- Dec 2020
-
github.com github.com
-
Some of these are absent-by-design
-
-
-
For a long time, the blue flame coming out of a gas burner has evoked cleanliness. That was no accident, but the result of a concerted advertising campaign.
design gone wrong
-
-
-
Familiar npm inspired dependency management.
Tags
Annotators
URL
-
- Nov 2020
-
github.com github.com
-
All projects here are completely frozen, though feel free to fork and continue using them on your own.
-
-
help.looker.com help.looker.com
-
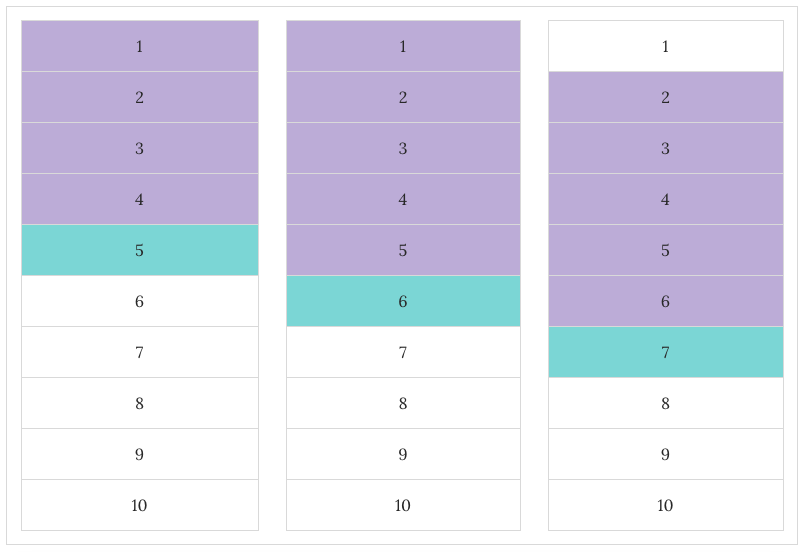
So far, all the grouping we've done is according to the unique values within a column or set of columns (using PARTITION BY). However, you can do even fancier things by making the group relative to each row. In other words, as SQL runs through each row, it will perform a calculation for the surrounding rows. This allows you to do things like get a sum for only the 5 previous rows. Here is a diagram that demonstrates which rows SQL will consider (in purple) when it reaches a given row (in aqua), if we tell it to look at the 5 previous rows:
-
-
opinionatedgamers.com opinionatedgamers.com
-
I’ve asked Mark about the inspiration and, yes, SNCF/Paris Connection, was in there, but he also cited Knizia’s Spectaculum for parts.
-
-
github.com github.com
-
at least in the meantime allow users to bypass the security protections in situations where they are confident of the source of the layers
-
-
github.com github.com
-
If the document is uncontroversial and agreement is reached quickly it might be committed directly with the "accepted" status. Likewise, if the proposal is rejected the status shall be "rejected". When a document is rejected a member of the core team should append a section describing the reasons for rejection.
-
-
github.com github.com
-
deprecated – plese see / use caly
Tags
Annotators
URL
-
-
github.com github.com
-
Highly inspired by Foreman.
Tags
Annotators
URL
-
-
github.com github.com
-
Or even keep as is, the simplicity of this feels right in line with svelte's simplicity :)
-
-
-
Since 'using decorators' has come to mean 'smothering your code in @ symbols' it's probably no longer a great name.
-
- Oct 2020
-
github.com github.com
-
Adding an API for something is an endorsement of that approach.
-
-
www.npmjs.com www.npmjs.com
-
This implementation is based upon following sources: JavaScript Debounce Function by David Walsh Lodash implementation
-
-
codesandbox.io codesandbox.io
-
codesandbox.io codesandbox.io
-
formvalidation.io formvalidation.io
-
All validators can be used independently. Inspried by functional programming paradigm, all built in validators are just functions.
I'm glad you can use it independently like:
FormValidation.validators.creditCard().validate({because sometimes you don't have a formElement available like in their "main" (?) API examples:
FormValidation.formValidation(formElement
-
-
-
hyperscript is much simpler to refactor and DRY up your code than with JSX, because, being vanilla javascript, its easier to work with variable assignment, loops and conditionals.
Tags
- template language: bad: by not reusing existing language constructs; forced to reinvent equivalents which are inferior and unfamiliar
- hyperscript
- reuse existing language constructs
- comparison with:
- making it easy for later refactoring
- JSX
- it's just _
- javascript
- template language vs. reusing existing language constructs
Annotators
URL
-
-
github.com github.com
-
It causes some implementation complexity just by existing.
-
-
github.com github.com
-
Deku is a library for rendering interfaces using pure functions and virtual DOM.
-
-
github.com github.com
-
bringing Vue-style reactive stores with data and computed properties into Svelte
Tags
Annotators
URL
-
-
github.com github.com
-
This library takes inspiration from Tailwind and utilizes Otion to provide means of efficiently generating atomic styles from shorthand syntax and appending them to the DOM at runtime.
-
-
github.com github.com
-
I'm suggesting there should be a way to write lifecycle related code that also responds to changing props, like how useEffect works. I think how React handles this could be a good source of inspiration.
-
-
www.technologyreview.com www.technologyreview.com
-
This piece makes a fascinating point about people and interactions. It's the sort of thing that many in the design and IndieWeb communities should read and think about as they work.
I came to it via an episode of the podcast The Happiness Lab.
-
Most of the tech news we get barraged with is about algorithms, AI, robots, and self-driving cars, all of which fit this pattern. I am not saying that such developments are not efficient and convenient; this is not a judgment. I am simply noticing a pattern and wondering if, in recognizing that pattern, we might realize that it is only one trajectory of many. There are other possible roads we could be going down, and the one we’re on is not inevitable or the only one; it has been (possibly unconsciously) chosen.
-
-
Local file Local file
-
duty of care
This reminds me of Mike Monteiro's book Ruined by Design from last year which pushes for a code of ethics for designers.
-
-
-
But Vue’s simplicity runs more deeply in its design.
-
-
commons.wikimedia.org commons.wikimedia.org
-
transport en commun
bus barré
-
-
github.com github.com
-
However, if you want to create a backend API that is meant to be consumed only by your frontend, then you don't need REST nor GraphQL — RPC, such as Wildcard, is enough.
-
-
visionmedia.github.io visionmedia.github.io
-
inspired by the Express router
Tags
Annotators
URL
-
-
-
The $ contract for auto-subscribing is lovely in its simplicity and flexibility. You can adapt your own preferred state-management pattern or library, with or without Svelte stores as helpers. Svelte does not fuss about how you want to manage your state.
-
-
www.digitalocean.com www.digitalocean.com
-
“Simplicity in all we do” is one of the core values at DigitalOcean. This includes all aspects of our product portfolio: UX, API, CLI, docs, billing, and pricing.
-
-
www.pnas.org www.pnas.org
-
Karatayev, Vadim A., Madhur Anand, and Chris T. Bauch. ‘Local Lockdowns Outperform Global Lockdown on the Far Side of the COVID-19 Epidemic Curve’. Proceedings of the National Academy of Sciences 117, no. 39 (29 September 2020): 24575–80. https://doi.org/10.1073/pnas.2014385117.
-
- Sep 2020
-
svelte.dev svelte.dev
-
Because Svelte is a compiler, we're not bound to the peculiarities of JavaScript: we can design a component authoring experience, rather than having to fit it around the semantics of the language.
-
-
medium.com medium.com
-
Rollup also does something very different compared to the other bundlers. It only tries to achieve one simple goal: Bundle ES modules together and optimise the bundle.
-
-
jimmyutterstrom.com jimmyutterstrom.com
-
Did you know that you can create a Svelte component and with almost no extra steps distribute- and use it like any classic old Javascript library through a global constructor (let myComponent = new MyComponent())?
-
-
github.com github.com
-
Svelta was greatly inspired by Vuexy.
-
Svelta was inspired by them.
-
-
drive.google.com drive.google.com
-
the narrator cries and is feeling upset because she is thinking about how her lover is very far away.
-
The narrators island is stricter than the one Wulf is on.
-
-
www.biblegateway.com www.biblegateway.com
-
“You are free to eat from any tree in the garden;(W) 17 but you must not eat from the tree of the knowledge of good and evil,(X) for when you eat from it you will certainly die.”
God instructed Adam and Eve to eat whatever they desired, though prohibited them to eat from the tree of the knowledge of good and evil. In Robin Wall Kimmerer's "Skywoman Falling", she explained how in Indigenous culture, they follow Original Instructions. These "instructions" are not rules but rather guidelines for each person. Kimmerer explains how during Skywoman's time, the first people's understanding of the Original Instructions were to care for the and have respect for hunted animals, value family, and hold respectful ceremonies for their beliefs.
-
-
github.com github.com
-
In a similar vein to (#33), it is arguably just something that compensates for the lack of power in the template language relative to JavaScript.
-
-
github.com github.com
-
The complaint is that by choosing less powerful languages, template-based frameworks are then forced to reintroduce uncanny-valley versions of those constructs in order to add back in missing functionality, thereby increasing the mount of stuff people have to learn.
-
-
github.com github.com
-
There are tools in Svelte that break this expectation to a degree, but they are a bit annoying to use, which makes it an active decision on the part of the developer. The API hints at the way we want you to do things because we feel that this will give the better experience.
-
-
css-tricks.com css-tricks.com
-
It’s become increasingly common to divide code into components, rather than by file type. React, for example, allows for the collocation of a components markup and JavaScript. In Svelte, this is taken one logical step further: the Javascript, markup and styling for a component can all exist together in a single `.svelte` file
-
-
www.codingwithjesse.com www.codingwithjesse.com
-
By enforcing this practice, Svelte can make some assumptions that simplify your code.
-
-
svelte.dev svelte.dev
-
For the editor level, we took inspiration from Pine's work in the Vue ecosystem via Vetur.
Tags
Annotators
URL
-
-
daveceddia.com daveceddia.com
-
This is what I love about React, it's JavaScript basically, not a DSL
-
-
marcin-piela.github.io marcin-piela.github.io
-
Extend ActionConfig interface in rfc-extended.d.ts file with new params: import * as RFC from 'react-fetching-library'; declare module 'react-fetching-library' { export interface ActionConfig { // Only new params skipAuth: boolean; params: any; }; }
-
- Aug 2020
-
meta.stackexchange.com meta.stackexchange.com
-
But it's easy to imagine that the caption was incorrect for too long because those who know the language, know where the mistake is, and those who don't, think that it's the correct way to spell it.
those who know the language, know where the mistake is, In other words, they can easily spot the mistake and no better than to repeat it themselves, but either are powerless or too lazy to actually fix it on SE.
and those who don't, think that it's the correct way to spell it. So those who should no better are inadvertently perpetuating the mistake and teaching others that it is an acceptable/correct usage.
-
+1 for taking the language back.
-
Can't upvote this enough. It is highly irritating to see language destroyed (and we wonder why kids bastardize the language..).
Tags
- example of: using incorrect terms
- even if majority makes a mistake; it doesn't make it correct
- be a good example for others
- combating widespread incorrectness/misconception by consistently doing it correctly
- hoping/trying to convince others that your view/opinion/way is right by consistently sticking to it despite many being ignorant/mistaken/unaware/holding different opinion
- popular misconceptions
- lead by example
- perpetuation
- correctness
Annotators
URL
-
-
-
en.wikipedia.org en.wikipedia.org
-
It reused many ideas and classes from Doug Lea's Collections package, which was deprecated as a result.
-
- Jul 2020
-
amp.dev amp.dev
-
In addition to the schema.org structured data format, there are other formats supported by search engines and social media networks. See the supported documentation: Twitter Cards meta tags Facebook Open Graph meta tags
-
-
amp.dev amp.dev
-
A growing number of platforms, vendors, and partners support the AMP Project by providing custom components or offering integration with AMP pages within their platforms.
I guess AMP is actually open-source software, but it still feels like it's something non-standard. I guess it's just an alternative open standard to the "main" web open standards.
-
-
amp.dev amp.dev
-
A growing number of email platforms, clients and providers support AMP for Email within their platforms.
-
-
amp.dev amp.dev
-
If you have worked with emails before, the idea of placing a script into an email may set off alarm bells in your head! Rest assured, email providers who support AMP emails enforce fierce security checks that only allow vetted AMP scripts to run in their clients. This enables dynamic and interactive features to run directly in the recipients mailboxes with no security vulnerabilities! Read more about the required markup for AMP Emails here.
-
-
bugs.ruby-lang.org bugs.ruby-lang.org
-
All activities are best-effort (keep in mind that most of us are volunteer developers).
-
The date, time and place are scheduled according to when/where we can reserve Matz's time.
-
- Jun 2020
-
www.newscientist.com www.newscientist.com
-
Kucharski, A. (n.d.). The pandemic playbook: A step-by-step guide to containing an outbreak. New Scientist. Retrieved June 17, 2020, from https://www.newscientist.com/article/mg24632871-500-the-pandemic-playbook-a-step-by-step-guide-to-containing-an-outbreak/
-
-
docs.syncthing.net docs.syncthing.net
-
Data that is sent over the network is compressed (optionally) and encrypted (always). When receiving data it must be decrypted and then (if compressed) decompressed.
Tags
Annotators
URL
-
-
grammarist.com grammarist.com
-
In a rare show of solidarity, both British English and American English spell advertise with an s in all forms.
-
As an act of defiance, I will only use advertize. I’ve added the word to my spell check. As an American, it makes sense for me to use this spelling since other -ise words use the more phonetic -ize suffix.
-
- May 2020
-
twitter.com twitter.com
-
Vaughan Bell en Twitter: “A brief guide for psychologists wanting to find research on the role of psychology relevant to COVID-19. You need to search for studies in the same way you search for studies normally. However, some pointers to sites and key words might be useful...” / Twitter. (n.d.). Twitter. Retrieved April 15, 2020, from https://twitter.com/vaughanbell/status/1242028124407242752
-
-
www.ganttlab.com www.ganttlab.com
-
Specify a GanttStart and a GanttDue, GanttLab will give you the higher overview.
-
-
about.gitlab.com about.gitlab.com
-
Where we got our inspiration The awesome Travis CI had the great idea to use a .yml file for builds and was followed by the popular CircleCI. We're happy to follow this approach, which we believe is superior than any other.
-
-
github.com github.com
-
touchpoints-demo.app.cloud.gov touchpoints-demo.app.cloud.gov
-
A United States government application
-
-
www.digitalocean.com www.digitalocean.com
-
We believe in the power of open source software. That’s why we participate in, contribute to, and support the open source community so strongly.
-
-
about.gitlab.com about.gitlab.com
-
Technical and general support for those using our free options is “Community First”. Like many other free SaaS products, users are first directed to find support in community sources such as the following:
-
-
-
For general questions, use cases, or anything else that does not fit into one of the above cases, please post in the GitLab Forum or on a third-party help site.
-
-
www.enchantingmarketing.com www.enchantingmarketing.com
-
Studying the masters will help you understand how all copywriting elements fit together.
-
-
www.grammarly.com www.grammarly.com
-
In other places, such as Great Britain and Canada, labelled is a more common spelling than labeled.
-
-
www.iubenda.com www.iubenda.com
-
Services generally fall into two categories: Services related to your own data collection activities (eg. contact forms)Services related to third-party data collection activities (eg. Google Analytics)
-
-
www.iubenda.com www.iubenda.com
-
Generally, these laws apply to any service targeting residents of the region, which effectively means that they may apply to your business whether it’s located in the region or not.
-
-
www.iubenda.com www.iubenda.com
-
Generally, such legislations apply to any service targeting residents of the region, which effectively means that they may apply to your business whether it’s located in the region or not
-
These rules usually apply to any company selling to EU residents but may vary for international sellers on a case-by-case basis. It is worth noting, however, that in recent cases US courts have chosen to uphold the applicable EU law.
-
-
-
While there are security benefits to disallowing unsigned extensions by default, it is not clear why there is no option to turn off this behavior, perhaps by making it configurable only with administrator rights.
-
It would be best to offer an official way to allow installing local, unsigned extensions, and make the option configurable only by root, while also showing appropiate warnings about the potential risks of installing unsigned extensions.
-
If any Firefox engineers are reading this, please don't try to subvert the above workaround, it requires multiple steps and administrator rights to set up, and we must all agree that it is of little sense for Firefox to try defending against unwanted programs or malware that has root access on the device.
-
They don't have to host the extension on their website, but it's absolutely and utterly unacceptable for them to interfere with me choosing to come to github and install it.
-
I appreciate the vigilance, but it would be even better to actually publish a technical reasoning for why do you folks believe Firefox is above the device owner, and the root user, and why there should be no possibility through any means and configuration protections to enable users to run their own code in the release version of Firefox.
-
I appreciate the vigilance, but it would be even better to actually publish a technical reasoning for why do you folks believe Firefox is above the device owner, and the root user, and why there should be no possibility through any means and configuration protections to enable users to run their own code in the release version of Firefox.
-
We must consider introducing sensible default options in Firefox, while also educating users and allowing them to override certain features, instead of placing marginal security benefits above user liberties and free choice.
Tags
- security
- balance
- freedom
- bypassing technical constraints
- the owner of a device/computer should have freedom to use it however they wish
- digital rights
- balance of power
- allowing security constraints to be bypassed by users
- good idea
- compromise
- trade-offs
- empowering individual users
- good point
- marginal benefits
- software freedom
- empowering people
- can't prevent abuse by processes with root access
- answer the "why?"
- secure by default
Annotators
URL
-
- Apr 2020
-
www.iubenda.com www.iubenda.com
-
purposes are grouped into 5 categories (strictly necessary, basic interactions & functionalities, experience enhancement, measurement, targeting & advertising)
-
-
grammarist.com grammarist.com
-
While Web site is still doing well in the U.S., it is all but dead in the U.K. Current Google News searches limited to U.K. publications find only about one instance of Web site (or web site) for every thousand instances of website. The ratio is similar in Australian and New Zealand publications. In Canada, the ratio is somewhere in the middle—about 20 to one in favor of the one-word form.
-
Exceptions are easily found, however, especially in American sources, where Web site (or web site, without the capital w) appears about once for every six instances of website. This is likely due to the influence of the New York Times, which is notoriously conservative with tech terms. The Times still uses Web site, and many American publications follow suit. Yet even those that often use Web site in their more closely edited sections tend to allow website in their blogs and other web-only sections.
-
-
ell.stackexchange.com ell.stackexchange.com
-
Other languages, German for example, are notorious for very long compunds like this and this, that are made up and written as one word directly. Perhaps the way your native language deals with compounds explains your (or other authors') personal preference and sense of "right"?
-
-
guides.rubyonrails.org guides.rubyonrails.org
-
superseded by: https://guides.rubyonrails.org/security.html
Tags
Annotators
URL
-
-
security.googleblog.com security.googleblog.com
-
At the same time, we need to ensure that no information about other unsafe usernames or passwords leaks in the process, and that brute force guessing is not an option. Password Checkup addresses all of these requirements by using multiple rounds of hashing, k-anonymity, and private set intersection with blinding.
-
Privacy is at the heart of our design: Your usernames and passwords are incredibly sensitive. We designed Password Checkup with privacy-preserving technologies to never reveal this personal information to Google. We also designed Password Checkup to prevent an attacker from abusing Password Checkup to reveal unsafe usernames and passwords. Finally, all statistics reported by the extension are anonymous. These metrics include the number of lookups that surface an unsafe credential, whether an alert leads to a password change, and the web domain involved for improving site compatibility.
-
-
github.com github.com
-
Can we merge this? Or will I have to maintain my own fork?
-
-
github.com github.com
-
Inspired by
Tags
Annotators
URL
-
-
github.com github.com
-
Inspired by AM::SecurePassword
Tags
Annotators
URL
-
-
www.techrepublic.com www.techrepublic.com
-
there's no reasonable way to communicate effectively with the less technically minded without acquiescing to the nontechnical misuse of the term "hacker"
-
The more easily relabeled of the two uses of the term "hacker" is the malicious security cracker: it is not only the more recent phenomenon to acquire that label, but also the one whose meaning is most easily evoked by an alternative term. This is why, when you read an article of mine that talks about malicious security crackers, I use the term "malicious security cracker"
Tags
- communicating with less technical people
- acquiescing/giving in
- hoping/trying to convince others that your view/opinion/way is right by consistently sticking to it despite many being ignorant/mistaken/unaware/holding different opinion
- popular misconceptions
- communication
- alternative to mainstream way
- "hacker" vs. "cracker"
- language
- language: misuse of word
Annotators
URL
-
-
www.troyhunt.com www.troyhunt.com
-
I'm not your personal lookup service And finally, for everyone who contacts me privately and says "but could you just look up my own password", please understand that you're one of many people who ask this. I try and reply to everyone who asks and politely refer them to my previous writing on the subject, but even then, all the time I spend replying to these requests is time I can't spend building out the service, adding more data, earning a living doing other things or spending time with my family. For the last 3 and a half years that I've run HIBP, I've kept all the same features free and highly available as a community service. I want to keep it that way but I have to carefully manage my time in order to do that so in addition to all the reasons already stated above, no, I'm not your personal lookup service.
-
-
accessmedicine.mhmedical.com accessmedicine.mhmedical.com
-
Delayed primary closure, or healing by tertiary intention, represents a combination of the first two, consisting of the placement of sutures, allowing the wound to stay open for a few days, and the subsequent closure of the sutures
-
Surgical wounds can heal in several ways. An incised wound that is clean and closed by sutures is said to heal by primary intention
-
Often, because of bacterial contamination or tissue loss, a wound will be left open to heal by granulation tissue formation and contraction; this constitutes healing by secondary intention
-
Fibroblasts stimulated by growth factors can produce type I collagen and glycosaminoglycans (e.g., chondroitin sulfates), which adhere to the wound surface to permit epithelial cell migration, as well as adhesive ligands (e.g., the matrix protein fibronectin), which promote cell adhesion.
-
-
www.w3.org www.w3.org
-
We will use the Open Annotation specs as the basis for a more formal data model standard.
Tags
Annotators
URL
-
-
github.com github.com
-
heavily inspired in RSpec Expectations
Tags
Annotators
URL
-
-
cucumber.io cucumber.io
-
Then the programmer(s) will go over the scenarios, refining the steps for clarification and increased testability. The result is then reviewed by the domain expert to ensure the intent has not been compromised by the programmers’ reworking.
-
-
cucumber.io cucumber.io
-
Enable Frictionless Collaboration CucumberStudio empowers the whole team to read and refine executable specifications without needing technical tools. Business and technology teams can collaborate on acceptance criteria and bridge their gap.
-
- Mar 2020
-
www.iubenda.com www.iubenda.com
-
it would appear impossible to require a publisher to provide information on and obtain consent for the installation of cookies on his own website also with regard to those installed by “third parties**”
-
Our solution goes a bit further than this by pointing to the browser options, third-party tools and by linking to the third party providers, who are ultimately responsible for managing the opt-out for their own tracking tools.
-
You are also not required to manage consent for third-party cookies directly on your site/app as this responsibility falls to the individual third-parties. You are, however, required to at least facilitate the process by linking to the relevant policies of these third-parties.
-
the publisher would be required to check, from time to time, that what is declared by the third parties corresponds to the purposes they are actually aiming at via their cookies. This is a daunting task because a publisher often has no direct contacts with all the third parties installing cookies via his website, nor does he/she know the logic underlying the respective processing.
-
-
www.jeffalytics.com www.jeffalytics.com
-
Decision point #2 – Do you send any data to third parties, directly or inadvertently? <img class="alignnone size-full wp-image-10174" src="https://www.jeffalytics.com/wp-content/uploads/7deb832d95678dc21cc23208d76f4144_Flowchart.png" alt="GDPR cookie consent flowchart" width="1451" height="601" srcset="https://www.jeffalytics.com/wp-content/uploads/7deb832d95678dc21cc23208d76f4144_Flowchart.png 1451w, https://www.jeffalytics.com/wp-content/uploads/7deb832d95678dc21cc23208d76f4144_Flowchart-300x124.png 300w, https://www.jeffalytics.com/wp-content/uploads/7deb832d95678dc21cc23208d76f4144_Flowchart-981x406.png 981w, https://www.jeffalytics.com/wp-content/uploads/7deb832d95678dc21cc23208d76f4144_Flowchart-761x315.png 761w, https://www.jeffalytics.com/wp-content/uploads/7deb832d95678dc21cc23208d76f4144_Flowchart-611x253.png 611w, https://www.jeffalytics.com/wp-content/uploads/7deb832d95678dc21cc23208d76f4144_Flowchart-386x160.png 386w, https://www.jeffalytics.com/wp-content/uploads/7deb832d95678dc21cc23208d76f4144_Flowchart-283x117.png 283w, https://www.jeffalytics.com/wp-content/uploads/7deb832d95678dc21cc23208d76f4144_Flowchart-600x249.png 600w, https://www.jeffalytics.com/wp-content/uploads/7deb832d95678dc21cc23208d76f4144_Flowchart-1024x424.png 1024w, https://www.jeffalytics.com/wp-content/uploads/7deb832d95678dc21cc23208d76f4144_Flowchart-50x21.png 50w, https://www.jeffalytics.com/wp-content/uploads/7deb832d95678dc21cc23208d76f4144_Flowchart-250x104.png 250w, https://www.jeffalytics.com/wp-content/uploads/7deb832d95678dc21cc23208d76f4144_Flowchart-241x100.png 241w, https://www.jeffalytics.com/wp-content/uploads/7deb832d95678dc21cc23208d76f4144_Flowchart-400x166.png 400w, https://www.jeffalytics.com/wp-content/uploads/7deb832d95678dc21cc23208d76f4144_Flowchart-350x145.png 350w, https://www.jeffalytics.com/wp-content/uploads/7deb832d95678dc21cc23208d76f4144_Flowchart-840x348.png 840w, https://www.jeffalytics.com/wp-content/uploads/7deb832d95678dc21cc23208d76f4144_Flowchart-860x356.png 860w, https://www.jeffalytics.com/wp-content/uploads/7deb832d95678dc21cc23208d76f4144_Flowchart-1030x427.png 1030w" sizes="(max-width: 1451px) 100vw, 1451px" /> Remember, inadvertently transmitting data to third parties can occur through the plugins you use on your website. You don't necessarily have to be doing this proactively. If the answer is “Yes,” then to comply with GDPR, you should use a cookie consent popup.
-
-
guides.rubyonrails.org guides.rubyonrails.org
-
For several reasons the Simple backend shipped with Active Support only does the "simplest thing that could possibly work" for Ruby on Rails3 ... which means that it is only guaranteed to work for English and, as a side effect, languages that are very similar to English. Also, the simple backend is only capable of reading translations but cannot dynamically store them to any format.That does not mean you're stuck with these limitations, though. The Ruby I18n gem makes it very easy to exchange the Simple backend implementation with something else that fits better for your needs, by passing a backend instance to the I18n.backend= setter.
-
-
developer.wordpress.org developer.wordpress.org
-
Used By
I like how they have indexed their core code base so they can show in both directions:
- which other core functions a function uses
- which other core functions use this function (references)
-
-
github.com github.com
-
Unless you specifically need the open source tool, most website owners will be better served by the hosted version
-
- Feb 2020
-
opensquare.nyupress.org opensquare.nyupress.org
-
By Any Media Necessary The New Youth Activism
book
-
-
k6.io k6.io
-
Load Impact is the initiator of, and an active participant in, the k6 open-source project, trying to serve its needs and lead by example
-
-
github.com github.com
-
We Open Source and actively participate in various OSS programs such as Google Summer of Code(GSoC), Rails Girls Summer of Code (RGSoC), Outreachy and Google Code-In (GCI).
-
-
github.com github.com
-
Inspired by Pundit
Tags
Annotators
URL
-
-
chrisbateman.github.io chrisbateman.github.io
-
Thanks also to this example from the D3 gallery for demonstating how to create sunburst charts.
-
- Jan 2020
-
www.techrepublic.com www.techrepublic.com
-
one that would borrow the best features from the ABC language
-
Well, why don't I create my own language', stealing my ideas from ABC
-
- Dec 2019
-
www.howtogeek.com www.howtogeek.com
-
There are thousands of to-do list apps out there, in part because no system works perfectly for everyone. I’m not going to say todo.txt is the exception, and that it will work for everyone, because that would be crazy. But todo.txt is the most flexible tool I’ve come across. In part, this is because of the sheer number of clients available, but also because the simplicity lends itself to improvisation.
First time I've seen improvisation used like this.
-
-
-
You're not going to find many checkboxes, drop-downs, reminders, or date pickers here.
Thankfully, some clients like https://github.com/QTodoTxt/QTodoTxt2 do have nice features like autocomplete, and date pickers.
-
Simplicity is todo.txt's core value
-
-
burnsoftware.wordpress.com burnsoftware.wordpress.com
-
Files are sorted by moving them all into a folder with today’s date, and you can organize these folders by day, week, or month.
-
-
unixwiz.net unixwiz.net
-
The tools are free... ... but support is not. I'm always happy to receive reports of errors or unclear spots in my Tips or tools, but they don't generally include free support. To the extent that you're operating outside your comfort zone, please retain professional advice from either iSystems Technical support, or from an experienced Evolution consultant. I'm available on an hourly basis, or with retainer plans that provided prioritized responses and reduced hourly rates.
Tags
Annotators
URL
-
-
-
Choose Your Plan
-
-
www.kickstarter.com www.kickstarter.com
-
In a nutshell, the King's Keys deck started as an experiment to see what card games would be like if you rebuilt playing cards from the ground up. Instead of using ranks and suits, each card has a number (from one to four), one of four items, and one of four colors. The result is what I call a 4x4x4 deck where 64 playing cards each have a unique combination of these three parts.
-
-
stackoverflow.com stackoverflow.com
-
Arguably, the rails-team's choice of raising ArgumentError instead of validation error is correct in the sense that we have full control over what options a user can select from a radio buttons group, or can select over a select field, so if a programmer happens to add a new radio button that has a typo for its value, then it is good to raise an error as it is an application error, and not a user error. However, for APIs, this will not work because we do not have any control anymore on what values get sent to the server.
-
-
stackoverflow.com stackoverflow.com
-
When the controller creates the user, instead of adding a validation error to the record, it raises an exception. How to avoid this?
-
-
stackoverflow.com stackoverflow.com
-
But now the first line throws an exception ArgumentError: '0' is not a valid audience
-
-
ewontfix.com ewontfix.com
-
Unfortunately, it also gets the other properties, including bringing down the whole system when it crashes. This matters because systemd is complex
Tags
Annotators
URL
-
- Nov 2019
-
www.youtube.com www.youtube.com
-
github.com github.com
-
We hope that this approach will bring us the best of worlds - the ability to have a commercially sustainable product, with high quality - as well as giving back to the open source communities by having our work eventually end up in the open, and ensuring that external contributions are always open source.
-
Because of the support we've received from open source communities, we've decided to dual-license the code after 18 months
Interesting licensing solution/choice...
-
Onivim 2 is a reimagination of the Oni editor. Onivim 2 aims to bring the speed of Sublime, the language integration of VSCode, and the modal editing experience of Vim together, in a single package.
-
-
www.valentinog.com www.valentinog.com
-
“Code without tests is broken by design”
-
- Oct 2019
-
github.com github.com
-
If I had more time, I would have explored an API close to https://sancho-ui.com/components/combobox and https://ui.reach.tech/combobox/.
Tags
Annotators
URL
-
-
sancho-ui.com sancho-ui.com
-
Sancho originally started as a fork of Evergreen but has since evolved to incorporate my favourite ideas from Bootstrap and Material-UI. We make substantial use of Reach-UI where possible to ensure proper accessibility. This project is obviously hugely indebted to all of these projects.
-
-
-
The annual festival, which takes place this Saturday, has grown to become one of the city's largest events, attracting about 100,000 people to the streets of Eastwood. Organisers say it is second only to the Royal Easter Show.
Oooh yeah, so big that if a self-serving politician didn't convince you to regurgitate this story (to divert attention from a historical failure) the best coverage it could have enjoyed in the SMH would have been a reference in one of your crossword puzzle! In the end Granny Smith got some great free publicity, and the narcissistic politician who made sure you (and your readers) missed half the story, would be happy you saved them from being reminded about another of their many failed campaigns.
-
-
stackoverflow.blog stackoverflow.blog
-
Robert Sedlack, my professor for Visual Communication Design I (who also happened to be my advisor and the driving reason why I decided to join the design program) banned two phrases during critiques in his class: “I like” and “I don’t like.”
-
- Sep 2019
-
github.com github.com
-
github.com github.com
-
Inspired by
Tags
Annotators
URL
-
-
github.com github.com
-
For a more modern alternative to ngReact, we recommend react2angular, angular2react, and ngimport.
-
- Aug 2019
-
material-ui.com material-ui.com
-
Material-UI's styling solution is inspired by many other styling libraries such as styled-components and emotion.
-
-
-
github.com github.com
-
Inspirations
-
-
codesandbox.io codesandbox.io
-
Demonstrates how label text will wrap at a point that appears to narrow when shrunk (the label can't even be as wide as the input it is labeling!), and how to work around this problem by adding styles:
'& label': { whiteSpace: 'nowrap' }Of course, you would only want to do this if you are going to only be showing the label in shrunk state (which I think is safe to say is the case for date picker inputs), since it would look bad to actually have text overflowing outside of the input box. But if it's in "shrink" state, then it's actually above the input, so as long as there isn't another input/label directly to the right, and/or as long as we adjust the width so the right side of the label mostly lines up with the right side of the input, then I think we should be safe.
The input label "shrink" state isn't always correct. The input label is supposed to shrink as soon as the input is displaying something. In some circumstances, we can't determine the "shrink" state (number input, datetime input, Stripe input). You might notice an overlap.
To workaround the issue, you can force the "shrink" state of the label.
You need to make sure that the input is larger than the label to display correctly.
-
-
emotion.sh emotion.sh
-
@emotion/core
-
-
www.schneier.com www.schneier.com
-
what does surveillance mean in this case? It could easily mean "oversight by citizens"
-
- May 2019
-
onbeing.org onbeing.org
-
It’s a more Eastern idea that suffering is part of life.
Note to self: try to find some good citation/literature on this
-
-
medium.com medium.com
- Apr 2019
-
www.ncbi.nlm.nih.gov www.ncbi.nlm.nih.gov
-
patients with a medical history of autoimmunity
That's a lot of people too.
-
That's a lot of people.
-
- Mar 2019
-
drive.google.com drive.google.com
-
This is a description of the form of backward design referred to as Understanding by Design. In its simplest form, this is a three step process in which instructional designers first specify desired outcomes and acceptable evidence before specifying learning activities. This presentation may be a little boring to read as it is text-heavy and black and white, but those same attributes make it printer friendly. rating 3/5
-
-
www.broadbentinstitute.ca www.broadbentinstitute.ca
-
to consider applying for this for Admin Data Coalition work.
-
- Feb 2019
-
www.npr.org www.npr.org
-
Blood Orange
What feminism is --- this first song gave me chills!! So good!
-
- Dec 2018
-
reimaginingthebom.com reimaginingthebom.com
-
my proceedings in my days
The Egyptian Book of the Dead as it is most commonly called today was and is also known as the Book of Breathings or the Book of Coming Forth by Day. In this last title it is strongly implied that, besides being a funerary text the book should be understood and read as a type of dreaming journal too. This very aptly applies to what we are reading here with regards Lehi's writings of the "many things" which he saw in "visions and dreams" and which he "prophesied and spake" (breathings) unto his children.
The combination of "learning of the Jews" with "language of the Egyptians" should be kept in mind throughout a reading of the BOM and will be especially plain at certain parts.
-
-
festive.ninja festive.ninja
-
It’s about doing the one little thing you can do, even if it’s useless: planting seeds in the midst of the apocalypse, spitting on a wildfire, bailing out the ocean with a bucket. Individual action is almost always pointless.
I believe there are things which can be easily classified as "useless" and have absolutely no impact on the end result (see: a single vote in a normal election)
On the other hand, there are things which do make a small contribution to the end result, even if it's very little. I don't like to call these "useless" because they do have an impact. These should be done even if the individual result is invisible.
The examples shown here belong to the second category.
-
- Oct 2018
-
opencontent.org opencontent.org
-
Consequently, the SA condition does not apply to your contributions to modified works including these kinds of changes.
Examples would really help. I can't imagine a scenario where anyone would care about this. As was pointed out in the comments, making minor corrections to a CC BY-SA work would not enable anyone to reshare that entire work with corrections under a new license. So the case here is if someone wanted to share minor corrections to a work independently of the work itself and license those minor corrections differently? For example: Here are my typo corrections to a published work, outside of the context of that published work? Example please...
-
In other words, the CC licenses (all of which include the BY condition) enable the creator of a work to prohibit you from attributing them. However, except in the extremely rare cases where the creator explicitly prohibits you from attributing them, you are always required to attribute the creator of a work shared under a CC BY license.
Except for the semi-famous case of the open resources collected in lardbucket, how often does this example appear in the wild?
-
-
cnx.org cnx.org
-
Federalism has the capability of being both bad and good. It just depends who you ask. On one side the advantages of fedaralism is it creates more effectiveness and makes the government stable. On the other hand federalism is risky it gets expensive, lead to a complex tax system and is slow in responses to crisis.
Tags
Annotators
URL
-
- Sep 2018
-
mashable.com mashable.com
-
Snapchat says it reaches 28.5 to 30 million 18-24 year old users in the U.S. According to a recent survey of Instagram users, approximately 32 percent of its 1 billion-strong user base is 18-24.
Snapchat reaches around 30 million 18-24 year old users; important ages that are more recently able to vote and take political action. Instagram and snapchat are most popular amongst younger users.
-
-
certificates.creativecommons.org certificates.creativecommons.org
-
To add to "More scholarship about CC licenses" and to support unit 4.1: Bishop, Carrie. “Creative Commons and Open Access Initiatives: How to Stay Sane and Influence People.” Art Libraries Journal 40.4 (2015): 8–12. Web.
Bishop presents a cheerful exploration of the Tate’s mammoth enterprise to digitize and release into the public Web 52,000 works of art, many of which are still under copyright. Commonly, galleries and museums would like to broaden exposure to the artwork in their collections, but when artists or their descendants are still actively monitoring use and income, there can be a barrier between connecting the public with the art work and the needs of the artistic community. Bishop describes the Tate’s desire to license the newly digitized images under a Creative Commons license to provide clear guidelines to the public, but at the same time to respond to the fears, hopes, and wishes of their artists. The Tate decided that it could best realize its goal to "democratize access" and to connect the public with British artists through applying the CC-BY-NC-ND license—both making the images available and quelling the concerns of the artists or their estate managing family members. The article provides an interesting perspective to the discussion of “open culture” or “free culture.” Some of this freedom may come about in incremental doses. The CC license might make it possible to allow an artist to connect their work with a larger public, at the same time that it makes them confident that their work won’t be misused or appropriated in an undesired manner. Aart museums seem to have a difficult relationship with open access and Creative Commons licensing. The Getty, for instance, has a fairly complicated statement of terms that make murky all that CC transparency, so there is viewing the material and then there is repurposing the material. The result is that a slow, measured pace, while nurturing the artist along, may be the way to ultimately make CC and Open Access a norm rather than an exception.
-
-
certificates.creativecommons.org certificates.creativecommons.org
-
Gulley, Nicola. “Creative Commons: Challenges and Solutions for Researchers; a Publisher’s Perspective of Copyright in an Open Access Environment.” Insights: the UKSG journal 26.2 (2013): 168–173. Web. Unit 3.2 (New Article)
Gulley, Nicola. “Creative Commons: Challenges and Solutions for Researchers; a Publisher’s Perspective of Copyright in an Open Access Environment.” Insights: the UKSG journal 26.2 (2013): 168–173. Web. Gulley, a publisher with Institute of Physics (IOP) sets out to describe and clarify the CC BY license for researchers who may be wary of making use of it for their own work. The Research Councils UK currently require APC funded OA articles to be made available under a Creative Commons Attribution license . This license is also favored by the UK’s Wellcome Trust).
Although this is a 2013 article, Gulley’s overview of the six licenses is still largely valid. The benefits she sites include clarity for the user, the ability to build on past research—the primary need for scientists and providing a nearly internationally applicable standard (something that has only improved since she wrote her article). Gulley cites that authors have expressed concern over maintaining control of their work over time and against derivative uses, maintaining the integrity and context of their work, and the compatibility as CC licenses are combined into a single work.
Gulley explains in detail the more weedy aspects of CC-BY licensing, and how to address some of the concerns she mentioned in line with established Creative Commons policy. In fact, IOP has adopted CC BY licensing for its publications (presumably for their openly accessible content) because the opportunities for sharing outweigh any negative effects.
-
- Jul 2018
-
-
“I support a social transition for a kid who is in distress and needs to live in a different way. And I do so because I am very focused on what the child needs at that time,” said Johanna Olson-Kennedy, medical director of the Center for Transyouth Health and Development at Children’s Hospital Los Angeles, the largest transgender youth clinic in the United States with some 750 patients. A social transition to the other gender helps children learn, make friends, and participate in family activities. Some will decide later they are not transgender, but Olson-Kennedy says the potential harm in such cases may be overstated.
This is one of the major problems in how so many approach this whole issue weather as a topic or in deciding a course of action for their own child. Furthermore the possibility of that happiness now rests on either on secrecy and passing or as is more often the case today it rests on the cooperation and orchestration of a comprehensive enough segment of the total people with whom your child is interacting to support this transition. What if we did that for gay kids. How much different would things be if tital 9 applied to all gender nonconforming kids even those who identified as gay? What if 12 states didn't have laws against speaking positively about gay as an identity in schools. What if parents where expected to do the work to insure that a self identified gay student was provided a social network for similarly identified adults and young people. And for just about any teen how might life be different emotionally speaking if we had been chemically castrated during our teen years. What if gay kids had the same wealth of support materials - public discourse etc. The reaason they don't is because we can not deal with their difference and we can not deal with it being about their sexual desire because we are unnerved by a the fact that children can identify and feel and act on sexual interests at a very young age. Gay kids know this and that is a big hurdle to comming out. I wished so much to have a boyfirend then I felt I could come out because it wouldn't mean telling my parents that I think about boys in a sexual way but I love this boy and won't deny him to anyone. No sad to say as was noted when oposition was initially raised amoung APA members over the introduction of GID to the DSM when they stated that it may just be that gay is a normal healthy worthy course of human development that as part of that process involves being in some way emotionally maimed by which they meant that there are certain painfull encounters with being different than ones own parents and most people in your community that gay people by dfinitioon must edure and untill society changes being gay is known to be a bad undesirable thing by children at a tremendously young age. So to be and develop as a person who is homosexual is not going to happen without certain paiuns and obsticles that others can easily avoid and mostly do.
-
- Jun 2018
-
www.seethingbrains.com www.seethingbrains.com
-
Am starved for meat, giddy for lack of sleep, With oath kept waking and with brawling fed:

-
-
hypothes.is hypothes.is
-
American but hyphenated, viewed by Anglos as perhaps exotic
-
- May 2018
-
eng125sp18.commons.gc.cuny.edu eng125sp18.commons.gc.cuny.edu
-
War in the east, War in the west, War up north, War down south – War – war –
This quote, want you pay attention to how there is war going on and focus basic on only war.
-
Will remain in but a fleeting illusion to be pursued, But never attained –
I feel as you can imagine go back in time feel every emotion as you read this quote.
-
- Nov 2017
-
mfeldstein.com mfeldstein.com
-
The selection committee declares that whatever LMS the university chooses next must work exactly like Blackboard and exactly like Moodle while having all the features of Canvas. Oh, and it must be "innovative" and "next-generation" too, because we're sick of LMSs that all look and work the same.
-
-
wrapping.marthaburtis.net wrapping.marthaburtis.net
-
Finding Our Metaphors
The visual metaphor is quite intriguing. For some weird reason, it reminds me of La Jetée.
-
every moment in which we walk a student through a fix is a deeply teachable moment
-
the breaking and fixing of things is where the most learning can occur
-
- Oct 2017
-
rampages.us rampages.us
-
poetry and music have always been closely related. poetry can contain many different kind of rhythm at the same time to create a complex rhythmic.
-
- Jul 2017
-
www.swamirara.com www.swamirara.com
- Jun 2017
-
inst-fs-iad-prod.inscloudgate.net inst-fs-iad-prod.inscloudgate.net
-
I use backwards de-sign to develop our lesson plans: What do we want our students to write, and why? What skills are required, and how do students acquire those skills (Wiggins and McTighe 34)?
McTighe's UbD advice to "think big, start small, and go for an early win" is helpful here (and whenever trying new approaches to teaching): https://youtu.be/d8F1SnWaIfE?t=3m40s
-
- Mar 2017
-
en.wikipedia.org en.wikipedia.org
-
The central idea of DbC is a metaphor on how elements of a software system collaborate with each other on the basis of mutual obligations and benefits.
Offer, acceptance, mutual consideration: CONTRACT!
-
-
www.edutopia.org www.edutopia.org
-
project-based learning (PBL), game-based learning (GBL), Understanding by Design (UbD), or authentic literacy, find an effective model to institute in your classroom
Project based learning Game based learning Understanding by design
-
- Feb 2017
-
0-quod.lib.umich.edu.mercury.concordia.ca 0-quod.lib.umich.edu.mercury.concordia.ca
-
That was the way I learned
We learn by doing. (And annotations do work on the text version. Neat!)
-
- Aug 2016
-
pdfsr.com pdfsr.com
-
Proteus Vulgaris Characteristics – Biofield Treatment Analysis Biofield energy treatment is an alternative therapy approach that is studied in this research to bring the positive alternations in the characteristics of Proteus Vulgaris.
-
-
works.bepress.com works.bepress.com
-
Proteus Vulgaris - Hospital Acquired Infections Proteus Vulgaris is a gram-negative bacterium that is ranked third as the cause of hospital-acquired infections. The present study was undertaken to study the impact of an alternative energy treatment on properties of Proteus Vulgaris.
Tags
Annotators
URL
-
-
loop.frontiersin.org loop.frontiersin.org
-
Study of Proteus Vulgaris Antimicrobials Susceptibility Proteus Vulgaris antimicrobials susceptibility analysis shows changes in minimum inhibitory concentration and susceptibility patterns as compared to control sample after biofield energy treatment.
Tags
Annotators
URL
-
-
www.mendeley.com www.mendeley.com
-
Proteus Vulgaris - Impact of Human Energy Treatment Biochemical test results shows the impact of human energy treatment on phenotyping and genotyping characteristics of Proteus Vulgaris. Read here to know about this study.
Tags
Annotators
URL
-
- Jul 2016
-
www.diplopiagame.com www.diplopiagame.com
-
Perceptual Learning - Training the brain to better perceive the information it is getting from the eyes.
This would be the optimal learning experience, for me.
-
- Feb 2016
-
www.raspberrypi.org www.raspberrypi.org
-
gender neutrality, creativity, imagination and tinker time are the basis for learning
Not just for Carrie Anne Philbin’s CS classroom. For so many approaches to learning, these principles help a lot.
-
- Oct 2015
-
cms.whittier.edu cms.whittier.edu
-
They succeed in doing so largely because the states underwhich they operate are the “soft-states,” in that despite their oftenauthoritarian disposition and political omnipresence, they lack the nec-essary capacity, the hegemony and technological efficacy, to impose full
control over society."
It's the people that push the boundaries who find out just how strong/weak they really are. It is more about the atmosphere of a disciplinary society aided by the people's fear that's being enacted throughout societies instead of actual and legitimate control.
-
-
192.168.43.3:8000 192.168.43.3:8000
-
namic languages such as JavaScript are more difficult to com-pile than statically typed ones. Since no concrete type informationis available, traditional compilers need to emit generic code that canhandle all possible type combinations at runtime. We present an al-ternative compilation technique for dynamically-typ
first comment!
-
- Sep 2015
-
www.jeffyoungdigital.com www.jeffyoungdigital.com
-
to prove this, let facts be submitted to a candid world, for the truth of which we pledge a faith yet unsullied by falsehood.
The Declaration of Independence impacted the United States in more ways than one, Jefferson makes clear when he states "to prove this, let facts be submitted to a candid world;" he is referring to the reign of the King of Great Britain who has brought injuries and tyranny over the states. He wants his people to realize the corruption and wrongdoings that the king has caused. Jefferson is essentially saying that people should be uncorrupt in this new world and man should strive to preserve the pureness of this country keeping it from falsehood and injustice. It sparked my attention when I came across a newspaper titled "The North Briton" written by J. Wilkes and others which contained very similar diction and ideals of society during that time period. Wilkes is criticizing King George III for his speech in favor of the Treaty of Paris ending the Seven Year’s War; he states “Articles 15 is for having corrupted the sacred fountain of truth and put falsehoods into the mouth of Majesty, in several speeches made in parliament.” Wilkes is trying to uncover the king’s corruption and bring to light that he is lying to his people which ties closely to Jefferson’s actions and morals of being uncorrupt. Most people carried similar beliefs in the United States during the 18th century, it is very possible that the Wilkes could have been from Jefferson's era carrying the same ideals and values as him due to similar style of writing, choice of diction, and beliefs.
-