Synchronously waiting for the specific child processes in a (specific) order may leave zombies present longer than the above-mentioned "short period of time"
- Nov 2022
-
en.wikipedia.org en.wikipedia.org
-
-
www.w3.org www.w3.org
-
The character exists in Unicode/ISO 10646, but not in the character encoding used for the document. In this case, use Numeric Character References (NCRs, example: 噸).
-
-
docdrop.org docdrop.org
-
the container ship was simply becoming so large so unwieldy that much of the infrastructure around them is struggling to cope a lot of the decisions to build Supply chains were really based on
Impact of cheap transportation
production costs and transport costs
With transportation costs so low and logistics assumed, manufactures chased cheaper production costs. They would outsource manufacturing to low-cost countries without considering the complexity risks.
Tags
Annotators
URL
-
- Oct 2022
-
oldschool.scripting.com oldschool.scripting.com
-
-
@route @twalpole as a community I think we're super grateful for your work on a CDP alternative to chromedriver/selenium, poltergeist etc. I do think collaboration could be very valuable though, although it would likely mean abandoning one of the projects and teaming up on the other, you both obviously have very deep knowledge of CDP and therefore would get a load more done than any of us "end users" trying to wade in there. The status for us on our Rails project is that Apparition fails with a ton of errors, they all seem related to handling timing events (accept_prompt doesn't work, opening new windows seems problematic etc etc etc) whereas Cuprite only rails with a cookie gem we're using (easy fixed) and doesn't support drag_to yet. So to me Cuprite seems more complete, but I don't know much about the internals.
-
As both projects are written by 2 different people independently there's huge difference in the code. I don't think I have time or wish to merge them because it's huge amount of work. The common thing between them is only CDP that's all. Though Cuprite is already stable and supports all features that Capybara requires, we run tests and do many cools things with it in production.
-
As a history mark, when back then I asked Thomas if he started to work on CDP, he said yes but never finished it, so I started this project from scratch which by now feels completed. After releasing it I only yesterday realized that he open-sourced his project and keeps working on it. I think it just feels hard to throw everything you have written to trash, but I wasn't proposed at the beginning to work together on common project and this is the reason Cuprite had began. Though since this project is completed I see no sense to work on something else especially for me, the only difference would be in Ruby implementation which is boring as you can do things in a different manner and CDP has issues too so the difference could be only how we workaround them.
-
And yeah, you two should probably gang up :)
-
what is the difference? and why do you write it from scratch?
-
Haven't really looked through your code, so not sure what the difference is - I would guess not too much. I told you about my version when we were discussing the issues you were having on cuprite -- It was 70+ percent done so I released it and finished up most of the rest. I guess one difference is that you appear to be aiming at bleeding edge Chromium, whereas I'm more focused on things working on Chrome release since I think that's more important for people to test with (no customer is going to be running Chromium alpha).
-
I also was surprised to see 2 "kind of similar" new drivers both targeting CDP I wonder if joining forces ultimately would be a good idea?
-
-
www.animenewsnetwork.com www.animenewsnetwork.com
-
The sense of wonder and discovery that made all the cruelty of the Abyss worth enduring is gone, replaced with increasingly over-the-top attempts at shock horror that crescendos with a concept so ludicrous it stops being horrifying and starts being embarrassing.
This is exactly right. The first 9 episodes of the first season of Made in Abyss represented some of the best anime of the previous decade precisely because they depicted "[t]he sense of wonder and discovery that made all the cruelty of the Abyss worth exploring..." It was a great, and haunting, adventure story. The end of season one stagnated, the movie went over the line that the first season flirted with, and the second season lost all of the qualities (other than high production values) that made season 1 memorable. The exploring was outsourced to the flashbacks of side-characters, and the whole season was stuck in a single location that was not particularly interesting.
-
I love the first season of MiA, even more now than I did when it first aired. And on paper I should be down for more of this fascinating, macabre world of wonders and horrors. But somewhere in this second season, the graceful balancing act that made it all so compelling fell apart. Maybe it's that our main trio feel like barely relevant observers of a story largely divorced from them, loading all of Reg's character development into a flashback he doesn't even remember and relegating Nanachi to a half-season-long nap just so we can retread their goodbye to Mitty. Maybe it's the fact that the slow-burn mystery of the titular city feels as hollow as its main residents, ramping up its increasingly aimless body horror to the point that it starts to feel like an Aristocrats joke that's gone on way too long.
I agree fully with this list of flaws about the second season of Made in Abyss. The first season was terrific, but it flirted with excess in terms of violence and general unpleasantness (excess was achieved in the movie). The second season feels stagnant, sidelines the main characters, and the "aimless body horror" is a good way to describe much of the violence and grossness, which reached Elfen Lied levels of absurdity toward the end.
-
-
www.saysomethingin.com www.saysomethingin.com
-
twitter.com twitter.com
-
One of W.G. Sebald’s masterpieces, The Rings of Saturn, an indescribable blend of fact and fiction, contains a section about one of his academic colleagues whose office was piled high with notes about Gustav Flaubert.
https://twitter.com/friendsofdarwin/status/1584936047929982976
-
-
library.scholarcy.com library.scholarcy.com
-
Mirriam also struggled as an adult English learner. A Spanish language teacher and the owner of a Spanish language school for school-age children, Mirriam immigrated to Oregon after completing two years of college in Mexico.
-
-
www.noixduquebec.org www.noixduquebec.org
-
pour effectuer environ 1200 greffes durantles 10 premiers jours de juin. Les greffes ont étéeffectuées en plein champ, en utilisantprincipalement deux techniques connues sousleurs désignations anglaises : « four flaps » et« in-lay bark graft ».Le taux de succès des greffes a été de 43% enmoyenne. Les arbres sur lesquels les greffesn’ont pas réussi seront taillés et reformés pourfaire l’objet d’une nouvelle greffe dans 1 ou 2ans. Les greffes les plus difficiles à réussir ontété celles des cultivars de noyers cendrés (8% desuccès), suivies des noyers hybrides (25%).
-
-
blog.appsignal.com blog.appsignal.com
-
If we would have kept the call to super out of the #initialize_dup method, we would never have called initialize_copy, so it is important to keep that in.
-
-
-
A. F. Leach divines from stray passages in Horace and Juvenalthat schools were almost defined by its presence: ‘The edification or cult ofcharacter...was effected by beginning school at dawn and shouting at andflogging the boys with the rod or cane (ferula), the tawse (scutica), and the birch(flagellum), very much as in the English schools down to 1850.’
-
-
Local file Local file
-
Sincecopying is a chore and a bore, use of the cards, the smaller thebetter, forces one to extract the strictly relevant, to distill from thevery beginning, to pass the material through the grinder of one’s ownmind, so to speak.
Barbara Tuchman recommended using the smallest sized index cards possible to force one only to "extract the strictly relevant" because copying by hand can be both "a chore and a bore".
In the same address in 1963, she encourages "distill[ing] from the very beginning, to pass the material through the grinder of one's own mind, so to speak." This practice is similar to modern day pedagogues who encourage this practice, but with the benefit of psychology research to back up the practice.
This advice is two-fold in terms of filtering out the useless material for an author, but the grinder metaphor indicates placing multiple types of material in to to a processor to see what new combinations of products come out the other end. This touches more subtly on the idea of combinatorial creativity encouraged by Raymond Llull, Matt Ridley, et al. or the serendipity described by Niklas Luhmann and others.
When did the writing for understanding idea begin within the tradition? Was it through experience in part and then underlined with psychology research? Visit Ahrens' references on this for particular papers to read.
Link to modality shift research.
-
-
physicstoday.scitation.org physicstoday.scitation.org
-
This list is a great framework for showing students what they don't know, so they can actively work and practice at becoming better at their craft.
I feel like actively annotating and "reading with a pen in hand" has been a great way to practice many of these points. Questioning texts, marking open problems, etc. goes a long way toward practicing these methods.
-
-
archive.org archive.org
-
I love the phrasing of the title of his penultimate section "Making the card-file work", which makes it seem like the card file is ultimately doing the work of writing. Ultimately however, it's the work that was put into it that makes the card file useful, a sentiment that Jacques Goutor emphasizes when he says "How well this succeeds depends partly upon what was put into the file, and partly on how it was put in." (p34)
-
As is common in the tradition of the zettelkasten, Goutor advises "that each note-card should contain only one item of information, whether a quotation, a summary, or anything else". (p28) He ascribes this requirement to his earlier need for clarity. (cross reference: https://hypothes.is/a/SfWFwENIEe2KfGMbR5n7Qg)
He indicates that while it may seem wasteful to have only one item on each card that the savings in time, efficiency in handling, classification, and retrieval will more than compensate for the small waste.
This sort of small local waste being compensated for by a larger global savings and efficiency can be seen in the design of the shipping container industry as discussed in Mark Levinson's The Box (Princeton University Press, 2008). Was this the exact sort of efficiency mentioned by Ahrens'? (Compare at https://hypothes.is/a/t4i32IXoEeyF2n9jQxu6BA)
-
-
bio.libretexts.org bio.libretexts.org
-
NAD+ is used by the cell to "pull" electrons off of compounds and to carry them to other locations within the cell, thus they are called electron carriers
What is the NAD+ used for?
-
The oxidation of, or removal of an electron from, a molecule (whether accompanied with the removal of an accompanying proton or not) results in a change of free energy for that molecule - matter, internal energy, and entropy have all changed in the process.
What does oxidation (removal of an electron from a molecule change about Delta G?
-
Each of these two types of molecules is involved in energy transfer that involve different classes of chemical reactions. It's interesting that while one class of carrier delivers electrons (and energy), the other delivers phosphates (and energy), but both include an adenine nucleotide(s).
What does ATP carry and what does NADH carry? How are they similar?
-
In this course we will examine two major types of molecular recyclable energy carriers: (1) nicotinamide adenine dinucleotide (NAD+), a close relative nicotinamide adenine dinucleotide phosphate (NADP+), and flavin adenine dinucleotide (FAD2+) and (2) nucleotide mono-, di- and triphosphates, with particular attention paid to adenosine triphosphate (ATP).
What are the two major types of molecular recyclable energy carriers?
-
Each individual carrier in the pool can exist in one of multiple distinct states: it is either carrying a "load" of energy, a fractional load, or is "empty".
What state can carriers be in?
-
Keep in mind that a positive ΔE0' gives you a negative ΔG
What does a positive deltaE0’ potential give you in terms of delta G’s sign
-
Using the Nerst equation essentially corrects for the number of electrons per transfer (here n = 2) and puts things into units biologists can use, and copes with the directionality (sign) for us. F has units of kJ*/volt, E has units of (Volts), so we end up with kJ, a unit of energy.
What units are used for n, F, E0’, and the final delta G0’
-
here n is the number of electrons involved in each transfer, and F is a constant that is a positive number
What is n and F in Delta G0’ = -nFdeltaE0’
-
E0' values and to help us predict the direction of electron flow between potential electron donors and acceptors.
What does the E0’ be used to predict?
-
Different compounds, based on their structure and atomic composition, have intrinsic and distinct attractions for electrons. This quality is termed reduction potential or E0’ and is a relative quantity (relative by comparison to some “standard” reaction).
What does a reduction potential depend on? What units does it use?
-
By convention we analyze and describe redox reactions with respect to reduction potentials (E0'), a term that quantitatively describes the "ability" of a compound to gain electrons.
What is reduction potential? What does it indicate?
-
If you consider a generic redox reaction and reflect back on the thermodynamic lectures, what factor will determine whether a redox reaction will proceed in a particular direction spontaneously, and what might determine its rate?
The E0’ potentials can be used to determine the change in delta G and if the delta G is negative then the reaction will proceed spontaneously. If its a negative or a positive delta G it will also determine what direction the reaction will go.
-
Sometimes a redox tower will list compounds in order of decreasing redox potentials (high values on top and low values on the bottom). Our towers do not- we list (reduced vs. oxidized state) molecule pairs with negative values (highly negative E˚') up top and positive ones (highly positive E˚') towards the bottom. Does presenting the data this way change the redox potential of a compound?
I don’t think it changes it, It is just a different way of looking at it. Like a reverse. It does not change the potential or the maths.
-
The electron tower is a tool that ranks different common half reactions based on how likely they are to donate or accept electrons.
What is the electron tower? What is it used for?
-
The amount of energy transferred in a redox reaction is associated with the difference between each half reactions' reduction potential, E0
What is reduction potential E0’ And how is it calculated?
-
Because oxidation and reduction usually occur together, these pairs of reactions are called oxidation reduction reactions, or redox reactions.
What is an Oxidation reaction? What is a Reduction Reaction? Do they Happen together or one at a time?
-
The ETC produces a proton gradient. No ATP is directly generated in this process. However, the proton gradient is then used by the cell (among other things) to run an enzyme called ATP synthase which catalyzes the reaction ADP + Pi --> ATP. This method of ATP production (called oxidative respiration) results in additional- many additional- ATPs being produced.
How are further ATP’s Produced through the proton gradient?
-
- Sep 2022
-
-
Mark Robert Rank
https://sociology.wustl.edu/people/mark-rank
Herbert S. Hadley Professor of Social Welfare Washington University in Saint Louis,
-
-
books-scholarsportal-info.proxy.library.carleton.ca books-scholarsportal-info.proxy.library.carleton.ca
-
Around 1439, Johannes Gutenberg introduced the moveable-type printing press to Europe, giv-ing average people access to books that had previously been available only to scholars or the wealthy.
The new forms of media boost the speed of spreading new thoughts across Europe.
-
-
-
All five moves focus on the necessity of incorporating outside voicesinto a student’s own writings,
I can't help but think about the older practice of writing texts as dialogues.
-
-
docdrop.org docdrop.org
-
we can kind of make an assumption that 00:04:22 complex brains and by extension complex intelligence should also be somewhat common in terms of evolutionary success and assuming that it's evolutionary preferential or basically that evolves many times throughout the history of the 00:04:35 planet we can then make a conjecture that it should exist somewhere out there where life exists on other planets okay just to rephrase this if we truly believe that extraterrestrial intelligence exists out there and that 00:04:48 it kind of evolved in the same way that it evolved here on planet earth it's pretty safe to assume that it might have evolved several times on the planet because we're making an assumption here that this is an evolutionary advantage 00:05:00 that all planets that potentially have life on them are going to end up with some kind of a species that's going to become super intelligent and that's going to be self-aware able to use technology and essentially kind of communicate in the same way that we 00:05:13 communicate using for example radio waves
!- in other words : there should be signs of complex intelligence like ours in the paleontological records
-
-
-
Also, some Specification constraints cannot be represented with the JSON Schema so it's highly recommended to employ other methods to ensure compliance.
-
-
github.com github.com
-
Maybe one day, JSON Schema would be able to express all the constraints in the OpenAPI spec, but I suspect some are going to be really hard.
-
When we do release a final version of JSON Schema, please do not use JSON Schema to guarantee an OpenAPI document is valid. It cannot do that. There are numerous constraints in the written specification that cannot be expressed in JSON Schema.
-
-
stackoverflow.com stackoverflow.com
-
Incidentally, I am also the author of the website you are referring to.
-
[author of the draft v4 validation spec here]
-
-
royalsocietypublishing.org royalsocietypublishing.org
-
human long-term GCC is characterized by an evolutionary transition in inheritance (from genes to culture) which entails a transition in individuality (from genetic individual to cultural group).
!- for : Cultural Evolution - the findings of this paper point to culture is displacing genetic adaptive potential as the main driver of evolution. This is a very profound finding!
-
-
bitfieldconsulting.com bitfieldconsulting.com
-
If you like the functional style of programming, though, you’ll find a lot more facilities for it in Rust, because Rust has a lot more facilities than Go in general.
-
-
hypothes.is hypothes.is
-
Why is this important in this history of psychology?
"The present work will, I venture to think, prove that I both saw at the time the value and scope of the law which I had discovered, and have since been able to apply it to some purpose in a few original lines of investigation. But here my claims cease. I have felt all my life, and I still feel, the most sincere satisfaction that Mr. Darwin had been at work long before me, and that it was not left for me to attempt to write 'The Origin of Species.' I have long since measured my own strength, and know well that it would be quite unequal to that task. Far abler men than myself may confess that they have not that untiring patience in accumulating and that wonderful skill in using large masses of facts of the most varied kinds, -- that wide and accurate physiological knowledge, -- that acuteness in devising, and skill in carrying out, experiments, and that admirable style of composition, at once clear, persuasive, and judicial, -- qualities which, in their harmonious combination, mark out Mr. Darwin as the man, perhaps of all men now living, best fitted for the great work he has undertaken and accomplished." This comes from the Classics in the History of Psychology Limits of Natural Selection By Chauncey Wright (1870). This shows us the importamce of the limits including in theories like this one. Natural selection indicates that the strongest will be the ones that will survive and there for will be the ones that will be able to have offsprings and make their generation endure. But thjis has a limit due to the sexual selection because it shows that the natural selection can not be impossed to people in any way or form. I see this working in psychology in a very big way because now that we are in a generation that is so ruled out by the social media this concept wants to persist and endure no matter what. I can see natural selecetion slowly decreasing amd really another type of selection evolving with the next future generations.
Angela Cruz Cubero (Christian Cruz Cubero)
-
-
www.youtube.com www.youtube.com
-
here's an old model from the 19th century of memory which actually in the 21st century has come 00:13:03 back as a pretty good one as a metaphor anyway so the idea is that rain comes down on the ground and there's a little regularities randomly there and at some point those regularities will be a 00:13:17 little more responsive to the rain and a little channel will form the channel acts as an amplifier and so wherever that channel got started it starts funneling lots more water through it other water is draining into 00:13:31 it and all of a sudden it starts cutting deeper and you get these gullies and you get down into these gullies you have to remember to look up because everything 00:13:44 down there in this gully is kind of pink you can think that the world is pink and in fact if you get into a real gully one of my favorites is Grand Canyon by the 00:13:57 way that's only a hundred million years of erosion to get the Grand Canyon it's relatively recent get into one of these things and the enormity of what you see 00:14:08 outwards Dwarfs what you can see if you look up if you've ever been on one of these things you're just in a different world it's a pink world you don't think 00:14:23 about climbing out of it you think about moving along in it
!- In other words : stuck in a groove - stuck in a conceptual groove -
-
if we grow up in that world we don't know it's pink right because that's all there is that is the background color 00:15:17 it's the thing we are least interested in because it's the most constant thing
!- similar to : fish in ocean metaphor - This is very similar to the fish in the ocean metaphor, where the fish do not know there is such a thing as water because it is so ubiquitous
-
-
criticalinstructionaldesign.pressbooks.com criticalinstructionaldesign.pressbooks.com
-
If your institution just spent $500,000 on a proctoring solution (a figure recently reported by Drew Harwell in The Washington Post), or $200,000, or even $30,000, put that number next to these: How many students at your school are food or housing insecure? How many faculty or staff have been furloughed, fired, or forced into early retirement? How many positions are currently frozen? How many faculty or staff have part-time or contingent positions? Then, add up all the money your institution spends on extraneous (often pedagogically suspect) edtech—like cameras in classrooms, plagiarism detection software, the LMS, proctoring solutions—and compare that number to the total budget for the center for teaching and learning.
An exercise needed to be completed to justify the actions of incompetency. Make the argument this does not align with the mission of our institution.
-
-
Local file Local file
-
We distinguish between the historian whoclassifies verified documents for the purposes ofhistorical work, and the scholar who compiles" Regesta'' By the words " Regesta " and " Corpus ''we understand methodically classified collections ofhistorical documents. In a " Corpus " documentsare reproduced in extenso ; in " Regesta " they areanalysed and described.
a few technical words to clearly define within this context versus other related contexts.
-
-
docdrop.org docdrop.orgUntitled1
-
‘He was by a neighbour found,‘With his sieull all smashed to peices,He did lay upon the ground5O’ then what news was for his som,‘To hear his father Was no more,: ‘To think by raffians he was murdered,& At the oge of sixty-four.|
Detailed how he was found
-
- Aug 2022
-
www.uml-diagrams.org www.uml-diagrams.org
-
The interaction operator strict requires a strict sequencing (order) of the operands on the first level within the combined fragment
-
The interaction operator seq means that the combined fragment represents a weak sequencing between the behaviors of the operands.
-
-
www.uml-diagrams.org www.uml-diagrams.org
-
psyarxiv.com psyarxiv.com
-
Rothmund, T., Farkhari, F., Azevedo, F., & Ziemer, C.-T. (2020). Scientific Trust, Risk Assessment, and Conspiracy Beliefs about COVID-19—Four Patterns of Consensus and Disagreement between Scientific Experts and the German Public. PsyArXiv. https://doi.org/10.31234/osf.io/4nzuy
-
-
www.theverge.com www.theverge.com
-
Roth, E. (2021, October 30). Facebook puts tighter restrictions on vaccine misinformation targeted at children. The Verge. https://www.theverge.com/2021/10/30/22754046/facebook-tighter-restrictions-vaccine-misinformation-children
-
-
www.dutchnews.nl www.dutchnews.nl
-
More people sign up for a vaccination after coronavirus passport news. (2021, September 16). DutchNews.Nl. https://www.dutchnews.nl/news/2021/09/more-people-sign-up-for-a-vaccination-after-coronavirus-passport-news/
-
-
twitter.com twitter.com
-
ReconfigBehSci. (2021, April 21). RT @covidoneyearago: One year ago today: A paper in Clinical Infectious Diseases identifies a 16.3% rate of in-household COVID-19 infection… [Tweet]. @SciBeh. https://twitter.com/SciBeh/status/1384784541873737729
-
-
jamanetwork.com jamanetwork.com
-
Dixon, B. C., Fischer, R. S. B., Zhao, H., O’Neal, C. S., Clugston, J. R., & Gibbs, S. G. (2021). Contact and SARS-CoV-2 Infections Among College Football Athletes in the Southeastern Conference During the COVID-19 Pandemic. JAMA Network Open, 4(10), e2135566. https://doi.org/10.1001/jamanetworkopen.2021.35566
-
-
twitter.com twitter.com
-
John Bye [@_johnbye]. (2021, October 6). The new covid sceptic All Party Parliamentary Group on Pandemic Response and Recovery is backed by Gupta and Heneghan’s Collateral Global to the tune of over £30,000. £5,000 in financial benefits plus £25,501—£27,000 benefits in kind (CG is acting as their secretariat). Https://t.co/qll20Sg9aA [Tweet]. Twitter. https://twitter.com/_johnbye/status/1445867760819396608
-
-
gidmk.medium.com gidmk.medium.com
-
Gideon, M.-K. (2022, February 23). Has Covid-19 Been Worse Than the 1918 Influenza Pandemic? Medium. https://gidmk.medium.com/has-covid-19-been-worse-than-the-1918-influenza-pandemic-1c3362f01bcc
-
-
www.bps.org.uk www.bps.org.uk
-
Decision-making in uncertainty | BPS. (n.d.). Retrieved November 22, 2021, from https://www.bps.org.uk/events/decision-making-uncertainty
-
-
www.sciencedirect.com www.sciencedirect.com
-
Weiss, D. J., & Shanteau, J. (2021). The futility of decision making research. Studies in History and Philosophy of Science Part A, 90, 10–14. https://doi.org/10.1016/j.shpsa.2021.08.018
-
-
psychclassics.yorku.ca psychclassics.yorku.ca
-
When the hen sees a white oval object on the ground, she cannot leave it; she must keep upon it and return to it, until at last its transformation into a little mass of moving chirping down elicits from her machinery an entirely new set of performances. The love of man for woman, or of the human mother for her babe, our wrath at snakes and our fear of precipices, may all be described similarly, as instances of the way in which peculiarly conformed pieces of the world's furniture will fatally call forth most particular mental and bodily reactions, in advance of, and often in direct opposition to, the verdict of our deliberate reason concerning them. The labours of Darwin and his successors are only just beginning to reveal the universal parasitism of each creature upon other special things, [p.191] and the way in which each creature brings the signature of its special relations stampted on its nervous system with it upon the scene. Every living creature is in fact a sort of lock, whose wards and springs presuppose special forms of key, - which keys however are not born attached to the locks, but are sure to be found in the world near by as life goes on. And the locks are indifferent to any but their own keys. The egg fails to fascinate the hound, the bird does not fear the precipice, the snake waxes not wroth at his kind, the deer cares nothing for the woman or the human babe. Those who wish for a full development of this point of view, should read Schneider's Der thierische Wille, - no other book shows how accurately anticipatory are the actions of animals, of the specific features of the environment in which they are to live.
Discusses how animals' special reactions are to their own type of animal or even offspring. A chicken doesnt look for the sent of a dog as a dog would not harbor a chicken egg.
-
-
www.youtube.com www.youtube.com
-
If I'm not mistaken, this is the original song which C.J. Craig sings a portion of in the Red Haven's on Fire episode of The West Wing. https://www.imdb.com/title/tt0745672
Tags
Annotators
URL
-
-
chem.libretexts.org chem.libretexts.org
-
Now if you think about it, the cation repels the positive end of the dipole and attracts the negative end, so the negative end is closer to the cation than the positive end. This means the attractive energies are greater than the repulsive (as they are closer together, the r of coulombs law is in the denominator of eq. So the net force is attractive since since the radius (in the denominator of Coulombs Law, Equation 11.2.111.2.1\ref{11.2.1}) for the +/- attraction is smaller than the radius for the +/+ repulsion. This difference is greatest when the polar molecule is "touching" the cation, and as they become further separated the relative differences in the radii between the two interactions become less, and at great distances they become equal, making these short range forces. This can be understood by looking at
Negative end of dipole closer to cation than positive end. Greatest difference is when the cation is “touching” cation, and the interactions become less as they get further apart-however at great distances they become equal which makes them short range forces.
-
-
www.bundleiq.com www.bundleiq.com
-
https://www.bundleiq.com/post/the-history-of-pkm
I positively don't recommend this article... good example of someone "trying on" information they've been reading about, but haven't quite mastered or gone deep enough on yet. Also potentially a good example of the sort of issues that can be seen when learning in public and potentially attempting to be an influencer in a space in which one is not an expert.
-
-
-
The sheet box
Interesting choice of translation for "Die Kartei" by the translator. Some may have preferred the more direct "file".
Historically for this specific time period, while index cards were becoming more ubiquitous, most of the prior century researchers had been using larger sheets and frequently called them either slips or sheets based on their relative size.
Beatrice Webb in 1926 (in English) described her method and variously used the words “cards”, “slips”, “quarto”, and “sheets” to describe notes. Her preference was for quarto pages which were larger pages which were likely closer to our current 8.5 x 11” standard than they were to even larger index cards (like 4 x 6".
While I have some dissonance, this translation makes a lot of sense for the specific time period. I also tend to translate the contemporaneous French word “fiches” of that era as “sheets”.
See also: https://hypothes.is/a/OnCHRAexEe2MotOW5cjfwg https://hypothes.is/a/fb-5Ngn4Ee2uKUOwWugMGQ
-
-
Local file Local file
-
Phenomena can be so familiar that wereally do not see them at all, a matter that has been much discussed by literarytheorists and philosophers. For example, Viktor Shklovskij in the early 1920sdeveloped the idea that the function of poetic art is that of “making strange”the object depicted. “People living at the seashore grow so accustomed to themurmur of the waves that they never hear it. By the same token, we scarcelyever hear the words which we utter . . . We look at each other, but we do not seeeach other any more. Our perception of the world has withered away; what hasremained is mere recognition.”
Fish in water effect
-
Contemporary scholarship is not in a position to give a definitive assessmentof the achievements of philosophical grammar. The ground-work has not beenlaid for such an assessment, the original work is all but unknown in itself, andmuch of it is almost unobtainable. For example, I have been unable to locate asingle copy, in the United States, of the only critical edition of the Port-RoyalGrammar, produced over a century ago; and although the French original isnow once again available, 3 the one English translation of this important workis apparently to be found only in the British Museum. It is a pity that this workshould have been so totally disregarded, since what little is known about it isintriguing and quite illuminating.
He's railing against the loss of theory for use over time and translation.
similar to me and note taking...
-
-
docs.gitlab.com docs.gitlab.com
-
Epics, issues, requirements, and others all have similar but just subtle enough differences in common interactions that the user needs to hold a complicated mental model of how they each behave.
-
-
www.nature.com www.nature.com
-
Needles (~2 nm in width and ~10 nm in length, Supplementary Figs. 4 and 5) were observed at the tip of some platelets, which confirms previous observations2,12 and supports the hypothesis that the HAp platelets evolve from needle-like crystals.
needle
-
-
theamericanscholar.org theamericanscholar.org
-
threadreaderapp.com threadreaderapp.com
-
The real issue with "learning in public" is them emphasis placed on "being an expert," which is *everywhere*. It's a capitalist mindset, convincing people that even as beginners they should consider themselves "experts" bc this is how you get exposure aka how u scale.
The public online commons, by means of context collapse, allows people to present themselves as experts within an area without actually being experts.
Some of these "experts" or "gurus" primarily have expertise in communication or promoting themselves or a small piece of a topic about which they know a little more than the average public.
-
-
-
jimmyhmiller.github.io jimmyhmiller.github.io
-
Most notably missing from the discussion is inheritance.
Nah. OOP is just "messaging, local retention and protection and hiding of state-process, and extreme late-binding of all things". Inheritance not needed.
-
-
secondstaxcom.sharepoint.com secondstaxcom.sharepoint.com
-
Complete all personal inform
-
-
scholarworks.wmich.edu scholarworks.wmich.edu
-
Why won't annotators use the "Page Notes"?
-
-
www.dasp.co www.dasp.co
-
It was first unveiled during a multimillion dollar heist which led to a hard fork of Ethereum. Reentrancy occurs when external contract calls are allowed to make new calls to the calling contract before the initial execution is complete.
Reenter attack - The DAO. Basically withdrawal calls before the end of initial execution.
-
-
link.springer.com link.springer.com
-
“on a decadal time scale, wecannot rely on software to run repeatably.
See also: Fielding
-
-
a16zcrypto.com a16zcrypto.com
-
But permissionless voting is vulnerable to governance attacks,
protocol complian attacks that can be mitigated through mechanism design
-
-
www.tandfonline.com www.tandfonline.com
-
The potential for digital technology to support learners in this process was highlighted in the studies reviewed, but commonly learners lacked the competence to use digital technologies for educational purposes. Learners often required support, especially with the planning and reviewing aspects of self-directed learning, as well as guidance regarding how digital technologies can be used effectively for educational purposes. Importantly, studies that focus on understanding the facilitation of self-directed learning in childhood education are seldom. Further studies on self-directed learning in childhood education are vital – given that this is a fundamental competence for preparing our youth to deal with work and life in our rapidly changing world.
Learners often required support, especially with the planning and reviewing aspects of self-directed learning, as well as guidance regarding how digital technologies can be used effectively for educational purposes. Importantly, studies that ..
-
-
link.springer.com link.springer.com
-
focused on the language that the children used when they were involved in a design and technology activity
Children’s Use of Technology in Learning
-
-
stackoverflow.com stackoverflow.com
-
When we have our git rev-parse examine our Git repository to view our origin/HEAD, what we see is whatever we have stored in this origin/HEAD. That need not match what is in their HEAD at this time. It might match! It might not.
-
- Jul 2022
-
www.liberation.fr www.liberation.fr
-
In 90 und damit in fast allen französischen Departements herrscht Wassermangel, sodass der Wasserverbrauch mehr oder weniger stark von den Präfekten reguliert wird. Die Trockenheit begünstigt nicht nur Waldbrände. Sie verringert die Erträge der Landwirtschaft, und erschwert zunehmend auch die Binnenschifffahrt.
-
-
www.windley.com www.windley.com
-
I didn't start out in 2007 to write a programming language that naturally supports decentralized programming using the actor-model while being cloud-native, serverless, and databaseless. Indeed, if I had, I likely wouldn't have succeeded. Instead picos evolved from a simple rule language for modifying web pages to a powerful, general-purpose programming system for building any decentralized application.
Lots of concepts ping like hail on a car hood for me. I don't really understand them but they resonate: decentralized programming, cloud-native, serverless, databaseless. It all seems like fungi in nature or the apricot you mention in an earlier post. I especially like the idea of learning systems "evolving from a simple rule language". Yes, I want to evolve and roll my own learning system then I want to teach others how to do it.
-
-
www.evernote.com www.evernote.com
-
SEO Services Company in India – Contributing to the Growth of Your Business
In the digital workspace, SEO Services Company in India is crucial for businesses of all sizes and kinds. From business growth to long-term success and higher ROI, these services play a key role for any business.
-
-
gist.github.com gist.github.com
-
4.5 Getting the right people in the right roles in support of your goal is the key to succeeding at whatever you choose to accomplish.
4.5 Getting the right people in the right roles in support of your goal is the key to succeeding at whatever you choose to accomplish.
-
-
github.com github.com
-
Interestingly, Rails doesn't see this in their test suite because they set this value during setup:
-
-
docdrop.org docdrop.org
-
let me comment on your quantum physics i have only one objection please i think it's uh uh it's 01:01:21 what you said about the two uh sort of prototypical uh quantum puzzles which is schrodinger the double slit experiment uh it's uh it's perfect um my only objection is that in my book 01:01:34 i described of course i had a chapter about schrodinger cat but i don't use a situation in which the cat is dead or alive 01:01:46 i prefer a situation in which the cat is asleep or awake just because i don't like killing cats even in in in in mental experiments so after that 01:01:58 uh uh replacing a sleep cut with a dead cat i think uh i i i i completely agree and let me come to the the serious part of the answer um 01:02:10 what you mentioned as the passage from uh the third and the fourth um between among the the sort of the versions of 01:02:25 wooden philosophy it's it's exactly what i what i think is relevant for quantum mechanics for this for the following reason we read in quantum mechanics books 01:02:37 that um we should not think about the mechanical description of reality but the description reality with respect to the observer and there is always this notion in in books that there's observer or there are 01:02:50 paratus that measure so it's a uh but i am a scientist which view the world from the perspective of 01:03:02 modern science where one way of viewing the world is that uh there are uh you know uh billions and billions of galaxies each one with billions and billions of 01:03:14 of of of stars probably with planets all around and uh um from that perspective the observer in any quantum mechanical experiment is just one piece in the big story 01:03:28 so i have found the uh berkeley subjective idealism um uh profoundly unconvincing from the point 01:03:39 of view of a scientist uh because it there is an aspect of naturalism which uh it's a in which i i i grew up as a scientist 01:03:52 which refuses to say that to understand quantum mechanics we have to bring in our mind quantum mechanics is not something that has directly to do with our mind has not 01:04:05 something directly to do about any observer any apparatus because we use quantum mechanics for describing uh what happened inside the sun the the the reaction the nuclear reaction there or 01:04:18 galaxy formations so i think quantum mechanics in a way i think quantum mechanics is experiments about not about psychology not about our mind not about consciousness not 01:04:32 about anything like that it has to do about the world my question what we mean by real world that's fine because science repeatedly was forced to change its own ideas about the 01:04:46 real world so if uh if to make sense of quantum mechanics i have to think that the cat is awake or asleep only when a conscious observer our mind 01:05:00 interacts with this uh i say no that's not there are interpretations of quantum mechanics that go in that direction they require either am i correct to say the copenhagen 01:05:14 school does copenhagen school uh talk about the observer without saying who is what is observed but the compelling school which is the way most 01:05:27 textbooks are written uh describe any quantum mechanical situation in terms okay there is an observer making a measurement and we're talking about the outcome of the measurements 01:05:39 so yes it's uh it assumes an observer but it's very vague about what what an observer is some more sharp interpretation like cubism uh take this notion observer to be real 01:05:54 fundamental it's an agent somebody who makes who thinks about and can compute the future so it's a it's a that's that's a starting point for for doing uh for doing the rest i was 01:06:07 i've always been unhappy with that because things happen on the sun when there is nobody that is an observer in anything and i want to think to have a way of thinking in the world that things happen there 01:06:20 independently of me so to say is they might depend on one another but why should they depend on me and who am i or you know what observers should be a you know a white western scientist with 01:06:32 a phd i mean should we include women should we include people without phd should we include cats is the cat an observer should we fly i mean it's just not something i understand
Carlo goes on to address the fundamental question which lay at the intersection of quantum mechanics and Buddhist philosophy: If a tree falls in the forest, does anybody hear? Carlo rejects Berkeley's idealism and states that even quantum mechanical laws are about the behavior of a system, independent of whether an observer is present. He begins to invoke his version of the Schrödinger cat paraodox to explain.
-
-
www.judithragir.org www.judithragir.org
-
When we see the world from the vantage point of all-at-oneness, always right here, we can be said to be like a pearl in a bowl. Flowing with every turn without any obstructions or stoppages coming from our emotional reactions to different situations. This is a very commonly used image in Zen — moving like a pearl in a bowl. As usual, our ancestors comment on this phrase, wanting to break open our solidifying minds even more. Working from Dogen’s fascicle Shunju, Spring and Autumn, we have an example of opening up even the Zen appropriate phrase — a pearl in a bowl. Editor of the Blue Cliff Record Engo ( Yuan Wu) wrote: A bowl rolls around a pearl, and the pearl rolls around the bowl. The absolute in the relative and the relative in the absolute. Dogen: The present expression “a bowl rolls around a pearl” is unprecedented and inimitable, it has rarely been heard in eternity. Hitherto, people have spoken only as if the pearl rolling in the bowl were ceaseless.
This is like the observation I often make in Deep Humanity and which is a pith BEing Journey
When we move is it I who goes from HERE to THERE? Or am I stationary, like the eye of the hurricane spinning the wild world of appearances to me and surrounding me?
I am like the gerbil running on a cage spinning appearances towards me but never moving an inch I move while I am still The bowl revolves around this pearl.
-
The absolute in the relative and the relative in the absolute
Title: The absolute in the relative and the relative in the absolute Author: Judith Ragir Date: ?
-
-
Local file Local file
-
NOTES AND REFERENCES
Dear god I really hate when publishers do their references/notes like this. Sitting here at the end, unlinked to the actual text. There's a special place in hell for editors that do this in the digital age.
-
-
www.contrastsecurity.com www.contrastsecurity.com
-
What is Open source security?
-
-
www.google.com www.google.com
-
Open Source Advantages and Risk Profile · 96% of applications include some form of OSS · 67% of applications contain open source vulnerabilities · 90% of software ...
-
-
www.infoq.com www.infoq.com
-
Learn how to detect vulnerable open source components and keep your products secure.
-
-
securitytoday.com securitytoday.com
-
The Dangers of Open-Source Vulnerabilities, and What You Can Do About It
-
- Jun 2022
-
comparewords.com comparewords.com
-
(2) The influence of the various concepts for the induction of lateral structure formation in lipid membranes on integral functional units like ionophores is demonstrated by analysing the single channel current fluctuations of gramicidin in bimolecular lipid membranes.
-
-
www.kcet.org www.kcet.org
-
Lois Weber<br /> - First woman accepted to Motion Picture Director's Association, precursor of Director's Guild<br /> - First directors committee of the Academy of Motion Picture Arts and Sciences<br /> - Mayor of Universal City<br /> - One of the highest paid and most influential directors in Hollywood of her day<br /> - one of first directors to form her own production company
See also: - https://en.wikipedia.org/wiki/Lois_Weber
-
-
Local file Local file
-
The Essential Habits ofDigital Organizers
This chapter is too entailed with productivity advice, which can be useful to some, but isn't as note taking focused for those who probably need more of that.
What is the differentiator between knowledge workers, knowledge creators, students, researchers, academics. How do we even clearly delineate knowledge worker as a concept. It feels far too nebulous which makes it more difficult to differentiate systems for them to use for improving productivity and efficiency.
-
send off your draft or beta orproposal for feedback. Share this Intermediate Packet with a friend,family member, colleague, or collaborator; tell them that it’s still awork-in-process and ask them to send you their thoughts on it. Thenext time you sit down to work on it again, you’ll have their input andsuggestions to add to the mix of material you’re working with.
A major benefit of working in public is that it invites immediate feedback (hopefully positive, constructive criticism) from anyone who might be reading it including pre-built audiences, whether this is through social media or in a classroom setting utilizing discussion or social annotation methods.
This feedback along the way may help to further find flaws in arguments, additional examples of patterns, or links to ideas one may not have considered by themselves.
Sadly, depending on your reader's context and understanding of your work, there are the attendant dangers of context collapse which may provide or elicit the wrong sorts of feedback, not to mention general abuse.
-
If we overlay the four steps of CODE onto the model ofdivergence and convergence, we arrive at a powerful template forthe creative process in our time.
The way that Tiago Forte overlaps the idea of C.O.D.E. (capture/collect, organize, distill, express) with the divergence/convergence model points out some primary differences of his system and that of some of the more refined methods of maintaining a zettelkasten.
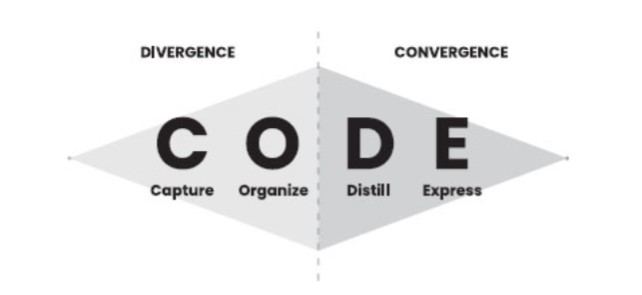 <small>Overlapping ideas of C.O.D.E. and divergence/convergence from Tiago Forte's book Building a Second Brain (Atria Books, 2022) </small>
<small>Overlapping ideas of C.O.D.E. and divergence/convergence from Tiago Forte's book Building a Second Brain (Atria Books, 2022) </small>Forte's focus on organizing is dedicated solely on to putting things into folders, which is a light touch way of indexing them. However it only indexes them on one axis—that of the folder into which they're being placed. This precludes them from being indexed on a variety of other axes from the start to other places where they might also be used in the future. His method requires more additional work and effort to revisit and re-arrange (move them into other folders) or index them later.
Most historical commonplacing and zettelkasten techniques place a heavier emphasis on indexing pieces as they're collected.
Commonplacing creates more work on the user between organizing and distilling because they're more dependent on their memory of the user or depending on the regular re-reading and revisiting of pieces one may have a memory of existence. Most commonplacing methods (particularly the older historic forms of collecting and excerpting sententiae) also doesn't focus or rely on one writing out their own ideas in larger form as one goes along, so generally here there is a larger amount of work at the expression stage.
Zettelkasten techniques as imagined by Luhmann and Ahrens smooth the process between organization and distillation by creating tacit links between ideas. This additional piece of the process makes distillation far easier because the linking work has been done along the way, so one only need edit out ideas that don't add to the overall argument or piece. All that remains is light editing.
Ahrens' instantiation of the method also focuses on writing out and summarizing other's ideas in one's own words for later convenient reuse. This idea is also seen in Bruce Ballenger's The Curious Researcher as a means of both sensemaking and reuse, though none of the organizational indexing or idea linking seem to be found there.
This also fits into the diamond shape that Forte provides as the height along the vertical can stand in as a proxy for the equivalent amount of work that is required during the overall process.
This shape could be reframed for a refined zettelkasten method as an indication of work
Forte's diamond shape provided gives a visual representation of the overall process of the divergence and convergence.
But what if we change that shape to indicate the amount of work that is required along the steps of the process?!
Here, we might expect the diamond to relatively accurately reflect the amounts of work along the path.
If this is the case, then what might the relative workload look like for a refined zettelkasten? First we'll need to move the express portion between capture and organize where it more naturally sits, at least in Ahren's instantiation of the method. While this does take a discrete small amount of work and time for the note taker, it pays off in the long run as one intends from the start to reuse this work. It also pays further dividends as it dramatically increases one's understanding of the material that is being collected, particularly when conjoined to the organization portion which actively links this knowledge into one's broader world view based on their notes. For the moment, we'll neglect the benefits of comparison of conjoined ideas which may reveal flaws in our thinking and reasoning or the benefits of new questions and ideas which may arise from this juxtaposition.
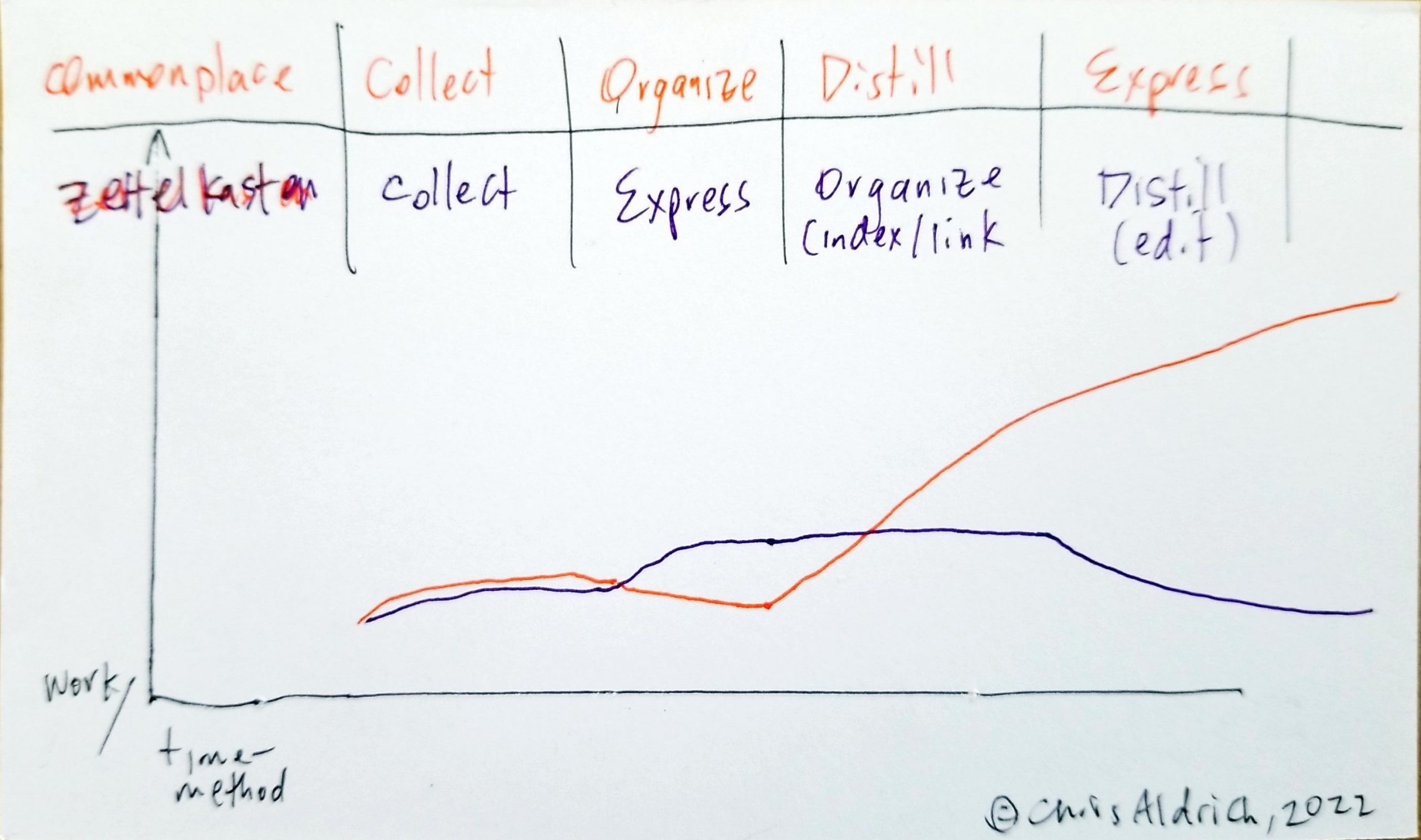
This sketch could be refined a bit, but overall it shows that frontloading the work has the effect of dramatically increasing the efficiency and productivity for a particular piece of work.
Note that when compounded over a lifetime's work, this diagram also neglects the productivity increase over being able to revisit old work and re-using it for multiple different types of work or projects where there is potential overlap, not to mention the combinatorial possibilities.
--
It could be useful to better and more carefully plot out the amounts of time, work/effort for these methods (based on practical experience) and then regraph the resulting power inputs against each other to come up with a better picture of the efficiency gains.
Is some of the reason that people are against zettelkasten methods that they don't see the immediate gains in return for the upfront work, and thus abandon the process? Is this a form of misinterpreted-effort hypothesis at work? It can also be compounded at not being able to see the compounding effects of the upfront work.
What does research indicate about how people are able to predict compounding effects over time in areas like money/finance? What might this indicate here? Humans definitely have issues seeing and reacting to probabilities in this same manner, so one might expect the same intellectual blindness based on system 1 vs. system 2.
Given that indexing things, especially digitally, requires so little work and effort upfront, it should be done at the time of collection.
I'll admit that it only took a moment to read this highlighted sentence and look at the related diagram, but the amount of material I was able to draw out of it by reframing it, thinking about it, having my own thoughts and ideas against it, and then innovating based upon it was incredibly fruitful in terms of better differentiating amongst a variety of note taking and sense making frameworks.
For me, this is a great example of what reading with a pen in hand, rephrasing, extending, and linking to other ideas can accomplish.
-
We’ve been taught that it’s important to work “with the end inmind.” We are told that it is our responsibility to deliver outcomes,whether that is a finished product on store shelves, a speechdelivered at an event, or a published technical document.
Example of someone else saying this...
We focus too much on the achievement and the end goal and the work and process doesn't receive its due.
Tags
- zettelkasten
- criticism
- work with the end in mind
- compounding value
- constructive criticism
- project management
- putting in the work
- idea links
- context collapse
- feedback loops
- commonplace books
- organization
- writing advice
- combinatorial creativity
- feedback
- knowledge creators
- visualizations
- working in public
- goals
- behavioral economics
- innovation
- imitation for innovation
- cognitive bias
- knowledge work
- commonplace books vs. zettelkasten
- writing
- writing process
- efficiency
- social media
- Tiago Forte
- knowledge workers
- note taking
- work
- year in reviews
- time
- writing for understanding
- C.O.D.E.
- productivity fallacy
- social annotation
- divergence/convergence
- misinterpreted-effort hypothesis
- trolling
- productivity
- processes
- reviews
Annotators
-
-
hybridpedagogy.org hybridpedagogy.org
-
For Jerome Bruner, the place to begin is clear: “One starts somewhere—where the learner is.”
One starts education with where the student is. But mustn't we also inventory what tools and attitudes the student brings? What tools beyond basic literacy do they have? (Usually we presume literacy, but rarely go beyond this and the lack of literacy is too often viewed as failure, particularly as students get older.) Do they have motion, orality, song, visualization, memory? How can we focus on also utilizing these tools and modalities for learning.
Link to the idea that Donald Trump, a person who managed to function as a business owner and president of the United States, was less than literate, yet still managed to function in modern life as an example. In fact, perhaps his focus on oral modes of communication, and the blurrable lines in oral communicative meaning (see [[technobabble]]) was a major strength in his communication style as a means of rising to power?
Just as the populace has lost non-literacy based learning and teaching techniques so that we now consider the illiterate dumb, stupid, or lesser than, Western culture has done this en masse for entire populations and cultures.
Even well-meaning educators in the edtech space that are trying to now center care and well-being are completely missing this piece of the picture. There are much older and specifically non-literate teaching methods that we have lost in our educational toolbelts that would seem wholly odd and out of place in a modern college classroom. How can we center these "missing tools" as educational technology in a modern age? How might we frame Indigenous pedagogical methods as part of the emerging third archive?
Link to: - educational article by Tyson Yunkaporta about medical school songlines - Scott Young article "You should pay for Tutors"
aside on serendipity
As I was writing this note I had a toaster pop up notification in my email client with the arrival of an email by Scott Young with the title "You should pay for Tutors" which prompted me to add a link to this note. It reminds me of a related idea that Indigenous cultures likely used information and knowledge transfer as a means of payment (Lynne Kelly, Knowledge and Power). I have commented previously on the serendipity of things like auto correct or sparks of ideas while reading as a means of interlinking knowledge, but I don't recall experiencing this sort of serendipity leading to combinatorial creativity as a means of linking ideas,
-
Maxine Greene for example, begins by writing that “We are convinced that the movement towards educational technology is irreversible and that our obligation as educators is to learn how to deal with it,” but then she turns that resignation into resistance by adding, “how, if you like, to live with it as fully conscious human beings working to enable other human beings to become conscious, to become responsible, to learn.”
If it's true that the movement toward technology is inevitable, how might we deal with it?
Compare this with the solution(s) that nomadic hunter-gatherers had to face when changing from a lifestyle built on movement to one of settling down to a life of agriculture. Instead of attaching their knowledge and memories to their landscape as before, they built structures (like Stonehenge) to form these functions.
Part of moving forward may involve moving back historically to better understand these ideas and methods and regaining them so that we might then reattach them to a digital substrate. How can we leverage the modalities of the digital for art, song, dance, music, and even the voice into digital spaces (if we must?). All digital or only digital certainly isn't the encompassing answer, but if we're going to do it, why not leverage the ability to do this?
As an example, Hypothes.is allows for annotating text to insert photos, emoji, audio (for music and voice), and even video. Videos might include dance and movement related cues that students might recreate physically. These could all be parts of creating digital songlines through digital spaces that students can more easily retrace to store their learnings for easier recall and to build upon in the future.
Tags
- orality
- educational tools
- arts in education
- orality vs. literacy
- Indigenous pedagogy
- attitudes
- location
- EdTech
- idea links
- movement
- literacy isn't everything
- indigenous knowledge
- combinatorial creativity
- Tyson Yunkaporta
- Jerome Bruner
- technobabble
- linguistics
- third archive
- toaster notifications
- educational substrates
- where
- pedagogy
- Donald J. Trump
- modality shifts
- mnemonic media
- inventories
- information as currency
- tutors
- quotes
- Indigenous knowledge as educational technology
Annotators
URL
-
-
effectiviology.com effectiviology.com
-
Interleaving is a learning technique that involves mixing together different topics or forms of practice, in order to facilitate learning. For example, if a student uses interleaving while preparing for an exam, they can mix up different types of questions, rather than study only one type of question at a time.Interleaving, which is sometimes referred to as mixed practice or varied practice, is contrasted with blocked practice (sometimes referred to as specific practice), which involves focusing on only a single topic or form of practice at a time.
Interleaving (aka mixed practice or varied practice) is a learning strategy that involves mixing different topics, ideas, or forms of practice to improve outcomes as well as overall productivity. Its opposite and less effective strategy is blocking (or block study or specific practice) which focuses instead on working on limited topics or single forms of practice at the same time.
This may be one of the values of of the Say Something In Welsh method which interleaves various new nouns and verbs as well as verb tenses in focused practice.
Compare this with the block form which would instead focus on lists of nouns in a single session and then at a later time lists of verbs in a more rote fashion. Integrating things together in a broader variety requires more work, but is also much more productive in the long run.
-
-
bulletproofmusician.com bulletproofmusician.com
-
the more effort they had to put into the study strategy, the less they felt they were learning.
misinterpreted-effort hypothesis: the amount of effort one puts into studying is inversely proportional to how much one feels they learn.
Is this why the Says Something In Welsh system works so well? Because it requires so much mental work and effort in short spans of time? Particularly in relation to Duolingo which seems easier?
-
-
www.reddit.com www.reddit.com
-
Ps) I am trying to post daily content like this on LinkedIn using my Slip-Box as the content generator (the same is posted on Twitter, but LinkedIn is easier to read), so if you want to see more like this, feel free to look me up on LinkedIn or Twitter.
Explicit example of someone using a zettelkasten to develop ideas and create content for distribution online and within social media.
https://www.reddit.com/r/antinet/comments/vgtyuf/mastery_requires_theory_application_of_theory_is/
-
-
danallosso.substack.com danallosso.substack.com
-
grandfathered in
@danallosso, this phrase has a problematic historical past... https://www.npr.org/sections/codeswitch/2013/10/21/239081586/the-racial-history-of-the-grandfather-clause
-
-
www.sas.ac.uk www.sas.ac.uk
-
Archaeology of Reading project
https://archaeologyofreading.org/
The Archaeology of Reading in Early Modern Europe (AOR) uses digital technologies to enable the systematic exploration of the historical reading practices of Renaissance scholars nearly 450 years ago. This is possible through AOR’s corpus of thirty-six fully digitized and searchable versions of early printed books filled with tens of thousands of handwritten notes, left by two of the most dedicated readers of the early modern period: John Dee and Gabriel Harvey.
Perhaps some overlap here with: - Workshop in the History of Material Texts https://pennmaterialtexts.org/about/events/ - Book Traces https://booktraces.org via Andrew Stauffer, et al. - Schoenberg Institute's Coffe with a Codex https://schoenberginstitute.org/coffee-with-a-codex/ (perhaps to a lesser degree)
-
-
-
you label boxes so you knowwhat’s in them; you arrange your clothes according to color. Eventually you reach apoint where you look around and you’re satisfied. There are no loose ends.Everything is in its place, put away or accounted for or easily accessed. The roomexudes order and harmony. When you look around, you’re happy.
Interlinking your ideas can help to create a harmony within your collection. There are no loose ends or lost ideas. There is a place for everything and everything is in its proper place, ready to be used and reused.
-
-
-
we see by learning to see. The brain evolved the mechanisms for finding patterns, finding relationships in information, 00:04:38 and associating those relationships with a behavioral meaning, a significance, by interacting with the world. We're very aware of this in the form of more cognitive attributes, like language. I'm going to give you some letter strings, and I want you to read them out for me, if you can. Audience: "Can you read this?" "You are not reading this." "What are you reading?" Beau Lotto: "What are you reading?" Half the letters are missing, right? 00:05:04 There's no a priori reason why an "H" has to go between that "W" and "A." But you put one there. Why? Because in the statistics of your past experience, it would have been useful to do so. So you do so again. And yet you don't put a letter after that first "T." Why? Because it wouldn't have been useful in the past. So you don't do it again.
Being journey 3 Linguistic BEing journey - filling in missing letters in incomplete sentence is based on our past experience with specific sentences that have those letters. This becomes compelling when we can demonstrate with multiple languages, including ones we are not familiar with. Those people in the other cultures will fill in missing letters in their words in their language that we would be completely clueless about.
-
-
www.cbc.ca www.cbc.ca
-
-
why is the moment you ask someone is a woman as electable as a man how come the moment you ask that everything changes yeah this is this was one of those really remarkable we didn't do this 00:21:01 research so i can brag about it right right it's regina bateson this is really fantastic research looking at gender bias in politics right because it's unbelievable 00:21:14 like women are so underrepresented in intellectual politics it's just you can't it's but like here's the thing like it's important to understand what's driving that and and for sure let's just be clear just straight up sexism 00:21:27 certainly is involved sometimes like that that's certainly the case but what what uh dr bateson found what i think was really fascinating is that given our winner-take-all um like sort of two-party system 00:21:41 so much is dependent on what the gatekeepers think who who because now like if we were doing something like ranked choice voting it doesn't really matter i don't have to care what i think anybody else thinks right but in a winner-take-all system i 00:21:54 have to do a little bit of guessing about who do i think most people are going to vote for right because otherwise my vote is quote unquote wasted right if i take a flyer on that so what was interesting is if you look at how women perform when they are 00:22:08 nominated in general elections women win at the same rate as white men it's just so i suggest obviously it's not a general election problem and what what she found was that it was like 00:22:20 party leaders especially donors right they're like well wait a minute i'm not sexist but i think most people in the party are so i don't think you're going to be able to win and so they don't get the support they don't get the the 00:22:32 resources and it becomes self-fulfilling it's so clear when you put it that way how that becomes a self-fulfilling prophecy but there there is so much pressure within certain groups to say this the the dominant ideology and just 00:22:44 like don't like if you can't it's like a cult right because like the second you question maybe you're like what does the evidence actually show they're like you're out you're not being loyal um wow 00:22:57 yeah so that's it's actually um in the book i i was looking at what i call these conformity traps like these these three kinds of situations where you are likely to slip into blind conformity and you are quite likely to do that 00:23:10 under an illusion to begin with and you know this this sort of identity trap where you've got these groups that matter so much to who you are right and and especially when it's just one group that group has cult-like power 00:23:23 over you
In summary, women don't do well in politics (and probably business) due to a collective illusion effect of the gatekeepers who believe everyone else thinks that they are rocking the boat.
Groups can influence a cult like power on individual group members.
-
-
www.linkedin.com www.linkedin.com
-
Energy efficiency has never been more crucial! The time to unleashing its massive potential has come
Will this conference debate rebound effects of efficiency? If not, it will not have the desirable net effect.
My linked In comments were:
Alessandro Blasi, will this conference address the rebound effect? In particular, Brockway et al. have done a 2021 meta-analysis of 33 research papers on rebound effects of energy efficiency efforts and conclude:
"...economy-wide rebound effects may erode more than half of the expected energy savings from improved energy efficiency. We also find that many of the mechanisms driving rebound effects are overlooked by integrated assessment and global energy models. We therefore conclude that global energy scenarios may underestimate the future rate of growth of global energy demand."
https://www.sciencedirect.com/science/article/pii/S1364032121000769?via%3Dihub
Unless psychological and sociological interventions are applied along with energy efficiency to mitigate rebound effects, you will likely and ironically lose huge efficiencies in the entire efficiency intervention itself.
Also, as brought up by other commentators, there is a difference between efficiency and degrowth. Intelligent degrowth may work, especially applied to carbon intensive areas of the economy and can be offset by high growth in low carbon areas of the economy.
Vaclav Smil is pessimistic about a green energy revolution replacing fossil fuels https://www.ft.com/content/71072c77-53b3-4efd-92ae-c92dc02f09ad, which opens up the door to serious consideration of degrowth, not just efficiency improvements. Perhaps the answer is in a combination of all of the above, including targeted degrowth.
Technology moves quickly and unexpectedly. At the time of Smil's book release, there was no low carbon cement. Now there is a promising breakthrough: https://www.cnbc.com/2022/04/28/carbon-free-cement-breakthrough-dcvc-put-55-million-into-brimstone.html
As researchers around the globe work feverishly to make low carbon breakthroughs, there is obviously no guarantee of when they will occur. In that case then, with only a few years to peak, it would seem the lowest risk pathway would be to prioritize the precautionary principle over a gambling pathway (such as relying on Negative Emissions Technology breakthroughs) and perhaps consider along with rebound effect conditioned efficiency improvements also include a strategy of at least trialing a temporary, intentional degrowth of high carbon industries / growth of low carbon industries.
-
-
www.linkedin.com www.linkedin.com
-
Perhaps one of the most important questions to be asked is “What are we not ‘seeing’?.” … “A collaborative project of the late botanists Erwin Lichtenegger and Lore Kutschera celebrates the power and beauty of these otherwise hidden systems through detailed drawings of agricultural crops, shrubs, trees, and weeds. Digitized by the Wageningen University & Research, the extensive archive is the culmination of 40 years of research in Austria that involved cultivating and carefully retrieving developed plant life from the soil for study. It now boasts more than 1,000 renderings of the winding, spindly roots, some of which branch multiple feet wide.”
These drawings are metaphors for the human meaningverse of an individual and the visible and invisible aspects of our ideas that we present to the rest of the world.
What is of greatest meaning lives in the individual's salience landscape. That salience landscape is the result of a lifetime of sense-making - all the books we've ever read, talks or presentations we've ever listened to, conversations we've had, courses we've studied. While the other person may have an idea of what is important to us, they are clueless of how that salience landscape came to be.
This vast network of formative events is usually invisible to the OTHER.
The public, open source Indyweb that is currently being designed will allow the individual user for the first time to consolidate all his or her digital learning in one place, the user's owned Indyhub. Since Indyweb also has built-in provenance, it will allow traceability of public ideas. This allows the individual to keep track of what would otherwise by invisible and lost - the history of his/her social interaction with ideas.
-
-
www.linkedin.com www.linkedin.com
-
What can we do with a shift in thinking backed by a total of $3.6 trillion in funds under management? I’m backing strategic circular initiatives to convert the highest return on value for anyone’s money. Stay tuned as we crack open new investment opportunities.
Her diagram explicitly shows a synthesis of planetary boundaries and circular economy. This is a connection that many in this area are tacitly aware of but is good to explicate it in a diagram of this sort..
If circular economy is about ultimate reuse and recirculating material flows to eliminate the concept of waste, then how does energy consumption fit into the picture? Obviously, CO2 emissions is a form of material waste that is an undesirable byproduct of carbon-based energy usage. Capturing CO2 and reusing it is one method, but not a very scalable solution presently.
-
-
www.linkedin.com www.linkedin.com
-
What happens in Indonesia when a textile manufacturer illegally dumps dye waste!
This is an example of the manufacturer / consumer dualism created by the Industrial Revolution. Since manufacturers have become a separate layer that no longer exist as part of the community, as artisans once did, along with globalized capitalism, the consumer does not know the life history of the product being consumed. The sensory bubble limits what a consumer can directly know.
One answer is to promote a trend back to local and artisan production. Relocalizing production can empower consumers to inspect producers of the products they consume, holding them accountable.
Another answer is to develop globalized trust networks of producers who are truly ethical.
Cosmolocal production has networks by the commons nature can promote such values.
-
- May 2022
-
yishunlai.medium.com yishunlai.medium.com
-
Chris, this is a great take, thanks! Visiting the origins of the system doesn't fit into my current interests, but I'm very happy to know more about them.I gave a mini-lecture to my students last night about this system; really it's more about the idea of networking your ideas over anything else, isn't it? My students, who are all working on creative nonfiction projects, were so relieved to have someplace to put and process all the things they inevitably flag in the books they read.
I've been collecting some feedback on folks who've introduced this to students. I'm curious how your experiment ultimately went? Did they take to it? Do you feel like some are still using or even experimenting with the methods?
-
-
github.com github.com
-
We document the order of hooks, but I don't think we document where in that order we integrate Rails helpers which makes this confusing, I do sort of think this is a bug but as we use RSpec to integrate Rails here and RSpec Core has no distinction that matches before / after teardown its sort of luck of the draw, we could possibly use prepend_after for Rails integrations which would sort of emulate these options.
-
-
github.com github.com
-
I think RSpec should provide around(:context)/around(:all). Not because of any particular use case, but simply for API consistency. It's much simpler to tell users "there are 3 kinds of hooks (before, after and around) and each can be used with any of 3 scopes (example, context and suite)". Having some kinds of hooks work with only some kinds of scopes makes the API inconsistent and forces us to add special case code to emit warnings and also write extra documentation for this fact.
-
Now I'm puzzled by the apparently biggest obstacle to implementation of this feature: possible misuse. I love ruby community, but sometimes saving the dummies' asses goes a bit too far.
-
-
docdrop.org docdrop.org
-
the memory castle that jordan peter peterson described i think it has potentially a risk of inducing 00:58:28 confirmation bias
Jordan Peterson apparently has described using a memory palace (castle?) he used with 12 spaces for writing his book (presumably 12 Rules for life?).
-
-
pluralistic.net pluralistic.net
-
Frank Wilhot's: "Conservatism consists of exactly one proposition, to wit: There must be in-groups whom the law protects but does not bind, alongside out-groups whom the law binds but does not protect." https://crookedtimber.org/2018/03/21/liberals-against-progressives/
-
Libertarianism is notionally grounded in the idea of self-determination and personal responsibility, but in practice, powerful libertarians routinely trade off (others') freedom for (their own) tax savings.
An intriguing thesis.
Too often we trade away others' freedom(s) for small benefits to ourselves. This pattern has got to stop. The system should be closed in such a manner that the small trade-offs are balanced out across all of society.
Cory Doctorow also highlights the recent Texas abortion law which targets abortion providers. Rich Republicans who have backed this law will still have the power and flexibility to drive or fly to another state for their abortions when desired. There are no consequences for them because they're not in a closed system. If abortions were illegal everywhere and anyone getting one were to be prosecuted regardless of where they got their abortion, then the system would be more "closed" and without loopholes they could use. As a result, laws like this would never be passed because they would apply equally to those who were making them. Legislators and judges should think more about walking a mile (or a lifetime) in another person's shoes more often.
For lack of a better term let's use the idea of "political calculus" to describe this. Calculus is the mathematical study of small changes. So a small change to an individual isn't a big thing, but in the aggregate it can have profound and destructive effects on large swaths of the people.
In large part, this is how institutionalized and structural racism flourishes. We take small bites of powerless individuals which in aggregate causes far more harm.
This is all closely related to the idea of "privatizing profits and socializing losses".
-
-
www.nbcnews.com www.nbcnews.com
-
If you assume cops are basically good and just need help doing their job better, then body cameras make sense.
This is a deductive argument, but I believe theres no error in the way it's used
-
-
-
Because the geothermal fluid leaves the heat exchanger at 196F in the mixture cycle, it could be used in heat exchange with a second working fluid mixture to obtainadditional work. Thus, a cascade system of two or more binary cycles could be developed to increase thework obtainable per pound of geothermal fluid passing through the geothermal power plant.
-
a situation which should minimize irreversibilities in the condenser
-
The fact that the mixtureand the isobutane leave the turbine with 138 F and 167 Fsuper-
It doesn't from the figure that I left at either of those temperatures.
-
The geothermalfluid is considered to have the properties of supercooled liquidwater
-
On the other hand, an essentially infinitespectrum of property behavior characteristics exists for mixtures and thus a mixture can in principle befound which matches the resource characteristics better than virtually any possible pure-fluid choice
-
(a) Higher pressures can beused in the cycle, which increases the net cycle thermalefficienc
-
the working fluid in the power production cycle (e.g.Rankine-type cycle) receives energy by heat transfer with the geothermal fluid
-
-
hasura.io hasura.io
-
But in GraphQL, all types are nullable by default, and you opt into non-nullability
-
In other typed languages, like TypeScript, Flow, Rust, or Haskell, all types are non-nullable by default, and you opt into nullability.
-
-
Local file Local file
-
The second way that people use their Second Brain is to connectideas together. Their Second Brain evolves from being primarily amemory tool to becoming a thinking tool. A piece of advice from amentor comes in handy as they encounter a similar situation on adifferent team. An illuminating metaphor from a book finds its wayinto a presentation they’re delivering. The ideas they’ve capturedbegin gravitating toward each other and cross-pollinating.
Missing from this description is the work that is involved in revisting, re-reading, and interacting with your notes. This is not an easy process, but this paragraph belies the work involved and makes it seem "magical" with the use of the words 'illuminating', 'gravitating', 'cross-pollinating' which are all external processes or forces that don't require work from the individual.
Tags
Annotators
-
-
wordpress.com wordpress.com
-
"I'd want to learn a lot from Professor Zimmerman so that I may obtain as much information as possible and use it in reality. It's not about the work."
Tags
- The backdrop of this annotation is that it was a late-semester free writing for an essay brainstorm. In this piece of writing, I mentioned how I didn't know what to expect going into the project and wanted to learn as much as possible for my own betterment.
- (Shorter Piece) First two-sentences
Annotators
URL
-
-
wordpress.com wordpress.com
-
"I didn't fully understand it at the time, but throughout my time as a freshman at Boston College I've realized that I have the power to alter myself for the better and broaden my perspective on life. For most of my high school experience, I was holding to antiquated thoughts that had an impact on the majority of my daily interactions. Throughout my life, growing up as a single child has affected the way am in social interactions. This was evident in high school class discussions, as I did not yet have the confidence to be talkative and participate even up until the spring term of my senior year."
-
"Specifically, when one of my classmates stated how he was struggling with the concept and another one of my classmates took the initiative to clarify it, I realized that that individual possibilities vary greatly among students."
-
"The need to engage with people in terms of evaluating them for the aim of acquiring a different point of view was one occasion this semester where the knowledge I received in class positively changed the way I approached an issue. I was patient enough to explore other perspectives, some of which disagreed with mine, so that I might learn about their opinions without bias or prejudice."
Tags
- (Major Essay) Introduction paragraph
- In my annotation, I addressed the problem of not stating how and why this circumstance benefits me in the future. In the annotation, I continued to describe how hearing other people's ideas and responding to their comments and insights during class discussions will aid me in my career aspirations.
- (Major Essay) Climax paragraph. 3
- In this annotation, I choose to expand on my introduction. Before I explain why I chose the words I did, I should mention that my first draft failed to meet one of the assignment's primary requirements: a "Story like" structure. Finally, I decided to rework my introduction because my first draft did not begin with a clear beginning. Instead, I started by describing the fundamental context of the encounter before detailing my previous experiences. To improve my final edit, I made sure I described my experiences and/or how I felt before they occurred.
- Introduction p.1
- (Major Essay) Ending/Conclusion paragraph. 5
- This annotation consisted of me continuing to do what I've been doing, which is primarily adding more direct experiences. In my draft for this one, I outlined the scenario of the triangle theory, but I did not go into further detail. Therefore, I resolved to describe the actual circumstances in order to offer the readers a better insight into the experience.
Annotators
URL
-
-
forum.artofmemory.com forum.artofmemory.com
-
https://forum.artofmemory.com/t/what-language-s-are-you-studying/73190
I've been studying Welsh on and off now for just over a year.
I've been using a mix of Duolingo for it's easy user interface and it's built in spaced repetition. I like the way that it integrates vocabulary and grammar in a holistic way which focuses on both reading, writing, and listening.
However, I've also been using the fantastic platform Say Something in Welsh. This uses an older method of listening and producing based teaching which actually makes my brain feel a bit tired after practice. The focus here is solely on listening and speaking and forces the student to verbally produce the language. It's a dramatically different formula than most high school and college based courses I've seen and used over the years having taken 3 years of Spanish, 2 of French, and 2 of Latin.
The set up consists of the introduction of a few words which are then used in a variety of combinations to create full sentences. The instructors say a sentence in English and the listener is encouraged in just a few seconds to attempt to produce it in the target language (Welsh, in my case), then the instructor says the sentence in Welsh with a pause for the student to repeat it properly, another instructor says it in Welsh with a pause for a third repeat. This goes on for 20 to 30 minutes at a time. The end result is that the learner gets into the language much more quickly and can begin both understanding the spoken language as well as produce it much more rapidly than older school based methods (at least in my experience, though I have known some college language labs to use a much more limited version of a similar technique). Each lesson adds new material, but also reviews over older material in a spaced repetition format as well so you're always getting something new mixed in with the old to make new and interesting sentences for conversation.
SSiW also has modules for Manx, Cornish, Dutch, and Spanish.
I find that the two done hand in hand has helped me produce much faster results in language acquisition in an immersive manner than I have done previously and with much less effort.
-
-
datatracker.ietf.org datatracker.ietf.org
-
www.pathlms.com www.pathlms.com
-
www.alastore.ala.org www.alastore.ala.org
- Apr 2022
-
-
The lateral keyword allows us to access columns after the FROM statement, and reference these columns "earlier" in the query ("earlier" meaning "written higher in the query").
-
-
cagrimmett.com cagrimmett.com
-
Why public? There is something about making your posts available to the rest of the world that holds your feet to the fire and makes you commit. I’ve tried dozens of times to keep a private ongoing digital notebook in Evernote, Devonthink, Roam, and Obsidian, but they never stick. But making my notes available to the world in my digital garden keeps me coming back and updating it daily.
-Chuck Grimmett
-
-
www.postgresql.org www.postgresql.org
-
This latter equivalence does not hold exactly when more than two tables appear, because JOIN binds more tightly than comma. For example FROM T1 CROSS JOIN T2 INNER JOIN T3 ON condition is not the same as FROM T1, T2 INNER JOIN T3 ON condition because the condition can reference T1 in the first case but not the second.
-
A LATERAL item can appear at top level in the FROM list, or within a JOIN tree. In the latter case it can also refer to any items that are on the left-hand side of a JOIN that it is on the right-hand side of.
Unlike with most joins (IIUC), order is important with lateral joins. Weird. Why?
Maybe because it is equivalent to a cross join lateral (see example), and in an explicit cross join, you have a LHS and RHS?
-
This allows them to reference columns provided by preceding FROM items.
-
-
Local file Local file
-
It is notinsignificant either that among the illustrations of the Roland Barthes par RolandBarthes there are a series of facsimile reproductions of the author’s handwriting,analogic reproductions of linguistic graphemes, pieces of writing silenced,abstracted from the universe of discourse by their photographic reproduction. Inparticular, as we have seen, the three index cards are reproduced not for the sakeof their content, not for their signified, but for a reality-effect value for which ourexpanding taste, says Barthes, encompasses the fashion of diaries, of testimonials,of historical documents, and, most of all, the massive development of photogra-
phy. In that sense, the reproduction of these three slips ironically resonates, if on a different scale, with the world tour of the mask of Tutankhamen. It refers, if not to the magic silence of a relic, at least to the ghostly parergonal quality of what French language calls a reliquat.
Hollier argues that Barthes' reproduced cards are not only completely divorced from their original context and use, but that they are reproduced for the sheen of reality and artistic fashion they convey to the reader. So much thought, value, and culture is lost in the worship of these items in this setting compared to their original context.
This is closely linked to the same sort of context collapse highlighted by the photo of Chief William Berens seated beside the living stones of his elders in Tim Ingold's Why Anthropology Matters. There we only appreciate the sense of antiquity, curiosity, and exoticness of an elder of a culture that is not ours. These rocks, by very direct analogy, are the index cards of the zettelkasten of an oral culture.
 Chief William Berens seated beside the living stones of his elders; a picture taken by A. Irving Hallowell in 1930, between Grand Rapids and Pikangikum, Ontario, Canada. (American Philosophical Society)
Chief William Berens seated beside the living stones of his elders; a picture taken by A. Irving Hallowell in 1930, between Grand Rapids and Pikangikum, Ontario, Canada. (American Philosophical Society)
-
-
archivesspace.library.northeastern.edu archivesspace.library.northeastern.edu
-
Neighborhood improvement programs designed to protect Upper Roxbury from urban blight began in 1949 when Freedom House joined with community members to organize neighborhood clean-up projects and playground construction. Abandoned houses and cars and empty lots were targeted for clean-up by Freedom House and other neighborhood block associations. Bars that were considered a nuisance were routed out of the neighborhood and alcohol licenses were denied due to the efforts of the group. Freedom House worked closely with the city to improve the services provided to Roxbury and with the police department to improve police-community relations. At the same time, Boston was beginning a formal urban renewal campaign that did not initially include Roxbury. A telegram from the Snowdens to Mayor Collins resulted in the inclusion of the Washington Park Urban Renewal Project in Boston's campaign. By 1963 Freedom House had entered into formal contracts with the Boston Redevelopment Authority (BRA) and the Action Boston Community Development (ABCD) to serve as a liaison between the planners and technicians, and the residents of Washington Park. This relationship, lasted until the Boston Redevelopment Authority withdrew from Roxbury in the late 1960s, leaving much of its work undone.
This moment in history is featured in the Norman B. Leventhal exhibit "More or Less in Common: Environment and Justice in Human Landscape" https://www.leventhalmap.org/exhibitions/
-
-
twitter.com twitter.com
-
Dr Ellie Murray, ScD. (2021, July 6). Also, see👇🏼 [Tweet]. @EpiEllie. https://twitter.com/EpiEllie/status/1412249702460968967
-
-
twitter.com twitter.com
-
ReconfigBehSci. (2022, March 8). RT @DrEricDing: ⚠️UPDATE—#BA2 is now 11.6% in US, up from 8.3% last week. It’s definitely increasing, as warned. #COVID19 still dropping, b… [Tweet]. @SciBeh. https://twitter.com/SciBeh/status/1501248333876240385
-
-
twitter.com twitter.com
-
ReconfigBehSci on Twitter: "RT @tylerblack32: Ghouls BEFORE COVID: 🤮🤮🤮🤮🤮🤮 ‘Only 0.2% of cancer deaths occur in children! <0.003% will die of cancer! Only about 0.16%…’ / Twitter. (n.d.). Retrieved 7 February 2022, from https://twitter.com/SciBeh/status/1490254426719899655
-
-
twitter.com twitter.com
-
Prof. Christina Pagel 🇺🇦. (2022, March 8). What could be causing it? Likely combo of: 1—Dominant BA.2 causing more infections (we await ONS!) 2—Reduction in masks, self-isolation & testing enabling more infections 3—Waning boosters in older people esp I worry that we will be stuck at high levels for long time. 2/2 https://t.co/xZ2SLFNVkS [Tweet]. @chrischirp. https://twitter.com/chrischirp/status/1501250081693048838
-
-
-
In these sessions, students didn’t listen to a description ofcomputer science concepts, or engage in a discussion about the work performedby computer scientists; they actually did the work themselves, under the tutors’close supervision.
The process seen in cognitive apprenticeships seems more akin to the sorts of knowledge transfer done in primary oral indigenous cultures by passing down stories and performing (song, dance, art, etc.) knowledge.
It shouldn't be surprising that cognitive apprenticeships work well given their general use by oral cultures over millennia.
link to: Writing out answers will show gaps in knowledge Performing actions will show gaps in knowledge
-
-
mg.co.za mg.co.za
-
South Africa has nearly 26 000 schools, 400 000 teachers and close to 13-million learners.
South Africa has an interesting number of school and learners. with a big number of learners in the country.
-
-
docdrop.org docdrop.org
-
Such radical compositional approaches arecontemporaneous with the Surrealist use of montage, but predateBurrough’s cut-up-fold-in technique, and ‘put[...] the avant-gardeclaims of hyperfiction to shame’ (Krapp, 2006: 362).
The compositional approaches mentioned here are those of Wittgenstein and Walter Benjamin.
What was Burrough's cut-up-fold-in technique?
-
-
-
But it is more difficult in a world of manuscriptsthan in the era of printing to evaluate what constitutes a note—that is, a piece ofwriting not meant for circulation but for private use, say, as preparatory toward afinished work
Based on this definition of a "note", one must wonder if my public notes here on Hypothes.is are then not notes as they are tacitly circulated publicly from the first use. However they are still specifically and distinctly preparatory towards some future finished work, I just haven't yet decided which ultimate work in which they'll appear.
-
A study of Samuel Johnson (1709–84) has identified four different kinds of reading in which Johnson described himself engaging: “hard study” for learned books read with pen in hand, “perusal” for purposeful consultation in search of information, “curious reading” for engrossment in a novel, and “mere reading” for browsing and scanning “without the fatigue of close attention.”216
"Mere reading" today consists of a lot of scrolling through never-ending social media posts on mobile phones....
-
-
sde.ok.gov sde.ok.gov
-
assistive technology
We should place the definition of Assistive Technology here: Assistive Technology is technology used by individuals with disabilities in order to perform functions that might otherwise be difficult or impossible.
-
- Mar 2022
-
movement-ontology.brandazzle.net movement-ontology.brandazzle.net
-
Put Eidsheim 2015 and O'Callaghan 2007 in dialogue with each other.
Brandon Lewis seems to be talking about actively taking two papers and placing them "in dialogue with each other" potentially by reading, annotating, and writing about them with himself as an intermediary.
-
-
en.wikipedia.org en.wikipedia.org
-
An early example of a timber circle witnessed by Europeans was recorded by watercolor artist John White in July 1585 when he visited the Algonquian village of Secotan in North Carolina. White was the artist-illustrator and mapmaker for the Roanoke Colony expedition sent by Sir Walter Raleigh to begin the first attempts at British colonization of the Americas.[2] White's works represent the sole-surviving visual record of the native inhabitants of the Americas as encountered by England's first colonizers on the Atlantic seaboard.[3] White's watercolor and the writings of the chronicler who accompanied him, Thomas Harriot, describes a great religious festival, possibly the Green Corn ceremony, with participants holding a ceremonial dance at a timber circle. The posts of the circle were carved with faces. Harriot noted that many of the participants had come from surrounding villages and that "every man attyred in the most strange fashion they can devise havinge certayne marks on the backs to declare of what place they bee." and that "Three of the fayrest Virgins" danced around a central post at the center of the timber circle.[4]
Artist, illustrator and mapmaker John White painted a watercolor in July 1585 of a group of Native Americans in the Secotan village in North America. Both he and chronicler Thomas Harriot described a gathering of Indigenous peoples gathered in the Algonquian village as part of Sir Walter Raleigh's Roanoke Colony expedition. They describe a festival with participants holding a dance at a timber circle, the posts of which were carved with with faces.
Harriot wrote that participants had come from surrounding villages and that "every man attyred in the most strange fashion they can devise havinge certayne marks on the backs to declare of what place they bee."

This evidence would generally support some of Lynne Kelly's thesis in Knowledge and Power. A group of neighboring peoples gathering, possibly for the Green Corn Ceremony, ostensibly to strengthen social ties and potentially to strengthen and trade knowledge.
Would we also see others of her list of markers in the area?
Read references: - Daniels, Dennis F. "John White". NCpedia. Retrieved 2017-12-19. - Tucker, Abigal (December 2008). "Sketching the Earliest Views of the New World". Smithsonian Magazine. Retrieved 2017-12-19. - "A Selection of John White's Watercolors : A festive dance". Encyclopedia Virginia. Retrieved 2017-12-19.
-
-
Tags
Annotators
URL
-
-
-
Wanta JampijinpaPatrick, a Warlpiri Elder, teaches that north corresponds to ‘Law’,south to ‘ceremony’, west to ‘language’ and east to ‘skin’. ‘Country’lies at the intersection of these directions, at the centre of thecompass: Westerners conceptualise it as ‘here’.
In Warlpiri, the cardinal directions of north, south, east and west associatively correspond with the ideas of "Law", "ceremony", "skin", and "language" respectively. The idea of "Country" lies at the center of these directions in a space that Westerners would describe as "here".
This directional set up underlines the value of each of the related concepts and provides pride of place to "Country" and one's being "in Country".
Compare these with the Japanese pattern of こ (ko), そ (so), あ (a), ど (do) which describe a location with respect to the speaker.
Western readers should notice here, that the author centers the name and position of the origin of this knowledge at the start of the sentence. While it is associated with him, it is also certainly associated with all his preceding ancestors and Elders who passed this information down.
One might suspect that this practice isn't as common with base-level cultural knowledge, but that it becomes more important at succeeding levels of intimate area-based restricted knowledge. Placing the origin of the knowledge here at a more basic level of knowledge may help to instruct Western readers slowly and more surely understand how this foreign culture works.
How closely does this practice generally look like the Western idea of citing one's sources which only evolved slowly over history and became more common with the flood of information in the 1500s?
-
-
docdrop.org docdrop.org
-
der eben sagt es gibt immer wieder neue galaxien
Vllt ist dieser Galaxienbegriff zu starr, zu voraussetzungsreich? Vllt hilft bspw. Latours Plug-in Idee hier etwas bescheidener zu sein, kritische Nähe, nicht kritische Distanz
Tags
Annotators
URL
-
-
-
chain to 00:34:22 your mobile
chained to you mobilephone
Mit Latour gesagt kann hier wieder ein gewinnbringender Perspektivwechsel vorgenommen werden. Ich denke u.a. an Latours Idee der Plug-ins und ein sein Bild einer Marionette, die an Fäden hängt. Wir werden nicht frei, wenn wir alle Fäden abschneiden, wir werden frei wenn wir uns der Transformationen durch die einzelnen Fäden und entlang dieser bewusst werden. So kann es möglich werden, ggf. auch einzelne Fäden zu kappen oder neue zu binden oder zu kreuzen. Einfach alles abzuschneiden, lässt eine im Nachhinein am Boden liegende Marionette nun auch nicht in der Magie der Freiheit sich Bewegen. m.E. werden hier auch zwei Freiheitsbegriffe durcheinander geworfen. Es wäre erstmal wichtig, zwischen positiver und negativer Freiheit zu unterscheiden (Politische Philosophie - Celikates und Gosepath)
Tags
Annotators
URL
-
-
niklasblog.com niklasblog.com
-
find us best news channel in punjab
skynewspunjab is India's biggest punjabi channel which is loaded with information and entertainment for you. We are best news channel in punjab endeavors to give you language content in your language that won't just assist you with moving forward in your life yet additionally make a stage that can speak loudly. You won't just get the most recent news on this stage however will likewise entertain you with valuable conversations on positions, training and the changing financial image of the new India as well as interesting stories from sports, cinema, unfamiliar chat and book world. All things considered, we are the best news channel in punjab have brought to you a world on the Internet that will fill you with the fervor of life. The vital administration behind the skynewspunjab has been dynamic in the electronic and print media industry for the last numerous years. We have wide openness underway, conveyance, deals and marketing of news and entertainment content featuring Punjabi, Hindi and English language programming. We are best news channel in Punjab resolved to give moral and trustworthy substance to our watchers. We have the energy to accomplish our objectives genuinely and intelligently. skynewspunjab continually endeavors to be an extraordinary wellspring of information for Punjabis around the world. We direct research and partake in various initiatives to continually foster ourselves in the industry and to add to society. Continue to observe best news channel in punjab and get the flash of our inventiveness.
Tags
Annotators
URL
-
-
www.nature.com www.nature.com
-
Shen, X.-R., Geng, R., Li, Q., Chen, Y., Li, S.-F., Wang, Q., Min, J., Yang, Y., Li, B., Jiang, R.-D., Wang, X., Zheng, X.-S., Zhu, Y., Jia, J.-K., Yang, X.-L., Liu, M.-Q., Gong, Q.-C., Zhang, Y.-L., Guan, Z.-Q., … Zhou, P. (2022). ACE2-independent infection of T lymphocytes by SARS-CoV-2. Signal Transduction and Targeted Therapy, 7(1), 1–11. https://doi.org/10.1038/s41392-022-00919-x
-
-
-
A number ofstudies have demonstrated that instructional videos that include gesture producesignificantly more learning for the people who watch them: viewers direct theirgaze more efficiently, pay more attention to essential information, and morereadily transfer what they have learned to new situations. Videos that incorporategesture seem to be especially helpful for those who begin with relatively littleknowledge of the concept being covered; for all learners, the beneficial effect ofgesture appears to be even stronger for video instruction than for live, in-personinstruction.
Gestures can help viewers direct their attention to the most salient and important points in a conversation or a lecture. As a result, learning has been show to be improved in watching lectures with gestures.
Learning using gestures has been shown to be stronger in video presentations over in-person instruction.
-
-
www.reseau-canope.fr www.reseau-canope.fr
-
L’imitation et l’influence du jeu interactif sont bien mises en évidence dans une étude de Orit Hetzroni et Juman Tannous, de la Faculté des Sciences de l’éducation de l’Université de Haifa (Israël)
==>l’échantillon de l’étude est est extrêmement limité, l’étude n’est pas répliqué et elle ne permet pas de retirer de résultats concluants
Tags
Annotators
URL
-
-
online.wsj.com online.wsj.com
-
young companies typically fail because you have a charismatic leader with a bunch of beliefs, but those beliefs don't translate to the rest of their company
failure in communication
-
-
docdrop.org docdrop.org
-
The imperial dream was always there, but you know, empires are often the creation of a very small gang of people at the top. I don’t think the Russian people [are] interested in this war. I don't think that the Russian people want to conquer Ukraine or to slaughter the citizens of Kyiv.
The interesting modern historical question is why does a small gang of authoritarian leaders seem to rise up to the top and take over Russia? Is there some fundamental lesson that the people of Russia have not yet learned that creates this atmosphere of enabling authoritarianism? Yeltsin tried but it failed and this vacuum created the space for the opportunity Putin to step in. The danger of failed democracy is authoritarianism waiting in the wings.
-
- Feb 2022
-
brainbaking.com brainbaking.com
-
I have little use for countless of “collected” links and likes. Published Obisidan Vaults look cool, but the initial excitement wears off pretty quickly.
Actual public digital gardens, or what I would consider good ones, are exceedingly rare. Even rarer are find ones which have enough subject overlap with my own areas of interest which tends to make them even less directly interesting to me.
What I wouldn't give to have well tended public digital gardens by people in my areas of interest.
-
-
www.jacobsen.no www.jacobsen.no
-
Hence an email address/mailbox/addr-spec is "local-part@domain"; "local-part" is composed of one or more of 'word' and periods; "word" can be an "atom" which can include anything except "specials", control characters or blank/space; and specials (the *only* printable ASCII characters [other than space, if you call space "printable"] *excluded* from being a valid "local-part") are: ()<>@,;:\".[] Therefore by the official standard for email on the internet, the plus sign is as much a legal character in the local-part of an email address as "a" or "_" or "-" or most any other symbol you see on the main part of a standard keyboard.
-
There's a common design flaw on many many websites that require an email address to register; most recently I came across this bug on CNet's download.com site: for some reason they don't accept me when I try to register an email address containing a "+", and they then send me back saying my address is invalid. It isn't!
-
"+" is a completely valid character in an email address; as defined by the internet messaging standard published in 1982(!) RFC 822 (page 8 & 9)... Any website claiming anything else is wrong by definition, plus they are prohibiting me and many fellow anti-spam activists from tracking where inbound spam comes from:
-
-
people.cs.rutgers.edu people.cs.rutgers.edu
-
Screening is a useful way of avoiding spam and/or other unwanted correspondence.
-
Filing is the simplest application to take advantage of plus signs.
-
The "+tag" portion of the email address can then be used both for filing mail and for screening it.
-
-
-
you can't see the beetle in my box nor I the one in yours ludwig wittgenstein use the beetle in the Box analogy to suggest that the meaning of sensation words such as pain isn't given 00:01:10 by referring to some private inner introspected something a sensation to which you alone have access in his view there can't be more to the public meaning of our language than we are capable of teaching each other and the 00:01:23 private something the beetle can't have a role in that teaching because we can't get at
The duality of self and other is the peculiar symmetrical asymmetry of being human, and possibly of being life itself.
Similarity and differences in the meaning of words between individuals is unavoidable because we all seem to share this quality of consciousness, as well as the quality of experiencing others as objects of our consciousness.
Nature instills the quality of "unique conscious experience" to each of us. Biological replication is the basis for the repetition of this pattern in all members of our species.
Why was I drawn to the content of this youtube, which came from this article interviewing Teodora Petkova: https://medium.com/content-conversations/a-semantic-text-strategy-conversation-teodora-petkova-fa6d8ad7c72f Through this youtube and through the interview with Teodora Petkova, I became aware of Ludwig Wittgenstein's beetle-in-a-box analogy for private thoughts.A meme is reproduced and shared over and over, drawing people who resonate with it.
Hence, my own discovery of this idea demonstrates the mechanics of self and other consciosness. In any rendition of the present, my semantic state has been influenced by countless number of other writers, content developers or consciousnesses, echoing Husserl's Lebenswelt. Once we are bootstrapped into language through a long gestation period of child development, we simply grow our vocabulary of words, and continuously upgrade their individual meaning through the unique experiences of our unique lifeworlds.
This symmetrical asymmetry is a distinct and unique property of the individual human, showing just how entangled the individual is with the collective, the self with the other.
It is said that the most obvious is at the same time the most difficult to see. The metaphor "a fish does not know of the water that surrounds it" is apt. Our symmetrical asymmetry of experience is so universal that its salience and peculiarity is easily overlooked and not explicitly discussed except by the philosophically inclined. It is more often subconsciously felt than made into an explicit subject of discourse. It is recognized as obvious and coming with the territory of being human.
Indeed, we might say that this common peculiarity of the private, subjective world is paradoxically one of the strangest and yet one of the most common at the same time. Its obviousness does not lessen its profound sense of magic.
The fact that we live in these two kinds of worlds, the private inner and the public outer, and that these terms "private inner" and "public outer" are themselves abstractions, also explains how our participation in collective reality may often not live up to expectations.
For example, in a time when the world needs to undergo a monumental whole system change, it is a challenge to mobilize sufficient number of people to drive the needed change. Part of the reason for this could be that the individual pole, the salience of the "private, inner" pole could prioritize it above even such collective action. The ideas and feelings in our own life as an individual, driven by our private inner lives may dominate our individual actions. Getting on with life often supersedes even threats to society.
-
-
Local file Local file
-
If we put effort into the attempt of retrievinginformation, we are much more likely to remember it in the long run,even if we fail to retrieve it without help in the end (Roediger andKarpicke 2006)
-
Learning requires effort, because we have to think to understandand we need to actively retrieve old knowledge to convince ourbrains to connect it with new ideas as cues. To understand howgroundbreaking this idea is, it helps to remember how much effortteachers still put into the attempt to make learning easier for theirstudents by prearranging information, sorting it into modules,categories and themes. By doing that, they achieve the opposite ofwhat they intend to do. They make it harder for the student to learnbecause they set everything up for reviewing, taking away theopportunity to build meaningful connections and to make sense ofsomething by translating it into one’s own language. It is like fastfood: It is neither nutritious nor very enjoyable, it is just convenient
Some of the effort that teachers put into their educational resources in an attempt to make learning faster and more efficient is actually taking away the actual learning opportunities of the students to sort, arrange, and make meaningful connections between the knowledge and to their own prior knowledge bases.
In mathematics, rather than showing a handful of methods for solving a problem, the teacher might help students to explore those problem solving spaces first and then assist them into creating these algorithms. I can't help but think about Inventional Geometry by William George Spencer that is structured this way. The teacher has created a broader super-structure of problems, but leaves it largely to the student to do the majority of the work.
-
A coach is not there to do the work,but to show us how to use our time and effort in the most effectiveway.
Much as coaches help their athletes become better, teachers are there to help students use their time and work efforts in the most effective ways.
-
-
medicalxpress.com medicalxpress.com
-
Michaud, M., & Center, U. of R. M. (n.d.). Trust in science at root of vaccine acceptance. Retrieved February 8, 2022, from https://medicalxpress.com/news/2022-01-science-root-vaccine.html
-
-
-
Jorge A. Caballero, MD (jorgecaballero.eth). (2022, January 10). 🧵/ I just spoke with two journalists about data that shows how the U.S. healthcare system is collapsing before our eyes. The million dollar question during both interviews was, “What else could we be doing right now?” The answer: Flatten the hospitalization curve. Now. [Tweet]. @DataDrivenMD. https://twitter.com/DataDrivenMD/status/1480607009867132928
-
- Jan 2022
-
www.theatlantic.com www.theatlantic.com
-
-
When you stumble across an influencer and want to know what their deal is, your first stop will be their link-in-bio.
This is a tautology because Instagram only allows you to include one link!
-
Even major corporations such as Qantas Airlines, Red Bull, and the Los Angeles Clippers have started putting a Linktree in their Instagram and TikTok bios, Anthony Zaccaria, Linktree’s co-founder and chief commercial officer, told me. These companies all have expensive websites, but he said that link-in-bios have come to represent a space in between social media and websites: a regularly updated page where artists can plug their new music, airlines can promote their new flight routes, and even non-influencers can list out the TV shows they’re currently watching. While a traditional website might remain relatively static over time—an airline like Qantas, for instance, is always going to want its flight-booking tool to be front and center—a link-in-bio is a sort of ever-shifting homepage, the ideal spot for brands and influencers to house updates or tout new products.
Who says the link in bio needs to go to a company's homepage? Why couldn't it be a custom landing page geared toward the social media site the link is placed on?
The reasoning here is completely false.
-
In a study done for The Atlantic, the web-analytics firm Parse.ly estimated that Linktree links account for nearly half of all the link-in-bio traffic on Instagram.
Nearly half of all the link in bio traffic on Instagram comes from Linktree links.
-
An explosion of companies sporting names such as Shorby, Linkin.bio, Beacons, Tab Bio, and Koji—Rockelle’s tool of choice—are giving the link-in-bio a glow-up.
How long before the pendulum swings all the way back to the original web?
cross reference: https://indieweb.org/link_in_bio
-
-
notesfromasmallpress.substack.com notesfromasmallpress.substack.com
-
If booksellers like to blame publishers for books not being available, publishers like to blame printers for being backed up. Who do printers blame? The paper mill, of course.
The problem with capitalism is that in times of fecundity things can seem to magically work so incredibly well because so much of the system is hidden, yet when problems arise so much becomes much more obvious.
Unseen during fecundity is the amount of waste and damage done to our environments and places we live. Unseen are the interconnections and the reliances we make on our environment and each other.
There is certainly a longer essay hiding in this idea.
-
-
uni-bielefeld.de uni-bielefeld.de
-
note or a (smaller) subject area thatis not linked to the web of references becomes lost irretrievably in the bulk of notes
Unlinked notes in paper-based knowledge systems can become lost in the shuffle. This is much harder to do in digital systems which have visual checks that highlight unlinked notes.
-