependent viral expression that occur only in Cre-positive mice.
This important control would be necessary to substantiate the conclusion that it is increased Mα2 cell activity that drives the observed changes in behavior and cortical activity.
eLife Assessment
This valuable study shows that regions of the human auditory cortex that respond strongly to voices are also sensitive to vocalizations from closely related primate species. The study is methodologically solid, though additional analyses - particularly those isolating the acoustic features that differentiate chimpanzee from bonobo calls - would further strengthen the conclusions. With additional analyses and discussions, the work has the potential to offer key insights into the evolutionary continuity of voice processing and would be of interest to researchers studying auditory processing and evolutionary neuroscience in general.
Reviewer #1 (Public review):
Summary:
This study investigates how human temporal voice areas (TVA) respond to vocalizations from nonhuman primates. Using functional MRI during a species-categorization task, the authors compare neural responses to calls from humans, chimpanzees, bonobos, and macaques while modeling both acoustic and phylogenetic factors. They find that bilateral anterior TVA regions respond more strongly to chimpanzee than to other nonhuman primate vocalizations, suggesting that these regions are sensitive not only to human voices but also to acoustically and evolutionarily related sounds.
The work provides important comparative evidence for continuity in primate vocal communication and offers a strong empirical foundation for modeling how specific acoustic features drive TVA activity.
Strengths:
(1) Comparative scope: The inclusion of four primate species, including both great apes and monkeys, provides a rare and valuable cross-species perspective on voice processing.
(2) Methodological rigor: Acoustic and phylogenetic distances are carefully quantified and incorporated into the analyses.
(4) Neuroscientific significance: The finding of TVA sensitivity to chimpanzee calls supports the view that human voice-selective regions are evolutionarily tuned to certain acoustic features shared across primates.
(4) Clear presentation: The study is well organized, the stimuli well controlled, and the imaging analyses transparent and replicable.
(5) Theoretical contribution: The results advance understanding of the neural bases of voice perception and the evolutionary roots of voice sensitivity in the human brain.
Weaknesses:
(1) Acoustic-phylogenetic confound: The design does not fully disentangle acoustic similarity from phylogenetic proximity, as species co-vary along both dimensions. A promising way to address this would be to include an additional model focusing on the acoustic features that specifically differentiate bonobo from chimpanzee calls, which share equal phylogenetic distance to humans.
(2) Selectivity vs. sensitivity: Without non-vocal control sounds, the study cannot determine whether TVA responses reflect true selectivity for primate vocalizations or general auditory sensitivity.<br /> <br /> (3) Task demands: The use of an active categorization task may engage additional cognitive processes beyond auditory perception; a passive listening condition would help clarify the contribution of attention and task performance.
(4) Figures and presentation: Some results are partially redundant; keeping only the most representative model figure in the main text and moving others to the Supplementary Material would improve clarity.
Reviewer #2 (Public review):
Summary:
This study investigated how the human brain responds to vocalizations from multiple primate species, including humans, chimpanzees, bonobos, and rhesus macaques. The central finding - that subregions of the temporal voice areas (TVA), particularly in the bilateral anterior superior temporal gyrus, show enhanced responses to chimpanzee vocalizations - suggests a potential neural sensitivity to calls from phylogenetically close nonhuman primates.
Strengths:
The authors employed three analytical models to consistently demonstrate activation in the anterior superior temporal gyrus that is specific to chimpanzee calls. The methodology was logical and robust, and the results supporting these findings appear solid.
Weakness:
The interpretation of the findings in this paper regarding the evolutionary continuity of voice processing lacks sufficient evidence. A simple explanation is that the observed effects can be attributed to the similarity in low-level acoustic features, rather than effects specific to phylogenetically close species. The authors only tested vocalizations from three non-human primate species, other than humans. In this case, the species specificity of the effect does not fully represent the specificity of evolutionary relatedness.
Reviewer #3 (Public review):
Summary:
Ceravolo et al. employed functional magnetic resonance imaging (fMRI) to examine how the temporal voice areas (TVA) in the human brain respond to vocalizations from different nonhuman primate species. Their findings reveal that the human TVA is not only responsible for human vocalizations but also exhibits sensitivity to the vocalizations of other primates, particularly chimpanzee vocalizations sharing acoustic similarities with human voices, which offers compelling evidence for cross-species vocal processing in the human auditory system. Overall, the study presents intellectually stimulating hypotheses and demonstrates methodological originality. However, the current findings are not yet solid enough to fully support the proposed claims, and the presentation could be enhanced for clarity and impact.
Strengths:
The study presents intellectually stimulating hypotheses and demonstrates methodological originality.
Weaknesses:
(1) The analysis of the fMRI data does not account for the participants' behavioral performance, specifically their reaction times (RTs) during the species categorization task.
(2) The figure organization/presentation requires significant revision to avoid confusion and redundancy.
eLife Assessment
This valuable simulation study proposes a new coarse-grained model to explain the effects of CpG methylation on nucleosome wrapping energy. The model accurately reproduces the all-atom molecular dynamics simulation data, and the evidence to support the claims in the paper is solid. This work will be of interest to researchers working on gene regulation, mechanisms of DNA methylation and effects of DNA methylation on nucleosome positioning.
Reviewer #1 (Public review):
In this manuscript, the authors used a coarse-grained DNA model (cgNA+) to explore how DNA sequences and CpG methylation/hydroxymethylation influence nucleosome wrapping energy and the probability density of optimal nucleosomal configuration. Their findings indicate that both methylated and hydroxymethylated cytosines lead to increased nucleosome wrapping energy. Additionally, the study demonstrates that methylation of CpG islands increases the probability of nucleosome formation.
The major strength of this method is that the model explicitly includes the phosphate group as DNA-histone binding site constraints, enhancing CG model accuracy and computational efficiency and allowing comprehensive calculations of DNA mechanical properties and deformation energies.
The revised version has addressed the concerns raised previously, significantly strengthening the study.
Reviewer #2 (Public review):
Summary:
This study uses a coarse-grained model for double stranded DNA, cgNA+, to assess nucleosome sequence affinity. cgNA+ coarse-grains DNA on the level of bases and accounts also explicitely for the positions of the backbone phosphates. It has been proven to reproduce all-atom MD data very accurately. It is also ideally suited to be incorporated into a nucleosome model because it is known that DNA is bound to the protein core of the nucleosome via the phosphates.
It is still unclear whether this harmonic model parametrized for unbound DNA is accurate enough to describe DNA inside the nucleosome. Previous models by other authors, using more coarse-grained models of DNA, have been rather successful in predicting base pair sequence dependent nucleosome behavior. This is at least the case as long as DNA shape is concerned whereas assessing the role of DNA bendability (something this paper focuses on) has been consistingly challenging in all nucleosome models to my knowledge.
It is thus of major interest whether this more sophisticated model is also more successful in handling this issue. As far as I can tell the work is technically sound and properly accounts for not only the energy required in wrapping DNA but also entropic effects, namely the change in entropy that DNA experiences when going from the free state to the bound state. The authors make an approximation here which seems to me to be a reasonable first step.
Of interest is also that the authors have the parameters at hand to study the effect of methylation of CpG-steps. This is especially interesting as this allows to study a scenario where changes in the physical properties of base pair steps via methylation might influence nucleosome positioning and stability in a cell-type specific way.
Overall, this is an important contribution to the questions of how sequence affects nucleosome positioning and affinity. The findings suggest that cgNA+ has something new to offer. But the problem is complex, also on the experimental side, so many questions remain open. Despite of this, I highly recommend publication of this manuscript.
Strengths:
The authors use their state-of-the-art coarse grained DNA model which seems ideally suited to be applied to nucleosomes as it accounts explicitly for the backbone phosphates.
Weaknesses:
The authors introduce penalty coefficients c_i to avoid steric clashes between the two DNA turns in the nucleosome. This requires c_i-values that are so high that standard deviations in the fluctuations of the simulation are smaller than in the experiments.
Reviewer #3 (Public review):
Summary:
In this study, authors utilize biophysical modeling to investigate differences in free energies and nucleosomal configuration probability density of CpG islands and nonmethylated regions in the genome. Toward this goal, they develop and apply the cgNA+ coarse-grained model, an extension of their prior molecular modeling framework.
Strengths:
The study utilizes biophysical modeling to gain mechanistic insight into nucleosomal occupancy differences in CpG and nonmethylated regions in the genome.
Weaknesses:
Although the overall study is interesting, the manuscripts need more clarity in places. Moreover, the rationale and conclusion for some of the analyses are not well described.
Comments on revised version:
The authors have addressed my concerns.
Author response:
The following is the authors’ response to the original reviews.
Reviewer #1 (Public Review):
Summary:
In this manuscript, the authors used a coarse-grained DNA model (cgNA+) to explore how DNA sequences and CpG methylation/hydroxymethylation influence nucleosome wrapping energy and the probability density of optimal nucleosomal configuration. Their findings indicate that both methylated and hydroxymethylated cytosines lead to increased nucleosome wrapping energy. Additionally, the study demonstrates that methylation of CpG islands increases the probability of nucleosome formation.
Strengths:
The major strength of this method is the model explicitly includes phosphate group as DNA-histone binding site constraints, enhancing CG model accuracy and computational efficiency and allowing comprehensive calculations of DNA mechanical properties and deformation energies.
Weaknesses:
A significant limitation of this study is that the parameter sets for the methylated and hydroxymethylated CpG steps in the cgNA+ model are derived from all-atom molecular dynamics (MD) simulations that use previously established force field parameters for modified cytosines (P´erez A, et al. Biophys J. 2012; Battistini, et al. PLOS Comput Biol. 2021). These parameters suggest that both methylated and hydroxymethylated cytosines increase DNA stiffness and nucleosome wrapping energy, which could predispose the coarse-grained model to replicate these findings. Notably, conflicting results from other all-atom MD simulations, such as those by Ngo T in Nat. Commun. 2016, shows that hydroxymethylated cytosines increase DNA flexibility, contrary to methylated cytosines. If the cgNA+ model were trained on these later parameters or other all-atom MD force fields, different conclusions might be obtained regarding the effects of methylated and hydroxymethylation on nucleosome formation.
Despite the training parameters of the cgNA+ model, the results presented in the manuscript indicate that methylated cytosines increase both DNA stiffness and nucleosome wrapping energy. However, when comparing nucleosome occupancy scores with predicted nucleosome wrapping energies and optimal configurations, the authors find that methylated CGIs exhibit higher nucleosome occupancies than unmethylated ones, which seems to contradict the expected relationship where increased stiffness should reduce nucleosome formation affinity. In the manuscript, the authors also admit that these conclusions “apparently runs counter to the (perhaps naive) intuition that high nucleosome forming affinity should arise for fragments with low wrapping energy”. Previous all-atom MD simulations (P´erez A, et al. Biophys J. 2012; Battistini, et al. PLOS Comput Biol. 202; Ngo T, et al. Nat. Commun. 20161) show that the stiffer DNA upon CpG methylation reduces the affinity of DNA to assemble into nucleosomes or destabilizes nucleosomes. Given these findings, the authors need to address and reconcile these seemingly contradictory results, as the influence of epigenetic modifications on DNA mechanical properties and nucleosome formation are critical aspects of their study.
Understanding the influence of sequence-dependent and epigenetic modifications of DNA on mechanical properties and nucleosome formation is crucial for comprehending various cellular processes. The authors’ study, focusing on these aspects, definitely will garner interest from the DNA methylation research community.
Training the cgNA+ model on alternative MD simulation datasets is certainly of interest to us. However, due to the significant computational cost, this remains a goal for future work. The relationship between nucleosome occupancy scores and nucleosome wrapping energy is still debated, as noted in our Discussion section. The conflicting results may reflect differences in experimental conditions and the contribution of cellular factors other than DNA mechanics to nucleosome formation in vivo. For instance, P´erez et al. (2012), Battistini et al. (2021), and Ngo et al. (2016) concluded that DNA methylation reduces nucleosome formation based on experiments with modified Widom 601 sequences. In contrast, the genome-wide methylation study by Collings and Anderson (2017) found the opposite effect. In our work, we also use whole-genome nucleosome occupancy data.
Comments on revised version:
The authors have addressed most of my comments and concerns regarding this manuscript.
Reviewer #2 (Public Review):
Summary:
This study uses a coarse-grained model for double stranded DNA, cgNA+, to assess nucleosome sequence affinity. cgNA+ coarse-grains DNA on the level of bases and accounts also explicitly for the positions of the backbone phosphates. It has been proven to reproduce all-atom MD data very accurately. It is also ideally suited to be incorporated into a nucleosome model because it is known that DNA is bound to the protein core of the nucleosome via the phosphates.
It is still unclear whether this harmonic model parametrized for unbound DNA is accurate enough to describe DNA inside the nucleosome. Previous models by other authors, using more coarse-grained models of DNA, have been rather successful in predicting base pair sequence dependent nucleosome behavior. This is at least the case as long as DNA shape is concerned whereas assessing the role of DNA bendability (something this paper focuses on) has been consistently challenging in all nucleosome models to my knowledge.
It is thus of major interest whether this more sophisticated model is also more successful in handling this issue. As far as I can tell the work is technically sound and properly accounts for not only the energy required in wrapping DNA but also entropic effects, namely the change in entropy that DNA experiences when going from the free state to the bound state. The authors make an approximation here which seems to me to be a reasonable first step.
Of interest is also that the authors have the parameters at hand to study the effect of methylation of CpG-steps. This is especially interesting as this allows to study a scenario where changes in the physical properties of base pair steps via methylation might influence nucleosome positioning and stability in a cell-type specific way.
Overall, this is an important contribution to the questions of how sequence affects nucleosome positioning and affinity. The findings suggest that cgNA+ has something new to offer. But the problem is complex, also on the experimental side, so many questions remain open. Despite of this, I highly recommend publication of this manuscript.
Strengths:
The authors use their state-of-the-art coarse grained DNA model which seems ideally suited to be applied to nucleosomes as it accounts explicitly for the backbone phosphates.
Weaknesses:
The authors introduce penalty coefficients c<sub>i</sub> to avoid steric clashes between the two DNA turns in the nucleosome. This requires c<sub>i</sub>-values that are so high that standard deviations in the fluctuations of the simulation are smaller than in the experiments.
Indeed, smaller c<sub>i</sub> values lead to steric clashes between the two turns of DNA. A possible improvement of our optimisation method and a direction of future work would be adding a penalty which prevents steric clashes to the objective function. Then the c<sub>i</sub> values could be reduced to have bigger fluctuations that are even closer to the experimental structures.
Reviewer #3 (Public Review):
Summary:
In this study, authors utilize biophysical modeling to investigate differences in free energies and nucleosomal configuration probability density of CpG islands and nonmethylated regions in the genome. Toward this goal, they develop and apply the cgNA+ coarse-grained model, an extension of their prior molecular modeling framework.
Strengths:
The study utilizes biophysical modeling to gain mechanistic insight into nucleosomal occupancy differences in CpG and nonmethylated regions in the genome.
Weaknesses:
Although the overall study is interesting, the manuscripts need more clarity in places. Moreover, the rationale and conclusion for some of the analyses are not well described.
We have revised the manuscript in accordance with the reviewer’s latest suggestions.
Comments on revised version:
Authors have attempted to address previously raised concerns.
Reviewer #1 (Recommendations for the authors):
The authors have addressed most of my comments and concerns regarding this manuscript. Among them, the most significant pertains to fitting the coarse-grained model using a different all-atom force field to verify the conclusions. The authors acknowledged this point but noted the computational cost involved and proposed it as a direction for future work. Overall, I recommend the revised version for publication.
Reviewer #2 (Recommendations for the authors):
My previous comments were addressed satisfactorily.
Reviewer #3 (Recommendations for the authors):
Authors have attempted to address previously raised concerns. However, some concerns listed below remain that need to be addressed.
(1) The first reviewer makes a valid point regarding the reconciliation of conflicting observations related to nucleosome-forming affinity and wrapping energy. Unfortunately, the authors don’t seem to address this and state that this will be the goal for the future study.
Training the cgNA+ model on alternative MD simulation datasets remains future work. However, we revised the Discussion section to more clearly address the conflicting experimental findings in the literature on how DNA methylation influences nucleosome formation.
(2) Please report the effect size and statistical significance value for Figures 7 and 8, as this information is currently not provided, despite the authors’ claim that these observations are statistically significant.
This information is now presented in Supplementary Tables S1-S4.
(3) In response to the discrepancy in cell lines for correlating nucleosome occupancy and methylation analyses, the authors claim that there is no publicly available nucleosome occupancy and methylation data for a human cell type within the human genome. This claim is confusing, as the GM12878 cell line has been extensively characterized with MNaseseq and WGBS.
We thank the reviewer for this remark. We have removed the statement regarding the lack of data from the manuscript; we intend to examine the suggested cell line in future research.
(4) In response to my question, the authors claimed that they selected regions from chromosome 1 exclusively; however, the observation remains unchanged when considering sequence samples from different genomic regions. They should provide examples from different chromosomes as part of the supplementary information to further support this.
The examples of corresponding plots for other nucleosomes are now shown in Supplementary Figure S9.
eLife Assessment
This useful study identifies knowledge of letter shape as a distinct component of letter knowledge and shows that children acquire it even before formal reading instruction and without knowing the corresponding letter sounds. However, the evidence supporting the main conclusions is incomplete at the current stage. With additional analyses examining the relationships among the underlying variables and/or revising interpretations, the work would be of broad interest to researchers studying language and vision.
Reviewer #1 (Public review):
Summary:
This study examines letter-shape knowledge in a large cohort of children with minimal formal reading instruction. The authors report that these children can reliably distinguish upright from inverted letters despite limited letter naming abilities. They also show a visual-search advantage for upright over inverted letters, and this advantage correlates with letter-shape familiarity. These findings suggest that specialized letter-shape representations can emerge with very limited letter-sound mapping practice.
Strengths:
This study investigates whether children can develop letter-shape knowledge independently of letter-sound mapping abilities. This question is theoretically important, especially in light of functional subdivisions within the visual word form area (VWFA), with posterior regions associated with letter/orthographic shape and anterior regions with linguistic features of orthography (Caffarra et al., 2021; Lerma-Usabiaga et al., 2018). The study also includes a large sample of children at the very beginning of formal reading instruction, thereby minimizing the influence of explicit instruction on the formation of letter-shape knowledge.
Weakness:
A central concern is that a production task (naming) is used to index letter-name knowledge, whereas letter-shape knowledge is assessed with recognition. Production tasks impose additional demands (motor planning, articulation) and typically yield lower performance than recognition tasks (e.g., letter-sound verification). Thus, comparisons between letter-shape and letter-name knowledge are confounded by task type. The authors' partial-correlation and multiple-regression analyses linking familiarity (but not production) to the upright-search advantage are informative; however, they do not resolve the recognition-versus-production mismatch. Consequently, the current data cannot unambiguously support the claim that letter-shape representations are independent of letter-name knowledge.
Reviewer #2 (Public review):
Summary:
In this study, the authors propose that there are two types of letter knowledge: knowledge about letter sound and knowledge about letter shape. Based on previous studies on implicit statistical learning in adults and babies, the authors hypothesized that passive exposure to letters in the environment allows early readers to acquire knowledge of letter shapes even before knowledge of letter-sound association. Children performed a set of experiments that measures letter shape familiarity, letter-sound association performance, visual processing of letters, and a reading-related cognitive skill. The results show that even the children who have little to no knowledge of letter names are familiar with letter shapes, and that this letter shape familiarity is predictive of performance in visual processing of letters.
Strengths:
The authors' hypothesis is based on widely accepted findings in vision science that repeated exposure to certain stimuli promotes implicit learning of, for example, statistical properties of the stimuli. They used simple and well-established tasks in large-scale experiments with a special population (i.e., children). The data analysis is quite comprehensive, accounting for any alternative explanations when needed. The data support at least a part of their hypothesis that the knowledge of letter shapes is distinct from, and precedes, the knowledge of letter-sound association, and is associated with performance in visual processing of the letters. This study shed light on a rather overlooked aspect of letter knowledge, i.e., letter shapes, challenging the idea that letters are learned only through formal instruction and calling for future research on the role of passive exposure to letters in reading acquisition.
Weaknesses:
Although the authors have successfully identified the knowledge of letter shapes as another type of letter knowledge other than the knowledge of letter-sound association, the question of whether it drives the subsequent reading acquisition remains largely unanswered, despite it being strongly implied in the Introduction. The authors collected a RAN score, which is known to robustly predict future reading fluency, but it did not show a significant partial correlation with familiarity accuracy (i.e., familiarity accuracy is not necessary to predict RAN score). The authors discussed that the performance in visual processing of letters might capture unique variance in reading fluency unexplained by RAN scores, but currently, this claim seems speculative.
Since even children without formal literacy instruction were highly familiar with letter shapes, it would be reasonable to assume that they had obtained the knowledge through passive exposure. However, the role of passive exposure was not directly tested in the study.
Given the superimposed straight lines in Figure 2, I assume the authors computed Pearson correlation coefficients. Testing the statistical significance of the Pearson correlation coefficient requires the assumption of bivariate normality (and therefore constant variance of a variable across the range of the other). According to Figure 2, this doesn't seem to be met, as the familiarity accuracy is hitting the ceiling. The ceiling effect might not be critical in Figure 2, since it tends to attenuate correlation, not inflate it. But in Figures 3 and 4, the authors' conclusion depends on the non-significant partial correlation. In fact, the authors themselves wrote that the ceiling effect might lead to a non-significant correlation even if there is an actual effect (line 404).
Reviewer #3 (Public review):
Summary:
This study examined how young children with minimal reading instruction process letters, focusing on their familiarity with letter shapes, knowledge of letter names, and visual discrimination of upright versus inverted letters. Across four experiments, kindergarten and Grade 1 children could identify the correct orientation of letters even without knowing their names.
Strengths:
This study addresses an important research gap by examining whether children develop letter familiarity prior to formal literacy instruction and how this skill relates to reading-related cognitive abilities. By emphasizing letter familiarity alongside letter recognition, the study highlights a potentially overlooked yet important component of emergent literacy development.
Weaknesses:
The study's methods and results do not effectively test its stated research goals. Reading ability was not directly measured; instead, the authors inferred its relationship with reading from correlations between letter familiarity and reading-related cognitive measures, which limits the validity of their conclusions. Furthermore, the analytical approach was rather limited, relying primarily on simple and partial correlations without employing more advanced statistical methods that could better capture the underlying relationships.
Major Comments:
(1) Limited Novelty and Unclear Theoretical Contribution:
The authors aim to challenge the view that children acquire letter shape knowledge only through formal literacy instruction, but similar questions regarding letter familiarity have already been explored in previous research. The manuscript does not clearly articulate how the present study advances beyond existing findings or why examining letter familiarity specifically before formal instruction provides new theoretical insight. Moreover, if letter familiarity and letter recognition are treated as distinct constructs, the authors should better justify their differentiation and clarify the theoretical significance of focusing on familiarity as an independent component of emergent literacy.
(2) Overgeneralization to Reading Ability:
Although the study measured several literacy-related cognitive skills and examined correlations with letter familiarity, it did not directly assess children's reading ability, as participants had not yet received formal literacy instruction. Therefore, the conclusion that letter familiarity influences reading skills (e.g., Line 519: "Our results are broadly consistent with previous work that has highlighted print letter knowledge as a strong predictor of future reading skills") is not fully supported and should be clarified or revised. To draw conclusions about the impact on reading ability, a longitudinal study would be more appropriate, assessing the relationship between letter familiarity and reading skills after children have received formal literacy instruction. If a longitudinal study is not feasible, measuring familial risk for dyslexia could provide an alternative approach to infer the potential influence of letter familiarity on later reading development.
(3) Confusing and Limited Analytical Approach with Potential for More Sophisticated Modeling:
The study employs a confusing analytical approach, alternating between simple correlational analyses and group-based comparisons, which may introduce circularity - for example, defining high vs. low familiarity groups partly based on performance differences in upright versus inverted letters and then observing a visual search advantage for upright letters within these groups. Moreover, the analyses are relatively simple: although multiple linear regression is mentioned, the results are not fully reported. These approaches may not fully capture the complex relationships among letter familiarity, recognition, visual search performance, RAN, and other covariates. More sophisticated modeling, such as mixed-effects models to account for repeated measures, structural equation modeling to examine latent constructs, or multivariate approaches jointly modeling familiarity and recognition effects, could provide a clearer understanding of the unique contribution of letter shape familiarity to early literacy outcomes. In addition, a large number of correlations were conducted without correction for multiple comparisons, which may increase the risk of false positives and raise concerns about the reliability of some significant findings.
--- The true parameters, starting values, parameter estimates, and their standard errors are: --- true pars starting values par estimates standard errors msigmaslow 150.00000 150.65207 150.65207 0.82817 beta_m 0.01000 0.00995 0.00994 0.00004 beta_v 0.10000 0.10575 0.10575 0.02735 sigma 200.00000 200.23232 200.23232 1.56670 rho -0.25000 -0.24442 -0.24442 0.01538
Why does the US have retail investor data?
eLife Assessment
This important work develops a new protocol to experimentally perturb target genes across a quantitative range of expression levels in cell lines. The evidence supporting their new perturbation approach is convincing, and we propose that focusing on single modality (activation or inhibition) would be sufficient to draw their conclusions. The study will be of broad interest to scientists in the fields of functional genomics and biotechnology.
Reviewer #1 (Public review):
In this manuscript, Domingo et al. present a novel perturbation-based approach to experimentally modulate the dosage of genes in cell lines. Their approach is capable of gradually increasing and decreasing gene expression. The authors then use their approach to perturb three key transcription factors and measure the downstream effects on gene expression. Their analysis of the dosage response curve of downstream genes reveals marked non-linearity.
One of the strengths of this study is that many of the perturbations fall within the physiological range for each cis gene. This range is presumably between a single-copy state of heterozygous loss-of-function (log fold change of -1) and a three-copy state (log fold change of ~0.6). This is in contrast with CRISPRi or CRISPRa studies that attempt to maximize the effect of the perturbation, which may result in downstream effects that are not representative of physiological responses.
Another strength of the study is that various points along the dosage-response curve were assayed for each perturbed gene. This allowed the authors to effectively characterize the degree of linearity and monotonicity of each dosage-response relationship. Ultimately, the study revealed that many of these relationships are non-linear, and that the response to activation can be dramatically different than the response to inhibition.
To test their ability to gradually modulate dosage, the authors chose to measure three transcription factors and around 80 known downstream targets. As the authors themselves point out in their discussion about MYB, this biased sample of genes makes it unclear how this approach would generalize genome-wide. In addition, the data generated from this small sample of genes may not represent genome-wide patterns of dosage response. Nevertheless, this unique data set and approach represents a first step in understanding dosage-response relationships between genes.
Another point of general concern in such screens is the use of the immortalized K562 cell line. It is unclear how the biology of these cell lines translates to the in vivo biology of primary cells. However, the authors do follow up with cell-type-specific analyses (Figures 4B, 4C, and 5A) to draw correspondence between their perturbation results and the relevant biology in primary cells and complex diseases.
The conclusions of the study are generally well supported with statistical analysis throughout the manuscript. As an example, the authors utilize well-known model selection methods to identify when there was evidence for non-linear dosage response relationships.
Gradual modulation of gene dosage is a useful approach to model physiological variation in dosage. Experimental perturbation screens that use CRISPR inhibition or activation often use guide RNAs targeting the transcription start site to maximize their effect on gene expression. Generating a physiological range of variation will allow others to better model physiological conditions.
There is broad interest in the field to identify gene regulatory networks using experimental perturbation approaches. The data from this study provides a good resource for such analytical approaches, especially since both inhibition and activation were tested. In addition, these data provide a nuanced, continuous representation of the relationship between effectors and downstream targets, which may play a role in the development of more rigorous regulatory networks.
Human geneticists often focus on loss-of-function variants, which represent natural knock-down experiments, to determine the role of a gene in the biology of a trait. This study demonstrates that dosage response relationships are often non-linear, meaning that the effect of a loss-of-function variant may not necessarily carry information about increases in gene dosage. For the field, this implies that others should continue to focus on both inhibition and activation to fully characterize the relationship between gene and trait.
Comments on revisions:
Thank you for responding to our comments. We have no further comments for the authors.
Reviewer #2 (Public review):
Summary:
This work investigates transcriptional responses to varying levels of transcription factors (TFs). The authors aim for gradual up- and down-regulation of three transcription factors GFI1B, NFE2 and MYB in K562 cells, by using a CRISPRa- and a CRISPRi line, together with sgRNAs of varying potency. Targeted single-cell RNA sequencing is then used to measure gene expression of a set of 90 genes, which were previously shown to be downstream of GFI1B and NFE2 regulation. This is followed by an extensive computational analysis of the scRNA-seq dataset. By grouping cells with the same perturbations, the authors can obtain groups of cells with varying average TF expression levels. The achieved perturbations are generally subtle, not reaching half or double doses for most samples, and up-regulation is generally weak below 1.5-fold in most cases. Even in this small range, many target genes exhibit a non-linear response. Since this is rather unexpected, it is crucial to rule out technical reasons for these observations.
Strengths:
The work showcases how a single dataset of CRISPRi/a perturbations with scRNA-seq readout and an extended computational analysis can be used to estimate transcriptome dose-responses, a general approach that likely can be built upon in the future.<br /> Moreover, the authors highlight tiling of sgRNAs +/-1000bp around TSS as a useful approach. Compared with conventional direct TSS-targeting (+/- 200 bp), the larger sequence window allows placing more sgRNAs. Also it requires little prior knowledge of CREs, and avoids using "attenuated" sgRNAs which would require specialized sgRNA design.
Weaknesses:
The experiment was performed in a single replicate and it would have been reassuring to see an independent validation of the main findings, for example through measuring individual dose-response curves .
Much of the analysis depends on the estimation of log-fold changes between groups of single cells with non-targeting controls and those carrying a guide RNA driving a specific knockdown. Generally, biological replicates are recommended for differential gene expression testing (Squair et al. 2021, https://doi.org/10.1038/s41467-021-25960-2). When using the FindMarkers function from the Seurat package, the authors divert from the recommendations for pseudo-bulk analysis to aggregate the raw counts (https://satijalab.org/seurat/articles/de_vignette.html). Furthermore, differential gene expression analysis of scRNA-seq data can suffer from mis-estimations (Nguyen et al. 2023, https://doi.org/10.1038/s41467-023-37126-3), and different computational tools or versions can affect these estimates strongly (Pullin et al. 2024, https://doi.org/10.1186/s13059-024-03183-0 and Rich et al. 2024, https://doi.org/10.1101/2024.04.04.588111). Therefore it would be important to describe more precisely in the Methods how this analysis was performed, any deviations from default parameters, package versions, and at which point which values were aggregated to form "pseudobulk" samples.
Two different cell lines are used to construct dose-response curves, where a CRISPRi line allows gene down-regulation and the CRISPRa line allows gene upregulation. Although both lines are derived from the same parental line (K562) the expression analysis of Tet2, which is absent in the CRISPRi line, but expressed in the CRISPRa line (Fig. S1F, S3A) suggests clonal differences between the two lines. Similarly, the UMAP in S3C and the PCA in S4A suggest batch effects between the two lines. These might confound this analysis, even though all fold changes are calculated relative to the baseline expression in the respective cell line (NTC cells). Combining log2-fold changes from the two cell lines with different baseline expression into a single curve (e.g. Fig. 3) remains misleading, because different data points could be normalized to different base line expression levels.
The study estimates the relationship between TF dose and target gene expression. This requires a system that allows quantitative changes in TF expression. The data provided does not convincingly show that this condition is met, which however is an essential prerequisite for the presented conclusions. Specifically, the data shown in Fig. S3A shows that upon stronger knock-down, a subpopulation of cells appear, where the targeted TF is not detected any more (drop-outs). Also in Fig. 3B (top) suggests that the knock-down is either subtle (similar to NTCs) or strong, but intermediate knock-down (log2-FC of 0.5-1) does not occur. Although the authors argue that this is a technical effect of the scRNA-seq protocol, it is also possible that this represents a binary behavior of the CRISPRi system. Previous work has shown that CRISPRi systems with the KRAB domain largely result in binary repression and not in gradual down-regulation as suggested in this study (Bintu et al. 2016 (https://doi.org/10.1126/science.aab2956), Noviello et al. 2023 (https://doi.org/10.1038/s41467-023-38909-4)).
One of the major conclusions of the study is that non-linear behavior is common. It would be helpful to show that this observation does not arise from the technical concerns described in the previous points. This could be done for instance with independent experimental validations.
Did the authors achieve their aims? Do the results support the conclusions?:
Some of the most important conclusions, such as the claim that non-linear responses are common, are not well supported because they rely on accurately determining the quantitative responses of trans genes, which suffers from the previously mentioned concerns.
Discussion of the likely impact of the work on the field, and the utility of the methods and data to the community:
Together with other recent publications, this work emphasizes the need to study transcription factor function with quantitative perturbations. The computational code repository contains all the valuable code with inline comments, but would have benefited from a readme file explaining the repository structure, package versions, and instructions to reproduce the analyses, including which input files or directory structure would be needed.
Author response:
The following is the authors’ response to the original reviews.
Reviewer #1 (Public review):
In this manuscript, Domingo et al. present a novel perturbation-based approach to experimentally modulate the dosage of genes in cell lines. Their approach is capable of gradually increasing and decreasing gene expression. The authors then use their approach to perturb three key transcription factors and measure the downstream effects on gene expression. Their analysis of the dosage response curve of downstream genes reveals marked non-linearity.
One of the strengths of this study is that many of the perturbations fall within the physiological range for each cis gene. This range is presumably between a single-copy state of heterozygous loss-of-function (log fold change of -1) and a three-copy state (log fold change of ~0.6). This is in contrast with CRISPRi or CRISPRa studies that attempt to maximize the effect of the perturbation, which may result in downstream effects that are not representative of physiological responses.
Another strength of the study is that various points along the dosage-response curve were assayed for each perturbed gene. This allowed the authors to effectively characterize the degree of linearity and monotonicity of each dosage-response relationship. Ultimately, the study revealed that many of these relationships are non-linear, and that the response to activation can be dramatically different than the response to inhibition.
To test their ability to gradually modulate dosage, the authors chose to measure three transcription factors and around 80 known downstream targets. As the authors themselves point out in their discussion about MYB, this biased sample of genes makes it unclear how this approach would generalize genome-wide. In addition, the data generated from this small sample of genes may not represent genome-wide patterns of dosage response. Nevertheless, this unique data set and approach represents a first step in understanding dosage-response relationships between genes.
Another point of general concern in such screens is the use of the immortalized K562 cell line. It is unclear how the biology of these cell lines translates to the in vivo biology of primary cells. However, the authors do follow up with cell-type-specific analyses (Figures 4B, 4C, and 5A) to draw a correspondence between their perturbation results and the relevant biology in primary cells and complex diseases.
The conclusions of the study are generally well supported with statistical analysis throughout the manuscript. As an example, the authors utilize well-known model selection methods to identify when there was evidence for non-linear dosage response relationships.
Gradual modulation of gene dosage is a useful approach to model physiological variation in dosage. Experimental perturbation screens that use CRISPR inhibition or activation often use guide RNAs targeting the transcription start site to maximize their effect on gene expression. Generating a physiological range of variation will allow others to better model physiological conditions.
There is broad interest in the field to identify gene regulatory networks using experimental perturbation approaches. The data from this study provides a good resource for such analytical approaches, especially since both inhibition and activation were tested. In addition, these data provide a nuanced, continuous representation of the relationship between effectors and downstream targets, which may play a role in the development of more rigorous regulatory networks.
Human geneticists often focus on loss-of-function variants, which represent natural knock-down experiments, to determine the role of a gene in the biology of a trait. This study demonstrates that dosage response relationships are often non-linear, meaning that the effect of a loss-of-function variant may not necessarily carry information about increases in gene dosage. For the field, this implies that others should continue to focus on both inhibition and activation to fully characterize the relationship between gene and trait.
We thank the reviewer for their thoughtful and thorough evaluation of our study. We appreciate their recognition of the strengths of our approach, particularly the ability to modulate gene dosage within a physiological range and to capture non-linear dosage-response relationships. We also agree with the reviewer’s points regarding the limitations of gene selection and the use of K562 cells, and we are encouraged that the reviewer found our follow-up analyses and statistical framework to be well-supported. We believe this work provides a valuable foundation for future genome-wide applications and more physiologically relevant perturbation studies.
Reviewer #2 (Public review):
Summary:
This work investigates transcriptional responses to varying levels of transcription factors (TFs). The authors aim for gradual up- and down-regulation of three transcription factors GFI1B, NFE2, and MYB in K562 cells, by using a CRISPRa- and a CRISPRi line, together with sgRNAs of varying potency. Targeted single-cell RNA sequencing is then used to measure gene expression of a set of 90 genes, which were previously shown to be downstream of GFI1B and NFE2 regulation. This is followed by an extensive computational analysis of the scRNA-seq dataset. By grouping cells with the same perturbations, the authors can obtain groups of cells with varying average TF expression levels. The achieved perturbations are generally subtle, not reaching half or double doses for most samples, and up-regulation is generally weak below 1.5-fold in most cases. Even in this small range, many target genes exhibit a non-linear response. Since this is rather unexpected, it is crucial to rule out technical reasons for these observations.
We thank the reviewer for their detailed and thoughtful assessment of our work. We are encouraged by their recognition of the strengths of our study, including the value of quantitative CRISPR-based perturbation coupled with single-cell transcriptomics, and its potential to inform gene regulatory network inference. Below, we address each of the concerns raised:
Strengths:
The work showcases how a single dataset of CRISPRi/a perturbations with scRNA-seq readout and an extended computational analysis can be used to estimate transcriptome dose responses, a general approach that likely can be built upon in the future.
Weaknesses:
(1) The experiment was only performed in a single replicate. In the absence of an independent validation of the main findings, the robustness of the observations remains unclear.
We acknowledge that our study was performed in a single pooled experiment. While additional replicates would certainly strengthen the findings, in high-throughput single-cell CRISPR screens, individual cells with the same perturbation serve as effective internal replicates. This is a common practice in the field. Nevertheless, we agree that biological replicates would help control for broader technical or environmental effects.
(2) The analysis is based on the calculation of log-fold changes between groups of single cells with non-targeting controls and those carrying a guide RNA driving a specific knockdown. How the fold changes were calculated exactly remains unclear, since it is only stated that the FindMarkers function from the Seurat package was used, which is likely not optimal for quantitative estimates. Furthermore, differential gene expression analysis of scRNA-seq data can suffer from data distortion and mis-estimations (Heumos et al. 2023 (https://doi.org/10.1038/s41576-023-00586-w), Nguyen et al. 2023 (https://doi.org/10.1038/s41467-023-37126-3)). In general, the pseudo-bulk approach used is suitable, but the correct treatment of drop-outs in the scRNA-seq analysis is essential.
We thank the reviewer for highlighting recent concerns in the field. A study benchmarking association testing methods for perturb-seq data found that among existing methods, Seurat’s FindMarkers function performed the best (T. Barry et al. 2024).
In the revised Methods, we now specify the formula used to calculate fold change and clarify that the estimates are derived from the Wilcoxon test implemented in Seurat’s FindMarkers function. We also employed pseudo-bulk grouping to mitigate single-cell noise and dropout effects.
(3) Two different cell lines are used to construct dose-response curves, where a CRISPRi line allows gene down-regulation and the CRISPRa line allows gene upregulation. Although both lines are derived from the same parental line (K562) the expression analysis of Tet2, which is absent in the CRISPRi line, but expressed in the CRISPRa line (Figure S3A) suggests substantial clonal differences between the two lines. Similarly, the PCA in S4A suggests strong batch effects between the two lines. These might confound this analysis.
We agree that baseline differences between CRISPRi and CRISPRa lines could introduce confounding effects if not appropriately controlled for. We emphasize that all comparisons are made as fold changes relative to non-targeting control (NTC) cells within each line, thereby controlling for batch- and clone-specific baseline expression. See figures S4A and S4B.
(4) The study uses pseudo-bulk analysis to estimate the relationship between TF dose and target gene expression. This requires a system that allows quantitative changes in TF expression. The data provided does not convincingly show that this condition is met, which however is an essential prerequisite for the presented conclusions. Specifically, the data shown in Figure S3A shows that upon stronger knock-down, a subpopulation of cells appears, where the targeted TF is not detected anymore (drop-outs). Also Figure 3B (top) suggests that the knock-down is either subtle (similar to NTCs) or strong, but intermediate knock-down (log2-FC of 0.5-1) does not occur. Although the authors argue that this is a technical effect of the scRNA-seq protocol, it is also possible that this represents a binary behavior of the CRISPRi system. Previous work has shown that CRISPRi systems with the KRAB domain largely result in binary repression and not in gradual down-regulation as suggested in this study (Bintu et al. 2016 (https://doi.org/10.1126/science.aab2956), Noviello et al. 2023 (https://doi.org/10.1038/s41467-023-38909-4)).
Figure S3A shows normalized expression values, not fold changes. A pseudobulk approach reduces single-cell noise and dropout effects. To test whether dropout events reflect true binary repression or technical effects, we compared trans-effects across cells with zero versus low-but-detectable target gene expression (Figure S3B). These effects were highly concordant, supporting the interpretation that dropout is largely technical in origin. We agree that KRAB-based repression can exhibit binary behavior in some contexts, but our data suggest that cells with intermediate repression exist and are biologically meaningful. In ongoing unpublished work, we pursue further analysis of these data at the single cell level, and show that for nearly all guides the dosage effects are indeed gradual rather than driven by binary effects across cells.
(5) One of the major conclusions of the study is that non-linear behavior is common. This is not surprising for gene up-regulation, since gene expression will reach a plateau at some point, but it is surprising to be observed for many genes upon TF down-regulation. Specifically, here the target gene responds to a small reduction of TF dose but shows the same response to a stronger knock-down. It would be essential to show that his observation does not arise from the technical concerns described in the previous point and it would require independent experimental validations.
This phenomenon—where relatively small changes in cis gene dosage can exceed the magnitude of cis gene perturbations—is not unique to our study. This also makes biological sense, since transcription factors are known to be highly dosage sensitive and generally show a smaller range of variation than many other genes (that are regulated by TFs). Empirically, these effects have been observed in previous CRISPR perturbation screens conducted in K562 cells, including those by Morris et al. (2023), Gasperini et al. (2019), and Replogle et al. (2022), to name but a few studies that our lab has personally examined the data of.
(6) One of the conclusions of the study is that guide tiling is superior to other methods such as sgRNA mismatches. However, the comparison is unfair, since different numbers of guides are used in the different approaches. Relatedly, the authors point out that tiling sometimes surpassed the effects of TSS-targeting sgRNAs, however, this was the least fair comparison (2 TSS vs 10 tiling guides) and additionally depends on the accurate annotation of TSS in the relevant cell line.
We do not draw this conclusion simply from observing the range achieved but from a more holistic observation. We would like to clarify that the number of sgRNAs used in each approach is proportional to the number of base pairs that can be targeted in each region: while the TSS-targeting strategy is typically constrained to a small window of a few dozen base pairs, tiling covers multiple kilobases upstream and downstream, resulting in more guides by design rather than by experimental bias. The guides with mismatches do not have a great performance for gradual upregulation.
We would also like to point out that the observation that the strongest effects can arise from regions outside the annotated TSS is not unique to our study and has been demonstrated in prior work (referenced in the text).
To address this concern, we have revised the text to clarify that we do not consider guide tiling to be inherently superior to other approaches such as sgRNA mismatches. Rather, we now describe tiling as a practical and straightforward strategy to obtain a wide range of gene dosage effects without requiring prior knowledge beyond the approximate location of the TSS. We believe this rephrasing more accurately reflects the intent and scope of our comparison.
(7) Did the authors achieve their aims? Do the results support the conclusions?: Some of the most important conclusions are not well supported because they rely on accurately determining the quantitative responses of trans genes, which suffers from the previously mentioned concerns.
We appreciate the reviewer’s concern, but we would have wished for a more detailed characterization of which conclusions are not supported, given that we believe our approach actually accounts for the major concerns raised above. We believe that the observation of non-linear effects is a robust conclusion that is also consistent with known biology, with this paper introducing new ways to analyze this phenomenon.
(8) Discussion of the likely impact of the work on the field, and the utility of the methods and data to the community:
Together with other recent publications, this work emphasizes the need to study transcription factor function with quantitative perturbations. Missing documentation of the computational code repository reduces the utility of the methods and data significantly.
Documentation is included as inline comments within the R code files to guide users through the analysis workflow.
Reviewer #1 (Recommendations for the authors):
In Figure 3C (and similar plots of dosage response curves throughout the manuscript), we initially misinterpreted the plots because we assumed that the zero log fold change on the horizontal axis was in the middle of the plot. This gives the incorrect interpretation that the trans genes are insensitive to loss of GFI1B in Figure 3C, for instance. We think it may be helpful to add a line to mark the zero log fold change point, as was done in Figure 3A.
We thank the reviewer for this helpful suggestion. To improve clarity, we have added a vertical line marking the zero log fold change point in Figure 3C and all similar dosage-response plots. We agree this makes the plots easier to interpret at a glance.
Similarly, for heatmaps in the style of Figure 3B, it may be nice to have a column for the non-targeting controls, which should be a white column between the perturbations that increase versus decrease GFI1B.
We appreciate the suggestion. However, because all perturbation effects are computed relative to the non-targeting control (NTC) cells, explicitly including a separate column for NTC in the heatmap would add limited interpretive value and could unnecessarily clutter the figure. For clarity, we have emphasized in the figure legend that the fold changes are relative to the NTC baseline.
We found it challenging to assess the degree of uncertainty in the estimation of log fold changes throughout the paper. For example, the authors state the following on line 190: "We observed substantial differences in the effects of the same guide on the CRISPRi and CRISPRa backgrounds, with no significant correlation between cis gene fold-changes." This claim was challenging to assess because there are no horizontal or vertical error bars on any of the points in Figure 2A. If the log fold change estimates are very noisy, the data could be consistent with noisy observations of a correlated underlying process. Similarly, to our understanding, the dosage response curves are fit assuming that the cis log fold changes are fixed. If there is excessive noise in the estimation of these log fold changes, it may bias the estimated curves. It may be helpful to give an idea of the amount of estimation error in the cis log fold changes.
We agree that assessing the uncertainty in log fold change estimates is important for interpreting both the lack of correlation between CRISPRi and CRISPRa effects (Figure 2A) and the robustness of the dosage-response modeling.
In response, we have now updated Figure 2A to include both vertical and horizontal error bars, representing the standard errors of the log2 fold-change estimates for each guide in the CRISPRi and CRISPRa conditions. These error estimates were computed based on the differential expression analysis performed using the FindMarkers function in Seurat, which models gene expression differences between perturbed and control cells. We also now clarify this in the figure legend and methods.
The authors mention hierarchical clustering on line 313, which identified six clusters. Although a dendrogram is provided, these clusters are not displayed in Figure 4A. We recommend displaying these clusters alongside the dendrogram.
We have added colored bars indicating the clusters to improve the clarity. Thank you for the suggestion.
In Figures 4B and 4C, it was not immediately clear what some of the gene annotations meant. For example, neither the text nor the figure legend discusses what "WBCs", "Platelets", "RBCs", or "Reticulocytes" mean. It would be helpful to include this somewhere other than only the methods to make the figure more clear.
To improve clarity, we have updated the figure legends for Figures 4B and 4C to explicitly define these abbreviations.
We struggled to interpret Figure 4E. Although the authors focus on the association of MYB with pHaplo, we would have appreciated some general discussion about the pattern of associations seen in the figure and what the authors expected to observe.
We have changed the paragraph to add more exposition and clarification:
“The link between selective constraint and response properties is most apparent in the MYB trans network. Specifically, the probability of haploinsufficiency (pHaplo) shows a significant negative correlation with the dynamic range of transcriptional responses (Figure 4G): genes under stronger constraint (higher pHaplo) display smaller dynamic ranges, indicating that dosage-sensitive genes are more tightly buffered against changes in MYB levels. This pattern was not reproduced in the other trans networks (Figure 4E)”.
Line 71: potentially incorrect use of "rending" and incorrect sentence grammar.
Fixed
Line 123: "co-expression correlation across co-expression clusters" - authors may not have intended to use "co-expression" twice.
Original sentence was correct.
Line 246: "correlations" is used twice in "correlations gene-specific correlations."
Fixed.
Reviewer #2 (Recommendations for the authors):
(1) To show that the approach indeed allows gradual down-regulation it would be important to quantify the know-down strength with a single-cell readout for a subset of sgRNAs individually (e.g. flowfish/protein staining flow cytometry).
We agree that single-cell validation of knockdown strength using orthogonal approaches such as flowFISH or protein staining would provide additional support. However, such experiments fall outside the scope of the current study and are not feasible at this stage. We note that the observed transcriptomic changes and dosage responses across multiple perturbations are consistent with effective and graded modulation of gene expression.
(2) Similarly, an independent validation of the observed dose-response relationships, e.g. with individual sgRNAs, can be helpful to support the conclusions about non-linear responses.
Fig. S4C includes replication of trans-effects for a handful of guides used both in this study and in Morris et al. While further orthogonal validation of dose-response relationships would be valuable, such extensive additional work is not currently feasible within the scope of this study. Nonetheless, the high degree of replication in Fig. S4C as well as consistency of patterns observed across multiple sgRNAs and target genes provides strong support for the conclusions drawn from our high-throughput screen.
(3) The calculation of the log2 fold changes should be documented more precisely. To perform a pseudo-bulk analysis, the raw UMI counts should be summed up in each group (NTC, individual targeting sgRNAs), including zero counts, then the data should be normalized and the fold change should be calculated. The DESeq package for example would be useful here.
We have updated the methods in the manuscript to provide more exposition of how the logFC was calculated:
“In our differential expression (DE) analysis, we used Seurat’s FindMarkers() function, which computes the log fold change as the difference between the average normalized gene expression in each group on the natural log scale:
Logfc = log_e(mean(expression in group 1)) - log_e(mean(expression in group 2))
This is calculated in pseudobulk where cells with the same sgRNA are grouped together and the mean expression is compared to the mean expression of cells harbouring NTC guides. To calculate per-gene differential expression p-value between the two cell groups (cells with sgRNA vs cells with NTC), Wilcoxon Rank-Sum test was used”.
(4) A more careful characterization of the cell lines used would be helpful. First, it would be useful to include the quality controls performed when the clonal lines were selected, in the manuscript. Moreover, a transcriptome analysis in comparison to the parental cell line could be performed to show that the cell lines are comparable. In addition, it could be helpful to perform the analysis of the samples separately to see how many of the response behaviors would still be observed.
Details of the quality control steps used during the selection of the CRISPRa clonal line are already included in the Methods section, and Fig. S4A shows the transcriptome comparison of CRISPRi and CRISPRa lines also for non-targeting guides. Regarding the transcriptomic comparison with the parental cell line, we agree that such an analysis would be informative; however, this would require additional experiments that are not feasible within the scope of the current study. Finally, while analyzing the samples separately could provide further insight into response heterogeneity, we focused on identifying robust patterns across perturbations that are reproducible in our pooled screening framework. We believe these aggregate analyses capture the major response behaviors and support the conclusions drawn.
(5) In general we were surprised to see such strong responses in some of the trans genes, in some cases exceeding the fold changes of the cis gene perturbation more than 2x, even at the relatively modest cis gene perturbations (Figures S5-S8). How can this be explained?
This phenomenon—where trans gene responses can exceed the magnitude of cis gene perturbations—is not unique to our study. Similar effects have been observed in previous CRISPR perturbation screens conducted in K562 cells, including those by Morris et al. (2023), Gasperini et al. (2019), and Replogle et al. (2022).
Several factors may contribute to this pattern. One possibility is that certain trans genes are highly sensitive to transcription factor dosage, and therefore exhibit amplified expression changes in response to relatively modest upstream perturbations. Transcription factors are known to be highly dosage sensitive and generally show a smaller range of variation than many other genes (that are regulated by TFs). Mechanistically, this may involve non-linear signal propagation through regulatory networks, in which intermediate regulators or feedback loops amplify the downstream transcriptional response. While our dataset cannot fully disentangle these indirect effects, the consistency of this observation across multiple studies suggests it is a common feature of transcriptional regulation in K562 cells.
(6) In the analysis shown in Figure S3B, the correlation between cells with zero count and >0 counts for the cis gene is calculated. For comparison, this analysis should also show the correlation between the cells with similar cis-gene expression and between truly different populations (e.g. NTC vs strong sgRNA).
The intent of Figure S3B was not to compare biologically distinct populations or perform differential expression analyses—which we have already conducted and reported elsewhere in the manuscript—but rather to assess whether fold change estimates could be biased by differences in the baseline expression of the target gene across individual cells. Specifically, we sought to determine whether cells with zero versus non-zero expression (as can result from dropouts or binary on/off repression from the KRAB-based CRISPRi system) exhibit systematic differences that could distort fold change estimation. As such, the comparisons suggested by the reviewer do not directly relate to the goal of the analysis which Figure S3B was intended to show.
(7) It is unclear why the correlation between different lanes is assessed as quality control metrics in Figure S1C. This does not substitute for replicates.
The intent of Figure S1C was not to serve as a general quality control metric, but rather to illustrate that the targeted transcript capture approach yielded consistent and specific signal across lanes. We acknowledge that this may have been unclear and have revised the relevant sentence in the text to avoid misinterpretation.
“We used the protein hashes and the dCas9 cDNA (indicating the presence or absence of the KRAB domain) to demultiplex and determine the cell line—CRISPRi or CRISPRa. Cells containing a single sgRNA were identified using a Gaussian mixture model (see Methods). Standard quality control procedures were applied to the scRNA-seq data (see Methods). To confirm that the targeted transcript capture approach worked as intended, we assessed concordance across capture lanes (Figure S1C)”.
(8) Figures and legends often miss important information. Figure 3B and S5-S8: what do the transparent bars represent? Figure S1A: color bar label missing. Figure S4D: what are the lines?, Figure S9A: what is the red line? In Figure S8 some of the fitted curves do not overlap with the data points, e.g. PKM. Fig. 2C: why are there more than 96 guide RNAs (see y-axis)?
We have addressed each point as follows:
Figure 3B: The figure legend has been updated to clarify the meaning of the transparent bars.
Figures S5–S8: There are no transparent bars in these figures; we confirmed this in the source plots.
Figure S1A: The color bar label is already described in the figure legend, but we have reformulated the caption text to make this clearer.
Figure S4D: The dashed line represents a linear regression between the x and y variables. The figure caption has been updated accordingly.
Figure S9A: We clarified that the red line shows the median ∆AIC across all genes and conditions.
Figure S8: We agree that some fitted curves (e.g., PKM) do not closely follow the data points. This reflects high noise in these specific measurements; as noted in the text, TET2 is not expected to exert strong trans effects in this context.
Figure 2C: Thank you for catching this. The y-axis numbers were incorrect because the figure displays the proportion of guides (summing to 100%), not raw counts. We have corrected the y-axis label and updated the numbers in the figure to resolve this inconsistency.
(9) The code is deposited on Github, but documentation is missing.
Documentation is included as inline comments within the R code files to guide users through the analysis workflow.
(10) The methods miss a list of sgRNA target sequences.
We thank the reviewer for this observation. A complete table containing all processed data, including the sequences of the sgRNAs used in this study, is available at the following GEO link:
(11) In some parts, the language could be more specific and/or the readability improved, for example:
Line 88: "quantitative landscape".
Changed to “quantitative patterns”.
Lines 88-91: long sentence hard to read.
This complex sentence was broken up into two simpler ones:
“We uncovered quantitative patterns of how gradual changes in transcription dosage lead to linear and non-linear responses in downstream genes. Many downstream genes are associated with rare and complex diseases, with potential effects on cellular phenotypes”.
Line 110: "tiling sgRNAs +/- 1000 bp from the TSS", could maybe be specified by adding that the average distance was around 100 or 110 bps?
Lines 244-246: hard to understand.
We struggle to see the issue here and are not sure how it can be reworded.
Lines 339-342: hard to understand.
These sentences have been reworded to provide more clarity.
(12) A number of typos, and errors are found in the manuscript:
Line 71: "SOX2" -> "SOX9".
FIXED
Line 73: "rending" -> maybe "raising" or "posing"?
FIXED
Line 157: "biassed".
FIXED
Line 245: "exhibited correlations gene-specific correlations with".
FIXED
Multiple instances, e.g. 261: "transgene" -> "trans gene".
FIXED
Line 332: "not reproduced with among the other".
FIXED
Figure S11: betweenness.
This is the correct spelling
There are more typos that we didn't list here.
We went through the manuscript and corrected all the spelling errors and typos.
RRID:IMSR_JAX:030220
DOI: 10.1038/s44318-025-00624-9
Resource: RRID:IMSR_JAX:030220
Curator: @dhovakimyan1
SciCrunch record: RRID:IMSR_JAX:030220
AB_2534017
DOI: 10.1038/s44318-025-00624-9
Resource: (Thermo Fisher Scientific Cat# A10042, RRID:AB_2534017)
Curator: @scibot
SciCrunch record: RRID:AB_2534017
AB_2534016
DOI: 10.1038/s44318-025-00624-9
Resource: (Thermo Fisher Scientific Cat# A10040, RRID:AB_2534016)
Curator: @scibot
SciCrunch record: RRID:AB_2534016
RRID:AB_162542
DOI: 10.1038/s44318-025-00624-9
Resource: (Molecular Probes Cat# A-31571, RRID:AB_162542)
Curator: @scibot
SciCrunch record: RRID:AB_162542
RRID:AB_221604
DOI: 10.1038/s44318-025-00624-9
Resource: (Molecular Probes Cat# A-31553, RRID:AB_221604)
Curator: @scibot
SciCrunch record: RRID:AB_221604
AB_141709
DOI: 10.1038/s44318-025-00624-9
Resource: (Thermo Fisher Scientific Cat# A-21208, RRID:AB_2535794)
Curator: @scibot
SciCrunch record: RRID:AB_2535794
RRID:AB_1520876
DOI: 10.1038/s44318-025-00624-9
Resource: (MBL International Cat# PD022, RRID:AB_1520876)
Curator: @scibot
SciCrunch record: RRID:AB_1520876
RRID:AB_10561522
DOI: 10.1038/s44318-025-00624-9
Resource: (Thermo Fisher Scientific Cat# A-11007, RRID:AB_10561522)
Curator: @scibot
SciCrunch record: RRID:AB_10561522
RRID:AB_882455
DOI: 10.1038/s44318-025-00624-9
Resource: (Abcam Cat# ab51502, RRID:AB_882455)
Curator: @scibot
SciCrunch record: RRID:AB_882455
RRID:AB_2064130
DOI: 10.1038/s44318-025-00624-9
Resource: (Abcam Cat# ab18465, RRID:AB_2064130)
Curator: @scibot
SciCrunch record: RRID:AB_2064130
RRID:AB_310177
DOI: 10.1038/s44318-025-00624-9
Resource: (Sigma-Aldrich Cat# 06-570, RRID:AB_310177)
Curator: @scibot
SciCrunch record: RRID:AB_310177
AB_2629281
DOI: 10.6084/m9.figshare.30234790
Resource: (Abcam Cat# ab110413, RRID:AB_2629281)
Curator: @scibot
SciCrunch record: RRID:AB_2629281
AB_476744
DOI: 10.6084/m9.figshare.30234790
Resource: (Sigma-Aldrich Cat# A5441, RRID:AB_476744)
Curator: @scibot
SciCrunch record: RRID:AB_476744
AB_1843992
DOI: 10.6084/m9.figshare.30234790
Resource: (Sigma-Aldrich Cat# WH0009804M1, RRID:AB_1843992)
Curator: @scibot
SciCrunch record: RRID:AB_1843992
AB_880234
DOI: 10.6084/m9.figshare.30234790
Resource: (Abcam Cat# ab54460, RRID:AB_880234)
Curator: @scibot
SciCrunch record: RRID:AB_880234
RRID:SCR_002798
DOI: 10.6084/m9.figshare.30234790
Resource: GraphPad Prism (RRID:SCR_002798)
Curator: @scibot
SciCrunch record: RRID:SCR_002798
AB_2232946
DOI: 10.6084/m9.figshare.30234790
Resource: (Cell Signaling Technology Cat# 2867, RRID:AB_2232946)
Curator: @scibot
SciCrunch record: RRID:AB_2232946
RRID:SCR_002285
DOI: 10.6084/m9.figshare.30234790
Resource: Fiji (RRID:SCR_002285)
Curator: @scibot
SciCrunch record: RRID:SCR_002285
AB_2313567
DOI: 10.6084/m9.figshare.30234790
Resource: (Jackson ImmunoResearch Labs Cat# 111-035-003, RRID:AB_2313567)
Curator: @scibot
SciCrunch record: RRID:AB_2313567
AB_2537819
DOI: 10.6084/m9.figshare.30234790
Resource: (Thermo Fisher Scientific Cat# MA5-16308, RRID:AB_2537819)
Curator: @scibot
SciCrunch record: RRID:AB_2537819
RRID:AB_10015289
DOI: 10.6084/m9.figshare.30234790
Resource: (Yeasen Biotech Cat# 33201ES60, RRID:AB_10015289)
Curator: @scibot
SciCrunch record: RRID:AB_10015289
RRID:CVCL_0431
DOI: 10.6084/m9.figshare.30234790
Resource: (BCRJ Cat# 0293, RRID:CVCL_0431)
Curator: @scibot
SciCrunch record: RRID:CVCL_0431
RRID:CVCL_0351
DOI: 10.6084/m9.figshare.30234790
Resource: (RRID:CVCL_0351)
Curator: @scibot
SciCrunch record: RRID:CVCL_0351
RRID:AB_2534073
DOI: 10.6084/m9.figshare.30234790
Resource: (Thermo Fisher Scientific Cat# A-11005, RRID:AB_2534073)
Curator: @scibot
SciCrunch record: RRID:AB_2534073
RRID:SCR_013672
DOI: 10.6084/m9.figshare.30234790
Resource: ZEISS ZEN Microscopy Software (RRID:SCR_013672)
Curator: @scibot
SciCrunch record: RRID:SCR_013672
RRID:SCR_003193
DOI: 10.1101/2025.11.19.689362
Resource: The Cancer Genome Atlas (RRID:SCR_003193)
Curator: @scibot
SciCrunch record: RRID:SCR_003193
Reintroduce the argument introduced in your thesis statement. Reiterate the key points of your research. Offer some forecasts for the future (example: “Hopefully now with a clearer understanding about free soloing and the rock-climbing community, others might understand the draw to such a seemingly risky sport…”).
Steps to conclude your essay
Begin with a topic sentence. Using one of the five Ws or H questions here will remind you and your readers what you will focus on in this paragraph. Introduce your sources in a sentence or two to summarize what the information revealed about your topic. Include a direct quote using P.I.E. and reflect on what the source illuminated about your question.
Steps for the body paragraphs
Define the topic. Provide short background information. Introduce who your intended audience is. State what your driving research question is. Create a thesis statement by identifying the scope of the informative essay (the main point you want your audience to understand about your topic).
Steps for a successful starting paragraph
The initial stage is an introduction, which should start with the sound hook sentence to engage the reader in what a writer plans to share. One example is: “A community is generally defined by people in a group who live together in a particular area, or a group of people who are considered a unit because of their shared interests or background.”
Best to start informative essays with a good intro sentence
The point of an informative essay is not to convince others to take a certain action or stance; that role is expressly reserved for persuasive essays. Instead, the main objective is to highlight specific information about your topic. In this project, you may be asking “after researching general aspects about my topic, what do I want others to understand about it?”
Informative essays are used to educate others on your topic
The purpose of an informative essay, sometimes called an expository essay, is to educate others on a certain topic. Typically, these essays aim to answer the five Ws and H questions: who, what, where, when, why, and how.
Informative writing using the 5 w's and how
The Informative Research Report is a report that relays the results of a central research question in an organized manner through more formal sources.
Researching proper sources to make a report about
It bridges the gap between AI and Anytype's powerful features by converting Anytype's OpenAPI specification into MCP tools, allowing you to manage your knowledge base through conversation.
Interesting conversation with tools
not people
itional narratives categorized as myth are not regarded asuntrue by their native tellers. "A
Stories in ʻōiwi traditions are not made up, or just for entertainment. They come from real experiences and observations of the world and teaches people how to live, behave, and so on. These stories can hold knowledge about nature, relationships, history, community values, and more. When the West calls them "myths" it can make it seem less than what it actually is, maybe sometimes even untrue, even though they are actually really important ways of explaining what is going on.
blows might be given to the attendant as his share,according to agreeme
Old stories like this are amusing to me. This is how people used to chop it up and have a laugh
O Prince of the Faithful! the third is enough for me, givehim the two thirds!” This restored the caliph’s good temper, and, laughing heartily,he rewarded them both.4 bastinado: a form of torture that involves caning (beating with a cane) the bare soles of aperson’s feet.
This is a pretty goofy story which seems rather harmless to me. Sure there are stereotypes, but I feel like this is an almost timeless type of story where locale is irrelevant. If you told me this same story but set it in England or France or anywhere in Europe in the 8th century I would not notice and I doubt anyone would. All that would need to be changed is the people's names and the name of the Tigris.
“If you do not make melaugh, I will beat you three times with this leathern bag,”
Here we have a hint of the stereotype of despotism.
Haroun al Rashed2
I've noticed how much these tales focus on powerful figures in the East. Just an observation.
interpreter-in-chief to the British forces
This dude was very accomplished, having a genuinely useful ability and serving in several high positions.
Using ChatGPT allows students to obtain quick and direct answers by simply asking questions, which may enhance their academic performance in the short term (Alshater, 2022; Rahman & Watanobe, 2023). Consequently, students may rely more on AI for immediate solutions rather than solving problems independently. In the long term, students with low academic self-efficacy are likely to overuse AI.
why students use ChatGPT
this is one of the first studies exploring the internal antecedents and potential consequences of AI dependency
more study needs to be done on ai dependency
From a practical perspective, the results suggest that more time and energy should be invested to reduce students' academic stress and mitigate AI-dependent behaviors. Additionally, guiding students toward reasonable use of AI technology and improving their AI literacy (Ng et al., 2021) are necessary to ensure that the potential of AI technology can be fully utilized and that its negative impacts can be mitigated. Finally, addressing misinformation and enhancing the reliability of AI technology are crucial tasks that requires continuous improvement.
ways to reduce ai dependency
Therefore, we recommend that future studies reevaluate college students' dependence on AI by taking these distinct aspects into account, offering deeper insights into both the legitimate and illicit use of AI in academic environments.
ways to improve the use of Ai for college students
. The consequences of AI dependency varied; the top five negative effects were increased laziness, the spread of misinformation, decreased creativity, and reduced critical and independent thinking.
consequences of overuse of AI
The Council of Europe defines artificial intelligence as: "a set of sciences, theories, technologies, the purpose of which is to reproduce human cognitive skills by a machine ".
Another good definition of AI
Artificial intelligence, like other technologies, has positive characteristics as well as negative ones, which are discussed in the world
AI is positive and negative it depends on context.
For years, AI was an isolated phenomenon that was used on a limited theoretical level in narrow circles. Along with the development of technologies, AI has gained special relevance.
introduces the topic of AI well
Artificial intelligence (AI) is a branch of computer science that aims to create an intelligent computer machine/program that can understand human intelligence. Determining the level of intelligence depends on what task we set out to solve.
Good definition of AI
Conversely, because students used the termslang to refer to several dimensions of the languagevariety that they spoke with friends and family,we were unable to tease apart their beliefs aboutAAVE grammar, AAVE style, formal and informalregisters, and widespread slang used by all youth.Teaching students about these dimensions of dialectsand interviewing students could help educators andresearchers gain greater clarity on students' beliefsabout bidialectalism and style shifting.
Again, even those who use it have a difficult time telling the difference...why is this?
ohn recognizes the racial and socioeconomicprejudice inherent in interviewers' perceptions that
Can we recognize this prejudice whilst still participating in the system?
Students' arguments in favor of using SE in worksettings seemed to be driven more by a perceptionof negative judgments of AAVE by mainstreamsociety than by reasons such as clear communicationor professional effectiveness. In fact, 71% of studentswho discussed professional settings focused on jobinterviews rather than on-the-job work
This is expected
The regressionanalysis showed that there was a statistically significantrelationship between students with high academicachievement (semester grade of 85% or greater) andthe view that only SE should be spoken in class(p = 0.047) when gender was held constant. In otherwords, students who received a semester grade of B orbetter were more likely to believe that students shouldonly speak SE in their English classes.This finding suggests that higher achievingstudents viewed speaking SE as necessary for academicsuccess and as more compatible with their individualand peer-group identities than lower achievingstudents, as Fordham (1999) found. We found nostatistically significant relationship between genderand students' responses
Interesting. It seems that those who have had success with code-switching in this way are the most okay with it
What dialects do bidialectal AfricanAmerican adolescents think should be spoken in theirELA classes and why? The students' responses werejointly analyzed by the authors, both self-identified aswhite and speakers of SE but not AAVE.
hypothesis
Although our ideas align with sociolinguists whoargue that dialects and slang reference different kindsof language variation, we included the terms slang andinformal English in the prompt since these were the termsthat students and Ms. Lang had used interchangeablywith Black English and AAVE throughout the unit onlanguage variation.
Why is it hard to distinguish the two, even for those who speak AAVE?
In a speaking activity for beginners, roles in the dialogue areassigned to different learners and each is responsible for one part (i.e. one learns A linesand the other learns B). By mimicking and memorizing the lines, they can perform authenticlanguage and play the audio over and over to assist their practice.
For beginner speaking practice, students are given different parts in a dialogue. Each memorizes their lines, listens to recordings, and repeats them to practice real conversations.
If the orthography for numbers in the language usesEnglish Romanized symbols, then providing images that illustrate the number or spellingout the words can help learners stay in the target language. Figure 4 illustrates the imagesand Miami–Illinois numbers spelled out.
When a language uses English letters to write its numbers, learners might slip into thinking in English. To keep them thinking in the target language, teachers can show pictures of the numbers or spell the words fully in that language
An initial challenge is that they maybe transcribed in an orthography that is not transparent to those who have not been trainedin its use. At the content level, some concepts may not be suitable for all potential learneraudiences. They also tend to be third-person narratives and may or may not include inter-active language. Finally, the structures might be too advanced for novice learners. Despitethese limitations, traditional stories can be a tremendous resource with some strategicmodification of orthography and content. We use an example from Kari’nja to illustrate theprocess of modification.Hoff (1968) includes a transcribed and translated text of De Goede Hoop, a Kari’nja story.The story in its entirety is not appropriate for all age groups in that it includes demons andmurder. However, the story also includes dialogue between characters that was modifiedfor use as a linguistic formula and for pattern practice.First, the story is ‘translated’ into the practical orthography currently in use by commu-nity members.3 Table 4 illustrates the practical orthography as well as a more useful format,from a teaching and learning perspective. The original was organized in side-by-side para-graph form, making it difficult to track the Kari’nja prose and English free translations. Asthe particular excerpt used here is a short conversation between characters, it is more usefulto teachers and learners to have it organized line by line rather than as a long string of prose. 4This exchange includes a common greeting for someone who has been away from thecommunity for some time. However, in the story, the exchange is in a more formal registerthan is common in everyday use. As such, the next step is to simplify the register for usewith novice learners. This includes eliminating the honorific markers common to the moreformal registers as well as adding in more formulaic responses, as illustrated in Table 5.
Old stories can be great language resources, but they often have challenges. They may use old or complicated writing systems, advanced grammar, or content that’s not suitable for all ages. Many are written as third-person stories and may not include dialogue for practice.
The authors use a Kari’nja story as an example. It had difficult writing and mature themes, so they changed the spelling to the modern system, focused on a short dialogue, and formatted it line by line to make it easier for learners.
An additional potential resource is the academic description of particular elements of alanguage. Standalone articles analyzing specific structural features tend to be too jargonheavy and narrowly focused to be of immediate use in revitalization. However, they ofteninclude functionally useful language in their examples. Articles tend to be formatted insuch a way that tokens of language used as examples are set apart from the rest of the text,making them easy to locate in a larger description. Although an article describing, forexample, nonconfigurationality in a Cariban language (Hoff 1995) may be too opaque fora novice linguist, it may provide examples that can form the basis for teaching and learningactivities.Although the article itself may be of interest to only a small subset of linguists, examplesin Hoff (1995) are peppered with useful vocabulary including kinship terms and possessivepronominal prefixes. These were extracted to create the word list of kinship terms in Table 1,as well as the paradigm of possessive pronominal prefixes in Table 2. Together, the examplesin Hoff (1995) form the basis for a variety of activities developed to teach and reinforcekinship terms.The focus of these examples is nouns and possession, but a more communicative approachwould include the use of verbs. Hoff (1995) also provides useful examples that includedifferent verb roots used in the same tense. Section 3.2 illustrates a mini dialogue based onthese terms. Although academic articles may at first glance seem opaque or irrelevant, ithas been our experience that simply skimming examples can provide a wealth of usefultokens of language.
Academic articles that study specific parts of a language are often full of technical jargon and can be hard to use for language revival.
The authors give an example from Hoff (1995), which contains vocabulary like kinship terms and possessive prefixes. They pulled these out to make teaching activities. Hoff’s article focuses on nouns and possession, but also has verbs that could make lessons more interactive.
Even though academic articles may seem too technical, examples can uncover a lot of helpful words and structures for creating learning materials.
A linguist’s field notes may not be readily available, and when they are, they are often orga-nized based on a system that is transparent only to the linguist who created them. Usingfield notes to locate functional language may be time-consuming as one must work todecipher what are often very idiosyncratic notational schemes. However, as they may alsocontain more contextualized language as well as examples that have not been publishedelsewhere, field notes may be worth the time investment necessary to comprehend them.Using Myammia as an example, Figure 1 illustrates highly functional language that is embed-ded in a documentary corpus of other information. The resource is part of the LeBoullengerdocumentation available in the Miami-Illinois Digital Archive (MIDA) and includes a listof numbers embedded within a larger stretch of documentation. Although this representsan extreme example, it is not unusual to find seemingly random tokens of functional lan-guage surrounded by documentation of something completely different.As numbers are highly functional and often among the first domains of language to belost when formal schooling introduces majority language numbers along with mathematicalconcepts, numbers such as those in Figure 1 represent an important discovery. This examplefrom the MIDA shows how archival contributions can make documentation more usefulto revitalization through organization and widespread availability of information. Inclusionof metadata about functional language found in sources such as field notes can providecontext, related expressions, and other potentially helpful linguistic cues. Detailed discussionin Baldwin, Costa, and Troy (2016) provides an overview of a process of transformingmanuscript documentation into searchable data. For those who have access to field notes,we suggest developing an organizational system that includes metadata about functionsand semantic domains found in particular corpora. In Section 3.3, we discuss the use ofnumbers in the development of materials and activities for language learning.
Linguists’ field notes can be hard to use because they’re written in personal systems, but they often include valuable, real life language that isn’t published anywhere else. The authors share an example from the Miami-Illinois Digital Archive, where useful words like numbers were found hidden in other notes.
Functional language refers to the range of constructions that are used to fulfill a variety ofcommunicative purposes. Functions are the answer to the question of, ‘What do peopleactually do with language’? In addition to greeting, as highlighted in our opening anecdote,people count, they tell stories, they complain, and they express likes and dislikes. Somefunctions are expressed through particular grammatical constructions found in academicdescriptions. Once located, these can provide immediately useful formulas or patterns(Hinton 2003) that foster interaction in the language.More traditional products of documentation are not typically organized in such a waythat functional language and corresponding structures are easy to find. Metadata may ormay not make clear what exists in a particular resource, and examples in academic descrip-tions tend to be context-independent. In the subsections that follow, we describe the processof extracting useful language from documentary sources including: field notes, academicdescriptions, reference grammars, and text.
Functional language means the ways people actually use a language, like greeting, counting, telling stories, or sharing opinions. These real-life uses often follow certain grammar patterns that can help learners communicate. However traditional records don’t organize language by how it’s used, so it’s hard to find these examples. The authors explain how they search through notes and texts to pull out useful, everyday language for teaching.
Finally, a particular resourceis only useful to the extent that metadata make clear what types of language it includes interms of semantic content, linguistic functions, and grammatical constructions. Extractingexamples of functionally relevant language can be like a treasure hunt, and useful tokensof speech may be embedded in a nonrelated stretch of discourse or descriptive prose. Ourgoal is to develop materials and activities that promote interaction in the language.
Old records often hide useful examples, so the authors aim to make clear, well-labeled resources that help learners actively use the language.
Of the variety of revitalization activities communitymembers engage in, formal teaching is often the most visible. In addition, this may be theactivity that most needs teaching and learning materials. As such, our focus will be oncreating materials for formal teaching in a classroom setting. However, the techniquesdescribed may be used by anyone interested in using available documentation to developmaterials and activities to support revitalization.
Of all language revival methods, classroom teaching is the most visible and needs the most materials. The authors focus on making resources for classes, but their ideas can help anyone use old records for revitalization.
Such documentation may formthe basis for academic descriptions such as reference grammars. Ideally, language docu-mentation projects take into account a wide range of possible end users and are conductedin collaboration with a number of stakeholders. However, for many speech communities,the reality is that what is available is far from perfect. It is just this type of situation, one inwhich available documentation of a language does not provide ideal support for revitaliza-tion, that motivates this article.
Old records often form the basis for academic works like grammars. Ideally, they’d be made with input from both scholars and community members, but many are incomplete or not very useful for revival. This article looks at how to use imperfect records to still help bring a language back.
The division between ‘outsideracademic’ and ‘insider speech community member’ is often blurred as more and morespeech community members seek out the tools and training to conduct academic researchon their own heritage languages.
The gap between researchers and community members is shrinking as more Indigenous and local people learn to study and document their own languages.
As there is no ‘one size fits all’ in language revitalization, we aim to provide a variety ofreal-world examples that can stimulate additional ideas for readers’ individual situations.Rather than a replicable model to be followed to the letter, we explore varied ways in whichthose we work with have integrated documentation and support for revitalization. Ourfocus on practical application is grounded in theories of second-language acquisition thatfoster communicative competence and emphasize creativity and interaction in the languageover rote memorization of forms in isolation.
There’s no one-size-fits-all for language revival. The authors share real examples of using old records creatively, focusing on communication and interaction rather than just grammar drills.
For speech communities with few to no remainingfirst-language speakers, extant documentation and description may be the only availablerecord of the language. Even in communities that still have first-language speakers, anurgency to begin activities in support of revitalization leaves many community membersunable to wait for the products of a new documentation project to be complete befo
When few or no fluent speakers remain, old records may be all that’s left of the language. Even where some speakers exist, people must teach it immediately using the materials they already have.
For communities that no longer have members who speak the language with native-likeconfidence, there is unlikely to be new documentation forthcoming. The current trend inwork with speakers of endangered languages is toward more collaborative models that seekto meet the needs of a wider array of stakeholders in a language project (Yamada 2007,2010;1 Czaykowska-Higgins 2009; Florey 2004; Penfield et al. 2008; Rice 2011; Stebbins2003).
If a community has no fluent speakers left, they can’t expect new documentation to be made. Instead, recent work with endangered languages focuses on collaboration
The traditional triad in documentation and description of lesser studied languages is anacademic reference grammar, a word list or dictionary, and a collection of transcribed andtranslated texts of spoken language. Although these documents provide a wealth of infor-mation about a language for those with enough linguistics training to be able to decipherthem, those with more limited training may find such representations intimidatingly
Linguists usually document a language by creating a grammar, a dictionary, and written transcripts of speech, there are helpful for experts, but regular people without linguistics training often find them too difficult to understand or use.
As the language has no living first-language speakers, she and othersin similar situations must rely on existing documentation to develop teaching and learningmaterials. As documentation often was produced for an academic audience, it may not beimmediately useful to those most affected by language endangerment–speech communitymembers themselves. In this article, we address how documentation for an academic audi-ence might be used to support revitalization activities.
The author explains that many people trying to reconnect with an endangered language just want to learn basic everyday expressions, but because the language has no fluent speakers left, they have to depend on old documentation written by linguists.
Finally, in their essay, “Decolonial Skillshares: IndigenousRhetorics as Radical Practice,” Driskill (2015) advocates for embodiedlearning through the teaching and learning of indigenous languages,rhetorical traditions, and maker-practices. Driskill situates this learning,though, within radical politics aimed at decolonizing the academy, theclassroom, and the curriculum as well as on cultivating transcultural,transracial relations characterized by mutual understanding, respect,and reciprocity—through the embodied sharing of knowledge. Driskilltraces their experience and development of the practice of decolonialskillshare to a history of activism within queer and trans communitiesof color, locating the concept, however, in punk and anarchist commu-nities seeking to resist and intervene in authoritarianism and capitalismthrough the cooperative sharing of a variety of “do-it-yourself skills”(p. 60). Driskill notes that the skillsharing practices of these communi-ties, however, tend to be dominated by white, middle-class men whoreproduce the very hegemonic power they seek to disrupt through theexclusion of meaningful analyses of racism, sexism, queerphobia, andcolonialism. And so, Driskill develops and theorizes a counter practicethat disrupts and subverts the justifications, logics, and practices ofcolonialism.
Embodies learning is to learn bty doing, experiencing, and practicing culture not just reading about it.
In the second half of her essay, King explores the pedagogicalimplications of these key concepts and the differing forms of empower-ment and engagement their uptake enables for Native and non-Nativestudents. She posits a general writing/rhetoric course and elaboratesthe ways in which an advertisement analysis assignment might advancegeneral learning goals as well as address the misrepresentations of in-digenous peoples in advertising. While the specificity of the course andassignment King describes might seem at first glance inapplicable towriting centre theory and practice, I am struck by the value there mightbe for writing centre pedagogy in cultivating tutor understanding thatnot all writing teachers privilege (or gate keep) the rhetorical traditionthat has historically dominated the academy—a tradition that frequentlyexcludes indigenous epistemologies and meaning-making practicesincluding story. Further, tutors should be prepared to offer culturallyappropriate and meaningful support to indigenous student writersexercising their own rhetorical sovereignty, as well as for non-Nativewriters seeking to compose themselves and their relations in resistanceto the array of cultural misrepresentations and appropriations to whichwe are all continuously exposed.Such projects as preparing tutors to recognize indigenous rhe-torical traditions, to respect the rhetorical sovereignty of indigenouswriters, and to provide culturally competent and appropriate supportto both indigenous writers and non-Native writers seeking to resist andcounter rhetorical (and linguistic) imperialism might be understood aspurposefully resonant with calls by such scholars as Marker, Mihesuah,and Powell to indigenize the academy. These scholars advocate not onlyfor greater inclusion of indigenous literature and scholarship, but also foran opening up of the academy to new languages, new epistemologies, andpedagogical practices that enable relations characterized by reciprocityand by respect (Watanabe, 2015). Reading Survivance, Sovereignty, andStory from the vantage point of the writing centre should lead us to askwhat indigenizing the writing centre might look like or feel like andhow our practice might be transformed by such a move—how we mightbe changed, too.
Writing centers need to support Indigenous rhetorical traditions, not force Indigenous students into traditional Euro-American academic styles.
he tracesbriefly historical legacies of the “Indian,” the “savage,” the “noble sav-age,” and the “vanishing Indian,” describing the relationship betweenrepresentations of indigenous peoples by Euro-Americans and shiftinghistorical contexts and ideologies. And, King argues, representationsand their constructions of “Indian” continue to morph, adapting to thepurposes of those who create and deploy them.
Indigenous people are often misrepresented by outsiders.
And, King points out, culture and religionbear an intimate, integral relation to the land inhabited by indigenouspeoples. She reminds readers, however, of the local, situational, andcontext-driven nature of indigenous understandings and applicationsof sovereignty. The concept will be understood differently in differentcontexts or within differing political frames and exigencies, but alwayslinked to the imperative to preserve and sustain indigenous peoplehoodsthat include cultures, languages, religions, and lands that are their pro-genitors.
Language and identity come from heritage and place.
In defining and elaborating these terms, King notes that alimited understanding of them may lead teachers (and their students)to misunderstand and misrepresent indigenous texts and the rhetoricaltraditions out of which those texts emerge and to resituate indigenoustexts within the amorphous category of work by “minority” writers.
Not fully understanding can lead to teaching, learning, or reinforcing sterotypes.
Lovejoy concludes withthe advice that teaching code-meshing has the potential to enliven andmore fully engage not only students in their own textual production,but also teachers with their subjects and the learning of their students.
code meshing makes everything more engaging for both the students and the teachers
Lovejoy advocates for the inclusionof self-directed writing in the composition classroom as a means to en-courage linguistic and rhetorical experimentation among students andto include students in drafting, revising, editing, and publishing prac-tices that are driven by a more expansive and inclusive understandingof language variety
He argues that letting students choose their language encourages creativity and helps them experiment with different dialects and identities.
Lovejoy carefully defines expressive writing,deconstructing reductive assumptions about the practice that confine itto “self-expression” and occlude its value to the meaningful articulationof perspective on the world, reflection about relations between worldand the self as well as about learning, and engagement of a more fulllinguistic and rhetorical repertoire.
Lovejoy says expressive writing is more than just “feelings” it helps students think, reflect, and understand themselves. ( Cultural identity)
Finally, Lovejoy extends the teaching focus of Other People’s En-glish to the post-secondary writing classroom. In his first essay, Lovejoyrecounts an initial foray into the teaching of code-meshing and resistanceto that approach not from students, but from a racially diverse group ofcolleagues
Students were more open minded than the adults.
Young-Rivera reminds readers that the relationship between “selfconfidence, self efficacy, and success” in student learning has been in-disputably established and issues a call for educational reformers to openthemselves to study and experimentation with language arts pedagogiespredicated on linguistic as well as cultural diversity and inclusion (p.
Students do better when they feel confident in their identities.
In her final essay, she refutes the notionthat code-meshing is incompatible with educational reform efforts.
Many people think code meshing “breaks the rules.” She thinks that it actually fits with modern teaching goals.
In her first essay, Young-Rivera traces her own journey fromresistant interlocutor to an advocate for educational experimentationwith the theory and practice of teaching code-meshing
Tells of how at first it was easy to be skeptical.
Young-Rivera draws on 20 years of experience as a teacher andadministrator in Chicago public schools, as well as knowledge gained asan educational consultant in her contributions to Other People’s English.She writes as an educator who, by her own account, resisted argumentsfor the teaching of code-meshing and who came see its value only aftersetting herself a course of study of the practice of code-meshing inpublic discourse, prior scholarship advocating linguistic inclusiveness inthe teaching of writing (including the texts associated with the NationalCouncil of Teachers of English’s landmark resolution on “StudentsRights to their Own Language”), and her own survey of languageteachers advocacy for or rejection of code-meshing and its associatedpedagogies.
Young-Rivera has actual experience and research background that gives her credibility when she talks about code meshing.
He demonstrates thelimitations of approaches that draw from and enact language bias in theThe Writing Center Journal 36.1 | 2017 221classroom as well as the array of negative impacts—harms, in fact—thatthe enactment of such bias has on student-writers and speakers.
Only teaching Standard English hurts students.
In his second and third essays, Young expands his argument for theteaching of code-meshing. He lays out the costs of code-switching prac-tice and pedagogy to students of colour.
code switching, not code meshing, is harmful for students of color.
He argues that teaching more people toavail themselves of the linguistic and rhetorical potency of code-meshedEnglishes is a more politically responsible and pedagogically efficaciousapproach to the teaching of writing for all students.
code meshing doesnt only help minority students, but also everyone.
oung notes the ubiquity ofcode-meshing in public discourse, both professional and political, andthe relative silence of the teaching profession on the prevalence and rhe-torical value of code-meshing.
Everywhere else, code meshing is utilized. However schools act like its not a thing.
Young advocates for a code-meshingpedagogy that teaches the conflicts associated with language use: thepower dynamics that inform the reception, valuation, privileging,and disenfranchising not only of dialects but also of their speakers andwriters.
Code meshing helps students understand the actual issues of language and the power it holds.
Young suggests that teach-ing students of colour to speak and write the favoured dialect ratherthan addressing the racism that, among other harms it inflicts, promotesthat dialect over and against students’ own languages constitutes akind of resignation to racism
Forcing students to change dialects gives into the racism.
He points out the implicit or agenticracism that shapes teachers’ “address” of linguistic racism by “puttinganother dialect, evidently one favoured by those perpetrating prejudice,in the mouths of the disadvantaged” (p. 55).
Teachers force students to use EAE instead of realizing that EAE is privledged.
While there is no easy exit from the morass of racial politics inNorth America and the roles assigned to teachers of writing, reading,and speaking within that morass, there are alternatives to thoughtlesslygoing along. If there is insufficient work within the field of writing stud-ies to teach us how to think more deeply and effectively about antiracistpedagogical practice in the writing centre, then perhaps we may findaid in published scholarship outside the field, as well as inspiration anda firmer footing for producing our own. In this regard, two recentlypublished books stand out to me as offering both a richly developedtheoretical framework and teaching advice that can easily be transferredfrom the classroom to the writing centre context: Other People’s English:Code-Meshing, Code-Switching, and African American Literacy, written byVershawn Ashanti Young, Rusty Barrett, Y’Shanda Young-Rivera,& Kim Brian Lovejoy (2014) (published by Teachers College Press),and Survivance, Sovereignty, and Story: Teaching American Indian Rhetorics,edited by Lisa King, Rose Gubele, & Joyce Rain Anderson (2015b)(published by Utah State University Press).
its hard to escape racism in writing education. Teachers can use existing scholarship to learn how to teach fairly.
f we speak for and gate keep on behalf of racistlinguistic and rhetorical intolerance and exclusion, that’s the house inwhich we will live. And if we tutor student-writers to do the same, thenthat’s the house in which they will live as well.
Enforcing "proper English" is also maintaining racism.
Displacing responsibility for the ways in which racism inflects andinforms the reception of othered languages, discourses, and rhetoricaltraditions—and the speakers and writers of those languages, discourses,and traditions—within and beyond the academy will never alleviatethe degree to which writing centre directors and tutors are implicated.
Teachers cant pretend racism in lanaguage isnt a thing as its part of the system already.
The first concern is, I think, at least partially true. We have somework to turn to within our field to begin to learn how to prepare ourThe Writing Center Journal 36.1 | 2017 219tutors and ourselves to encourage, support, and teach linguistic andrhetorical diversity, but not enough. We need to learn more.
Author says writing centers dont fully know how to teach or support language diversity yet.
chol-arship that does address theory, practice, and pedagogy of languagediversity (and its intersections with racial justice) is largely being pro-duced outside the field of writing centre studies
Research on diverse languages come from other fields.
Over four months of ethylene production: Unlocking the potential of solid-state photosynthetic cell factories
Further details on engineering solid-state photosynthetic cell factories are presented in these two videos: Engineering biofilm architecture for efficient light utilization and Photosynthetic cell factories
Yann Braga | Storybook Vitest | ViteConf 2025
I love this, this is fantastic. They way this program breaks things down, tracks changes in a clear fashion, debugging and other features are done directly on the interface, even the reusability factor is impressive. I imagine how this could assist designers who learn visually, or help green engineers learn how pieces of programs talk in a clear, traceable steps. This seems like an incredibly promising program for designers and developers alike.
Part of the effort to ensure quality and proper programmingfor prisoners includes a governor-commissioned ‘‘Lifer’’advisory committee, consisting of 20 to 30 formerly incar-cerated men and women who successfully reintegrated intosociety.
This is very important because it offers those who have been released to always have someone to talk to if needed
During incarceration, prisoners are tested for basicreading comprehension. If a prisoner demonstrates skillslower than a ninth-grade level, they are enrolled in theAdult Basic Education (ABE) program, offering more
Testing is very important because it provides information on whether the program is working or not.
More precisely, each variety may differ in its phonetic implementation rules, phonology, lexical items or semantics, morphology, syntax, and the pragmatic functions of discourse markers or syntactic structures.
Dialects still build on it's base language, so being able to use certain dialects instead of SE in certain scenarios isn't a crazy idea.
Because dialect boundaries are fuzzy, contiguous regional dialects may form dialect chains. Within the chain, two adjacent dialects will display greater similarity than two dialects that exist at a distance from one another.
Dialects can be very widespread, or can be very short spread, like a friend group's way of speaking is technically considered a dialect.
Qualitative and quantitative dialect differences may map onto groups defined by geographical regions or by social characteristics.
AAVE in the south sounds much different than how is sounds in the west. That is why when people use an artificial dialect, it is easy to notice.
Most speakers of English will sometimes pronounce the initial consonant as a fricative [ð] and sometimes as a stop [d]. This alternation between [ð] and [d] can be quantified. In turn, the frequencies with which individuals say [ð] versus [d] may correlate to categories of identity, such as age, gender, class, or ethnicity. Alternating forms, like [ð] ~ [d], are called variants of a sociolinguistic variable.
There are usually patterns to dialects.
During incarceration, prisoners are tested for basicreading comprehension. If a prisoner demonstrates skillslower than a ninth-grade level, they are enrolled in theAdult Basic Education (ABE) program, offering moreremedial levels of education. 4 ABE is an academic programemphasizing reading, writing, and mathematics.
Testing to see where inmates are at in their progress is crucial for seeing if the program is actually worth keeping around or trying something new should be pursued.
After release, Johnson earned a bachelor’s degree in psychology, graduatingsumma cum laude. He is an alcohol and drug counselor in two different Californiacounties and a lead facilitator for an Alternatives to Violence Project in his home town.Johnson’s efforts were recently recognized by His Holiness the Dalai Lam
First hand experience often provides the best opportunity for those who want to change something for the betterment of others.
The Division of Rehabilitative Programs (DRP), the rehabil-itative arm of CDCR, provides programming and teachesskills to both prisoners and parolees to reduce their re-conviction or return-to-prison rate, three years after releasefrom a CDCR institution. As part of CDCR, DRP exists tohelp prisoners leave prison with better life and job skills,more education, and the confidence to reintegrate into ourcommunities.
CDRC stands for California Department of Corrections and Rehabilitation. California is one of the best states for educational inmate programs.
s, "If fellow studentsare to provide honest and useful feedback, theyshould constitute the real audience, at least in therevision stages. This places students in the positionof writing truly to communicate" (37
forcing students into language conventions that are outside their lived experiences does not serve them or help them acquire language skills for their lives
When students are aware of the intended audi-ence, they can critically reflect on their choice of w
this is a brilliant thought
at, "[allthough be-coming proficient in standard American English maybe an important school goal for all students, it shouldnot be viewed as a prerequisite for literate classroombehavior.... When it is viewed as a prerequisite,teachers deny students the opportunity to use theirown language as a tool for learning" (1
is this preparing students for success?
. To respect AAVE in the classroom, wemust create a learning environment that values di-versity in experience, culture, and languag
I think we have begun to do a much better job as a country with this since this article was published
Many of the educators working with AfricanAmerican students are "white, middle-class, mono-lingual English-speaking women and men who havehad little direct experience with cultural, ethnic,linguistic or other kinds of diversity"
I have seen this in my own community-- often the demographics of teachers do not represent the demographics of the students they serve
African Holocaust" (19).
an entirely different linguistic culture that emerged during the horrors of slavery and segregation
n 1983, at the age of twenty-one, Michael Johnson 1 had a deadly confrontation with a drug dealer and was convicted of second-degree murder and sentenced to fifteen-years-to-life. He spent the next twenty-eight years in California prisons. While incarcerated, Johnson earned his drug counselor certification through an offender-mentor certification program. He cofounded a program that tutors offenders to take their General Education Development high school equivalency test. He also became a licensed x-ray technician and was a team coordinator for California’s Alter- natives to Violence Project. After release, Johnson earned a bachelor’s degree in psychology, graduating summa cum laude. He is an alcohol and drug counselor in two different California counties and a lead facilitator for an Alternatives to Violence Project in his home town. Johnson’s efforts were recently recognized by His Holiness the Dalai Lama. Johnson is well remembered by those remaining within the walls of the prison; his life continues to shine as a beacon of hope to those who knew him. ‘‘I have been helped greatly by the kindness of others,’’ Johnson remembers. ‘‘I was shown unconditional love and com- passion. I want to pass that on to everyone I meet.’’ Vincent Morales was sentenced to fifteen years in prison. As he came closer to his release date, he realized he needed skills in order to support his family. He chose a woodworking arts program, where he developed carpentry skills with an emphasis on crafting guitars. Upon release, he taught his son and brother his artistry. Over a period of years, they developed a family business where Morales and his son now build high- end guitars for famous artists. BOOM: The Journal of California, Vol. 6, Number 2, pps 52–56, ISSN 2153-8018, electronic ISSN 2153-764X. © 2016 by The Regents of the University of California. All rights reserved. Please direct all requests for permission to photocopy or reproduce article content through the University of California Press’s Reprints and Permissions web page, http://www.ucpress.edu/journals.php?p¼reprints. DOI: 10.1525/boom.2016.6.2.52. 52 B O O M C A L I F O R N I A . C O M Justine Sultano struggled with substance abuse for a long time, eventually committing a crime and receiving a five-year prison sentence. While in prison, she took advantage of the rehabilitative services offered by the California Department of Corrections and Rehabilitation (CDCR), participated in self- help groups, received substance-use disorder treatment, and pursued academic and career technical education programs. While in prison, Justine mastered software programs such as Microsoft Word, Excel, and PowerPoint. Upon her release, she entered a rehabilitation facility in San Francisco, where she learned how to send emails, create a re´sume´, and search for a job. After eighteen months, Justine found a desk-clerk position at a local business. After leaving the rehabilitation facility, she enrolled in a prison-run program that provided transitional housing and emotional support; it also helped her navigate the court process to regain custody of her daughter. Sultano states, ‘‘I used to be a person who pointed fingers at others for my problems, but through the programs offered by CDCR, I learned to be honest and upfront with who I was, and where I wanted to go, and CDCR’s programs helped me get here.’’ Justine completed her journey with CDCR on 9 Septem- ber, 2015, successfully finishing her parole. Today, she still works at the local business, has custody of her daughter, and plans to attend school this year to further her career. Every day, men and women are released from prison and return to their homes and communities. Unfortunately, many will commit another crime and return to prison. CDCR has the tools to break the cycle and give offenders the skills that will enable them to be productive members of our communities. Assessment The Division of Rehabilitative Programs (DRP), the rehabil- itative arm of CDCR, provides programming and teaches skills to both prisoners and parolees to reduce their re- conviction or return-to-prison rate, three years after release from a CDCR institution. As part of CDCR, DRP exists to help prisoners leave prison with better life and job skills, more education, and the confidence to reintegrate into our communities. This process begins the moment they enter the prison system through the community reentry process. BOO M | S U M M E R 2 0 1 6 53 Once a convicted felon enters the prison system, their likelihood of being convicted of a new crime is based on a range of risk factors. CDCR uses the California Static Risk Assessment (CSRA) tool to calculate an offender’s risk of being convicted of a new offense after release from prison. Based on their criminal history and demographics, offen- ders are designated as having a low, moderate, or high risk of being convicted of a new offense after release. CDCR uses the Correctional Offender Management and Profiling Alternative Sanctions (COMPAS) tool to assess an offender’s criminogenic needs and inform decisions regard- ing placement, supervision, and case management. Once a prisoner’s needs are assessed, a correctional counselor assists them with program placement. Prisoners have many in-prison rehabilitative services and programs available to them statewide, including treatment for sub- stance abuse, Cognitive Behavioral Therapy (CBT), aca- demic and college education, and technical training. According to CDCR’s 2014 Outcome Evaluation Report, offenders who received in-prison Substance Abuse Treat- ment (SAT) and completed aftercare returned to prison at a lower rate (20.9 percent) after three years of follow-up than offenders who did not receive in-prison SAT or after- care (55.6 percent). Statewide, the three-year return to prison rate—CDCR’s primary measure of recidivism—for all offenders released in fiscal year 2011-12 was almost double (54.3 percent) the rate of offenders who received in-prison SAT and completed aftercare (20.9 percent). 2 CBT addresses negative patterns of thought that can potentially lead to criminal relapse. Negative patterns might include anything from substance abuse, anger mismanage- ment, strained family relationships, and a propensity to think about committing crimes. These negative patterns are addressed through treatment, individual and group discus- sions, counseling, motivational interviewing, role-playing, and other methods. CBT programs help prisoners deter- mine what leads them to certain actions and how to avoid situations that can trigger relapse. Continuing Education DRP’s Office of Correctional Education (OCE) provides edu- cation programming developed to prepare prisoners upon their release. OCE has established an array of educational programs that enhance the prisoners’ skill levels while providing effective tools and resources to reduce recidi- vism. 3 In fact, many enter prison with poor literacy skills and no vocational trade or college diploma. Most prisoners attend classes for at least thirty hours per week in a traditional school setting with desks, marker boards, and a teacher. Mobilizing thousands of students throughout state prisons and classrooms presents organi- zational and safety challenges, but DRP is committed to organizing classes based upon a model that provides indi- vidualized, self-paced programs for each prisoner. Those who fail to meet the behavior standards are not allowed to attend classes. During incarceration, prisoners are tested for basic reading comprehension. If a prisoner demonstrates skills lower than a ninth-grade level, they are enrolled in the Adult Basic Education (ABE) program, offering more remedial levels of education. 4 ABE is an academic program emphasizing reading, writing, and mathematics. ABE pre- pares prisoners for entry into a high school equivalency or high school diploma program, which they can complete in prison. The OCE currently provides 19 CTE programs designed to train prisoners for a career path in multiple employment and vocational sectors upon release. 5 These sectors include building and construction, energy and utilities, finance and business, public service, manufacturing and product development, and transportation. Many CTE programs include green employment skills relevant to solar, geother- mal, and smart energy management practices. Each pro- gram aligns with a positive employment outlook within the state of California, providing opportunities to earn a livable wage. For many prisoners, having the ability and opportuni- ties to earn a livable wage marks the difference between relapsing into crime or becoming a contributing member of the community. Others focus on a college education, many receiving Associate of Arts degrees in Sociology, Human Services, Business, and General Studies. The Transition Transitioning back to society can be intimidating for prison- ers; often the world has shifted dramatically during years of incarceration. The shock of little-to-no contact with the 54 B O O M C A L I F O R N I A . C O M outside world, followed by release into the community fueled with new technology can be overwhelming without assistance. The Male Community Reentry Program (MCRP) is one of CDCR’s efforts to support the transition back into society. 6 CDCR contracts with established community pro- viders for housing, treatment, and other rehabilitative services. To ease reentry into society, the MCRP allows eligible prisoners to serve the last six months of their sentences in a contracted provider’s community facility instead of state prison. Not quite the same as a halfway house, an older term now used to designate sober living homes, in the case of MCRP men are still ‘‘in custody.’’ Parole is also technically a version of being ‘‘in custody,’’ and yet the MCRP function is both pre-parole and pre-release. The significance of this is found when many inmates today, especially with so many increased commuted sentences from major sentencing law changes, never become paroled. MCRP participants are assisted in obtaining their California identification and Social Security cards—both necessary to find employment. Re´sume´ writing, professional certifications, and job search assistance are also provided. If a qualified participant finds a job while participating in MCRP, they are allowed to work while still serving their remaining sentence, and the money they earn is saved for use upon release. In addition, prison- ers in the MCRP are provided access to a wide range of community-based rehabilitative services designed to deflect negative thought patterns that can lead to relapse, such as CBT. Some prisoners close to release from prison may not be eligible for the MCRP due to their level of offense or med- ical/mental health needs. Instead, they are assigned to an in- prison reentry program, where they can receive similar rehabilitative services such as CTE classes, substance-use disorder treatment, anger management and family relation- ship counseling, and trauma informed gender-responsive treatment for women. While some of these programs may be available to prisoners with longer sentences, the in- prison reentry program’s primary focus is to prepare those who will soon return to our communities. Reentry pro- grams provide prisoners, within 18 months of release, with training for career readiness, job search skills, and practical financial literacy to facilitate a successful reentry into their communities. BOO M | S U M M E R 2 0 1 6 55 Technological Advances Like other educational institutions, California’s prisons are harnessing technology to better reach students. Implement- ing new technology in California prisons poses a raft of challenges due to the physical space, location, security, con- nectivity, firewalls, and funding requirements. However, these challenges are not insurmountable. 7 E-readers allow prisoners enrolled in college correspon- dence programs to study for their classes with digital text- books. They also allow prisoners living in high security areas to continue their education through independent study. Streaming television channels exponentially increase the quantity and quality of media content currently available for education, rehabilitation, and training purposes within Cali- fornia’s prison system. Four channels were branded and designated to stream specific content to aid prisoners in different stages and areas of their rehabilitation process. The four channels managed by and streamed to the institutions directly from CDCR headquarters focus on four subjects critical to the success of a recently released prisoner. Freedom TV focuses on how to prepare for reentry to society. Formerly incarcerated individuals and community members help prisoners prepare for the roadblocks they may face upon reentry. Wellness TV provides inmates infor- mation on developing and maintaining healthy habits. This channel teaches the factors that affect wellness of mind and body. Education TV streams academic programming com- plementing the lessons taught within the education classes developed by OCE and community colleges. Employment TV teaches job search techniques, interviewing skills, re´sume´ building and financial literacy. Continuing Rehabilitation Some prisoners, depending on the duration of their sentence, may not complete all programming by the time of their release. To address this issue, Community Reentry Services (CRS) offers rehabilitative DRP services outside of prison.8 CRS works with contracted community-based partnerships statewide, creating a network of services for parolees. This network provides education, substance-use disorder treat- ment, transitional housing, life skills training, financial plan- ning, and assistance in reestablishing family relationships. Thus, DRP displays a commitment to provide prisoners ongoing rehabilitation in an effort to prevent recidivism. Relapses, especially in criminal thinking, can be very hard to avoid and sometimes take years to overcome. Reducing recidivism is, therefore, a continuous effort— an effort that requires more than conventional tools. The Way Forward Part of the effort to ensure quality and proper programming for prisoners includes a governor-commissioned ‘‘Lifer’’ advisory committee, consisting of 20 to 30 formerly incar- cerated men and women who successfully reintegrated into society. Under the direction of DRP, this advisory group meets to weigh the strengths and weaknesses of the in- prison and community reentry system. As portrayed on reality television shows and often in the news media, California prisons can be very difficult, violent places. The media often misses, however, the many positive programs available to those who desire to change. Tens of thousands of California prisoners are enrolled in some form of rehabilitative program—most want to change. Many are carrying books, not shackles. Many encourage peace, not violence. Most will return to our communities. It is our duty to help them become productive citizens when they do
This study's findings highlight the important role of translanguaging as an effective pedagogical method for improving English language acquisition in EFL classrooms, especially at the high school level in Indonesia.
The study concludes overall that translanguaging is a highly-effective way of teaching English to non-English speakers and is an important role for all teachers to adopt for their students' success.
1) knowledge construction, which pertains to utilizing Translanguaging for comprehension of the subject matter; 2) classroom management, wherein educators employ translanguaging to oversee student conduct during the learning process; 3) interpersonal relationships, encompassing the teacher's initiatives to foster connections with students; and 4) personal and affective meanings, which signify the articulation of personal experiences, emotions, and sociocultural dimensions of the educator.
The four primary functions of translanguaging are; 1.) Knowledge construction 2.) Classroom management 3.) Interpersonal relationships between teachers and students 4.) Personal and affective meanings to articulate the multiple dimensions of the educator
Baker (2001) highlighted four advantages of translanguaging in bilingual or multilingual education. Initially, it improves content comprehension by prompting students to read in one language and write in another, fostering deeper analysis and understanding. Secondly, it enhances proficiency in the less dominant language by augmenting communication and reading abilities, thereby fostering bilingualism and biliteracy. Third, it enhances home-school links, enabling kids to discuss academic content at home in their mother language, so facilitating comprehension. Fourth, it promotes classroom integration by uniting students with diverse language proficiency levels, thereby cultivating a more inclusive learning environment.
The four advantages stated here are; 1.) Content comprehension through prompts read in one language but written in another 2.) Enhances proficiency in the less dominant language by focusing on communication and reading skills 3.) Enhances home-school links by allowing children to discuss topics learned at school in their mother-tongue 4.) Promotes classroom diversity by uniting students under their shared language proficiency
In regarding to the teachers' practice on translanguaging in EFL classroom, we observed seven strategies that can be discussed in this article.
The 7 strategies stated here are; 1.) Reinforce prior knowledge 2.) Translanguaging in grammatical instruction 3.) Facilitate students' responses 4.) Emphasize key points 5.) Promote classroom management 6.) Enhance and build vocabulary understanding 7.) Give clear directions and feedback
In order to truly engage students’ dynamic idiolects inthe literacy classroom where texts remain relatively staticentities, reading research and instruction can explore theways in which languagers bring themselves into the compre-hension process by providing languaging opportunities withothers in relation to text and in the service of comprehen-sion. Figure 3 reflects one such configuration at the smallgroup level.
This is why discussion is so important because it can bring together and widen views.
Even when a reader encounters text that might be moreopaque to the reader (i.e., less linguistic awareness to drawon), they must still make sense of it,
Even if everything was in SE, people could still interpret it differently based on their background.
Building on the idea oflaminated identity (Holland & Leander, 2004) where differ-ent identities can “retain some of their original distinctive-ness” (p. 13) or “thicken” through multiple interactions,linguistic laminating is the layering or building of one’sidiolect vis-a-vis interactions with other languagers orprinted language
This is what happens through your day to day life, and is why you speak like you do.
In other words, when two languagers commu-nicate, Languager A (La) will intentionally use linguistic fea-tures (e.g., vocabulary, grammar) that they assume are high“quality” with Languager B (Lb).
These are the fundamentals of Code Meshing.
The term reflects theunique linguistic repertoires upon which the languagerdraws, how they interpret input from other languagers
How each person understands language based on their upbringing and background.
When and how to use Standard English Maybe you have cousins or friends in other parts of the country, and there have been times when you have misunderstood each other? Perhaps you were trying to play a game that has different names in different parts of the country. Such local words, which are not Standard English, should not be used in formal situations such as in an exam or going for a job interview. In formal situations, it is required that you use Standard English, which also means not using slang words that you would use with your friends.
standard English used in different parts of country.
Standard English today Although language changes all the time – think of new words like Internet, Web site, and so on – we still use Standard English as the formal form of our language. Standard English is the form that is taught in schools, following set rules of grammar and spelling. Newspapers are written in Standard English and it is used by newsreaders on national television, who need to be understood by people with different local dialects, all over the country.For some people, it is not difficult to use Standard English, because it happens to be their local dialect. But for others in different parts of the country, they may have to remind themselves to follow the rules, including the sentence order and grammar of Standard English, when they are speaking or writing in a formal context. However, Standard English can be spoken in any accent, and must not be confused with talking ‘posh’.
Different ways to use a formal and informal standard English.
Middle English developed at a crucial time in history, forcing the English language into some stability. One of the main reasons for this was that language started to be written down, and in 1458, the German Johannes Gutenberg invented printing, a process that William Caxton introduced to England in 1475. With all the differences and varieties in the language, Caxton had to make some choices about printing, which served to stabilize and standardize English to a certain extent. Because of where Caxton lived, he chose the east Midlands dialect, the language form used in London and around the southeast. The fixed spellings of what came to be known as Standard English, had been born, and were now, literally, set down in black and white.
difference and variation about standard English
An important influence then came from the Normans who invaded England with William the Conqueror in 1066. The Normans settled here permanently, bringing with them the French language and Latin. Old English was still spoken by most of the ordinary people, while French and Latin became the languages of the ruling classes, and was used for legal and religious duties.
The Normans bring french and Latin languages
Do you speak more than one language? Perhaps you are taught French or German at school, or English is your second language, and you speak a different tongue at home. But have you ever thought that you also speak different forms of language? For example, you probably speak to your friends in a way that you would never speak to, say, an interviewer in an interview. Hopefully, you would write differently in an exam than you would in a text message or e-mail! When we communicate with different people and in different situations, we naturally follow different sets of rules and patterns, often without having to think about the switches and transitions we are making. The most used form of English is Standard English.
the people speak in different forms.
Standard English The history of English is quite a story in itself, with dramatic changes and great variety. Up to about 450, British (Celtic) tribes spoke languages related to modern Welsh, Scots Gaelic, and Irish (Erse). However, the years between 450 and 1066 brought about great change. The Angles, Saxons, and Jutes invaded from North Germany in around 450, and settled on the eastern side of what is now called England. Their language, Anglo-Saxon, spread across to the west of England and developed into what we now call Old English. Many of the words we use today still relate back to Old English – but this was soon to change too. Other invasions, this time in the form of the Vikings from Scandinavia, influenced the language with new words from the Viking's language Old Norse that entered Old English between 800 and 900.
the language Anglo-Saxon are used in the west of England is called old English.