If you happen to annotate page three, and then weeks or years later visit the single page view wouldn’t you want to see the annotation you made? If the tool you are using queries for annotations using only the URL of the document you are viewing you won’t see it.
- Mar 2022
-
web.hypothes.is web.hypothes.is
-
-
www.linkinglearning.com.au www.linkinglearning.com.au
-
Learning happens when a connection is made between these nodes;
I think that this is a powerful statement - it shows that true learning occurs when we share, experience and learn from each other and through networking.
-
PLE is the educational manifestation of the web’s “small pieces loosely joined,” a “world of pure connection, free of the arbitrary constraints of matter, distance, and time.”
The quotation here is a strong one because I have always felt that many curriculums are constrained by the rules and laws that govern certain institutes - it leaves little to be explored and imagined sometimes ... so the aspect of small pieces coming together to create a larger whole feeds into that aspects of 'ecology'. It is what we might refer to in the design/ art space as gestalt.
-
PLNs (professional learning networks) and their role in supporting the development of ‘connected educators’.
Professional learning networks support professional development of educators (who are digitally literate). Is this a more modern connected version or an extension of communities of practice?
-
-
www.elizabethfilips.com www.elizabethfilips.com
-
MY LECTURE NOTES
Elizabeth Filips has digital versions of medical school notes online. She's drawn them (in software) by hand with color and occasional doodles in them (there's an image of Einstein's head with an E=mc^2 under it on one page) which makes them more memorable for having made them in the first place, but with the color and the pictures, they act as a memory palace.
I've found no evidence (yet) that she's using direct mnemonics or that she's been specifically trained in the method of loci or other techniques. This doesn't, however, mean that she's not tangentially using them without knowing about them explicitly.
One would suspect that this sort of evolutionary movement towards such techniques would have been how they evolved in the first place.
-
-
-
the going through abstraction and re-specification so i think i became interested in cetera carson also because i saw a lot of similarities 01:11:30 to what historians of science describe as experimental work in laboratories and that is especially in the field of science and technology 01:11:43 studies especially the work of hanzio greinberger he works for the max planck institute for history of science in berlin and the way he describes 01:11:55 um experimental work as a form of material deconstruction um is my blueprint for understanding 01:12:10 the work of lumen
Sönke Ahrens used Hans-Jörg Rheinberger's description of experimental work as a form of material deconstruction as a framework for looking at Niklas Luhmann.
-
-
en.wikipedia.org en.wikipedia.org
-
Hans-Jörg Rheinberger (born 12 January 1946) is an historian of science who comes from Liechtenstein. He was director of the Max Planck Institute for the History of Science in Berlin from 1997 to 2014. His focus areas within the history of science are the history and epistemology of the experiment, and further the history of molecular biology and protein biosynthesis.
-
-
Local file Local file
-
Topic A topic was once a spot not a subjecttopic. to ̆p’ı ̆k. n. 1. The subject of a speech, essay, thesis, or discourse. 2. A subject of discussion or con-versation. 3. A subdivision of a theme, thesis, or outline.*With no teleprompter, index cards, or even sheets of paper at their disposal, ancient Greek and Roman orators often had to rely on their memories for holding a great deal of information. Given the limi-tations of memory, the points they chose to make had to be clustered in some meaningful way. A popular and quite reliable method for remembering information was known as loci (see Chapter 9), where loci was Latin for “place.” It involved picking a house you knew well, imagining it in your mind’s eye, and then associating the facts you wanted to recall with specifi c places inside of that house. Using this method, a skillful orator could mentally fi ll up numerous houses with the ideas he needed to recall and then simply “visit” them whenever he spoke about a particular subject. The clusters of informa-tion that speakers used routinely came to be known as commonplaces, loci communes in Latin and koinos topos in Greek. The great Greek philosopher Aristotle referred to them simply as topos, meaning “places.” And that’s how we came to use topic to refer to subject or grouping of information.**
Even in the western tradition, the earliest methods of mnemonics tied ideas to locations, from whence we get the ideas of loci communes (in Latin) and thence commonplaces and commonplace books. The idea of loci communes was koinos topos in Greek from whence we have derived the word 'topic'.
Was this a carryover from other local oral traditions or a new innovation? Given the prevalence of very similar Indigenous methods around the world, it was assuredly not an innovation. Perhaps it was a rediscovery after the loss of some of these traditions locally in societies that were less reliant on orality and moving towards more reliance on literacy for their memories.
-
-
movement-ontology.brandazzle.net movement-ontology.brandazzle.net
-
Put Eidsheim 2015 and O'Callaghan 2007 in dialogue with each other.
Brandon Lewis seems to be talking about actively taking two papers and placing them "in dialogue with each other" potentially by reading, annotating, and writing about them with himself as an intermediary.
-
-
citeseerx.ist.psu.edu citeseerx.ist.psu.edudownload2
-
The complete overlapping of readers’ and authors’ roles are important evolution steps towards a fully writable web, as is the ability of deriving personal versions of other authors’ pages.
-
Writing for the web is still a complex and technically sophisticated activity. Too many tools, languages, protocols, expectations and requirements have to be considered together for the creation of web pages and sites.
-
-
github.com github.com
-
ransack is a very dirty solution that completely integrates the Searching, Sorting, and Views as requirements of eachother
-
-
adjacentpossible.substack.com adjacentpossible.substack.com
-
www.theguardian.com www.theguardian.com
-
Waterson, J. (2022, January 11). BBC does not subscribe to ‘cancel culture’, says director of editorial policy. The Guardian. https://www.theguardian.com/media/2022/jan/11/bbc-does-not-subscribe-to-cancel-culture-says-director-of-editorial-policy
-
-
inst-fs-iad-prod.inscloudgate.net inst-fs-iad-prod.inscloudgate.net
-
insidious declamations should have no effect upon the wise legislators who have decreed liberty to humanity. The attacks the colonists propose against this liberty must be feared all the more insofar as they hide their detestable projects under the veil of patriotism. We know that illusory and specious descriptions have been made to you of the renewal of terrible violence. Already, perfidious emissaries have crept among us to foment destruction at the hands ofliberticides. They will not succeed, this 1 swear by all that is most sacred in liberty. My attachment to France, the gratitude that all the blacks conserve for her, make it my duty to hide from you neither the plans being fomented nor the oath that we renew to bury ourselves beneath the ruins of a country revived by liberty rather than suffer the return of slavery.
Here Toussaint states that he refuses to let Vaublanc convince 'property' owners in St. Domingue to regress back to the use of enslavement. Toussaint also says that it he and other Blacks have gratitude to France and will not try to hide the fact they will all fight should, the "enemy of liberty" slavery return.
-
-
askubuntu.com askubuntu.com
-
The reason for the new name is that the "dist-upgrade" name was itself extremely confusing for many users: while it was named that because it was something you needed when upgrading between distribution releases, it sounded too much as though it was only for use in that circumstance, whereas in fact it's much more broadly applicable.
-
-
www.theguardian.com www.theguardian.com
-
Geddes, L., & Sample, I. (2022, March 7). Covid can shrink brain and damage its tissue, finds research. The Guardian. https://www.theguardian.com/world/2022/mar/07/covid-can-shrink-brain-and-damage-its-tissue-finds-research
-
-
www.bmj.com www.bmj.com
-
Limb, M. (2022). Covid-19: Updated PPE guidance puts NHS staff at risk of infection, say medics. BMJ, 376, o733. https://doi.org/10.1136/bmj.o733
-
-
insights.som.yale.edu insights.som.yale.edu
-
Health & Veritas: Is Long COVID One Disease or Many? (Ep. 19). (n.d.). Yale Insights. Retrieved 21 March 2022, from https://insights.som.yale.edu/insights/health-veritas-is-long-covid-one-disease-or-many-ep-19
-
-
www.haaretz.com www.haaretz.com
-
The historic books of the Bible were written by a “Yahweh only party” and are thus keenly critical of the worship of other gods in Judah. Still, it is clear from their description that polytheism was the norm in the First Temple period. It was only during King Josiah’s reform that the "Yahweh only party" really took control and began pushing other gods out of Judean minds.
Polytheism was the cultural norm during the First Temple period. It wasn't until the reforms of King Josiah described in 2 Kings in the second half of the 7th century BCE that other Semitic gods were actively removed from the Temple and parts of culture in favor of Yahweh.
-
Yet the ancient Hebrews clearly adored them just like the other West Semites did. Ezekiel (8:16) recounts seeing people worshiping the sun in the Temple. We can infer this because the bible specifically condemns their worship, and we are told that Josiah took actions to stomp out the cult in the late First Temple period, the second half of the 7th century B.C.E. These actions included removing cult objects from the Temple itself (2 Kings 23:11).
-
"Josiah smashed the sacred stones and cut down the Asherah poles and covered the sites with human bones" (2 Kings 23:14, New International Version)
2 Kings 23:14 indicates that King Josiah cut down the Asherah poles as a monotheistic reform in the second half of the 7th century BCE.
Could these have have been in circles? Could they have been used as mnemonic devices?
link this to the idea of the standing stone found at Khirbet Qeiyafa.
Link this to my Ark of Covenant example.
Link to Stonehenge and other henge examples as well as other timber circles.
-
El had a consort, the goddess Asherah, and as Yahweh took El’s place, Asherah became Yahweh’s consort. We are told that the Asherah was worshipped in the earliest Temple of Jerusalem – not explicitly, but we are definitely told that her symbols were removed from the Temple, so they had to be there in the first place (1 Kings 15:13 and 2 Kings 23:14).It was only at the very end of the First Temple period, during the reign of King Josiah (the second half of the 7th century B.C.E.) that the cult objects of Asherah were taken out of the Temple, quite dramatically. There are quite a number of references to Josiah's monotheistic reforms, such as:."Josiah smashed the sacred stones and cut down the Asherah poles and covered the sites with human bones" (2 Kings 23:14, New International Version)
1 Kings 15:13, 2 Kings 23:14 and 2 Kings 23:14 indicate that the symbols of the goddess Asherah, a consort of El, were in the earliest Temple of Jerusalem as these sections describe the fact that they were removed.
-
In this ancient text, we can see that El and Yahweh were still perceived as being two separate deities, with Yahweh subordinate to El. But as time went by, El and Yahweh became conflated: the two deities began to be seen as one and the same.In Exodus 6:3 God tells Moses: "I appeared unto Abraham, unto Isaac, and unto Jacob, by the name of God Almighty (El Elyon), but by my name Jehovah was I not known to them." Thus the ancients only knew God as El, but as time went by they discovered that El was just another name of Yahweh.
In Deuteronomy 32 the gods El and Yahweh are separate deities which, over time, became conflated into one god as indicated in Exodus 6:3.
-
It seems that what this story and other biblical stories like it are telling is that the belief in Yahweh supplanted the worship of Ba’al. In fact it seems that in some ways, Yahweh subsumed Ba’al, taking on his attributes and powers.In some of the Bible’s more poetic texts, Yahweh is presented as a storm god in very much the same language that Ba’al is described:“At the brightness that was before him his thick clouds passed, hail stones and coals of fire. The Lord also thundered in the heavens, and the Highest gave his voice; hail stones and coals of fire. Yea, he sent out his arrows, and scattered them; and he shot out lightnings, and discomfited them” (Psalms 18:12-14).
Biblical passages like Psalms 18:12-24 may be indicative of Yahweh subsuming the powers and attributes of other regional gods like Ba'al.
This makes one wonder if Yahweh evolved from other cultures into the one true god of the Hebrews?
Tags
- mnemonic devices
- Khirbet Qeiyafa
- Baal
- henges
- polytheism
- archaeology
- Asherah poles
- Yahweh
- examples
- El
- sun worship
- Exodus 6
- Psalms
- Asherah
- monotheism
- Josiah
- religion
- Temple of Jerusalem
- moon worship
- Ark of the Covenant
- evolution of religion
- standing stones
- timber circles
- 2 Kings 23
Annotators
URL
-
-
-
Peter Eseli of Mabuiag Island (known locally as Mabuyag)in the western Torres Strait began writing down traditional knowledgein the Kala Lagau Ya language in the early twentieth century. By1939, Eseli had amassed a 77-page manuscript, complete withdrawings, songs and genealogies as well as a wealth of starknowledge, some of which is included in this book. He continuedadding to it until his death in 1958. His manuscript was latertranslated into English.
-
In 1898, Māori man Te Kōkau and his son, Rāwairi Te Kōkau,began recording traditional star knowledge in the Māori language.After 35 years, they had amassed a 400-page manuscript that
contained over a thousand star names. Rāwairi passed the manuscript to his grandson, Timi Rāwairi. In 1995, Timi’s own grandson asked him about Matariki, a celebration that kicks off the Māori new year, heralded by the dawn rising of the Pleiades star cluster. Timi went to a cupboard, pulled out the manuscript and handed it to his grandson, Rangi Mātāmua.
Was it partially coincidence that this knowledge was written down and passed on within the family or because of the primacy of the knowledge within the culture that helped to save in spanning from orality into literacy?
What other examples might exist along these lines to provide evidence for the passing of knowledge at the border of orality and literacy?
Link this to ideas about the border of orality and literacy in Welsh and Irish.
-
This hierarchical system ensures accuracy, rigour and competencyof information.
Hierarchical systems of knowledge in Indigenous cultures helps to ensure rigor, competency, and most importantly accuracy of knowledge passed down from generation to generation.
-
In the Warlpiri Aboriginal language of Central Australia, you do notdescribe positions of things with yourself as the focal reference point.Rather, your position is defined within the world around you. InWarlpiri, my computer is south of me, my cat is sleeping west of meand the door is east of me. It requires you to always know thecardinal directions (north, south, east and west), no matter yourorientation. Any one person is not the centre of the world, they arepart of it.
Western cultures describe people's position in the world with them as the center, while Indigenous cultures, like those of the Warlpiri Aboriginal language of Central Australia, embed the person as part of the world and describe their position with respect to it using the cardinal directions.
-
A sense ofconnectedness is a unique part of Indigenous science. In Westernscience, knowledge is often considered separate from the people whodiscover it, while Indigenous cultures see knowledge as intricatelyconnected to people.
A primary difference between Indigenous science and Western science is the first is intimately connected to the practitioners while the second is wholly separate.
Would Western science be in a healthier space currently if its practice were more tightly bound to the people who need to use it (everyone)? By not being bound to the everyday practice and knowledge of our science, increasingly larger portions of Western society don't believe in science or its value.
-
All the knowledge provided by Elders in this book has beenapproved for public eyes. Higher, secret levels of knowledge exist,but they are not presented here.
-
The First Astronomers challenges commonly held views thatIndigenous ways of knowing do not contain science.
When reviewing back over at the end, ask:
Did the book show that Indigenous ways of knowing do contain "science"? What evidence is presented here?
-
These ways of knowinghave inherent value and are leading Western scientists to betterunderstand celestial phenomena and the history and heritage thisconstitutes for all people.
The phrase "ways of knowing" is fascinating and seems to have a particular meaning across multiple contexts.
I'd like to collect examples of its use and come up with a more concrete definition for Western audiences.
How close is it to the idea of ways (or methods) of learning and understanding? How is it bound up in the idea of pedagogy? How does it relate to orality and memory contrasted with literacy? Though it may not subsume the idea of scientific method, the use, evolution, and refinement of these methods over time may generally equate it with the scientific method.
Could such an oral package be considered a learning management system? How might we compare and contrast these for drawing potential equivalencies of these systems to put them on more equal footing from a variety of cultural perspectives? One is not necessarily better than another, but we should be able to better appreciate what each brings to the table of world knowledge.
Tags
- anthropology
- relative motion
- intellectual history
- Indigenous science
- history of information
- Western science
- definitions
- position
- hierarchies
- indigenous knowledge
- orality vs. literacy
- sociology
- experimental learning
- examples
- scientific method
- Western culture
- culture
- levels of indigenous knowledge
- information theory
- history of science
- pedagogy
- approval of Elders
- center of the world
- science denial
- learning
- indigenous cultures
- indigenous ways of knowing
- astronomy
- discovery learning
- learning management systems
- orality on the border of literacy
Annotators
-
-
www.evolutionarymanifesto.com www.evolutionarymanifesto.com
-
The role of governance in organizing cooperation
And it seems like we are going for structural solutionism i.e. we will solve free rider by governance ...
-
As a result, members who pursue their own individual interests will also pursue the interests of the organization, as if guided by an invisible hand. Cooperation pays. Members capture the benefits of anything they can do to assist the organization. Within the group, they therefore treat the other as self.
Within the group, they therefore treat each other as self.
But what about when they don't - when people "free-ride". That's a key question. I agree that should we really treat others as ourselves suddenly completely new levels of cooperation would become possible and become easy. However, I think that needs quite a profound ontological shift and that isn't easy.
-
-
momentjs.com momentjs.com
-
Modern JavaScript environments will also implement the by ECMA-402 specification, which provides the Intl object
-
-
-
www.haaretz.com www.haaretz.com
-
The kothon of Motya in southern Sicily had first been assumed to be an artificial harbor. It wasn’t, archaeologist Lorenzo Nigro of Sapienza proves
Overview of paper: https://doi.org/10.15184/aqy.2022.8
-
The constellations’ positions in the night sky on significant dates, such as solstices and equinoxes, are mirrored in the alignments of the main structures at the compound, he found. Steles were “carefully placed within the temenos to mark the rising, zenith, or setting of the stars over the horizon,” he writes.
Phoenicians use of steles and local environment in conjunction with their astronomy fits the pattern of other uses of Indigenous orality and memory.
Link this example to other examples delineated by Lynne Kelly and others I've found in the ancient Near East.
How does this example potentially fit into the broader framework provided by Lynne Kelly? Are there differences?
Her thesis fits into a few particular cultural time periods, but what sorts of evidence should we expect to see culturally, socially, and economically when the initial conditions she set forth evolve beyond their original context? What should we expect to see in these cases and how to they relate to examples I've been finding in the ancient Near East?
-
But crucially, he believes the pool at the center of the complex may have also served as a surface to observe and map the stars. The water surface would have mirrored the sky, as water does – none other than Leonardo da Vinci pointed out the attributes of inert standing water when studying the night sky. For one thing, the stars were adored by the Phoenicians, whether as gods or deceased ancestors; and the position of the constellations was of keen interest to the sailors among them for navigation purposes, Nigro points out.
Lorenzo Nigro indicates that the "kothon" of Motya in southern Sicily was a pool of Baal whose surface may have been used to observe and map the stars. He also indicates that the Phoenicians adored the stars potentially as gods or deceased ancestors. This is an example of a potentially false assumption often seen in archaeology of Western practitioners misconstruing Indigenous practices based on modern ideas of religion and culture.
I might posit that this sort of practice is more akin to that of the science of Indigenous peoples who used oral and mnemonic methods in combination with remembering their histories and ancestors.
Cross reference this with coming reading in The First Astronomers (to come) which may treat this in more depth.
Leonardo da Vinci documented the attributes of standing water for studying the night sky.
Where was this and what did it actually entail?
-
-
www.amazon.com www.amazon.com
-
www.cs.umd.edu www.cs.umd.edu
-
Democratic processes take time. The goal of a legislation-writing genex is not necessarily to speed the process or increase the number of bills, but to engage a wider circle of stakeholders, support thoughtful deliberation, and improve the quality of the resulting legislation.
What are the problems here in such a democratic process online or even in a modern context?
People who aren't actually stakeholders feel that they're stakeholders and want to control other's actions even when they don't have a stake. (eg: abortion)
People don't have time to become properly informed about the ever-increasing group of topics and there is too much disinformation and creation of fear, uncertainty and doubt.
Thoughtful deliberation does not happen.
The quality of legislation has dropped instead of increased.
Bikeshedding is too easy.
What if instead of electing people who run, we elected people from the electorate at random? This would potentially at least nudge us to have some representation by "one of the least of these". This would provide us to pay more attention to a broader swath of society instead of the richest and most powerful. What might the long term effects of this be?
-
Finding relevant information and understanding it well enough to integrate it into existing knowledge requires intense commitment and concentration.
-
The current mass media such as t elevision, books, and magazines are one-directional, and are produced by a centralized process. This can be positive, since respected editors can filter material to ensure consistency and high quality, but more widely accessible narrowcasting to specific audiences could enable livelier decentralized discussions. Democratic processes for presenting opposing views, caucusing within factions, and finding satisfactory compromises are productive for legislative, commercial, and scholarly pursuits.
Social media has to some extent democratized the access to media, however there are not nearly enough processes for creating negative feedback to dampen ideas which shouldn't or wouldn't have gained footholds in a mass society.
We need more friction in some portions of the social media space to prevent the dissemination of un-useful, negative, and destructive ideas swamping out the positive ones. The accelerative force of algorithmic feeds for the most extreme ideas in particular is one of the most caustic ideas of the last quarter of a century.
-
Since any powerful tool, such as a genex, can be used for destructive purposes, the cautions are discussed in Section 5.
Given the propensity for technologists in the late 90s and early 00s to have rose colored glasses with respect to their technologies, it's nice to see at least some nod to potential misuses and bad actors within the design of future tools.
Tags
- evolution of knowledge
- time
- technology for destruction
- self-publishing
- information overload
- bikeshedding
- subversion of democracy
- legislation
- user interface
- human resources
- legislating thought
- Weapons of Math Destruction
- new media
- personal knowledge management
- democracy
- social media
- democratization of publishing
- techno-utopianism
- one of the least of these
- publishing
- genex
- cautionary tales
- technology
- algorithmic feeds
Annotators
URL
-
-
inst-fs-iad-prod.inscloudgate.net inst-fs-iad-prod.inscloudgate.net
-
Capitalization conveys a certain distinction, the elevated position of humans and their creations in the hierarchy of beings. Biologists have widely adopted the convention of not capital-izing the common names of plants and animals unless they include the name of a human being or an official place name. Thus, the first blossoms of the spring woods are written as bloodroot and the pink star of a California woodland is Kellogg’s tiger lily. This seemingly trivial grammatical rulemaking in fact expresses deeply held assump-tions about human exceptionalism, that we are somehow different and indeed better than the other species who surround us. Indigenous ways of understanding recognize the personhood of all beings as equally important, not in a hierarchy but a circle.
Rules for capitalization in English give humans elevated hierarchical positions over animals, plants, insects, and other living things. We should revise this thinking and capitalize words like Maple, Heron, and Mosquito when we talking of beings and only use only use the lower case when referring to broad categories or concepts like maples, herons, and humans.
-
-
www.allenandunwin.com www.allenandunwin.com
-
The First Astronomers: How Indigenous Elders read the stars by Duane Hamacher, with Elders and Knowledge Holders
<small><cite class='h-cite via'>ᔥ <span class='p-author h-card'>LynneKelly</span> in Un-Stupiding Myself - a Memory Training Journal - Memory Training Journals - Art of Memory Forum (<time class='dt-published'>03/14/2022 18:43:38</time>)</cite></small>
-
-
en.wiktionary.org en.wiktionary.org
-
https://en.wiktionary.org/wiki/idle_hands_are_the_devil%27s_workshop
Proverbs 16:27 "Scoundrels concoct evil, and their speech is like a scorching fire." (Oxford, NSRV, 5th Edition) is translated in the King James version as "An ungodly man diggeth up evil: and in his lips there is as a burning fire." The Living Bible (1971) translates this section as "Idle hands are the devil’s workshop; idle lips are his mouthpiece."
The verse may have inspired St. Jerome to write "fac et aliquid operis, ut semper te diabolus inveniat occupatum" (translation: "engage in some occupation, so that the devil may always find you busy.”) This was repeated in The Canterbury Tales which may have increased its popularity.
-
-
-
Elinor Ostrom
-
the tragedy of the commons is a multiplayer prisoner's dilemma. And she said that people are only prisoners if they consider themselves to be. They escape by creating institutions for collective action. And she discovered, I think most interestingly, that among those institutions that worked, there were a number of common design 00:12:04 principles, and those principles seem to be missing from those institutions that don't work.
collaborative institutions relying on common design principles are seen helping to avoid the tragedy of commons
-
-
psyarxiv.com psyarxiv.com
-
Böhm, Robert, Cornelia Betsch, Yana Litovsky, Philipp Sprengholz, Noel Brewer, Gretchen Chapman, Julie Leask, et al. ‘Crowdsourcing Interventions to Promote Uptake of COVID-19 Booster Vaccines’. PsyArXiv, 10 February 2022. https://doi.org/10.31234/osf.io/n5b6x.
-
-
acestoohigh.com acestoohigh.com
-
This was Hitler’s OWN PERSONAL BRAND OF MANIA. And it is traceable to the insecurity of his existence in his own family, the insecurity of a child constantly living under the threat of violence and humiliation. Later millions were to forfeit their lives so that this child – now a childless adult – could avenge himself by unconsciously projecting the grim scenario of his childhood onto the political stage.
Hitler's unhealed trauma induced the death of millions of other lives, continuing a cycle of trauma.
-
-
www.reseau-canope.fr www.reseau-canope.fr
-
En somme, les études sur la communication des élèves atteints d’autisme permettent de mettre en évidence l’importance d’un contexte riche en stimulations appropriées (sons et images), mais également une évidente « stabilité » de l’information à décoder, le suivi des émotions des personnages, le rôle de l’imitation dans les apprentissages. Ces résultats encouragent donc l’usage d’outils informatiques adéquats pour améliorer la communication sociale chez les enfants atteints d’autisme.
L'association de deux sujets qui n'ont pas de corrélation vérifiéé, revient dans la conclusion en contradiction avec la conclusion de l'étude de Ramdoss, S et al.
-
Nous allons montrer par une courte analyse de quelques études l’impact du travail éducatif informatisé dans l’apprentissage de la communication sociale chez des enfants atteints d’autisme.
En contradiction avec l'hypothèse :
Results suggest that CBI should not yet be considered a researched-based approach to teaching communication skills to individuals with ASD. However, CBI does seem a promising practice that warrants future research. Les résultats suggèrent que le CBI ne devrait pas encore être considéré comme un approche fondée sur la recherche pour enseigner les compétences en communication aux personnes ayant Troubles du Spectre Autistique. Cependant, le CBI semble être une pratique prometteuse qui justifie des recherches futures.
Tags
- Ramdoss, S., Lang, R., Mulloy, A., Franco, J., O’Reilly, M., Didden, R., & Lancioni, G. (2010a). Use of Computer-Based Interventions to Teach Communication Skills to Children with Autism Spectrum Disorders : A Systematic Review. Journal of Behavioral Education, 20(1), 55‑76. https://doi.org/10.1007/s10864-010-9112-7
- Ramdoss, S., Lang, R., Mulloy, A., Franco, J., O’Reilly, M., Didden, R., & Lancioni, G. (2010b). Use of Computer-Based Interventions to Teach Communication Skills to Children with Autism Spectrum Disorders : A Systematic Review. Journal of Behavioral Education, 20(1), 55‑76. https://doi.org/10.1007/s10864-010-9112-7
Annotators
URL
-
-
www.edwardtufte.com www.edwardtufte.com
-
The report is 33 slides long; yet about 10 slide-equivalents are essentially content-free (compulsive repetitive branding, twiddly hierarchical organization, empty space, assorted title pages, and so on). This PP fluffed-up material here and quite a bit more could easily be placed in a technical report on 4 pages of an 11" by 17" piece of paper (folded in half)
-
One does not read a printout of someone's two-month old PowerPoint slides, one guesses, decodes, and attempts to glean meaning from the series of low-resolution titles, bullets, charts, and clipart. At least they do that for a while...until they give up. With a written document, however, there is no reason for shallowness or ambiguity (assuming one writes well).
-
-
mcdreeamiemusings.com mcdreeamiemusings.com
-
The Board views the endemic use of PowerPoint briefing slides instead of technical papers as an illustration of the problematic methods of technical communication at NASA.
-
-
niklasblog.com niklasblog.com
-
Best Instrumental Hindi Songs of All time
The loud piece of sufiscore Best Instrumental Hindi Songs of All time is given out "sahityam" and sahityam is actually like singing the swaras certainly at any rate using the spaces of the tune. The songs of Samaveda contain melodic substance, plan, beat and metric association. This game plan is, regardless, not extraordinary or limited to Samaveda. Best Instrumental Hindi Songs of All time has two focal parts, raga and tala. The raga, considering a varied assortment of swara, structures the outside of a profoundly many-sided melodic course of action, while the tala evaluates the time cycle. The raga gives a specialist a reach to cultivate the tune from sounds, while the tala outfits them with an innovative construction for cadenced unconstrained creation using time. In Best Instrumental Hindi Songs of All time music, the space between the notes is habitually more fundamental than the authentic notes, and it generally avoids Western customary examinations like concordance, inconsistency, harmonies, or change. The foundation of Best Instrumental Hindi Songs of All time in old India are found in the Vedic association of Hinduism. The earliest Indian thought joined three clarifications, syllabic show, melos and dance. As these fields were made, sangeeta changed into a verifiable kind of workmanship, in an advancement muddled from contemporary music. Sufiscore Best Instrumental Hindi Songs of All time is the old style music of the Indian subcontinent. It has two gigantic practices: the North Indian conventional music custom is called Hindustani, while the South Indian verbalization is called Carnatic. These practices were not irrefutable until about the fifteenth century. Best Instrumental Hindi Songs of All time underlines unrehearsed creation and evaluation of all pieces of a raga, while Carnatic grandstands will overall be short connection based. Regardless, the two plans continue to have more common features than contrasts. The central establishments of the Best Instrumental Hindi Songs of All time of India are found in the Vedic game plan of Hinduism and the obsolete Natyashastra, the magnificent Sanskrit text on execution verbalizations by Bharata Muni. The thirteenth period Sanskritic language text Sangita-Ratnakara of Sarangadeva is seen as the convincing substance by both the Hindustani music and the Carnatic music customs.
-
-
www.bbc.com www.bbc.com
-
quarter of the key nutrients used in European food production come from Russia.
Sorld is dangerously dependent on an aggressor nation’s supply of fertilizer.
-
-
-
Such a flexible concept allows for a meshing of Russian state interests with claims to be acting to protect a diversity of ethnic and linguistic communities outside Russia. It also negates the idea of other legitimate national communities that could underpin states in the region.
Flexible explanations or motivations are bad -- they can justify nearly anything and undermine contrary arguments.
-
-
docdrop.org docdrop.org
-
A few people are asking about the link to the climate crisis, particularly when it relates to the energy flows. Like, Europe is very dependent, part of Europe, is very dependent on Russian oil and gas, which is, as far as we know, still flowing until today. But could this crisis, in a sort of paradoxical way, 00:40:22 a bit like the pandemic, accelerate climate action, accelerate renewables and and so on? YNH: This is the hope. That Europe now realizes the danger and starts a green Manhattan Project that kind of accelerates what already has been happening, but accelerates it, the development of better energy sources, 00:40:49 better energy infrastructure, which would release it from its dependence on oil and gas. And it will actually undercut the dependence of the whole world on oil and gas. And this would be the best way to undermine the Putin regime and the Putin war machine, because this is what Russia has, oil and gas. 00:41:13 That's it. When was the last time you bought anything made in Russia? They have oil and gas, and we know, you know, the curse of oil. That oil is a source of riches, but it’s also very often a support for dictatorships. Because to enjoy the benefits of oil, you don't need to share it with your citizens. 00:41:38 You don't need an open society, you don't need education, you just need to drill. So we see in many places that oil and gas are actually the basis for dictatorships. If oil and gas, if the price drops, if they become irrelevant, it will not only undercut the finance, the power of the Russian military machine, it will also force Russia, force Putin or the Russians to change their regime.
This is the key strategy relating dictatorship, the fossil fuel industry and climate change. We can solve multiple crisis all at once by rapidly phasing out fossil fuels.
fossil fuels have this other huge footprint of the impacts of authoritarianism.
-
If humans, some humans, start making bad decisions and start destroying the institutions that kept the peace, then we will be back in the era of war with budgets, military budgets going to 20, 30, 40 percent. It can happen. It's in our hands.
An economic diversion of this scale would make it far more likely that humanity will not be able to prevent, but indeed accelerate planetary tipping points! Hence the urgency of this crisis for the climate movement. This implies that the climate movement and the antiwar movement must now synchronize resources and form a coherent, unified strategy
-
You wrote another essay last week in “The Economist”, and you argue that what's at stake in Ukraine is, and I quote you, "the direction of human history" because it puts at risk what you call the greatest political and moral achievement of modern civilization, 00:18:31 which is the decline of war. So now we are back in a war and potentially afterwards into a new form of cold war or hot war, but hopefully not.
This is why Ukraine is not just a localized problem, but the problem for humanity going forward.
-
I think another very important thing is what has been dividing the West over the several years now, it’s what people term the “culture war”. The culture war between left and right, between conservatives and liberals. And I think this war can be an opportunity to end the culture war within the West, to make peace in the culture war. 00:15:59 First of all, because you suddenly realize we are all in this together. There are much bigger things in the world than these arguments between left and right within the Western democracies. And it's a reminder that we need to stand united to protect Western liberal democracies. But it's deeper than that. 00:16:22 Much of the argument between left and right seemed to be in terms of a contradiction between liberalism and nationalism. Like, you need to choose. And the right goes with nationalism, and the left goes more liberalism. And Ukraine is a reminder that no, the two actually go together. Historically, nationalism and liberalism are not opposites. 00:16:47 They are not enemies. They are friends, they go together. They meet around the central value of freedom, of liberty. And to see a nation fighting for its survival, fighting for its freedom, you see it on Fox News or you see it in CNN. And yes, they tell the story a little differently, but they suddenly see the same reality. 00:17:14 And they find common ground. And the common ground is to understand that nationalism is not about hating minorities or hating foreigners, it's about loving your compatriots, and reaching a peaceful agreement about how we want to run our country together. And I hope that seeing what is happening would help to end the culture war in the West.
Harari makes a very astute observation here. This is an opportunity to reflect on the divisiveness of the culture wars. The acceleration of the culture wars is, in fact no accident, but directly related to Putin's information warfare on the West, especially the election and support of Trump in the US and Johnson in the UK.
-
I hope, for the sake of everybody -- Ukrainians, Russians and the whole of humanity -- that this war stops immediately. Because if it doesn't, it's not only the Ukrainians and the Russians 00:11:39 that will suffer terribly. Everybody will suffer terribly if this war continues. BG: Explain why. YNH: Because of the shock waves destabilizing the whole world. Let’s start with the bottom line: budgets. We have been living in an amazing era of peace in the last few decades. And it wasn't some kind of hippie fantasy. You saw it in the bottom line. 00:12:06 You saw it in the budgets. In Europe, in the European Union, the average defense budget of EU members was around three percent of government budget. And that's a historical miracle, almost. For most of history, the budget of kings and emperors and sultans, like 50 percent, 80 percent goes to war, goes to the army. 00:12:31 In Europe, it’s just three percent. In the whole world, the average is about six percent, I think, fact-check me on this, but this is the figure that I know, six percent. What we saw already within a few days, Germany doubles its military budget in a day. And I'm not against it. Given what they are facing, it's reasonable. For the Germans, for the Poles, for all of Europe to double their budgets. And you see other countries around the world doing the same thing. 00:12:58 But this is, you know, a race to the bottom. When they double their budgets, other countries look and feel insecure and double their budgets, so they have to double them again and triple them. And the money that should go to health care, that should go to education, that should go to fight climate change, this money will now go to tanks, to missiles, to fighting wars. 00:13:25 So there is less health care for everybody, and there is maybe no solution to climate change because the money goes to tanks. And in this way, even if you live in Australia, even if you live in Brazil, you will feel the repercussions of this war in less health care, in a deteriorating ecological crisis, 00:13:48 in many other things. Again, another very central question is technology. We are on the verge, we are already in the middle, actually, of new technological arms races in fields like artificial intelligence. And we need global agreement about how to regulate AI and to prevent the worst scenarios. How can we get a global agreement on AI 00:14:15 when you have a new cold war, a new hot war? So in this field, to all hopes of stopping the AI arms race will go up in smoke if this war continues. So again, everybody around the world will feel the consequences in many ways. This is much, much bigger than just another regional conflict.
Harari makes some excellent points here. Huge funds originally allocated to fighting climate change and the other anthropocene crisis will be diverted to military spending. Climate change, biodiversity, etc will lose. Only the military industrial complex will win.
Remember that the military industry is unique. It's only purpose is to consume raw materials and capacity in order to destroy. What is the carbon footprint of a bomb or a bullet?
-
The key issue of the war, at least for President Putin, is whether Ukraine is an independent nation, whether it is a nation at all. He has this fantasy that Ukraine isn't a nation, that Ukraine is just a part of Russia, that Ukrainians are Russians. In his fantasy, Ukrainians are Russians that want to be back in the fold of Mother Russia, 00:02:43 and that the only ones preventing it is a very small gang at the top, which he portrays as Nazis, even if the president is Jewish; but OK, a Nazi Jew.
If the people of Russia know that the president of Ukraine is a jew, Putin's entire story collapses.So do the people of Russia actually know this? And if so, what is their response? Does confirmation bias even refute that absurdity?
Tags
- significance of the Russian invasion.
- multiple benefits of decarbonizing
- end of culture wars
- culture wars
- the whole world loses
- Impact of Putin's war on climate change
- contradiction of de-nazification
- escalation of military budgets
- anti-war and climate movement unity
- carbon footprint of war
Annotators
URL
-
-
www.theguardian.com www.theguardian.com
-
Each highlighted statement expresses political talking points aligned to induce trump-like support.
Trump introduced new marketing and strategy, formulated using concepts and metrics mastered by Reality TV and Hollywood and then paired with advertising propaganda and "selling" techniques to create a "Brand". This is after-all Donald Trump, this is what he does, has done and is the only way he has found to make money. Trump built the "brand" (just barely) while teetering on self destruction.
His charismatic persona became "the glue" that allowed creative narratives to stick to certain types of people in-spite of risk. Trump learned OTJ how to capture a specific type of audience.
The mistake people make about Trump is assuming his audience to be "Joe Six-Pack", redneck's with limited education! This assumption does not have merit on its own.<br /> * There is a common "follower" theme among his audience that is exploited by those who: * Bought the "licensing rights" to the master-class Trump "how-to" course.
Tags
- Politics
- Trump licensed how-to
- Putin-Trump
- Trump
- Smoke and Mirrors
- Savvy Strongman
- Creation of Brand
- Used Car salesman
- Reality TV
- Modern day Politician
- Trump Audience
- PR
- BS
- Multi-Level-Marketing
- Manipulation
- MLM
- Prosperity Preachers
- Snake-oil salesmen
- Professional Wrestling
- Mafia
- Vladimir Putin
Annotators
URL
-
- Feb 2022
-
lincolnquirk.com lincolnquirk.com
-
If you put a bunch of research into designing a really great product and it succeeds but gets effectively copied by low-cost clones, you’ll be sad. I am not sure how to defend this, and I think it is probably the weakest point of this business model;
By getting to economies of scale faster than other people can?
-
-
niklas-luhmann-archiv.de niklas-luhmann-archiv.de
-
9/8g Hinter der Zettelkastentechnik steht dieErfahrung: Ohne zu schreiben kann mannicht denken – jedenfalls nicht in anspruchsvollen,selektiven Zugriff aufs Gedächtnis voraussehendenZusammenhängen. Das heißt auch: ohne Differenzen einzukerben,kann man nicht denken.
Google translation:
9/8g The Zettelkasten technique is based on experience: You can't think without writing—at least not in contexts that require selective access to memory.
That also means: you can't think without notching differences.
There's something interesting about the translation here of "notching" occurring on an index card about ideas which can be linked to the early computer science version of edge-notched cards. Could this have been a subtle and tangential reference to just this sort of computing?
The idea isn't new to me, but in the last phrase Luhmann tangentially highlights the value of the zettelkasten for more easily and directly comparing and contrasting the ideas on two different cards which might be either linked or juxtaposed.
Link to:
- Graeber and Wengrow ideas of storytelling
-
Shield of Achilles and ekphrasis thesis
-
https://hypothes.is/a/I-VY-HyfEeyjIC_pm7NF7Q With the further context of the full quote including "with selective access to memory" Luhmann seemed to at least to make space (if not give a tacit nod?) to oral traditions which had methods for access to memories in ways that modern literates don't typically give any credit at all. Johannes F.K .Schmidt certainly didn't and actively erased it in Niklas Luhmann’s Card Index: The Fabrication of Serendipity.
-
-
darekkay.com darekkay.com
-
This tool requires Node
shouldn't
-
-
bvsd.schoology.com bvsd.schoology.com
-
-
Greenland’s Melting Ice Is No Cause for Climate-Change Panic
Overall scientific credibility: 'very low' according to the scientists who analyzed this article.
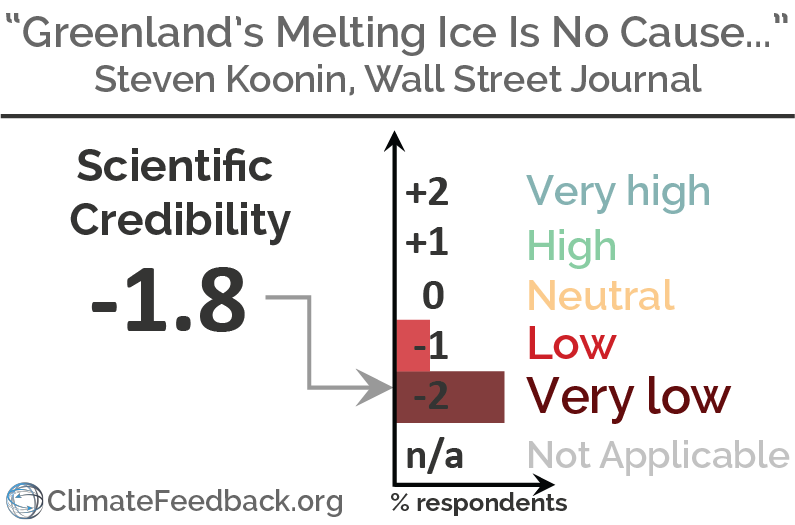
Find more details in Climate Feedback's analysis
-
-
sites.google.com sites.google.com
-
Now wave your flagNow wave your flag
The repetition of these phrase shows how he will leave people passionate about something and encourage them to soar up high like a waving flag

Tags
Annotators
URL
-
-
arstechnica.com arstechnica.com
-
Google killed SG&E about one year after Stadia launched, before the studio had released a game or done any public work. In a blog post announcing Stadia's pivot to a "platform technology," Stadia VP Phil Harrison explained the decision to shutter SG&E, saying, "Creating best-in-class games from the ground up takes many years and significant investment, and the cost is going up exponentially."
I suspect Google wanted faster, more measurable results than is possible with game development. There's a reason why tech companies are vastly more profitable than game companies.
I don't particularly see the shame in changing a strategy that isn't working. As an early user of Stadia I do see the lost potential though, maybe that's where this is coming from.
-
-
pennmaterialtexts.org pennmaterialtexts.org
-
https://pennmaterialtexts.org/homepage
How awesome looking is this? Note the regular online meetings/presentations and the backlog of videos on their YouTube channel: https://www.youtube.com/channel/UC8Ng6px3fgc4Yjw-en1GcsA
-
-
www.baltimoresun.com www.baltimoresun.com
-
Pretending we were all the same never worked, because it ignored the fact that we’re not all given the same opportunities to succeed or fail on our merits; some are privileged, others are oppressed. Refusing to recognize that only prolonged difficult conversations and much-needed soul-searching, dooming more generations to repeat the cycle.
Tags
- myth of meritocracy
- quotes
- institutional racism
- colorblind
- diversity equity and inclusion
- privilege
- oppression
Annotators
URL
-
-
twitter.com twitter.com
-
Hmm...this page doesn’t exist. Try searching for something else.
Apparently Persuall was embarrassed about their pro-surveillance capitalism stance and perhaps not so much for its lack of kindness and care for the basic humanity of students.
Sad that they haven't explained or apologized for their misstep.
https://web.archive.org/web/20220222022208/https://twitter.com/perusall/status/1495945680002719751
Additional context: https://twitter.com/search?q=(%40perusall)%20until%3A2022-02-23%20since%3A2022-02-21&src=typed_query
-
-
thestarphoenix.com thestarphoenix.com
-
COVID-19 vaccine mandates a key issue in federal election campaign. (n.d.). Thestarphoenix. Retrieved February 22, 2022, from https://thestarphoenix.com/news/local-news/covid-19-vaccine-mandates-a-key-issue-in-federal-election-campaign
-
-
www.nature.com www.nature.com
-
Shelton, J. F., Shastri, A. J., Fletez-Brant, K., Stella Aslibekyan, & Auton, A. (2022). The UGT2A1/UGT2A2 locus is associated with COVID-19-related loss of smell or taste. Nature Genetics, 54(2), 121–124. https://doi.org/10.1038/s41588-021-00986-w
-
-
www.unige.ch www.unige.ch
-
https://www.unige.ch/callector/lara
example: https://www.issco.unige.ch/en/research/projects/callector/le_petit_prince_abc2vocabpages/hyperlinked_text.html
-
The basic approach is in line with Krashen's influential Theory of Input, suggesting that language learning proceeds most successfully when learners are presented with interesting and comprehensible L2 material in a low-anxiety situation.
Stephen Krashen's Theory of Input indicates that language learning is most successful when learners are presented with interesting and comprehensible material in low-anxiety situations.
-
-
blog.devgenius.io blog.devgenius.io
-
Currently you need to have Node and npm installed on your machine once this is done you can use it with the following command
There's no real reason why Node/NPM should be required for this. You could dump the logic into a bookworms.html file and run it in the JS runtime that's already on someone's machine (their Web browser)...
-
-
underpassapp.com underpassapp.com
-
underpassapp.com underpassapp.com
-
StopTheMadness is a web browser extension that stops web sites from making your browser harder to use
-
"The good news is that you can wrest control of your browser back from these malicious, control-freak sites."
-
-
www.sciencedirect.com www.sciencedirect.com
-
self-regulation of learning
-
-
www.theguardian.com www.theguardian.com
-
Yang, M. (2022, February 14). Arkansas jail’s ivermectin experiments recall historical medical abuse of imprisoned minorities. The Guardian. https://www.theguardian.com/us-news/2022/feb/14/arkansas-prison-covid-19-ivermectin-experiment-minorities-medical-abuse
-
-
www.iza.org www.iza.org
-
COVID-19 Vaccination Mandates and Vaccine Uptake. (n.d.). Retrieved February 16, 2022, from https://www.iza.org/publications/dp/14946/covid-19-vaccination-mandates-and-vaccine-uptake
-
-
www.abc.net.au www.abc.net.au
-
The idea of the index was invented twice in roughly 1230.
Once by Hugh of Saint-Cher in Paris as a concordance of the Bible. The notes towards creating it still exist in a variety of hands. The project, executed by a group of friars at the Dominican Friary of Saint-Jacques, listed 10,000 words and 129,000 locations.
The second version was invented by Robert Grosseteste in Oxford who used marginal marks to create a "grand table".
The article doesn't mention florilegium, but the head words from them must have been a likely precursor. The article does mention lectures and sermons being key in their invention.
<small><cite class='h-cite via'>ᔥ <span class='p-author h-card'>Aaron Davis</span> in 📑 Monks, a polymath and an invention made by two people at the same time. It’s all in the history of the index | Read Write Collect (<time class='dt-published'>02/15/2022 21:22:10</time>)</cite></small>
-
-
-
Dispatch a custom event. This differs from Svelte's component event system, because these events require a DOM element as a target, can bubble (and do by default), and are cancelable with event.preventDefault(). All SMUI events are dispatched with this instead of Svelte's createEventDispatcher.
-
This is especially useful for UI library components, as it is generally unknown which events will be required from them for all desired use cases. For example, if a Button component only forwards a click event, then no use case that requires the mouseover or the keypress event can be used with it.
-
-
Local file Local file
-
“Manipulations such as variation, spacing, introducing contextualinterference, and using tests, rather than presentations, as learningevents, all share the property that they appear during the learningprocess to impede learning, but they then often enhance learning asmeasured by post-training tests of retention and transfer. Conversely,manipulations such as keeping conditions constant and predictable andmassing trials on a given task often appear to enhance the rate oflearning during instruction or training, but then typically fail to supportlong-term retention and transfer” (Bjork, 2011, 8).
This is a surprising effect for teaching and learning, and if true, how can it be best leveraged. Worth reading up on and testing this effect.
Indeed humans do seem built for categorizing and creating taxonomies and hierarchies, and perhaps allowing this talent to do some of the work may be the best way to learn not only in the short term, but over longer term evolutionary periods?
-
his suggests that successful problem solvingmay be a function of flexible strategy application in relation to taskdemands.” (Vartanian 2009, 57)
Successful problem solving requires having the ability to adaptively and flexibly focus one's attention with respect to the demands of the work. Having a toolbelt of potential methods and combinatorially working through them can be incredibly helpful and we too often forget to explicitly think about doing or how to do that.
This is particularly important in mathematics where students forget to look over at their toolbox of methods. What are the different means of proof? Some mathematicians will use direct proof during the day and indirect forms of proof at night. Look for examples and counter-examples. Why not look at a problem from disparate areas of mathematical thought? If topology isn't revealing any results, why not look at an algebraic or combinatoric approach?
How can you put a problem into a different context and leverage that to your benefit?
-
We need to getour thoughts on paper first and improve them there, where we canlook at them. Especially complex ideas are difficult to turn into alinear text in the head alone. If we try to please the critical readerinstantly, our workflow would come to a standstill. We tend to callextremely slow writers, who always try to write as if for print,perfectionists. Even though it sounds like praise for extremeprofessionalism, it is not: A real professional would wait until it wastime for proofreading, so he or she can focus on one thing at a time.While proofreading requires more focused attention, finding the rightwords during writing requires much more floating attention.
Proofreading while rewriting, structuring, or doing the thinking or creative parts of writing is a form of bikeshedding. It is easy to focus on the small and picayune fixes when writing, but this distracts from the more important parts of the work which really need one's attention to be successful.
Get your ideas down on paper and only afterwards work on proofreading at the end. Switching contexts from thinking and creativity to spelling, small bits of grammar, and typography can be taxing from the perspective of trying to multi-task.
Link: Draft #4 and using Webster's 1913 dictionary for choosing better words/verbiage as a discrete step within the rewrite.
Linked to above: Are there other dictionaries, thesauruses, books of quotations, or individual commonplace books, waste books that can serve as resources for finding better words, phrases, or phrasing when writing? Imagine searching through Thoreau's commonplace book for finding interesting turns of phrase. Naturally searching through one's own commonplace book is a great place to start, if you're saving those sorts of things, especially from fiction.
Link this to Robin Sloan's AI talk and using artificial intelligence and corpuses of literature to generate writing.
-
You may remember from school the difference between an exergonicand an endergonic reaction. In the first case, you constantly need toadd energy to keep the process going. In the second case, thereaction, once triggered, continues by itself and even releasesenergy.
The build up of complexity which results in the creation of life with increasing complexity must certainly be endergonic if the process is to last for any extensive length of time. Once the process becomes exergonic or reaches homeostasis, then the building of complexity and even life itself will cease to exist.
Must this always be true? Proof? Counter examples?
Tags
- ITBio
- open questions
- hierarchies
- dictionaries
- Draft #4
- problem solving
- play
- perspective
- books of quotations
- Webster's dictionary
- human resources
- words matter
- types of focus
- taxonomies
- there's more than one way to skin a cat
- artificial intelligence
- context shifts
- commonplace books
- mathematics
- associative memory
- evolution of order
- Robin Sloan
- exergonic reactions
- Henry David Thoreau
- modality shifts
- proofreading
- play based learning
- bikeshedding
- creativity
- writing process
- phrasing
- attention
- pedagogy
- waste books
- endergonic reactions
- learning
- combinatorial creativity
- creative writing
- quotes
- origin of life
- focus
- complexity
Annotators
-
-
Local file Local file
-
Starosielski (2021) - The Politics of Cable Supply from the British Empire to Huawei Marine - https://is.gd/8LgG2R - urn:x-pdf:dce28e61ffb8c3b2ecc2b99241b1d22a
-
-
www.scientificamerican.com www.scientificamerican.com
-
We added a mechanism for the variable motion of the sun and an epicyclic mechanism for calculating the “nodes” of the moon—the points at which the moon’s orbit cuts through the plane of the ecliptic, making an eclipse possible. Eclipses happen only when the sun is close to one of these nodes during a full or new moon. Medieval and renaissance astronomers called a double-ended pointer for the nodes of the moon a “dragon hand.” The epicyclic gearing for this dragon hand also exactly explained a prominent bearing on one of the spokes that had previously appeared to have no function.
The nodes of the moon are the points at which the moon's orbit cuts through the plane of the ecliptic. These nodes make an eclipse possible and they happen only when the sun is close to one of these nodes during either a full or a new moon.
Medieval and renaissance astronomers called a double-ended pointer for the nodes of the moon a "dragon hand".
-
-
reallifemag.com reallifemag.com
-
https://reallifemag.com/rank-and-file/
An interesting example of someone who fell into the trap of thinking that a particular tool or tools would magically make them smarter or help them do a particular line of work without showing any deep evidence of knowing what they were doing. The discussion here flows over a number of mixed note taking domains with no clear thrust for what they were using it pointedly for. The multiple directions and lack of experience likely doomed them to failure here.
-
This is a widespread mistake among those who think that a sexy note-taking app like Roam will suddenly free their minds, or that they can train themselves into geniuses with enough spaced repetition, or that they can build a zettelkasten capable of thinking original thoughts for them.
Thinking that the tool will solve a particular problem without knowing what the tool does or how to use it properly will surely set one up for failure. You can use a screwdriver like a hammer, but your results won't be as good as using a hammer and using it properly.
-
-
Local file Local file
-
Research is needed to determine the situations in which the redundancy principle does not hold
p. 144-145
The authors describe limits to the research (circa 2016) as follows: 1. Kinds of learners, 2. kinds of material, and 3. kinds of presentation methods. Each of these situations present interesting possibilities for research related to the use of closed captions used by first-year law students while watching course-related videos.
When considering how "kinds of learners" might be relevant, the authors ask how redundant on-screen text might hurt or help non-native speakers of a language or learners with very low prior knowledge. It is probably reasonable to consider first-year law students as having "very low prior knowledge". Is there any sense in which those same students could be understand as having overlapping characteristics with TBD
-
Principle 2: Consider Adding On‐Screen Text to Narration in Special Situations
p. 139-141
Clark and Mayer describe a key exception to the first principle they describe. One of the special situations they describe consists of when a learner must "exert greater cognitive effort to comprehend spoken text rather than printed text" (p. 140). This could be when the verbal material is complex and challenging, such as when learners are learning another language or when terminology is challenging such as might be encountered in scientific, technical, or legal(?) domains (p. 141).
[P]rinting unfamiliar technical terms on the screen may actually reduce cognitive processing because the learner does not need to grapple with decoding the spoken words.
However, it may be necessary to ensure that video is slow-paced or learner-controlled under circumstances where both audio narration and on-screen text are provided. Mayer, Lee, and Peebles (2014) found that when video is fast-paced, redundant text can cause cognitive overload, even when learners are non-native speakers.
Mayer, R. E., Lee, H., & Peebles, A. (2014). Multimedia Learning in a Second Language: A Cognitive Load Perspective. Applied Cognitive Psychology, 28(5), 653–660. https://doi.org/10.1002/acp.3050
-
boundary conditions.
p. 131-132
Clark and Mayer provide a brief summary of the boundary conditions, the situations in which learners benefit from the use redundant on-screen text. These situations include adding printed text when 1) there are no graphics, 2) the presentation rate of the on-screen text is slow or learner-controlled, 3) the narration includes technical or unfamiliar words, and the 3) on-screen text is shorter than the audio narration.
The first three conditions described bear some similarity to closed caption use by students in legal education watching class lecture videos, especially students in first-year courses. Typically, the students are viewing videos with very few detailed graphics, they have control over the speed, pause, review, and advance features of the video player, and the narration provides numerous legal terms.
Although closed captions are intended for hard of hearing and deaf viewers, they may have some benefits for other learners if the boundary conditions described by the authors turn out to be true. Dello Stritto and Linder (2017) shared findings from a large survey of post-secondary students reporting that a range of students found closed captions to be helpful.
Dello Stritto, M. E., & Linder, K. (2017). A Rising Tide: How Closed Captions Can Benefit All Students. Educause Review Online. https://er.educause.edu:443/articles/2017/8/a-rising-tide-how-closed-captions-can-benefit-all-students
-
graphics using words in both on‐screen text and audio narration in which the audio repeats the text. We call this technique redundant on‐screen text because the printed text (on‐screen text) is redundant with the spoken text (narration or audio).
Clark and Mayer provide a definition of redundant: Graphics accompanied by words in both on-screen text and audio narration in which that text is repeated. p. 131
The authors go on to provide guidance about concurrent graphics, audio, and on-screen text. Based upon the research that they summarize in Chapter Seven, they advise instructors not to add printed text to an on screen graphic.
p. 131
-
-
bvsd.schoology.com bvsd.schoology.com
-
workshift.opencampusmedia.org workshift.opencampusmedia.org
-
A study released today from the nonprofit Burning Glass Institute found that among new hires at leading firms such as Facebook, Apple, Microsoft, and Google, the share of positions in job postings requiring a bachelor’s degree remains extremely high. “There are a whole bunch of tech companies that continue to be pretty reliant on degrees,”
Skills-based is growing in adoption. And degrees still matter.
-
-
www.latimes.com www.latimes.com
-
Riverside teacher who dressed up and mocked Native Americans for a trigonometry lesson involving a mnemonic using SOH CAH TOA in Riverside, CA is fired.
There is a right way to teach mnemonic techniques and a wrong way. This one took the advice to be big and provocative went way overboard. The children are unlikely to forget the many lessons (particularly the social one) contained here.
It's unfortunate that this could have potentially been a chance to bring indigenous memory methods into a classroom for a far better pedagogical and cultural outcome. Sad that the methods are so widely unknown that media missed a good teaching moment here.
referenced video:
https://www.youtube.com/watch?v=Bu4fulKVv2c
A snippet at the end of the video has the teacher talking to rocks and a "rock god", but it's extremely unlikely that she was doing so using indigenous methods or for indigenous reasons.
read: 7:00 AM
-
-
www.ncbi.nlm.nih.gov www.ncbi.nlm.nih.gov
-
Afkhami, S., D’Agostino, M. R., Zhang, A., Stacey, H. D., Marzok, A., Kang, A., Singh, R., Bavananthasivam, J., Ye, G., Luo, X., Wang, F., Ang, J. C., Zganiacz, A., Sankar, U., Kazhdan, N., Koenig, J. F. E., Phelps, A., Gameiro, S. F., Tang, S., … Xing, Z. (2022). Respiratory mucosal delivery of next-generation COVID-19 vaccine provides robust protection against both ancestral and variant strains of SARS-CoV-2. Cell, S0092867422001453. https://doi.org/10.1016/j.cell.2022.02.005
-
-
www.sciencedirect.com www.sciencedirect.com
-
Chatterjee, D., Tauzin, A., Marchitto, L., Gong, S. Y., Boutin, M., Bourassa, C., Beaudoin-Bussières, G., Bo, Y., Ding, S., Laumaea, A., Vézina, D., Perreault, J., Gokool, L., Morrisseau, C., Arlotto, P., Fournier, É., Guilbault, A., Delisle, B., Levade, I., … Finzi, A. (2022). SARS-CoV-2 Omicron Spike recognition by plasma from individuals receiving BNT162b2 mRNA vaccination with a 16-weeks interval between doses. Cell Reports, 0(0). https://doi.org/10.1016/j.celrep.2022.110429
-
-
github.com github.com
-
Is the name "delegated type" up for review? I don't see any delegation happening in the code. It looks more like a "subtype", or "secondary type", or something like that.
-
-
www.gotquestions.org www.gotquestions.org
-
God sees me as His child (cf. John 1:12–13). This is “to the praise of [God’s] glorious grace, with which he has blessed us in the Beloved” (Ephesians 1:6). In Christ God sees me in love, and He lavishes upon me His abundant gifts and the “riches of his grace” (verses 7–8).
God of his rich grace found the ransom price, and gave his Son, as well as he gave himself, his life, a ransom for many; and how much soever it cost Christ to procure redemption and pardon, they are free to his people; who are redeemed without money and price of theirs, and whose sins are forgiven freely for Christ's sake.
-
-
www.joshmcarthur.com www.joshmcarthur.com
-
Remember, our wizard controller is responsible for showing and updating steps, but our top-level controller is still responsible for managing our Pet models.
-
-
github.com github.com
-
The goal of this gem is to reduce the amount of code that needs to be written when developing a ruby on rails website.
-
-
news.ycombinator.com news.ycombinator.com
-
and keep your site consistent
But maybe you don't need to do that. Maybe it would be instructive to take lessons from the traditional (pre-digital) publishing industry and consider how things like "print runs" and "reissues" factored in.
If you write a blog post in 2017 and the page is acceptable*, and then five years later you're publishing a new post today in 2022 under new design norms and trying to retrofit that design onto your content from 2017, then that sounds a lot like a reprint. If that makes sense and you want to go ahead and do that, then fair enough, but perhaps first consider whether it does make sense. Again, that's what you're doing—every time you go for a visual refresh, it's akin to doing a new run for your entire corpus. In the print industry (even the glossy ones where striking a chord visually was and is something considered to merit a lot of attention), publishers didn't run around snapping up old copies and replacing them with new ones. "The Web is different", you might say, but is it? Perhaps the friction experienced here—involved with the purported need to pick up a static site generator and set your content consistently with templates—is actually the result of fighting against the natural state of even the digital medium?
* ... and if you wrote a blog post in 2017 and the page is not acceptable now in 2022, maybe it's worth considering whether it was ever really acceptable—and whether the design decisions you're making in 2022 will prove to be similarly unacceptable in time (and whether you should just figure out the thing where that wouldn't be the case, and instead start doing that immediately).
-
-
www.harpweek.com www.harpweek.com
-
The cartoon also has the specific aim of endorsing ratification of the Fifteenth Amendment to the U.S. Constitution, which was intended to guarantee that federal voting rights could not be denied on the basis of race.
I think Thomas Nast really did do a good job depicting the message that was intended. The drawing which showed and displayed America as a melting pot, where everyone is seated comfortably and has a seat at the table. It shows that we all make up what America is today and that the diversity of our nation is what makes it beautiful, and that since we all make America what it is, we all should have the same equal rights.
-
-
www.thelancet.com www.thelancet.com
-
Wong, S.-C., Au, A. K.-W., Chen, H., Yuen, L. L.-H., Li, X., Lung, D. C., Chu, A. W.-H., Ip, J. D., Chan, W.-M., Tsoi, H.-W., To, K. K.-W., Yuen, K.-Y., & Cheng, V. C.-C. (2022). Transmission of Omicron (B.1.1.529) - SARS-CoV-2 Variant of Concern in a designated quarantine hotel for travelers: A challenge of elimination strategy of COVID-19. The Lancet Regional Health – Western Pacific, 18. https://doi.org/10.1016/j.lanwpc.2021.100360
-
-
twitter.com twitter.com
-
AbScent. (2022, February 7). the study quoted here looked at an 18 month time interval. In our Covid19 FB group of 34.5k, we have reports of recovery after 18 months—2 years is not unknown @Dr_Ellie @MailOnline https://t.co/5DdXDWLBSQ [Tweet]. @AbScentUK. https://twitter.com/AbScentUK/status/1490636119322644484
-
-
-
Indeed, the Jose-phinian card index owes its continued use to the failure to achieve a bound
catalog, until a successor card catalog comes along in 1848. Only the<br /> absence of a bound repertory allows the paper slip aggregate to answer all inquiries about a book ’ s whereabouts after 1781. Thus, a failed undertaking tacitly turns into a success story.
The Josephinian card index was created, in part on the ideas of Konrad Gessner's slip method, by accumulating slips which could be rearranged and then copied down permanently. While there was the chance that the original cards could be disordered, the fact that the approximately 300,000 cards in 205 small boxes were estimated to fill 50 to 60 folio volumes with time and expense to print it dissuaded the creation of a long desired compiled book of books. These problems along with the fact that new books being added later was sure to only compound problems of having a single reference. This failure to have a bound catalog of books unwittingly resulted in the success of the index card catalog.
-
You may say that it isn ’ t necessary to read every last book. Well, it ’ s also true that in war you don ’ t have to kill every last soldier, but we still need every one of them. — General Stumm von Bordwehr, in Robert Musil, The Man without Qualities
-
-
every.to every.to
-
I learned from using those Macs early on that form is always malleable. This became even more apparent when the web came into the picture. Think about it: there’s no way to make a web page or a blog that is not an act of playing with its form at the same time as you're creating its content. So it just seemed natural: the world was always telling me that you worked on those two things – the container and its contents – together.
There is a generation of people who grew up at the edge of the creation of computers and the web where they were simultaneously designing both the container and its contents at the same time. People before and after this typically worked on one or the other and most often on the contents themselves without access to the containers.
-
-
psyarxiv.com psyarxiv.com
-
Białek, Michał, Ethan Andrew Meyers, Patricia Arriaga, Damian Harateh, and Arkadiusz Urbanek. ‘COVID-19 Vaccine Sceptics Are Persuaded by pro-Vaccine Expert Consensus Messaging’. PsyArXiv, 14 January 2022. https://doi.org/10.31234/osf.io/kgsy3.
-
-
news.ycombinator.com news.ycombinator.com
-
I used Publii for my blog, but it was very constraining in terms of its styling
This is a common enough feeling (not about Publii, specifically; just the general concern for flexibility and control in static site generators), but when you pull back and think in terms of normalcy and import, it's another example of how most of what you read on the internet is written by insane people.
Almost no one submitting a paper for an assignment or to a conference cares about styling the way that the users of static site generators (or other web content publishing pipelines) do. Almost no one sending an email worries about that sort of thing, either. (The people sending emails who do care a lot about it are usually doing email campaigns, and not normal people carrying out normal correspondence.) No one publishing a comment in the thread here—or a comment or post to Reddit—cares about these things like this, nor does anyone care as much when they're posting on Facebook.
Somehow, though, when it comes to personal Web sites, including blogs, it's MySpace all over again. Visual accoutrement gets pushed to the foreground, with emphasis on the form of expression itself, often with little relative care for the actual content (e.g. whether they're actually expressing anything interesting, or whether they're being held back from expressing something worthwhile by these meta-concerns that wouldn't even register if happening over a different medium).
When it comes to the Web, most instances of concern for the visual aesthetic of one's own work are distractions. It might even be prudent to consider those concerns to be a trap.
-
-
stackoverflow.com stackoverflow.com
-
At this point I would call into question the job of Event to both be responsible for managing what gets charged and how something should be charged. I would probably investigate moving those to external service classes to keep charging responsibilities out of a simple event object.
-
-
www.gutenberg.org www.gutenberg.org
-
He assured me that he would never open another hypothetical book after he had taken his degree, but would follow out the bent of his own inclinations.
An all too common response to schooling! Is that rebellion against the system part of "unreason" in some way? The development of one's own inclinations through restriction?
-
every one is a genius, more or less
Highly amusing take on "talent".
-
But here they depart from the principles on which they justify their study of hypothetics; for they base the importance which they assign to hypothetics upon the fact of their being a preparation for the extraordinary, while their study of Unreason rests upon its developing those faculties which are required for the daily conduct of affairs.
Seems like a fundamental tension in education generally and the liberal arts and sciences in particular. The balance between wide-ranging creativity and mastery of content and skill isn't simple.
-
If the youths chose it for themselves I should have wondered less; but they do not choose it; they have it thrust upon them, and for the most part are disinclined towards it.
Interesting take on education and freedom. Implies that it's allright for some people not to worry about the unknowable parts of the future.
-
The main feature in their system is the prominence which they give to a study which I can only translate by the word “hypothetics.” They argue thus—that to teach a boy merely the nature of the things which exist in the world around him, and about which he will have to be conversant during his whole life, would be giving him but a narrow and shallow conception of the universe, which it is urged might contain all manner of things which are not now to be found therein. To open his eyes to these possibilities, and so to prepare him for all sorts of emergencies, is the object of this system of hypothetics. To imagine a set of utterly strange and impossible contingencies, and require the youths to give intelligent answers to the questions that arise therefrom, is reckoned the fittest conceivable way of preparing them for the actual conduct of their affairs in after life.
Education for a contingent future.
-
-
twitter.com twitter.com
-
James 💙 Neill - 😷 🇪🇺🇮🇪🇬🇧🔶. (2022, January 27). Norman has NOIDea Covid is almost entirely notified by labs not GPs. Norman is an embarrassment to @QMUL 🤦 https://t.co/3EqNd25OXZ [Tweet]. @jneill. https://twitter.com/jneill/status/1486671110372577290
-
-
www.theatlantic.com www.theatlantic.com
-
Schwitzgebel, E. (2022, February 3). The COVID Jerk. The Atlantic. https://www.theatlantic.com/ideas/archive/2022/02/covid-jerk-sarah-palin/621466/
-
-
thehustle.co thehustle.co
-
In crowded housing markets in large cities, house flipping is often viewed as a driver of inequality.
If house flipping is viewed as a driver of inequality in crowded housing markets in larger cities, what spurs it on? What do the economics look like and how can the trend be combatted?
What effect does economic speculation have?
-
So to attract newcomers, towns have attempted a dizzying array of stunts and initiatives.
Have they considered consolidation? Abandon three or four cities to aggregate into one?
-
“When I moved to Kansas,” Roberts said, “I was like, ‘holy shit, they’re giving stuff away.’”
This sounds great, but what are the "costs" on the other side? How does one balance out the economics of this sort of housing situation versus amenities supplied by a community in terms of culture, health, health care, interaction, etc.? Is there a maximum on a curve to be found here? Certainly in some places one is going to overpay for this basket of goods (perhaps San Francisco?) where in others one may underpay. Does it have anything to do with the lifecycle of cities and their governments? If so, how much?
-
-
-
a recitation of their names will be accompanied by a traditional libation, or pouring out of water, in accordance with West African traditions for honoring the deceased. "The ritual of libation holds the belief that saying people's names keeps them alive. It makes them free. It carries their personhood beyond their physical time on this earth," says event organizer Jasmine Blanks Jones, a postdoctoral fellow in the Program in Racism, Immigration, and Citizenship who is also part of Inheritance Baltimore, an interdisciplinary program for humanities education, research, and community engagement in Baltimore.
The West African tradition of libation, or pour out of water, honors the deceased and holds the belief that saying people's names aloud keeps them alive.
-
-
blogs.lse.ac.uk blogs.lse.ac.uk
-
academics (and students)
Shouldn't this parenthetical be written, if anything, as "academics (including students)"?
-
-
-
US government moves to end daily COVID-19 death reporting by hospitals. (n.d.). World Socialist Web Site. Retrieved February 2, 2022, from https://www.wsws.org/en/articles/2022/01/15/hhhs-j15.html
-
-
utcc.utoronto.ca utcc.utoronto.ca
-
keeping your website's look 'up to date' requires changes
Yeah, but...
Keeping your website's look 'up to date' requires changes, but keeping your website up does not require "keeping its look 'up to date'".
-
The problem almost certainly starts with the conception of what we're doing as "building websites".
When we do so, we mindset of working on systems
If your systems work compromises the artifacts then it's not good work
This is part of a broader phenomenon, which is that when computers are involved with absolutely anything people seem to lose their minds good sensibilities just go out the window
low expectations from everyone everyone is so used to excusing bad work
sui generis medium
violates the principle of least power
what we should be doing when grappling with the online publishing problem—which is what this is; that's all it is—is, instead of thinking in terms of working on systems, thinking about this stuff in such a way that we never lose sight of the basics; the thing that we aspire to do when we want to put together a website is to deal in
documents and their issuing authority
That is, a piece of content and its name (the name is a qualified name that we recognize as valid only when the publisher has the relevant authority for that name, determined by its prefix; URLs)
that's it that's all a Web site is
anything else is auxiliary
really not a lot different from what goes on when you publish a book take a manuscript through final revisions for publication and then get an ISBN issued for it
so the problem comes from the industry
people "building websites" like politicians doing bad work and then their constituents not holding them accountable because that's not how politics works you don't get held accountable for doing bad work
so the thing to do is to recognize that if we're thinking about "websites" from any other position things that technical people try to steer us in the direction of like selecting a particular system and then propping it up and how to interact with a given system to convince it to do the thing we want it to do— then we're doing it wrong
we're creating content and then giving it a name
-
-
www.excellentwebworld.com www.excellentwebworld.com
-
Theoretically speaking, we will answer all your queries inclusive of What is an Embedded System, Embedded System Characteristics, and various Types of Embedded Systems.
-
- Jan 2022
-
www.acf.hhs.gov www.acf.hhs.gov
-
HBCC is the most common form of nonparental child care for infants and toddlers
Notice the particular importance of HBCC for infants and toddlers (i.e., approximately birth to age three years).
-
-
hypothes.is hypothes.is
-
The nature of technical writing is explained in "The nature of technical writing". Technical communication is something we do every day without even noticing. Having strong communication skills is beneficial in all areas of one's life, from personal to professional. From a business standpoint, communication is key to every transaction. Communicating effectively allows others and yourself to understand information at a faster and more accurate rate. A lack of communication skills leads to frequent misunderstandings and frustration.
-
Technical communication/writing is something that has been around for a very long time. The earliest examples belong to Aristotle and his dictionary of "philosophical terms" and his summary of the "Doctrines of Pythagoras". World War I is considered the "Golden Age" of technical writing due to advances in medicine and aerospace.
-
-
www.nytimes.com www.nytimes.com
-
When I think back to the creation of that infographic, I wonder whether we had shown the care demanded of the data. Whether we had, in creating this abstraction, re-enacted — however inadvertently — some of the objectification of the slave trade.
This sort of objectification seems very similar to the type of erasure that Poland is doing with the Holocaust as they begin honoring Poles who helped Jews while simultaneously ignoring Poland's part in collaborating with the Nazis in creating the Holocaust.
How can we as a society and humanity add more care to these sorts of acts so as not to continue erasing the harm and better heal past wrongs?
Cross reference: https://www.nytimes.com/2022/01/29/opinion/holocaust-poland-europe.html and https://hyp.is/hrsb9oIOEey8sEObTYhk0A/www.nytimes.com/2022/01/29/opinion/holocaust-poland-europe.html
-
Consider, as well, the extent to which the tools of abstraction are themselves tied up in the history of the trans-Atlantic slave trade. As the historian Jennifer L. Morgan notes in “Reckoning With Slavery: Gender, Kinship, and Capitalism in the Early Black Atlantic,” the fathers of modern demography, the 17th-century English writers and mathematicians William Petty and John Graunt, were “thinking through problems of population and mobility at precisely the moment when England had solidified its commitment to the slave trade.”Their questions were ones of statecraft: How could England increase its wealth? How could it handle its surplus population? And what would it do with “excessive populations that did not consume” in the formal market? Petty was concerned with Ireland — Britain’s first colony, of sorts — and the Irish. He thought that if they could be forcibly transferred to England, then they could, in Morgan’s words, become “something valuable because of their ability to augment the population and labor power of the English.”This conceptual breakthrough, Morgan told me in an interview, cannot be disentangled from the slave trade. The English, she said, “are learning to think about people as ‘abstractable.’
This deserves to be delved into more deeply. This sounds like a bizarre stop on the creation of institutional racism.
How do these sorts of abstraction hurt the move towards equality?
-
-
www.nytimes.com www.nytimes.com
-
Books can indeed be dangerous. Until “Close Quarters,” I believed stories had the power to save me. That novel taught me that stories also had the power to destroy me. I was driven to become a writer because of the complex power of stories. They are not inert tools of pedagogy. They are mind-changing, world-changing.
—Viet Thanh Nguyen
-
-
notes.linkingyourthinking.com notes.linkingyourthinking.com
-
A Mental Squeeze Point is when your unsorted knowledge becomes so messy it overwhelms and discourages you. Either you are equipped with frameworks to overcome the squeeze point, or you are discouraged and possibly abandon your project.
Cross reference: https://hypothes.is/a/BuMcAnr4EeyxO-PwNBfPrg (Dan Allosso's analogy about the Kuiper Belt)
-
-
-
Different people have different responses to technology, even on the same platform. Scholars call this phenomenon “differential susceptibility” to media effects among a subgroup of people, and it holds equally for the differential well-being and mental health impacts of social media on young adults.
Differential susceptibility is a technical term used to describe the ways that different people and different groups have different responses to technology even on the same platform. Similar versions of it can be applied to other areas outside of technology, which is but one target. Other areas include differential well-being and mental health.
It could also be applied to drug addiction as some are more susceptible to becoming addicted to nicotine than others. Which parts of this might be nature, nurture, culture, etc.
-
Current approaches to improving digital well-being also promote tech solutionism, or the presumption that technology can fix social, cultural, and structural problems.
Tech solutionism is the presumption that technology (usually by itself) can fix a variety of social, cultural, and structural problems.
It fits into a category of problem that when one's tool is a hammer then every problem looks like a nail.
Many tech solutionism problems are likely ill-defined to begin with. Many are also incredibly complex and difficult which also tends to encourage bikeshedding, which is unlikely to lead us to appropriate solutions.
-
-
notesfromasmallpress.substack.com notesfromasmallpress.substack.com
-
If booksellers like to blame publishers for books not being available, publishers like to blame printers for being backed up. Who do printers blame? The paper mill, of course.
The problem with capitalism is that in times of fecundity things can seem to magically work so incredibly well because so much of the system is hidden, yet when problems arise so much becomes much more obvious.
Unseen during fecundity is the amount of waste and damage done to our environments and places we live. Unseen are the interconnections and the reliances we make on our environment and each other.
There is certainly a longer essay hiding in this idea.
-
-
www.biorxiv.org www.biorxiv.org
-
Hirose, R., Itoh, Y., Ikegaya, H., Miyazaki, H., Watanabe, N., Yoshida, T., Bandou, R., Daidoji, T., & Nakaya, T. (2022). Differences in environmental stability among SARS-CoV-2 variants of concern: Omicron has higher stability [Preprint]. Microbiology. https://doi.org/10.1101/2022.01.18.476607
-
-
towardsdatascience.com towardsdatascience.com
-
standard error
-
-
accessmedicine-mhmedical-com.proxy.library.maryville.edu accessmedicine-mhmedical-com.proxy.library.maryville.edu
-
Respiratory failure can be broadly categorized as hypoxemic respiratory failure (respiratory insufficiency) or hypercapnic respiratory failure (ventilatory failure), and the two forms may coexist
Hypercapnic and Hypoxic Resp failure can co-exist
-
-
uni-bielefeld.de uni-bielefeld.de
-
Three types of linking can be distinguished:a) References in the context of a larger structural outline: When beginning a major line of thoughtLuhmann sometimes noted on the first card several of the aspects to be addressed and marked themby a capital letter that referred to a card (or set of consecutive cards) that was numbered accordinglyand placed at least in relative proximity to the card containing the outline. This structure comesclosest to resembling the outline of an article or the table of contents of a book and therefore doesn’treally use the potentials of the collection as a web of notes.b) Collective references: At the beginning of a section devoted to a specific subject area, one can oftenfind a card that refers to a number of other cards in the collection that have some connection withthe subject or concept addressed in that section. A card of this kind can list up to 25 references andwill typically specify the respective subject or concept in addition to the number. These referencescan indicate cards that are related by subject matter and in close proximity or to cards that are farapart in other sections of the collection, the latter being the normal case.c) Single references: At a particular place in a normal note Luhmann often made a reference to anothercard in the collection that was also relevant to the special argument in question; in most cases the re
ferred card is located at an entirely different place in the file, frequently in the context of a completely different discussion or subject.
Niklas Luhmann's index card system had three different types of links. Direct links to individual notes, outlines with links to cards (similar to tables of contents or maps of content), and what Schmidt (2018) refers to as "collective references". These collective references sound a lot like search queries for related topics that have links to a variety of resources/cards related to a particular topic and sound like a table of contents, but without a specific hierarchy.
-
-
www.cnn.com www.cnn.com
-
Howard, J. (2022, January 21). Covid-19 vaccinations do not impair fertility in men or women, new study finds—CNN. CNN Health. https://edition.cnn.com/2022/01/20/health/covid-vaccine-fertility-study/index.html?utm_source=twCNN&utm_term=link&utm_medium=social&utm_content=2022-01-21T00%3A08%3A17
-
-
canvas.ucsc.edu canvas.ucsc.eduFiles1
-
The Culture Industry: Mass Deception in Dialectic of Enlightenment
The culture industry is any industry that is producing cultural products: news, beauty, music, fashion industry has one goal: generate profit. They will produce things that are produced like a factory. They are intended to produce consumerism. In the way that sex sells, rebellion also sells. The industries that are making our culture are feeding us our news so are corporaterized. Adorno and Horkheimer would not be suprised about YouTube. That cultural adversary may be dialectical.
Academia. You know more about less and less.
Backdrop context: Shaky ground of liberal democracy in the beginnings of WW2,rise of social movements, rise of nationalism and facism.
Englightment: Reason & Individual liberty Bacon: a larger system that synthesized knowledge and power as one; a flipping of nature over man and man over nature; but A/H thought that this played out in a human global scale.
If Enlightenment was supposed to create logic and reason why did we experience WW2, for A/H if we're to take Bacon seriously we have to consider DOMINATION in newer notions of freedom.
Regression: Enlightenment as Myth. Englightenment becomes totalitarian it ABSTRACTS. Ex. Hitler youth, a difference among others yet they become homogenous sameness among each other.
The result of the sacrifice continues that is far more reaching that MArx's alienation. --> UNFETTERED ACCEPTANCE
Adorno/H say that positivism: 1) a system of philiospgy were every assertion can be proved 2) as ideoogy where eveyrthing is true by default and questioning it goes against objective foundations.
Kant saw a short-sighted view of self-reason
IDEOLOGY of defintiion #2 the process of Englightenment is brought into analysis of the Culture Industry.
Context: AMerica is becoming global powerhouse, Soviet underwent their own Industrial Revolution, change was everywhere and revolutionary change with one large outlier thus the immediat question. Despite a global population of workers revolitng around the globe then why didnt the United States or Western Countries embrace similar post-capitalist systems seen across teh globe? And how is Soviet existing as a post-capitalist system alongside the capitalist system?
Art is being systematized, newer technology is being synthesized into one and the same narrative. The same repackaged story; subject and authority. This mimics the governance of a few over many.
A/H utilize Kant's idea of schemtaism (being how the midn communicates with objects and other structures aorund us, how to reason and cogantate; synthesize and bring Froyd into the mix, how we suppress ourselves and our desires to how we fit into society. We cognitively pick up how the world is presented to us. Viewership creates the bounds within which we can do art. A psychological realism that is difficult to break for a person who works a 9-5pm; to break it in a capitalist system is used to labor and build wealth. Art becomes the same even when it tries to stand out. There is a unifornm aethetic if you wnat to be different, the sameness and constant
Art is now abstracted a fulfilmmnet of mere numbers rather than aesthetic work and utility. Regarding art in newer creation, A/H bring up autombiles as an example, a film must have a romatic sequence that the industry now demands. This is part of Mechanical reproduction. Art will become tailored to your class relation as well. But it's not only class and poleconomy but it's not just corporate art is entirely based oof profit but rather there is a cyclcial ideology that reinforces this ideology. see
The focus isn't on marvel movies (for their thrist for profit) or to tell consumers to not consume this art but its the industry itself that reproduces the
"Thirst" is not conscious it is a result of the structure that is capitalism the culture industry modling of our desires in the first place.
It's not good enough to tell individuals to not consume said tailored art. Example anti-semitism is a result of essentialist notions of race. Largest incubators of anti-semitism stem from the bourigeoise themselves but a ruling class of people attempting to hide a ruling class domination. Here the bouregoise know the struggles of individuals and pins this to Jewish individuals.
Thus its not really just pushing Jewish people out of certain borders this marks the downfall of bouregoise property.
Look up: > Cultural education became....
The whole world is made to pass through the filter of the culture industry...
Culture is a paradoxical commodity. It is so completely subject to the law of exchange that it is no longer exchanged; it is so blindly equated with use that it can no longer be used. For this reason it merges with the advertisement. The more meaningless the latter appears under monopoly, the more omnipotent culture becomes. (pg 131).
Unending sameness also governs the relationship to the past. What is new in the phase of mass culture compared to that of late liberalism is the exclusion of the new.
-
-
openhistoryseminar.com openhistoryseminar.com
-
forced into the American Union
It is important to think about the fear of being "forced into the American Union" in the context of the time. At this time, the American Civil War is still ongoing, and the situation was fragile. Since Canada did not exist and it was only colonies, it is realistic to view America as a threat to the possible development of Canada as a country.
-
-
eductive.ca eductive.ca
-
L’un des thèmes récurrents pendant les discussions a été celui de la rigueur.
Not too surprising. It's an important consideration for the Academe. Almost part of the definition. And it's useful that learning pros are tackling such issues instead of jumping to conclusions. In a way, it's an extension of work done in the Sociology of Education since 1918.
-
-
-
Maybe once the core onError lifecycle is implemented (if maintainers decide to go that way) everyone will discover you're right and an implementation will be built in. I think that's probably what's going to happen. But until real life has proved it, it's usually best to go for the smallest most broadly applicable solution. I can definitely imagine <svelte:error> eventually being a thing, but it's a pretty dramatic change compared to an added importable function.
-
and if I think this is too boilerplatey, I can export a handler from some .js file and pass the error to that: <script> import { onError } from 'svelte' import { genericHandler } from '../my-error-handler.js' onError(genericHandler(e => { // code which is called first to try to handle this locally return true // we've handled it here, don't do anything else. }) </script>
-
-
github.com github.com
-
but you want to style your components yourself and not be constrained by existing design systems like Material UI
-
-
news.ycombinator.com news.ycombinator.com
-
Yes, precisely because I've been involved in maintaining codebases built without real full stack frameworks is why I say what I said.The problem we have in this industry, is that somebody reads these blog posts, and the next day at work they ditch the "legacy rails" and starts rewriting the monolith in sveltekit/nextjs/whatever because that's what he/she has been told is the modern way to do full stack.No need to say those engineers will quit 1 year later after they realize the mess they've created with their lightweight and simple modern framework.I've seen this too many times already.It is not about gatekeeping. It is about engineers being humble and assume it is very likely that their code is very unlikely to be better tested, documented, cohesive and maintained than what you're given in the real full stack frameworks.Of course you can build anything even in assembler if you want. The question is if that's the most useful thing to do with your company's money.
-
-
stackoverflow.com stackoverflow.com
-
The RFC2617 model is one-user, one-credentials so the case where the user may have a second set of credentials that could be authorized may be ignored. It neither suggests nor implies that some sort of login page or other non-RFC2617 authentication protocol may or may not help - that is outside the RFC2616 standards and definition.
-
-
www.niemanlab.org www.niemanlab.org
-
https://www.niemanlab.org/collection/predictions-2022/
In the bustle of the holidays and life, I'd nearly forgotten to check out NiemanLab's annual Predictions for Journalism. I can't wait to catch up on the series.
h/t @Klingebeil
-
-
johannesklingebiel.de johannesklingebiel.de
-
To learn—A rather obvious one, but I wanted to challenge myself again.
I love that Johannes Klingbiel highlights having his own place on the Internet as a means to learn. While I suspect that part of the idea here is to learn about the web and programming, it's also important to have a place you can more easily look over and review as well as build out on as one learns. This dovetails in part with his third reason to have his own website: "to build". It's much harder to build out a learning space on platforms like Medium and Twitter. It's not as easy to revisit those articles and notes as those platforms aren't custom built for those sorts of learning affordances.
Building your own website for learning makes it by definition a learning management system. The difference between my idea of a learning management system here and the more corporate LMSes (Canvas, Blackboard, Moodle, etc.) is that you can change and modify the playground as you go. While your own personal LMS may also be a container for holding knowledge, it is a container for building and expanding knowledge. Corporate LMSes aren't good at these last two things, but are built toward making it easier for a course facilitator to grade material.
We definitely need more small personal learning management systems. (pLMS, anyone? I like the idea of the small "p" to highlight the value of these being small.) Even better if they have social components like some of the IndieWeb building blocks that make it easier for one to build a personal learning network and interact with others' LMSes on the web. I see some of this happening in the Digital Gardens space and with people learning and sharing in public.
[[Flancian]]'s Anagora.org is a good example of this type of public learning space that is taking the individual efforts of public learners and active thinkers and knitting their efforts together to facilitate a whole that is bigger than the sum of it's pieces.
-
-
-
The key thing about the REST approach is that the server addresses the client state transitions. The state of the client is almost totally driven by the server and, for this reason, discussions on API versioning make little sense, too. All that a client should know about a RESTful interface should be the entry point. The rest should come from the interpretation of server responses.
-
-
-
en.wikipedia.org en.wikipedia.org
-
-
The client transitions through application states by selecting from the links within a representation or by manipulating the representation in other ways afforded by its media type. In this way, RESTful interaction is driven by hypermedia, rather than out-of-band information.
-
-
www.bbc.co.uk www.bbc.co.uk
-
Should bad science be censored on social media? (2022, January 19). BBC News. https://www.bbc.com/news/technology-60036861
-
-
johannesklingebiel.de johannesklingebiel.de
-
I am committed to tending to this world as a gardener. I am committed to cultivating new shoots, new stories, new hopes, new futures. I do this work with dirt under my nails, with curiosity, reverence and respect.—Georgina Reid
What a great quote for a digital garden. Reminiscent of the philosophy of care seen in the book Braiding Sweetgrass.
-
-
en.wikipedia.org en.wikipedia.org
-
China Illustrata emphasized the Christian elements of Chinese history, both real and imagined: the book noted the early presence of Nestorian Christians (with a Latin translation of the Nestorian Stele of Xi'an provided by Boym and his Chinese collaborator, Andrew Zheng),[23] but also claimed that the Chinese were descended from the sons of Ham, that Confucius was Hermes Trismegistus/Moses and that the Chinese characters were abstracted hieroglyphs.
Example of non-Europeans being considered the sons of Ham, in this case by an incredibly learned and influential Roman Catholic scholar.
-
-
-
Local file Local file
-
Survivals of this spatially oriented technique still mark our language when we say “in the first place” and “passing on to the next point.”
The use of mnemonic techniques through history have been crystalized into our language with phrases like "in the first place" and "passing on to the next point".
-
-
-
Choose your custom packaging style
I liked the strategy of customizing the boxes according to the customer's needs. The customer assembles how his box will best serve him.
-
-
-
When Simonides offered to teach the Athenian statesman Themistocles the art of Memory, Cicero reports that he refused. "Teach me not the art of remem- bering," he said, "but the art of forgetting, for I remember things I do not wish to remember, but I cannot forget things I wish to forget."
-
The effect was beautifully suggested by Victor Hugo in a familiar passage in Notre-Dame de Paris (183 1) when the scholar holding his first printed book turns away from his manuscripts, looks a t the cathedral, and says "This will kill that" (Ceci tuera cela). Print also destroyed "the invisible cathedrals of memory." For the printed book made it less nec- essary to shape ideas and things into vivid images and then store them in Memory-places.
In Notre-Dame de Paris (1831) Victor Hugo depicts a scholar holding his first printed book. He turns away from his manuscripts to look at the cathedral and says "This will kill that" (Ceci tuera cela). Similarly the printed book made it far less necessary to store one's knowledge into cathedrals of memory.
-
For centuries the standard work on Latin grammar was the 12th- century Doctrinale, by Alexander of Villedieu, in 2,000 lines of doggerel. Versified rules were easier to remember, though their crudity appalled Aldus Manutius when he reprinted this work in 1501.
Alexander de Villedieu's Latin grammer Doctrinale from the 12th century was the standard work on the subject. Its 2,000 lines of doggerel were used as a mnemonic device because they were easier to remember. Famed publisher Aldus Manutius was appalled at their crude nature when he reprinted the book in 1501.
-
The Lost Arts of Memory by Daniel J. Boorstin The Wilson Quarterly, Spring 1984 104-113
-
-
-
#5. Game of Thrones - The Rains of Castamere
-
#3. Game of Thrones - The Winds of Winter
-
#2. Game of Thrones - Battle of the Bastards
-
-
en.wikipedia.org en.wikipedia.org
-
Autopoiesis has been proposed as a potential mechanism of abiogenesis, by which primitive cells evolved into more complex molecules that could support the development of life.
-
Until recently[30][31][32] there have been almost no attempts to compare the different theories and discuss them together.
- Letelier, J C; Cárdenas, M L; Cornish-Bowden, A (2011). "From L'Homme Machine to metabolic closure: steps towards understanding life". J. Theor. Biol. 286 (1): 100–113. Bibcode:2011JThBi.286..100L. doi:10.1016/j.jtbi.2011.06.033. PMID 21763318.
- Igamberdiev, A.U. (2014). "Time rescaling and pattern formation in biological evolution". BioSystems. 123: 19–26. doi:10.1016/j.biosystems.2014.03.002. PMID 24690545.
- Cornish-Bowden, A; Cárdenas, M L (2020). "Contrasting theories of life: historical context, current theories. In search of an ideal theory". BioSystems. 188: 104063. doi:10.1016/j.biosystems.2019.104063. PMID 31715221. S2CID 207946798.
Relationship to the broader idea in Loewenstein as well...
-
Autopoiesis is just one of several current theories of life, including the chemoton[20] of Tibor Gánti, the hypercycle of Manfred Eigen and Peter Schuster,[21] [22] [23] the (M,R) systems[24][25] of Robert Rosen, and the autocatalytic sets[26] of Stuart Kauffman, similar to an earlier proposal by Freeman Dyson.[27] All of these (including autopoiesis) found their original inspiration in Erwin Schrödinger's book What is Life?[28] but at first they appear to have little in common with one another, largely because the authors did not communicate with one another, and none of them made any reference in their principal publications to any of the other theories.
-
-
adjacentpossible.substack.com adjacentpossible.substack.com
-
archive.org archive.org
-
https://archive.org/details/bub_gb_IgMVAAAAQAAJ/page/n155/mode/2up
On page 138 Placcius shows an (uncredited?) version of Thomas Harrison's Ark of Studies.
p 140:
-
-
-
Kirby, J. (2021, December 23). Omicron collides with a struggling global vaccination campaign. Vox. https://www.vox.com/22846774/omicron-global-vaccines-covronavirus-covid-19
-
-
-
ike Jungius, Boyle made use of loose folio sheets that he called memorials or adversaria; yet he did not worry too much about a system of self-referential relationships that enabled intentional knowl-edge retrieval. When he realized that he was no longer able to get his bearings in an ocean of paper slips, he looked for a way out, testing several devices, such as colored strings or labels made of letters and numeral codes. Unfortunately, it was too late. As Richard Yeo clearly noted, ‘this failure to develop an effective indexing system resulted from years of trusting in memory in tandem with notes’.69
69 Yeo, ‘Loose Notes’, 336
Robert Boyle kept loose sheets of notes, which he called memorials or adversaria. He didn't have a system of organization for them and tried out variations of colored strings, labels made of letters, and numerical codes. Ultimately his scrap heap failed him for lack of any order and his trust in memory to hold them together failed.
I love the idea of calling one's notes adversaria. The idea calls one to compare one note to another as if they were combatants in a fight (for truth).
Are working with one's ideas able to fit into the idea of adversarial interoperability?
-
With respect to the Ark of Studies, for example, Johann Benedict Metzler did not use gratifying words; yet he nonetheless recommended numbering the hooks (aciculas) to which the paper slips should be attached and recording the matching of number and heading in a subject index. In this way, Metzler noted, scholars would not be compelled to leave empty spaces between entries and to recalibrate the entire content any time a new entry (a new commonplace) should be added.65
65 Johann Benedict Metzler, Artificium excerpendi genuinum dictus Die rechte Kunst zu excer-piren (Leipzig, 1709), 23–4; 30; 91–2
Is there really any mathematical difference between alphabetical order and a numerical decimal order? Can't they be shown to be one-to-one and onto?
To a layperson they may seem different...
-
-
prospect.org prospect.org
-
DrPH, M. D. H., M. D. (2022, January 11). The Folly of School Openings as a Zero-Sum Game. The American Prospect. https://prospect.org/api/content/4a1fc36e-7263-11ec-9e7d-12f1225286c6/
Tags
- economic oppression
- children
- remote learning
- risk
- online learning
- disparity
- economy
- mortality
- systemic racism
- paediatric hospitalization
- work from home
- school closure
- is:webpage
- COVID-19
- low-income
- ventilation
- USA
- vaccine
- priviledge
- perception
- multigenerational family structure
- people of colour
- school
- safety
- education
- race
- lang:en
- homeschooling
- white supremacy
- in-person schooling
- exposure
- virtual learning
- transmission
- Omicron
Annotators
URL
-
-
twitter.com twitter.com
-
Eric Topol. (2022, January 14). Much less loss of smell and taste with Omicron, but more sore throat than with Delta https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/1046623/Technical-Briefing-34-14January2022.pdf @UKHSA symptom data from ~175,000 Omicron and ~88,000 Delta cases https://t.co/DIGRGkoXa9 [Tweet]. @EricTopol. https://twitter.com/EricTopol/status/1482029245580808192
-
-
Local file Local file
-
My point is school is ment to be a safe learning ground, so let's keep it that way.”
The writer uses a claim of value, saying school is meant to be a safe place for learning, and implying that when minors or exercising shirtless, school is no long such a place, but rather dangerous and an unfit place for learning.
-
Yes, age played a part. I find it disgusting and degrading that any parent would let their minor child run aroun in shorts and a bra anywhere.
The speaker of the text is using a claim of value, stating that minors should not be able to exercise or be on school property without a shirt covering specifically bras. The speaker believes age to be a main contributor. The speaker is stating because of age, it is wrong to allow minors to exercise on school property. This is the speakers point of view.
-
-
drive.google.com drive.google.com
-
Most of the world's great books are available today, in reprint editions.
Published in 1941, this article precedes the beginning of the project of publishing the Great Books of the Western World for Encyclopedia Britannica, so Adler isn't just writing this from a marketing perspective.
https://en.wikipedia.org/wiki/Great_Books_of_the_Western_World
Tags
Annotators
URL
-
-
twitter.com twitter.com
-
Jennifer K McDonald. (2021, October 16). Here’s the rebreathed fraction of air table from the all-knowing @DavidElfstrom [Tweet]. @JenniferKShea. https://twitter.com/JenniferKShea/status/1449380211435479047
-
-
www.medrxiv.org www.medrxiv.org
-
Home
Zuo, F., Abolhassani, H., Du, L., Piralla, A., Bertoglio, F., Campos-Mata, L. de, Wan, H., Schubert, M., Wang, Y., Sun, R., Cassaniti, I., Vlachiotis, S., Kumagai-Braesch, M., Andréll, J., Zhang, Z., Xue, Y., Wenzel, E. V., Calzolai, L., Varani, L., … Pan-Hammarström, Q. (2022). Heterologous immunization with inactivated vaccine followed by mRNA booster elicits strong humoral and cellular immune responses against the SARS-CoV-2 Omicron variant (p. 2022.01.04.22268755). https://doi.org/10.1101/2022.01.04.22268755
-
