https://en.wikipedia.org/wiki/Station_Fire_(2009)

Einer neuen Modellierung zufolge sind die wirtschaftlichen Auswirkungen der globalen Erhitzung deutlich gravierender, als es bisher von vielen in den Wirtschaftswissenschaften angenommen wurde. Eine globale Temperaturerhöhung um 2° wird danach das Bruttosozialprodukt weltweit um 16% senken. Bei einer Temperaturerhöhung um vier Grad wären die Menschen auf der Erde durchschnittlich 40 % ärmer als ohne diese Erhöhung. Die neue Modellierung bezieht die Folgen von Extremereignissen und anderen Auswirkungen der Erhitzung ein, die bisher meist nicht berücksichtigt wurden. https://www.theguardian.com/environment/2025/apr/01/average-person-will-be-40-poorer-if-world-warms-by-4c-new-research-shows
Der Bericht eines britischen Instituts für Versicherungsmathematik geht davon aus, dass die Folgen der globalen Erhitzung das Bruttosozialprodukt um 15% verringern werden, wenn die aktuelle Politik fortgesetzt wird.
Studie: https://iopscience.iop.org/article/10.1088/1748-9326/adbd58 Bericht von Institute und Faculty of Actuaries der Universität Exeter: https://actuaries.org.uk/planetary-solvency
Extremwettereignisse als Folgen.der globalen Erhitzung haben viele Brücken in den USA beschädigt. Jede vierte der 80.000 Stahlbrücken droht bis 2050 einzubrechen. Vor allem aber gefährdet die hitzebedingte Erosion des Bodens die Stabilität der Pfeiler. Neue Standards für klimaresilienten Brückenbau vergrößern den ohnehin enormen Investitionsbedarf fürdie Erneuerung der US-Infrastruktur. Allein in Colorado düfte das Vier- bis Fünffache der vorhandenen Beträge gebraucht werden. https://www.nytimes.com/2024/09/02/climate/climate-change-bridges.html
Eine neue, grundlegende Studie zu Klima-Reparationen ergibt, dass die größten Fosssilkonzerne jählich mindestens 209 Milliarden Dollar als Reparationen an von ihnen besonders geschädigte Communities zahlen müssen. Dabei sind Schäden wie der Verlust von Menschenleben und Zerstörung der Biodiversität nicht einberechnet. https://www.theguardian.com/environment/2023/may/19/fossil-fuel-firms-owe-climate-reparations-of-209bn-a-year-says-study
Studie: Time to pay the piper: Fossil fuel companies’ reparations for climate damages https://www.cell.com/one-earth/fulltext/S2590-3322(23)00198-7
Der bisherige Präsident der G77 Gruppe, Pedro Pedroso, fordert von den Industrieländern sich endlich an den Pariser Zielen zu orientieren. Neben Verzicht auf die geplante fossile Expansion ist dazu Finanzierung erneuerbarer Energien in globalen Süden nötig. Der zusammenfassende Guardian-Artikel enthält Infografiken zu der geplanten Steigerung von Öl- und Gasproduktion sowie LNG-Exporten der USA. https://www.theguardian.com/environment/2024/jan/19/cop28-fossil-fuels-climate-deal-pedro-pedroso-us-uk-canada-pollution
Eine Gruppe von NGOs hat ein Konzept für eine Klimaschaden-Steuer ausgearbeitet, zu der Öl- und Gasgesellschaften ausgehend vom von ihnen verursachten CO2-Ausstoß herangezogen würden. Würde die Steuer in den OECD-Ländern mit 5$ pro Kilotonne CO2 beginnen und sich jährlich um weitere 5$ erhöhen, stünden 2030 jährlich 900 Milliarden $ vor allem für den Loss and Damage Fund zur Verfügung, der bei der COP28 beschlossen wurde.
Bericht: https://www.greenpeace.fr/wp-content/uploads/2024/03/CDT_guide_2024_embargoed_version.pdf
Pakistan hat bei einer Geberkonferenz Zusagen über ca. 9 Milliarden USD für den Wiederaufbau nach den Überflutungen des letzten Jahres erhalten. Der pakistanische Premierminister wies darauf hin, dass das internationale Finanzsystem katastrophal schlecht auf Loss and Damage durch die Klimakrise ausgerichtet ist
Extremer Regen hat in Pakistan und Afghanistan mindestens 135 Todesfälle verursacht und große Flächen bebauten Landes zerstört. Vorausgegangen war eine lange Periode ungewöhnlicher Trockenheit. Die Regenfälle wurden von demselben Wettersystem verursacht, das kurz zuvor Überflutungen in den Vereinigten Arabischen Emiraten und Oman verursacht hatte.
So last move (2 years ago) my Kiddo(chronic mental and medical high time demand) dumped my cards and I am still trying to sort them back. ** As of now I am using hair ties to make sure they don't get "accidentally" dumped again. If they do it will have to be done with some fore thought.
Example of someone using hair ties and smaller internal boxes to prevent zettelkasten cards from being dumped out due to child mischief.
via: https://www.reddit.com/r/antinet/comments/1bv6sxy/moving_again_and_a_tip_on_transporting/
Interview mit Mia Mottley, der Premierministerin von Barbados und Hauptvorkämpferin der von ihr ins Leben gerufenen Bridgetown Initiative zur Klimafinanzierung für den globalen Süden. Mottley geht auf die Schuldenkrise in vielen Ländern nach der Pandemie ein und fordert, wie sie sagt, unorthodoxe CO2-Steuern, z.B Abgaben von fossilen Konzernen und Fluggesellschaften. Die derzeit Mächtigen verhinderten eine wirksame Klimafinanzierung, obwohl es Fortschritte z.B. bei Finanzinstitutionen gebe. Dass Finanztransfers vor allem zu einer klimagerechten Transformation nötig sei, werde nicht anerkannt. https://taz.de/Barbados-Premier-ueber-Klimakrise/!5994100/
Able to see lots of cards at once.
ZK practice inspired by Ahrens, but had practice based on Umberto Eco's book before that.
Broad subjects for his Ph.D. studies: Ecology in architecture / environmentalism
3 parts: - zk main cards - bibliography / keywords - chronological section (history of ecology)
Four "drawers" and space for blank cards and supplies. Built on wheels to allow movement. Has a foldable cover.
He has analog practice because he worries about companies closing and taking notes with them.
Watched TheNoPoet's How I use my analog Zettelkasten.
, one of the reasons that the New York Public Library had toclose its public catalog was that the public was destroying it. TheHetty Green cards disappeared. Someone calling himself Cosmoswas periodically making o� with all the cards for Mein Kampf. Cardsfor two Dante manuscripts were stolen: not the manuscripts, thecards for the manuscripts.
book at a public phone rather than bothering to copy down anaddress and a phone number, library visitors—the heedless, thecrazy—have, especially since the late eighties, been increasinglycapable of tearing out the card referring to a book they want.
The huge frozen card catalog of the Library of Congress currently suers from alarming levels of public trauma: like the movie trope in which the private eye tears a page from a phone
Radical students destroyed roughly ahundred thousand cards from the catalog at the University of Illinoisin the sixties. Berkeley’s library sta� was told to keep watch overthe university’s card catalogs during the antiwar turmoil there.Someone reportedly poured ink on the Henry Cabot Lodge cards atStanford
They donot grow mold, as the card catalog of the Engineering Library of theUniversity of Toronto once did, following water damage.
(The more modi�cation a library demands of eachMARC record, the more it costs.) In Harvard’s case she typicallyaccepts the record as is, even when the original card bearsadditional subject headings or enriching notes of various kinds.
Information loss in digitizing catalog cards...
An image of the front of every card for Widener thus now exists onmicro�che, available to users in a room o� the lobby. (Anyinformation on the backs of the cards—and many notes do carryover—was not photographed
Curtis mentioned one example of information that he found: “One of the first drawers of the author-title catalog I looked through held a card for Benjamin Smith Barton’s ‘Elements of Botany’ [the 1804 edition]. The card indicated that UVA’s copy of this book was signed by Joseph C. Cabell, who was instrumental in the founding of the University.”Curtis checked to see if the Virgo entry included this detail, but he found no record of the book at all. “I thought perhaps that was because the book had been lost, and the Virgo entry deleted, but just in case, I emailed David Whitesell [curator in the Albert and Shirley Small Special Collections Library] and asked him if this signed copy of Barton’s ‘Elements of Botany’ was on the shelves over there. Indeed it was.
Digitization efforts in card collections may result in the loss or damage of cards or loss of the materials which the original cards represented in the case of library card catalogs.
for - 2nd Trump term - 2nd Trump presidency - 2024 U.S. election - existential threat for climate crisis - Title:Trump 2.0: The climate cannot survive another Trump term - Author: Michael Mann - Date: Nov 5, 2023
Summary - Michael Mann repeats a similiar warning he made before the 2020 U.S. elections. Now the urgency is even greater. - Trump's "Project 2025" fossil-fuel -friendly plan would be a victory for the fossil fuel industry. It would - defund renewable energy research and rollout - decimate the EPA, - encourage drilling and - defund the Loss and Damage Fund, so vital for bringing the rest of the world onboard for rapid decarbonization. - Whoever wins the next U.S. election will be leading the U.S. in the most critical period of the human history because our remaining carbon budget stands at 5 years and 172 days at the current rate we are burning fossil fuels. Most of this time window overlaps with the next term of the U.S. presidency. - While Mann points out that the Inflation Reduction Act only takes us to 40% rather than Paris Climate Agreement 60% less emissions by 2030, it is still a big step in the right direction. - Trump would most definitely take a giant step in the wrong direction. - So Trump could singlehandedly set human civilization on a course of irreversible global devastation.
The GOP has threatened to weaponize a potential second Trump term
for - 2nd Trump term - regressive climate policy
other nations are wary of what a second Trump presidency could portend,
for - 2nd Trump presidency - elimination of loss and damage fund - impact on global decarbonization effort
That’s what the “loss and damage” agreement does,
for - loss and damage fund - global impact
FireKing File Cabinet, 1-Hour Fire Protection, 6-Drawer, Small Document Size, 31" Deep<br /> https://www.filing.com/FireKing-Card-Check-Note-Cabinet-6-Drawer-p/6-2552-c.htm
A modern index card catalog filing solution with locks and fireproofing offered by FireKing for $6,218.00 with shipment in 2-4 weeks. 6 Drawers with three sections each. Weighs 860 lbs.
at 0.0072" per average card, with filing space of 25 15/16" per section with 18 sections, this should hold 64,843 index cards.
One of the benefits of having a separate working bibliography for a project is that it provides a back up copy in the case that one loses or misplaces one's original bibliography note cards. (p 50)
https://www.amazon.com/JUNDUN-Dividers-Collapsible-Fireproof-4x6-Inch/dp/B0BNHZ3JTR/?th=1
A card index box which is waterproof and fireproof for potential travel.
Deutschland hat sich bereiterklärt, 100 Millionen Euro in den Fonds für Klimaschäden einzuzahlen. Das ist etwa ein Promille der geplanten Militärausgaben l. https://taz.de/Deutsche-Zusagen-zur-Klimafinanzierung/!5973914/
CO?28-Präsident Sultan Al Jaber hat den Verdacht zurückgewiesen, er benutze Klimagespräche, um Geschäfte des von ihm geleiteten staatlichen Ölkonzerns Adnoc vorzubereiten. Aktivist:innen nahmen seine Erklärungen nicht ernst. Die geleakten Information müssten der letzte Nagel im Sarg der schon längst enttarnten Idee sein, dass die Fossilindustrie eine Rolle bei der Lösung der Krise spielen könne, die sie geschaften hat (Alice Harrison) https://www.theguardian.com/environment/2023/nov/29/cop28-president-denies-on-eve-of-summit-he-abused-his-position-to-sign-oil-deals
Zu Beginn der COP28 wurde die Einrichtung eines loss and damage-Fonds entsprechend den kurz vorher vereinbarten Regularien beschlossen. Deutschland und die UAE sind die ersten Einzahler, andere Länder folgen. Damit kann die Konferenz mit einer Erfolgsmeldung beginnen. Die weitere Finanzierung ist allerdings unklar; die zu erwartenden Beträge bleiben weit hinter dem Bedarf zurück. https://www.theguardian.com/environment/2023/nov/30/agreement-on-loss-and-damage-deal-expected-on-first-day-of-cop28-talks
Rich in manuscripts and correspondence for Arendt’s productive years as a writer and lecturer after World War II, the papers are sparse before the mid-1940s because of Arendt’s forced departure from Nazi Germany in 1933 and her escape from occupied France in 1941.
Kurzer grundsätzlicher Artikel zur Climate Accountabilty kurz vor der COP28. Einer der Autor:innen, der gerade verstorbene Saleemul Huq, war ein wichtiger Kämpfer gegen globale Klima-Ungerechtigkeit. Das Übergangskomitee der Vereinten Nationen kam erst im November zu einer umstrittenen Einigung über die Zahlungen an den Loss-and damage-Fonds. Großbritannien und die USA (der historisch größte Verschmutzer) lehnen Klimareparationen grundsätzlich ab. https://www.theguardian.com/commentisfree/2023/nov/01/climate-destruction-rich-countries-cop28
Kurz vor der COP28 kam es zu einer grundsätzlichen Einigung über die Umsetzung des Loss-and-damage-Fonds, der auf der letzten COP beschlossen worden war. Er wird zunächst von der Weltbank verwaltet werden. Die Höhe der Einzahlungen ist noch nicht klar. Aktivist:innen reagierten enttäuscht. https://www.theguardian.com/environment/2023/nov/05/countries-agree-key-measures-to-fund-most-vulnerable-to-climate-breakdown
MONDAY, NOVEMBER 2, 1942Dear Kitty,Bep stayed with us Friday evening. It was fun, but she didn’t sleepvery well because she’d drunk some wine. For the rest, there’snothing special to report. I had an awful headache yesterday andwent to bed early. Margot’s being exasperating again.This morning I began sorting out an index card �le from theo�ce, because it’d fallen over and gotten all mixed up. Before long Iwas going nuts. I asked Margot and Peter to help, but they were toolazy, so I put it away. I’m not crazy enough to do it all by myself!Anne Frank
In a diary entry dated Monday, November 2, 1942, Anne Frank in an entry in which she includes a post script about the "important news that [she's] probably going to get [her] period soon." she mentions spending some time sorting out an index card file. Presumably it had been used for business purposes as she mentions that she got it from the office. Given that it had "fallen over and gotten all mixed up", it presumably didn't use a card rod to hold the cards in. It must have been a fairly big task as she asked for help from two people and not getting it, she abandoned the task because, as she wrote: "I'm not crazy enough to do it all by myself!"
found via:
<script async src="https://platform.twitter.com/widgets.js" charset="utf-8"></script>Niklas Luhmann rejected out of town teaching positions for fear that his hard copy / analog zettelkasten might get destroyed in the moving process 🧵
— Bob Doto (@thehighpony) August 19, 2022
<script async src="https://platform.twitter.com/widgets.js" charset="utf-8"></script>"He rejected a number of other universities' interests in hiring him...at an early stage, arguing that he couldn't risk taking his Zettelkasten with him in the event of an accident to lose by car, ship, train or plane." https://t.co/SmK2gLJpQ0
— Bob Doto (@thehighpony) August 19, 2022
reference ostensibly in this text, but may need to hunt it down.
Bob confirmed that it was Luhmann Handbuch: Leben, Werk, Wirkung, 2012
As someone who lost multiple notebooks to water (I love typhoon season), I will actively refute the claim that an analog zettelkasten is more secure than a digital one1[3:05 AM] Both have weaknesses, both die to water[3:05 AM] The distinction comes from how much water is necessary for them to die
—Halleyscomet08 on 2023-07-07 3:05 AM at https://discord.com/channels/686053708261228577/979886299785863178/1126816131659878491
This joke card has a comic clipped from a newspaper glued to it. During the digitization process, the index card was put in a clear Mylar sleeve to prevent the comic, with its brittle glue, from being damaged or separated from the card.
The potential separation of newspaper clippings from index cards and their attendant annotations/meta data (due to aging of glue) can be a potential source of note loss when creating a physical card index.
In the documentary California Typewriter (Gravitas Pictures, 2016) musician John Mayer mentions that he's never lost a typed version of his notes, while digital versions of his work essentially remain out of sight and thus out of mind or else they risk digital erasure by means of either data loss, formatting changes, or other damage.
Mayer also mentions that he loves typewriters for their ability to easily get out stream of consciousness thinking which is a mode of creativity he prefers for writing lyrics.
Die aktuellen Vorbereitungen eines Fonds zum Ausgleich von Loss and Damage durch die Klimakrise berücksichtigen die Bedürfnisse von Ländern mit mittlerem Einkommen zu wenig. Der Präsident der karibischen Entwicklungsbank, Hyginus Leon, weist in einem Interview mit dem Guardian darauf hin, dass auch viele dieser Länder so verwundbar sind, dass sie die nötigen Maßnahmen nach und gegen – nicht von ihnen verursachte – Katastrophen nicht finanzieren können. https://www.theguardian.com/environment/2023/jul/28/mid-income-developing-countries-risk-losing-out-on-climate-rescue-funds-banker-warns
ble to pay $170tn in climate reparations by 2050 to ensure targets to curtail climate breakdown are met, a new study calculates.
Eine neue Studie hat erstmals berechtigt, wieviele Klima-Reparationen die Industrieländer, die die meisten Emissionen verursacht haben, an Staaten des globalen Südens bezahlen müssten. In der Summe sind es 170 Billionen US-Dollar. Berechnet wird, welchen wirtschaftlichen Verlust ärmere Länder ausgleichen müssen, weil ihnen fossile Energien nicht mehr zur Verfügung stehen. Daei wird der Verbrauch seit 1060 zugrundegelegt. https://www.theguardian.com/environment/2023/jun/05/climate-change-carbon-budget-emissions-payment-usa-uk-germany
Edit: also, my antinet gaining some personality points by having parrot bite marks here and there. ‘:D
via u/nagytimi85 at https://www.reddit.com/r/antinet/comments/13s84q3/comment/jlof6b9/?utm_source=reddit&utm_medium=web2x&context=3
File this one under the most bizarre potential note collection damage vector: a parrot who bites index cards!
In the 20th century it mostly came to be regarded like graffiti: something polite and respectful people did not do.AdvertisementContinue reading the main storyPaul F. Gehl, a curator at the Newberry, blamed generations of librarians and teachers for “inflicting us with the idea” that writing in books makes them “spoiled or damaged.”
One idea to store pictures of an analog Zettelkasten: Tropy - it's a side project to Zotero. https://tropy.org/
—u/stockwestfale at https://www.reddit.com/r/antinet/comments/12jjsgl/about_archiving_my_analog_zettelkasten/
The TLL was moved to a monastery in Bavaria during WWII because they were worried that the building that contained the zettelkasten would be bombed and it actually was.
The slips have been microfilmed and a copy of them is on store at Princeton as a back up just i case.
[01:17:00]
Related here is the horcrux problem of note taking or even social media. The mental friction of where did I put that thing? As a result, it's best to put it all in one place.
How can you build on a single foundation if you're in multiple locations? The primary (only?) benefit of multiple locations is redundancy in case of loss.
Ryan Holiday and Robert Greene are counter examples, though Greene's books are distinct projects generally while Holiday's work has a lot of overlap.
Wie durch ein Wunder blieben vier Holzkisten mit hochbrisantem Inhalt verschont. Sie waren zum Zeitpunkt des Infernos in einem anderen Gebäude eingelagert. Sie enthielten 20'000 Gästekarten, die Concierges und Rezeptionisten zwischen 1920 und 1960 heimlich geführt hatten.
Google translate:
four wooden boxes with highly explosive contents were spared. They were stored in a different building at the time of the inferno. They contained 20,000 guest cards that concierges and receptionists had kept secretly between 1920 and 1960.
The Grandhotel Waldhaus burned down in 1989, but saved from the inferno were 20,000 guest cards with annotations about them that were compiled between 1920 and 1960.
At the Grandhotel Waldhaus in Vulpera, Switzerland concierges and receptionists maintained a business-focused zettelkasten of cards. In addition to the typical business function these cards served denoting names, addresses, and rooms, the staff also made annotations commenting on the guests and their proclivities.

1: 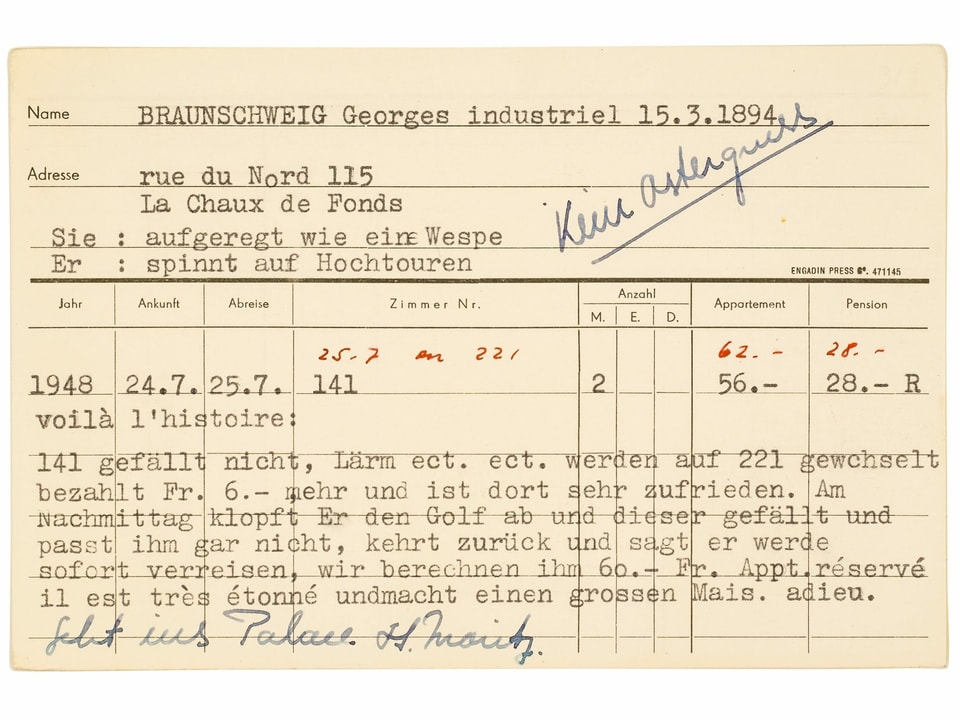
2: 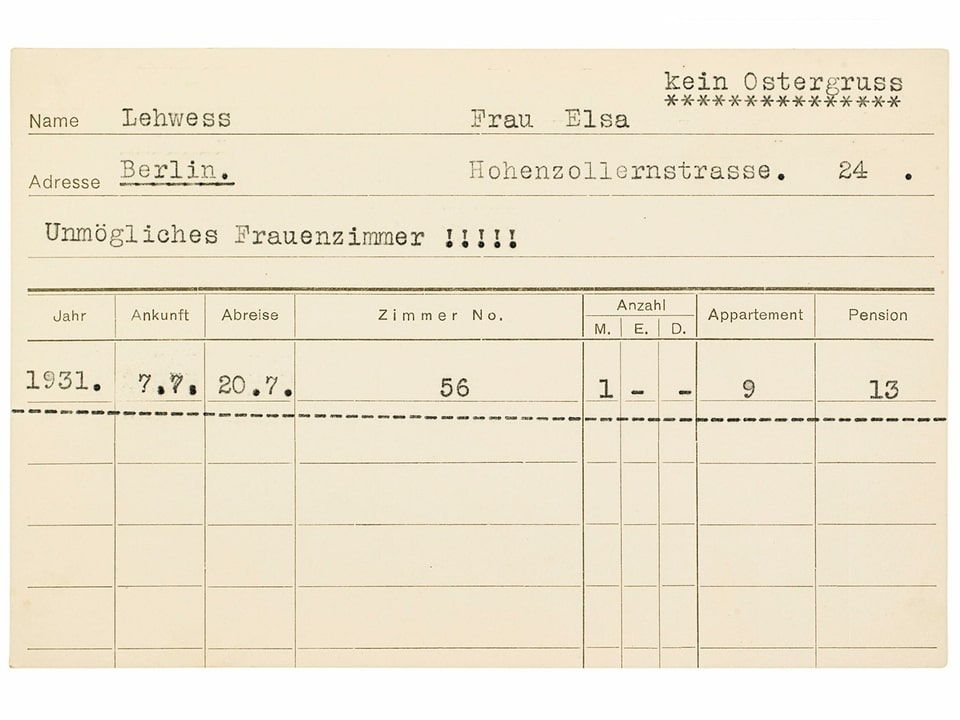
3: 
4: 
5:
6: 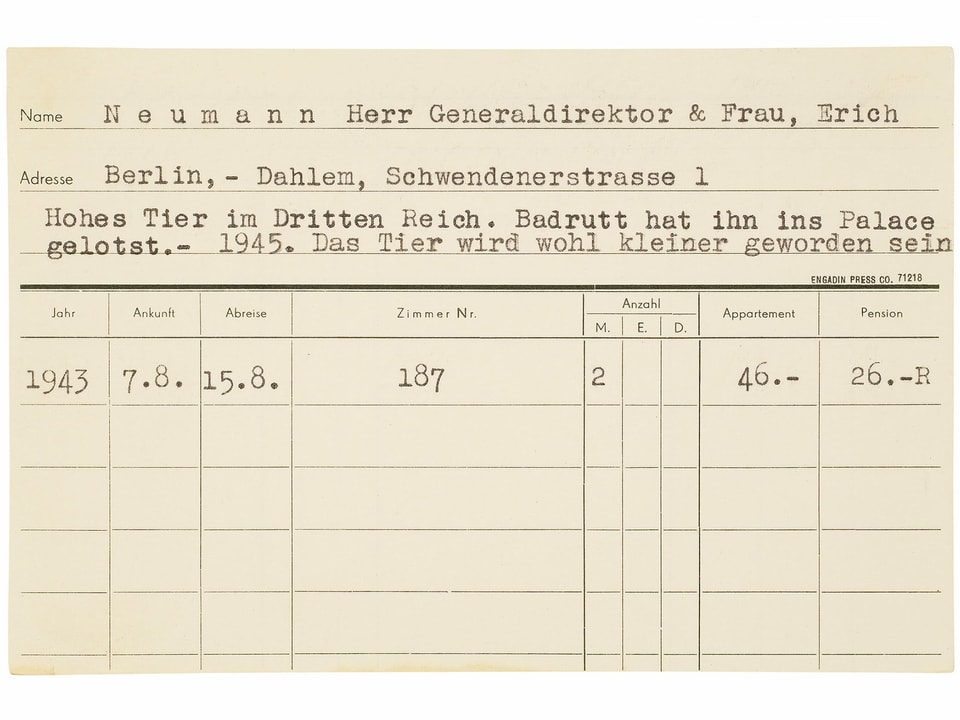
Note 9/8j says - "There is a note in the Zettelkasten that contains the argument that refutes the claims on every other note. But this note disappears as soon as one opens the Zettelkasten. I.e. it appropriates a different number, changes position (or: disguises itself) and is then not to be found. A joker." Is he talking about some hypothetical note? What did he mean by disappearing? Can someone please shed some light on what he really meant?
9/8j Im Zettelkasten ist ein Zettel, der das Argument enthält, das die Behauptungen auf allen anderen Zetteln widerlegt.
Aber dieser Zettel verschwindet, sobald man den Zettelkasten aufzieht.
D.h. er nimmt eine andere Nummer an, verstellt sich und ist dann nicht zu finden.
Ein Joker.
—Niklas Luhmann, ZK II: Zettel 9/8j
Translation:
9/8j In the slip box is a slip containing the argument that refutes the claims on all the other slips. But this slip disappears as soon as you open the slip box. That is, he assumes a different number, disguises himself and then cannot be found. A joker.
Many have asked about the meaning of this jokerzettel over the past several years. Here's my slightly extended interpretation, based on my own practice with thousands of cards, about what Luhmann meant:
Imagine you've spent your life making and collecting notes and ideas and placing them lovingly on index cards. You've made tens of thousands and they're a major part of your daily workflow and support your life's work. They define you and how you think. You agree with Friedrich Nietzsche's concession to Heinrich Köselitz that “You are right — our writing tools take part in the forming of our thoughts.” Your time is alive with McLuhan's idea that "The medium is the message." or in which his friend John Culkin said, "We shape our tools and thereafter they shape us."
Eventually you're going to worry about accidentally throwing your cards away, people stealing or copying them, fires (oh! the fires), floods, or other natural disasters. You don't have the ability to do digital back ups yet. You ask yourself, can I truly trust my spouse not to destroy them?,What about accidents like dropping them all over the floor and needing to reorganize them or worse, the ghost in the machine should rear its head?
You'll fear the worst, but the worst only grows logarithmically in proportion to your collection.
Eventually you pass on opportunities elsewhere because you're worried about moving your ever-growing collection. What if the war should obliterate your work? Maybe you should take them into the war with you, because you can't bear to be apart?
If you grow up at a time when Schrodinger's cat is in the zeitgeist, you're definitely going to have nightmares that what's written on your cards could horrifyingly change every time you look at them. Worse, knowing about the Heisenberg Uncertainly Principle, you're deathly afraid that there might be cards, like electrons, which are always changing position in ways you'll never be able to know or predict.
As a systems theorist, you view your own note taking system as a input/output machine. Then you see Claude Shannon's "useless machine" (based on an idea of Marvin Minsky) whose only function is to switch itself off. You become horrified with the idea that the knowledge machine you've painstakingly built and have documented the ways it acts as an independent thought partner may somehow become self-aware and shut itself off!?!
https://www.youtube.com/watch?v=gNa9v8Z7Rac
And worst of all, on top of all this, all your hard work, effort, and untold hours of sweat creating thousands of cards will be wiped away by a potential unknowable single bit of information on a lone, malicious card and your only recourse is suicide, the unfortunate victim of dataism.
Of course, if you somehow manage to overcome the hurdle of suicidal thoughts, and your collection keeps growing without bound, then you're sure to die in a torrential whirlwind avalanche of information and cards, literally done in by information overload.
But, not wishing to admit any of this, much less all of this, you imagine a simple trickster, a joker, something silly. You write it down on yet another card and you file it away into the box, linked only to the card in front of it, the end of a short line of cards with nothing following it, because what could follow it? Put it out of your mind and hope your fears disappear away with it, lost in your box like the jokerzettel you imagined. You do this with a self-assured confidence that this way of making sense of the world works well for you, and you settle back into the methodical work of reading and writing, intent on making your next thousands of cards.
He saw that her suitcase had shoved all his trays of slips over to one side of the pilot berth.They were for a book he was working on and one of the four long card-catalog-type trays wasby an edge where it could fall off. That's all he needed, he thought, about three thousand four-by-six slips of note pad paper all over the floor.He got up and adjusted the sliding rest inside each tray so that it was tight against the slipsand they couldn't fall out. Then he carefully pushed the trays back into a safer place in therear of the berth. Then he went back and sat down again.It would actually be easier to lose the boat than it would be to lose those slips. There wereabout eleven thousand of them. They'd grown out of almost four years of organizing andreorganizing and reorganizing so many times he'd become dizzy trying to fit them all together.He'd just about given up.
Worry about dropping a tray of slips and needing to reorganize them.
https://www.youtube.com/watch?v=SYj1jneBUQo
Forrest Perry shows part of his note taking and idea development process in his hybrid digital-analog zettelkasten practice. He's read a book and written down some brief fleeting notes on an index card. He then chooses a few key ideas he wants to expand upon, finds the physical index card he's going to link his new idea to, then reviews the relevant portion of the book and writes a draft of a card in his notebook. Once satisfied with it, he transfers his draft from his notebook into Obsidian (ostensibly for search and as a digital back up) where he may also be refining the note further. Finally he writes a final draft of his "permanent" (my framing, not his) note on a physical index card, numbers it with respect to his earlier card, and then (presumably) installs it into his card collection.
In comparison to my own practice, it seems like he's spending a lot of time after-the-fact in reviewing over the original material to write and rewrite an awful lot of material for what seems (at least to me—and perhaps some of it is as a result of lack of interest in the proximal topic), not much substance. For things like this that I've got more direct interest in, I'll usually have a more direct (written) conversation with the text and work out more of the details while reading directly. This saves me from re-contextualizing the author's original words and arguments while I'm making my arguments and writing against the substrate of the author's thoughts. Putting this work in up front is often more productive at least for areas of direct interest. I would suspect that in Perry's case, he was generally interested in the book, but it doesn't impinge on his immediate areas of research and he only got three or four solid ideas out of it as opposed to a dozen or so.
The level of one's conversation with the text will obviously depend on their interest and goals, a topic which is relatively well laid out by Adler & Van Doren (1940).
Before they were sent, however, the contents of itstwenty-six drawers were photographed in Princeton, resulting in thirty mi-crofilm rolls. Recently, digital pdf copies of these microfilm rolls have been
circulating among scholars of the documentary Geniza.
Prior to being shipped to the National Library of Israel, Goitein's index card collection was photographed in Princeton and transferred to thirty microfilm rolls from which digital copies in .pdf format have been circulating among scholars of the documentary Geniza.
Link to other examples of digitized note collections: - Niklas Luhmann - W. Ross Ashby - Jonathan Edwards
Are there collections by Charles Darwin and Linnaeus as well?
https://youtu.be/VFs3_COOMp8?t=1130
He mentions (not seriously) getting into a spat with his wife who threatens to throw his zettelkasten out the window as a means of retaliation! 🤣
https://youtu.be/VFs3_COOMp8?t=1103
Mention of worry over losing a zettelkasten due to fire or water damage, versus digital loss due to electric/power failure.
Hard drive failure and lack of back ups are also a problem.
even Socrates himself, we learnby way of his followers, derided the emerging popularity of taking physicalnotes.
I recall portions about Socrates deriding "writing" as a mode of expression, but I don't recall specific sections on note taking. What is Ann Blair's referent for this?
The "emerging popularity of taking physical notes" seems not to be in evidence with only one exemplar of a student who lost their notes within the Blair text.
DanAllosso · 36 min. agoThanks, Scott! I'll have a Scrintal "board" with photographed analog notes to show soon, too. Solved the fire and flood problem.
I continued to use this analog method right up through my Ph.D. dissertation and first monograph. After a scare in the early stages of researching my second monograph, when I thought all of my index cards had been lost in a flood, I switched to an electronic version: a Word doc containing a table with four cells that I can type or paste information into (and easily back up).
NER * Helix distortion * ERCC6 and 8 mutation -- Cockayne's syndrome * XP proteins (XPE or DDB2, XPC, XPA) mutated in xeroderma pigmentosum. * TFIIH, the same helicases as seen in DNA replication.
BER * For non-helix distorting base lesions. * Base is not present, a gap is present in DNA. * Specific DNA glycosylases used for identification. * APEX1 and APEX2 (AP endonucleases): responsible for end processing * An AP site (apurinic/apyrimidinic site). * The exposed 3' OH is available to a replicative polymerase. * Ligation performed by ligase * Short or long patch BER is possible.
In HR, * MRN -- begginings of dsDNA resection. * The PARP1 protein is active on ssDNA. * Free 3' ends made available, crucial for later DNA pol binding. * RPA binds, coats, the ssDNA.<br /> * Rad51 searches for strand for invasion. * Strand invasion carried out by sister chromatid, etc. * D-loop formation.
May have. * DSBR * SDSA * BIR
NHEJ relies on microhomologies. Doesn't require homologous sequence from another source. * Ku protein instrumental in identification of DSB and recruits DNA-PKcs. * DNa-PKcs autophosphorylates. * DNA ends processed by Artemis. * LIG4 and XCRR4 are needed for strand ligation.
NHEJ and HR can be compared.
"If the Reagans' home in Palisades (Calif.) were burning," Brinkley says, "this would be one of the things Reagan would immediately drag out of the house. He carried them with him all over like a carpenter brings their tools. These were the tools for his trade."
Another example of someone saying that if their house were to catch fire, they'd save their commonplace book (first or foremost).
He took it toWashington when he went into war service in 1917-1918;
Frederic Paxson took his note file from Wisconsin to Washington D.C. when he went into war service from 1917-1918, which Earl Pomeroy notes as an indicator of how little burden it was, but he doesn't make any notation about worries about loss or damage during travel, which may have potentially occurred to Paxson, given his practice and the value to him of the collection.
May be worth looking deeper into to see if he had such worries.
Filing is a tedious activity and bundles of unsorted notes accumulate. Some of them get loose and blow around the house, turning up months later under a carpet or a cushion. A few of my most valued envelopes have disappeared altogether. I strongly suspect that they fell into the large basket at the side of my desk full of the waste paper with which they are only too easily confused.
Relying on cut up slips of paper rather than the standard cards of equal size, Keith Thomas has relayed that his slips often "get loose and blow around the house, turning up months later under a carpet or cushion."
He also suspects that some of his notes have accidentally been thrown away by falling off his desk and into the nearby waste basket which camouflages his notes amongst similar looking trash.
I am less worried about natural disaster than my own negligence. I take the cards with me too much. I am not stationary in my office and so to use the cards I am taking them. I am afraid they will lost or destroyed. I have started to scan into apple notes. I will see how that goes. It is easy and might be a great overall solution.
episcopal-orthodox reply to: https://www.reddit.com/r/antinet/comments/y77414/comment/isyqc7b/
As long as you're not using flimsy, standard paper for your slips like Luhmann (they deteriorate too rapidly with repeated use), you can frame your carrying them around more positively by thinking that use over time creates a lovely patina to your words and ideas. The value of this far outweighs the fear of loss, at least for me. And if you're still concerned, there's always the option that you could use ars memoria to memorize all of your cards and meditate on them combinatorially using Llullan wheels the way Raymond Llull originally did. 🛞🗃️🚀🤩
Worried about paper cards being lost or destroyed .t3_y77414._2FCtq-QzlfuN-SwVMUZMM3 { --postTitle-VisitedLinkColor: #9b9b9b; --postTitleLink-VisitedLinkColor: #9b9b9b; --postBodyLink-VisitedLinkColor: #989898; } I am loving using paper index cards. I am, however, worried that something could happen to the cards and I could lose years of work. I did not have this work when my notes were all online. are there any apps that you are using to make a digital copy of the notes? Ideally, I would love to have a digital mirror, but I am not willing to do 2x the work.
u/LBHO https://www.reddit.com/r/antinet/comments/y77414/worried_about_paper_cards_being_lost_or_destroyed/
As a firm believer in the programming principle of DRY (Don't Repeat Yourself), I can appreciate the desire not to do the work twice.
Note card loss and destruction is definitely a thing folks have worried about. The easiest thing may be to spend a minute or two every day and make quick photo back ups of your cards as you make them. Then if things are lost, you'll have a back up from which you can likely find OCR (optical character recognition) software to pull your notes from to recreate them if necessary. I've outlined some details I've used in the past. Incidentally, opening a photo in Google Docs will automatically do a pretty reasonable OCR on it.
I know some have written about bringing old notes into their (new) zettelkasten practice, and the general advice here has been to only pull in new things as needed or as heavily interested to ease the cognitive load of thinking you need to do everything at once. If you did lose everything and had to restore from back up, I suspect this would probably be the best advice for proceeding as well.
Historically many have worried about loss, but the only actual example of loss I've run across is that of Hans Blumenberg whose zettelkasten from the early 1940s was lost during the war, but he continued apace in another dating from 1947 accumulating over 30,000 cards at the rate of about 1.5 per day over 50 some odd years.
"In the event of a fire, the black-bound excerpts are to be saved first," instructed the poet Jean Paul to his wife before setting off on a trip in 1812.
Writer Jean Paul on the importance of his Zettelkasten.
»Bei Feuer sind die schwarzeingebundnen Exzerpten zuerst zu retten«, wies der Dichter Jean Paul seine Frau vor Antritt einer Reise im Jahr 1812 an.
"In the event of a fire, the black-bound excerpts are to be saved first," the poet Jean Paul instructed his wife before setting out on a journey in 1812.
https://www.reddit.com/r/antinet/comments/ur5xjv/handwritten_cards_to_a_digital_back_up_workflow/
For those who keep a physical pen and paper system who either want to be a bit on the hybrid side, or just have a digital backup "just in case", I thought I'd share a workflow that I outlined back in December that works reasonably well. (Backups or emergency plans for one's notes are important as evidenced by poet Jean Paul's admonition to his wife before setting off on a trip in 1812: "In the event of a fire, the black-bound excerpts are to be saved first.") It's framed as posting to a website/digital garden, but it works just as well for many of the digital text platforms one might have or consider. For those on other platforms (like iOS) there are some useful suggestions in the comments section. Handwriting My Website (or Zettelkasten) with a Digital Amanuensis
What if something happened to your box? My house recently got robbed and I was so fucking terrified that someone took it, you have no idea. Thankfully they didn’t. I am actually thinking of using TaskRabbit to have someone create a digital backup. In the meantime, these boxes are what I’m running back into a fire for to pull out (in fact, I sometimes keep them in a fireproof safe).
His collection is incredibly important to him. He states this in a way that's highly reminiscent of Jean Paul.
"In the event of a fire, the black-bound excerpts are to be saved first." —instructions from Jean Paul to his wife before setting off on a trip in 1812 #
Blu-menberg’s first collection of note cards dates back to the early 1940s butwas lost during the war; the Marbach collection contains cards from 1947onwards. 18
18 Von Bülow and Krusche, “Vorla ̈ ufiges,” 273.
Hans Blumenberg's first zettelkasten dates to the early 1940s, but was lost during the war though he continued the practice afterwards. The collection of his notes housed at Marbach dates from 1947 onward.
There is a box stored in the German Literature Archive in Marbach, thewooden box Hans Blumenberg kept in a fireproof steel cabinet, for it con-tained his collection of about thirty thousand typed and handwritten notecards.1
Hans Blumenberg's zettelkasten of about thirty thousand typed and handwritten note cards is now kept at the German Literature Archive in Marbach. Blumenberg kept it in a wooden box which he kept in a fireproof steel cabinet.
Pyle, G., & Huang, J. H. (2022, January 17). Myocarditis: COVID-19 is a much bigger risk to the heart than vaccination. The Conversation. http://theconversation.com/myocarditis-covid-19-is-a-much-bigger-risk-to-the-heart-than-vaccination-174580
Marsh, S. (2021, December 1). Severe Covid infection doubles chances of dying in following year, study finds. The Guardian. https://www.theguardian.com/world/2021/dec/01/severe-covid-infection-doubles-chances-of-dying-in-following-year-study
bug bounty program
one ways to counter security flaws in SC is to incentivize bug hunting.
Instead of hiking the trail yourself, the trees, rocks and moss move past you in flashes with no trace of what came before and no way to see what lies ahead.
Just as there are deficits like dyslexia in the literate world, are there those who have similar deficits relating to location in the oral world? What do these look like? What are they called specifically?
There are definitely memory deficits withing cognitive neuropsychology. Is there a comprehensive list one could look at?
Some people aren't as good at spatial orientation as others. Women are stereotyped as being less good at direction and direction finding.
the things that cluster up top they were things like um 00:12:21 relationships uh character related things um and then like education but not from i want to go to the most elite school possible just i want to they want to get they want to get training to do things that matter to 00:12:33 them right they wanted purposeful lives and they want to be good people and let me give you one specific example so in the aggregate the number three most important trade-off priority for people this was this was just in the united 00:12:46 states was to be viewed as trustworthy [Music] like and yet they don't think anybody else really cares about it it's the third most important thing to 00:12:59 them and yet they don't think that it's like they think people would prioritize it very very low now think about the problem right i want to be trusted i believe i'm trustworthy but i don't think anybody else really cares and i don't really 00:13:12 think they're trustworthy how does how does a democracy function if we really don't think not only are people untrustworthy but that they don't even care about it and it's just not true so this is the kind of damage that illusions do to 00:13:24 societies
Collective illusions do great damage to society. Think about political polarization, climate change, the pandemic to name a few crisis marred by polarization.
Al Newman. (2022, March 8). @danaparish @jennybluebird2U To your point: Https://t.co/CsULpIACoI [Tweet]. @AlNewman_. https://twitter.com/AlNewman_/status/1501056062262333441
Geddes, L., & Sample, I. (2022, March 7). Covid can shrink brain and damage its tissue, finds research. The Guardian. https://www.theguardian.com/world/2022/mar/07/covid-can-shrink-brain-and-damage-its-tissue-finds-research
Spinney, L. (2022). Pandemics disable people—The history lesson that policymakers ignore. Nature, 602(7897), 383–385. https://doi.org/10.1038/d41586-022-00414-x
COVID-19 takes serious toll on heart health—A full year after recovery. (n.d.). Retrieved February 11, 2022, from https://www.science.org/content/article/covid-19-takes-serious-toll-heart-health-full-year-after-recovery
Yaneer Bar-Yam on Twitter. (n.d.). Twitter. Retrieved February 7, 2022, from https://twitter.com/yaneerbaryam/status/1474091037861761026
Nast, C. (2022, January 15). Do the Omicron Numbers Mean What We Think They Mean? The New Yorker. https://www.newyorker.com/magazine/2022/01/24/do-the-omicron-numbers-mean-what-we-think-they-mean
•. (n.d.). Even Mild COVID Infections Can Have Lasting Impacts Like ‘Chemo Brain,’ Study Finds. NBC New York. Retrieved 12 January 2022, from https://www.nbcnewyork.com/news/coronavirus/even-mild-covid-infections-can-have-lasting-impacts-like-chemo-brain-study-finds/3489958/
Wenzel, J., Lampe, J., Müller-Fielitz, H., Schuster, R., Zille, M., Müller, K., Krohn, M., Körbelin, J., Zhang, L., Özorhan, Ü., Neve, V., Wagner, J. U. G., Bojkova, D., Shumliakivska, M., Jiang, Y., Fähnrich, A., Ott, F., Sencio, V., Robil, C., … Schwaninger, M. (2021). The SARS-CoV-2 main protease Mpro causes microvascular brain pathology by cleaving NEMO in brain endothelial cells. Nature Neuroscience, 1–12. https://doi.org/10.1038/s41593-021-00926-1
Full Fact. ‘What Do We Know about the Covid-19 Vaccines Crossing the Placenta?’, 16:58:51+00:00. https://fullfact.org/pregnant-then-screwed/vaccines-crossing-placenta/.
Bloomberg Quicktake on Twitter: “70% of long Covid sufferers develop damage to at least one vital organ like the heart or liver, a new U.K. study found https://t.co/JrqG9zZ1UN” / Twitter. (n.d.). Retrieved September 28, 2021, from https://twitter.com/Quicktake/status/1442555369427984390
ReconfigBehSci. (2021, July 28). RT @trishgreenhalgh: ⬇️⬇️⬇️ Cower from this virus, or risk serious complications. It’s not a cold. Https://t.co/CN4hZYQwMw [Tweet]. @SciBeh. https://twitter.com/SciBeh/status/1420913883997360131
Facebook Sided With The Science Of The Coronavirus. What Will It Do About Vaccines And Climate Change? (n.d.). BuzzFeed News. Retrieved 11 February 2021, from https://www.buzzfeednews.com/article/alexkantrowitz/facebook-coronavirus-misinformation-takedowns
CNN, M. F. (n.d.). How coronavirus affects the entire body. CNN. Retrieved July 13, 2020, from https://www.cnn.com/2020/07/10/health/coronavirus-entire-body-effects-columbia/index.html
Blakemore, E. (n.d.). New diabetes cases linked to covid-19. Washington Post. Retrieved February 11, 2021, from https://www.washingtonpost.com/health/2021/02/01/covid-new-onset-diabetes/
Wilson, C. (n.d.). The coronavirus is leaving some people with permanent lung damage. New Scientist. Retrieved June 26, 2020, from https://www.newscientist.com/article/2247086-the-coronavirus-is-leaving-some-people-with-permanent-lung-damage/
‘Chinatown Businesses Face a Particularly Brutal Winter’. Bloomberg.Com, 7 December 2020. https://www.bloomberg.com/news/articles/2020-12-07/covid-19-has-been-a-disaster-for-u-s-chinatowns.
Greene, G. (1999). The Woman who Knew Too Much: Alice Stewart and the Secrets of Radiation. University of Michigan Press.
Geddes, L. (2020, November 15). Damage to multiple organs recorded in ‘long Covid’ cases. The Guardian. https://www.theguardian.com/world/2020/nov/15/damage-to-multiple-organs-recorded-in-long-covid-cases
Kaiser, F., Ronellenfitsch, H., & Witthaut, D. (2020). Discontinuous transition to loop formation in optimal supply networks. Nature Communications, 11(1), 5796. https://doi.org/10.1038/s41467-020-19567-2
Dennis, A., Wamil, M., Kapur, S., Alberts, J., Badley, A. D., Decker, G. A., Rizza, S. A., Banerjee, R., Banerjee, A., & Investigators, O. behalf of the C. study. (2020). Multi-organ impairment in low-risk individuals with long COVID. MedRxiv, 2020.10.14.20212555. https://doi.org/10.1101/2020.10.14.20212555
Long Covid: What we know so far. (2020, October 15). The Guardian. http://www.theguardian.com/world/2020/oct/15/long-covid-what-we-know-so-far
Building an Online Community for Behavioural Science COVID-19 Response – Prof. Ulrike Hahn. (2020, August 8). https://www.youtube.com/watch?v=noWjiDQSD14
Long after a Covid-19 infection, mental and neurological effects smolder. (2020, August 12). STAT. https://www.statnews.com/2020/08/12/after-covid19-mental-neurological-effects-smolder/
Thomas, K., & Rabin, R. C. (2020, October 4). Trump’s Treatment Suggests Severe Covid-19, Medical Experts Say. The New York Times. https://www.nytimes.com/2020/10/04/health/trump-covid-treatment.html
DNA damage-induced cell death: from specific DNA lesions to the DNA damage response and apoptosis
lit review
Nick Brown on Twitter. (n.d.). Twitter. Retrieved October 1, 2020, from https://twitter.com/sTeamTraen/status/1311282470084644865
Long-term effects of Covid include damage to heart, liver, kidneys. (2020, September 29). ITV News. https://www.itv.com/news/2020-09-29/long-covid-long-term-effects-of-coronavirus-include-damage-to-heart-liver-kidneys-oxford-study-reveals
Chu, H., Chan, J. F.-W., Yuen, T. T.-T., Shuai, H., Yuan, S., Wang, Y., Hu, B., Yip, C. C.-Y., Tsang, J. O.-L., Huang, X., Chai, Y., Yang, D., Hou, Y., Chik, K. K.-H., Zhang, X., Fung, A. Y.-F., Tsoi, H.-W., Cai, J.-P., Chan, W.-M., … Yuen, K.-Y. (2020). Comparative tropism, replication kinetics, and cell damage profiling of SARS-CoV-2 and SARS-CoV with implications for clinical manifestations, transmissibility, and laboratory studies of COVID-19: An observational study. The Lancet Microbe, 1(1), e14–e23. https://doi.org/10.1016/S2666-5247(20)30004-5
Barber, C. (n.d.). COVID-19 Can Wreck Your Heart, Even if You Haven’t Had Any Symptoms. Scientific American. Retrieved September 1, 2020, from https://www.scientificamerican.com/article/covid-19-can-wreck-your-heart-even-if-you-havent-had-any-symptoms/
Consiglio, C. R., Cotugno, N., Sardh, F., Pou, C., Amodio, D., Zicari, S., Ruggiero, A., Pascucci, G. R., Rodriguez, L., Santilli, V., Tan, Z., Eriksson, D., Wang, J., Lakshmikanth, T., Marchesi, A., Lakshmikanth, T., Campana, A., Villani, A., Rossi, P., … Brodin, P. (2020). The Immunology of Multisystem Inflammatory Syndrome in Children with COVID-19. MedRxiv, 2020.07.08.20148353. https://doi.org/10.1101/2020.07.08.20148353
Salahudeen, A. A., Choi, S. S., Rustagi, A., Zhu, J., O, S. M. de la, Flynn, R. A., Margalef-Català, M., Santos, A. J. M., Ju, J., Batish, A., Unen, V. van, Usui, T., Zheng, G. X. Y., Edwards, C. E., Wagar, L. E., Luca, V., Anchang, B., Nagendran, M., Nguyen, K., … Kuo, C. J. (2020). Progenitor identification and SARS-CoV-2 infection in long-term human distal lung organoid cultures. BioRxiv, 2020.07.27.212076. https://doi.org/10.1101/2020.07.27.212076
Zhou, Dong, and Amir Bashan. ‘Dependency-Based Targeted Attacks in Interdependent Networks’. Physical Review E 102, no. 2 (3 August 2020): 022301. https://doi.org/10.1103/PhysRevE.102.022301.
West, D. K. & G. (2020, July 8). The Damage We’re Not Attending To. Nautilus. http://nautil.us/issue/87/risk/the-damage-were-not-attending-to
These Canadians say they suffered COVID-19 symptoms for months. (n.d.). Global News. Retrieved July 5, 2020, from https://globalnews.ca/news/7107137/coronavirus-long-term-symptoms/
writers, G. (2020, June 18). World spends to protect culture from economic ruin. The Guardian. https://www.theguardian.com/culture/2020/jun/18/world-spends-to-protect-culture-from-economic-ruin
Horton, R. (2020). Offline: CoHERE—a call for a post-pandemic health strategy. The Lancet, 395(10232), 1242. https://doi.org/10.1016/S0140-6736(20)30895-3
If easy-to-use software like Signal somehow became inaccessible, the security of millions of Americans (including elected officials and members of the armed forces) would be negatively affected.
health, L. B. closeLenny B. covering, & medicineEmailEmailBioBioFollowFollow. (n.d.). More evidence emerges on why covid-19 is so much worse than the flu. Washington Post. Retrieved May 31, 2020, from https://www.washingtonpost.com/health/more-evidence-emerges-on-why-covid-19-is-so-much-worse-than-the-flu/2020/05/21/e7814588-9ba5-11ea-a2b3-5c3f2d1586df_story.html
This approach decreases the collateral damage that one team’s non-deterministic tests have on other teams.
The key change here is the removal of an intent to defraud and replacing it with willfully; it will be illegal to share this information as long as you have any reason to know someone else might use it for unauthorized computer access.It is troublesome to consider the unintended consequences resulting from this small change.
The problem is that it is that the laws themselves change the very definition of a criminal and put many innocent professionals at risk.
As serious leaks become more common, surely we can expect tougher laws. But these laws are also making it difficult for those of us who wish to improve security by studying actual data. For years we have fought increasingly restrictive laws but the government’s argument has always been that it would only affect criminals.
Another approach I toyed with (very transiently) was blocking entire countries from accessing the API. I was always really hesitant to do this, but when 90% of the API traffic was suddenly coming from a country in West Africa, for example, that was a pretty quick win.
The term has also been borrowed by the computing community to refer to the refusal of service to legitimate users when administrators take blanket preventative measures against some individuals who are abusing systems. For example, Realtime Blackhole Lists used to combat email spam generally block ranges of Internet Protocol (IP) addresses rather than individual IPs associated with spam, which can deny legitimate users within those ranges the ability to send email to some domains.
even a 1-kiloton blast would be a catastrophic event, having a deadly radius between one-third and one-half that of a 10-kiloton blast
Mass Spectrometry of Structurally Modified DNA
extensive review