Updates/edits based on comments should preferably be reflected in the question itself. This way other readers don't have to weed out the whole comment section. You find the edit option under the question.
- Jan 2022
-
stackoverflow.com stackoverflow.com
-
-
news.ycombinator.com news.ycombinator.com
-
Yes, precisely because I've been involved in maintaining codebases built without real full stack frameworks is why I say what I said.The problem we have in this industry, is that somebody reads these blog posts, and the next day at work they ditch the "legacy rails" and starts rewriting the monolith in sveltekit/nextjs/whatever because that's what he/she has been told is the modern way to do full stack.No need to say those engineers will quit 1 year later after they realize the mess they've created with their lightweight and simple modern framework.I've seen this too many times already.It is not about gatekeeping. It is about engineers being humble and assume it is very likely that their code is very unlikely to be better tested, documented, cohesive and maintained than what you're given in the real full stack frameworks.Of course you can build anything even in assembler if you want. The question is if that's the most useful thing to do with your company's money.
-
-
stackoverflow.com stackoverflow.com
-
Checks are usually done in this order: 404 if resource is public and does not exist or 3xx redirection OTHERWISE: 401 if not logged-in or session expired 403 if user does not have permission to access resource (file, json, ...) 404 if resource does not exist or not willing to reveal anything, or 3xx redirection
-
-
-
The spider web system was, in fact, a work in progress; the resulting hypertext was designed to be open-ended.
One's lifetime of notes could be thought of as a hypertext work in progress that is designed to be open-ended.
Tags
Annotators
-
-
learn-us-east-1-prod-fleet01-xythos.content.blackboardcdn.com learn-us-east-1-prod-fleet01-xythos.content.blackboardcdn.com
-
Even finding terms totranslate concepts like ‘lord’, ‘commandment’ or ‘obedience’ intoindigenous languages was extremely difficult; explaining theunderlying theological concepts, well-nigh impossible.
Example of the difficulty of translating words when the underlying concepts don't exist in a culture.
-
-
prospect.org prospect.org
-
DrPH, M. D. H., M. D. (2022, January 11). The Folly of School Openings as a Zero-Sum Game. The American Prospect. https://prospect.org/api/content/4a1fc36e-7263-11ec-9e7d-12f1225286c6/
Tags
- virtual learning
- priviledge
- economic oppression
- race
- economy
- work from home
- safety
- lang:en
- COVID-19
- transmission
- white supremacy
- education
- risk
- multigenerational family structure
- systemic racism
- people of colour
- homeschooling
- perception
- remote learning
- school closure
- ventilation
- USA
- school
- paediatric hospitalization
- is:webpage
- online learning
- disparity
- Omicron
- vaccine
- exposure
- children
- low-income
- in-person schooling
- mortality
Annotators
URL
-
-
psyarxiv.com psyarxiv.com
-
Benson-Greenwald, T., Trujillo, A., White, A., & Diekman, A. (2021). Science for Others or the Self? Presumed Motives for Science Shape Public Trust in Science. PsyArXiv. https://doi.org/10.31234/osf.io/yjvbw
-
-
quantifiedself.com quantifiedself.com
-
Developing a skill, such as data visualization,
my self data project is an internet methodion (a methodic ritual almost religion) that consists of self-improvement through engaging in constructive neocultural practices that are focused on novel, alternative and provocative ideas to create a critical citizin in a society.
Tags
Annotators
URL
-
- Dec 2021
-
www.xml.com www.xml.com
-
Of the many brilliant individual XML leaders from the early days, almost all have moved focus to entirely different technologies. Almost all the companies who sponsored the efforts of these leaders have moved on to different strategic initiatives, seeking competitive advantage elsewhere now that XML has lost its fairy sheen.
-
-
luhmann.surge.sh luhmann.surge.sh
-
The possibility of arbitrary internal branching.
Modern digital zettelkasten don't force the same sort of digital internal branching process that is described by Niklas Luhmann. Internal branching in these contexts is wholly reliant on the user to create it.
Many digital systems will create a concrete identifier to fix the idea within the system, but this runs the risk of ending up with a useless scrap heap.
Some modern systems provide the ability for one to add taxonomies like subject headings in a commonplace book tradition, which adds some level of linking. But if we take the fact that well interlinked cards are the most valuable in such a system then creating several links upfront may be a bit more work, but it provides more value in the long run.
Upfront links also don't require quite as much work at the card's initial creation as the creator already has the broader context of the idea. Creating links at a future date requires the reloading into their working memory of the card's idea and broader context.
Of course there may also be side benefits (including to memory) brought by the spaced repetition of the card's ideas as well as potential new contexts gained in the interim which may help add previously unconsidered links.
It can certainly be possible that at some level of linking, there is a law of diminishing returns the decreases the value of a card and its idea.
One of the benefits of physical card systems like Luhmann's is that the user is forced to add the card somewhere, thus making the first link of the idea into the system. Luhmann's system in particular creates a parent/sibling relation to other cards or starts a brand new branch.
-
-
boook.link boook.link
-
This looks a lot like Linktree, but for books.
Tags
Annotators
URL
-
-
www.instagram.com www.instagram.com
-
https://www.instagram.com/p/CXH2-x3Jt1S/
Hilarious!
Tags
Annotators
URL
-
-
learn-us-east-1-prod-fleet01-xythos.content.blackboardcdn.com learn-us-east-1-prod-fleet01-xythos.content.blackboardcdn.com
-
But we often find such regional networks developinglargely for the sake of creating friendly mutual relations, or having anexcuse to visit one another from time to time;33 and there are plentyof other possibilities that in no way resemble ‘trade’.
There is certainly social lubrication of visiting people from time to time which can help and advance societies, but this regular visiting can also be seen as a means of reinforcing one's oral cultural history through spaced repetition.
It can be seen as "trade" but in a way that anthropologists have generally ignored for lack of imagination for what may have been actually happening.
-
Already tens of thousands of years ago, one can find evidence ofobjects – very often precious stones, shells or other items ofadornment – being moved around over enormous distances. Oftenthese were just the sort of objects that anthropologists would laterfind being used as ‘primitive currencies’ all over the world.
Is it also possible that these items may have served the purpose of mnemonic devices as a means of transporting (otherwise invisible) information from one area or culture to another?
Can we build evidence for this from the archaeological record?
Relate this to the idea of expanding the traditional "land, labor, capital" theory of economics to include "information" as a basic building block
-
-
-
most people trained in our subjects are aware of is the 00:28:22 phenomenon of slavery among non farming populations and actually the classic example is precisely that of the the indigenous societies of the Northwest Coast who are known to have kept slaves 00:28:36 who were actually hereditary slaves in their households which were organized on these highly stratified aristocratic sort of lines what nobody seems to have 00:28:48 been interested up to now is why this practice of keeping slaves seems to sort of fizzle out and stop as you head south into what is now broadly speaking the 00:29:00 area of coastal California
How many non-agricultural societies practiced slavery?
Apparently some indigenous societies on the American Northwest Coast did down into coastal California.
-
-
www.jstor.org www.jstor.org
-
https://www.jstor.org/stable/26337970
Reviewed Work: Knowledge and Power in Prehistoric Societies: Orality, Memory, and the Transmission of Culture by LYNNE KELLY Review by: Asa R. https://www.jstor.org/stable/26337970
-
-
niklasblog.com niklasblog.com
-
Are you looking the best digital marketing expert in Bangalore
Best digital marketing expert in Bangalore, Aditya Aggarwal is India's top digital marketing guru. He is perhaps the most trusted figure in Best digital marketing expert in Bangalore, with a focus on giving customers outcomes through the digital media. I can assist you in growing your internet business as your online marketing specialist in India. My clients benefit from first-rate destinations, web advertising, lead generation, and a variety of other services that I provide.
In this post, we'll look at the most commonly asked questions and challenging areas, as well as how to direct and resolve them with the help of a Best digital marketing expert in Bangalore. Every firm in India is confronted with the challenge of promoting its products or services through digital marketing. Because the Indian market is genuine in terms of business errands and limits.
We understand the challenges that any company or organisation seeking the best digital marketing professional in Bangalore faces. We will have a separate discussion regarding Aditya Aggarwal's administration as the Best digital marketing expert in Bangalore. We are providing a massive display of digital marketing administrations in India to assist business proprietors and new business people.
As your Best digital marketing expert in Bangalore, I assist firms in attracting more customers by establishing finest zones that enhance their image, increase traffic to their website page, and develop their business online via the use of a show strategy. I'm a full-service internet marketing professional in India who can build and maintain your online business through SEO, Social Media, and Display campaigns, and I'm a right hand with outbound clients and contacts to execute marketing strategies, create content, and cultivate brand awareness.
Best digital marketing expert in Bangalore has built his digital marketing project from the perspective of the consequences of a culture that has been preserved in his submitted staff at Shoot Order and its interests. He's led missions of brands taking leisurely strolls around new domains or studied the paths of set-up marketing campaigns.
Aditya Aggarwal, the Best digital marketing expert in Bangalore, perhaps more than other experts in many industrial fields, does not accept the usual persona of getting his capacity from experience or intuition. He is reliant on a consistent design that maintains a proof-based concept and work measure.
-
Find the Best Startup consulting firms in India
Startup consulting firms in India and marketing service providers are rapidly growing, catering to various government locations as well as private SMEs, including new businesses. Business meeting, prototyping, R&D - Strategy Planning, Customized Web and Mobile Application Development Solutions, Web-GIS course of action, Branding and Digital Marketing Solutions are all included in the assistance with the outing case.
Change is the only constant. One of the challenges in this constantly changing world is the lack of a guiding ability to overcome these impediments to movement. Change, according to Startup consulting firms in India's startup consulting businesses, does not have to be a burden, but may actually be an empowering force for improvement. With a basic understanding of the internet, you have access to a wealth of information; however, the trick is knowing how and when to use it to help your business flourish. Startup consulting firms in India are specialists in execution, which is the best way to manage progressions.
In India, there are startup consulting services with the goal of transforming a CEO's movement vision into major, focal, and vital strategies that produce results. Our main goal is to assist organisations in rapidly accelerating their revenue growth.
It may be both exhilarating and overwhelming to start a new business. Startup consulting firms in Indiacurrent genuine environment, business people and innovators rely on starting projects and reaching to market as quickly as possible – yet they can get bogged down and relegated to a back seat due to administrative or major obstacles that prevent them from concentrating on the big picture. So that they can meet with Indian startup consulting businesses.
Startup consulting firms in India are professionals in establishing new businesses and are well-versed in the requirements of today's projects. It's only a starting point for us. To ensure business success, Startup consulting firms in India stroll around you while implementing these techniques.
The business climate is always evolving. To start your partnership for an unrivalled tomorrow, you'll need authority and the wellbeing that comes with it. Maintaining bargains, marketing, company, or helpful significance necessitates more fundamental administrative considerations. Paying attention to less obvious nuances would be impossible to achieve because they would take up an enormous amount of trade time. More importantly, you will require the 'X FACTOR' that is required to take your business to the next level of execution with Startup consulting firms in India.
-
Who is the best Digital marketing consultant in Delhi NCR
Aditya Aggarwal, the Digital marketing consultant in Delhi NCR, is perhaps superior to most specialists in several industry fields. He does not accept the usual persona of getting his ability by experience or intuition. He is reliant on the dependable design's proof-based thought and work measurement. He has built his digital marketing project on a point of view on the aftereffects of a culture ingested in his Shoot Order submitted workforce and its interests.
Digital *marketing consultant* in Delhi NCR has a wide range of digital marketing affiliations, from fresh connections to top-of-mind brands. He's overseen missions of brands taking leisurely strolls across new domains or evaluated marketing campaigns that had been put up.
Any brand or association looking for a Digital marketing consultant in Delhi NCR can come to us for help. We'll have a separate talk regarding Aditya Aggarwal's administration as a digital marketing consultant in Delhi NCR. We are giving a fantastic demonstration of digital marketing administrations in India to assist business owners and new entrepreneurs.
In this piece, we'll look at the value of using a Digital marketing consultant in Delhi NCR to oversee and address the most widely observed questions and complex zones. Almost every business in India is confronted with the challenge of promoting its products or services through digital marketing. Because the Indian market is exceptionally real in terms of company endeavours and worth.
Aditya Aggarwal is one of India's most impressive Digital marketing consultant in Delhi NCR. He is arguably the most certain name in Digital marketing consultant in Delhi NCR, with an emphasis on giving consumers results through the digital media. I can assist you in growing your internet business as your online marketing consultant in India. As your digital marketing superstar in India, I assist firms in attracting more customers by developing best practises that enhance their image, increasing traffic to their website page, and encouraging their online association by developing a show strategy.
-
-
blogs.dickinson.edu blogs.dickinson.edu
-
Whatever dies, was not mixed equally
In Galen's medicine, disease and death were the consequence of a disproportion in one's constituent elements, the 4 humors: black bile, yellow bile, blood, and phlegm.
-
eye
The another spherical image in the poem
Each eye, which is able to be interpreted as each hemisphere, is really a perfect world because, though they are not combined into one, when facing each other, contains both lovers (the one who is reflected and one who reflects is in unity in the eye).
Source: The Visual Paradigm of 'The Good-Morrow': Donne's Cosmographical Glasse (1986)
-
-
www.quantamagazine.org www.quantamagazine.org
-
“That’s one of the exciting things about math,” said Jack Morava, a mathematician at Johns Hopkins University and the inventor of Morava K-theory. “You can go through a door and you wind up in a completely different universe. It’s very much like Alice in Wonderland.”
-
-
-
The card index appeared to be simply what it was: a wooden box for paper slips. On one of these file cards, Luhmann once summarized his own reflections on just such an experience: ‘People come, they see everything and nothing more than that, just like in porn movies; consequently, they leave disappointed’ (Figure 1).8
- Cf. Schmidt, ‘Luhmanns Zettelkasten’, 7. The heading of this file card is formulated in form of a question: ‘Geist im Kasten?’ (‘Does Spirit hide in the filing cabinet?’). Obviously, the answer is no. Many thanks to Johannes Schmidt for providing the image of this file card.
In a zettel in his system entitled "Does Spirit hide in the filing cabinet", Niklas Luhmann wrote the note: "People come, they see everything and nothing more than that, just like in porn movies; consequently, they leave disappointed." This is a telling story about the simplicity of the idea of a slip box (zettelkasten, card catalog, or commonplace book).
Niklas Luhmann, Zettelkasten II, index card no. 9/8,3
It's also a testament to the fact that the value of it is in the upfront work that is required in making valuable notes and linking them. Many end up trying out the simple looking system and then wonder why it isn't working for them. The answer is that they're not working for it.
Tags
Annotators
-
-
-
Deeply importing Svelte components is not supported. Either import all components from one entrypoint, or always stick to deep imports, otherwise it could cause multiple instance of the Svelte library running.
-
-
link.springer.com link.springer.com
-
Cryospheric and hydrological changes in combination with socioeconomic changes are threatening downstream water security (Drenkhan et al., 2019; IPCC, 2019). Glacial melting impacts river discharge and the availability of water in areas downstream and change in runoff pattern of rivers draining from the glaciated catchments (Table 4). Hydroelectric power generation depends completely on water availability, and any variability in flow pattern of rivers can have far-reaching consequences for energy security of the country. Available hydrological simulations indicate reduced rainfall and shrinkage of glacier, thereby leading to shortage of water supply for power generation and irrigation particularly in highly glaciated basins (Gautam et al., 2013). The increasing drought frequency combined with other environmental degradation has already affected the livelihoods particularly of smallholder farmers.
YEs!
-
-
-
The second volume of the Bibliotheca Universalis , published in 1548 under the title Pandectarum sive Partitionum Universalium , contains a list of keywords, ordered not by authors ’ names, but thematically. This intro-duces a classifi cation of knowledge on the one hand, and on the other hand offers orientation for the novice about patterns and keywords (so-called loci communes ) that help organize knowledge to be acquired.
Konrad Gessner's second edition of Bibliotheca Universalis in 1548 contains a list of keywords (loci communes) thus placing it into the tradition of the commonplace book, but as it is published for use by others, it accelerates the ability for others to find and learn about information in which they may have an interest.
Was there a tradition of published or manuscript commonplace books prior to this?
-
- Nov 2021
-
inst-fs-iad-prod.inscloudgate.net inst-fs-iad-prod.inscloudgate.net
-
And then they met— the offspring of Skywoman and the children of Eve— and the land around us bears the scars of that meeting, the echoes of our stories.
There's a subtle sense of repetition here. She frames the result of the meeting in two different cultures: a Western-centric one and an Indigenous one. The Western result is a "scar", but it's retranslated into "echoes of our stories" from the indigenous perspective.
-
Our elders say that ceremonies are the way we “remember to remember,”
The Western word "ceremony" is certainly not the best word for describing these traditions. It has too much baggage and hidden meaning with religious overtones. It's a close-enough word to convey some meaning to those who don't have the cultural background to understand the underlying orality and memory culture. It is one of those words that gets "lost in translation" because of the dramatic differences in culture and contextual collapse.
Most Western-based anthropology presumes a Western idea of "religion" and impinges it upon oral cultures. I would maintain that what we would call their "religion" is really an oral-based mnemonic tradition that creates the power of their culture through knowledge. The West mistakes this for superstitious religious practices, but primarily because we can't see (or have never been shown) the larger structures behind what is going on. Our hubris and lack of respect (the evils of the scala naturae) has prevented us from listening and gaining entrance to this knowledge.
I think that the archaeological ideas of cultish practices or ritual and religion are all more likely better viewed as oral practices of mnemonic tradition. To see this more easily compare the Western idea of the memory palace with the Australian indigenous idea of songline.
-
-
-
Forbes, P., Pronizius, E., Feneberg, A. C., Nater, U., Piperno, G., Silani, G., Stijovic, A., & Lamm, C. (2021). The benefits and limits of social interactions during COVID-19 lockdown. PsyArXiv. https://doi.org/10.31234/osf.io/ae6t9
-
-
asiasociety.org asiasociety.org
-
Huang, who has a background in paleography, warns that many characters do not function as a “signific,” a linguistic term indicating a relationship to the word’s meaning. Additionally, the meanings of numerous characters changed over time, or they were “loaned” to other words with separate meanings. Even though more than 86 percent of characters have radicals that also function as significs, Huang encourages teachers to understand some of the exceptions, saying, “It is all right for Chinese teachers not to lecture on these, but they have to know them because students may ask.”
More than 86% of characters in Chinese function as significs, a linguistic term indicating an association to the word's meaning. Sometimes these meanings can change with time and drift from original meanings.
The drift can be interesting and important from the perspective of historical linguistics as well as to give clues to changes in culture.
An example in English might be the use in computer user interfaces that include telephone handset images or old 3.5" floppy disk images used to respectively indicate "call" or "save" despite the fact that these items have either changed shape or are no longer commonly used.
-
-
www.lynnekelly.com.au www.lynnekelly.com.au
-
Over the years in academic settings I've picked up pieces of Spanish, French, Latin and a few odd and ends of other languages.
Six years ago we put our daughter into a dual immersion Japanese program (in the United States) and it has changed some of my view of how we teach and learn languages, a process which is also affected by my slowly picking up conversational Welsh using the method at https://www.saysomethingin.com/ over the past year and change, a hobby which I wish I had more targeted time for.
Children learn language through a process of contextual use and osmosis which is much more difficult for adults. I've found that the slowly guided method used by SSiW is fairly close to this method, but is much more targeted. They'll say a few words in the target language and give their English equivalents, then they'll provide phrases and eventually sentences in English and give you a few seconds to form them into the target language with the expectation that you try to say at least something, or pause the program to do your best. It's okay if you mess up even repeatedly, they'll say the correct phrase/sentence two times after which you'll repeat it again thus giving you three tries at it. They'll also repeat bits from one lesson to the next, so you'll eventually get it, the key is not to worry too much about perfection.
Things slowly build using this method, but in even about 10 thirty minute lessons, you'll have a pretty strong grasp of fluent conversational Welsh equivalent to a year or two of college level coursework. Your work on this is best supplemented with interacting with native speakers and/or watching television or reading in the target language as much as you're able to.
For those who haven't experienced it before I'd recommend trying out the method at https://www.saysomethingin.com/welsh/course1/intro to hear it firsthand.
The experience will give your brain a heavy work out and you'll feel mentally tired after thirty minutes of work, but it does seem to be incredibly effective. A side benefit is that over time you'll also build up a "gut feeling" about what to say and how without realizing it. This is something that's incredibly hard to get in most university-based or book-based language courses.
This method will give you quicker grammar acquisition and you'll speak more like a native, but your vocabulary acquisition will tend to be slower and you don't get any writing or spelling practice. This can be offset with targeted memory techniques and spaced repetition/flashcards or apps like Duolingo that may help supplement one's work.
I like some of the suggestions made in Lynne's post as I've been pecking away at bits of Japanese over time myself. There's definitely an interesting structure to what's going on, especially with respect to the kana and there are many similarities to what is happening in Japanese to the Chinese that she's studying. I'm also approaching it from a more traditional university/book-based perspective, but if folks have seen or heard of a SSiW repetition method, I'd love to hear about it.
Hopefully helpful by comparison, I'll mention a few resources I've found for Japanese that I've researched on setting out a similar path that Lynne seems to be moving.
Japanese has two different, but related alphabets and using an app like Duolingo with regular practice over less than a week will give one enough experience that trying to use traditional memory techniques may end up wasting more time than saving, especially if one expects to be practicing regularly in both the near and the long term. If you're learning without the expectation of actively speaking, writing, or practicing the language from time to time, then wholesale mnemotechniques may be the easier path, but who really wants to learn a language like this?
The tougher portion of Japanese may come in memorizing the thousands of kanji which can have subtly different meanings. It helps to know that there are a limited set of specific radicals with a reasonably delineable structure of increasing complexity of strokes and stroke order.
The best visualization I've found for this fact is the Complete Listing of the 214 Radicals and Major Variations from An Introduction to Japanese Kanji Calligraphy by Kunii Takezaki (Tuttle, 2005) which I copy below:
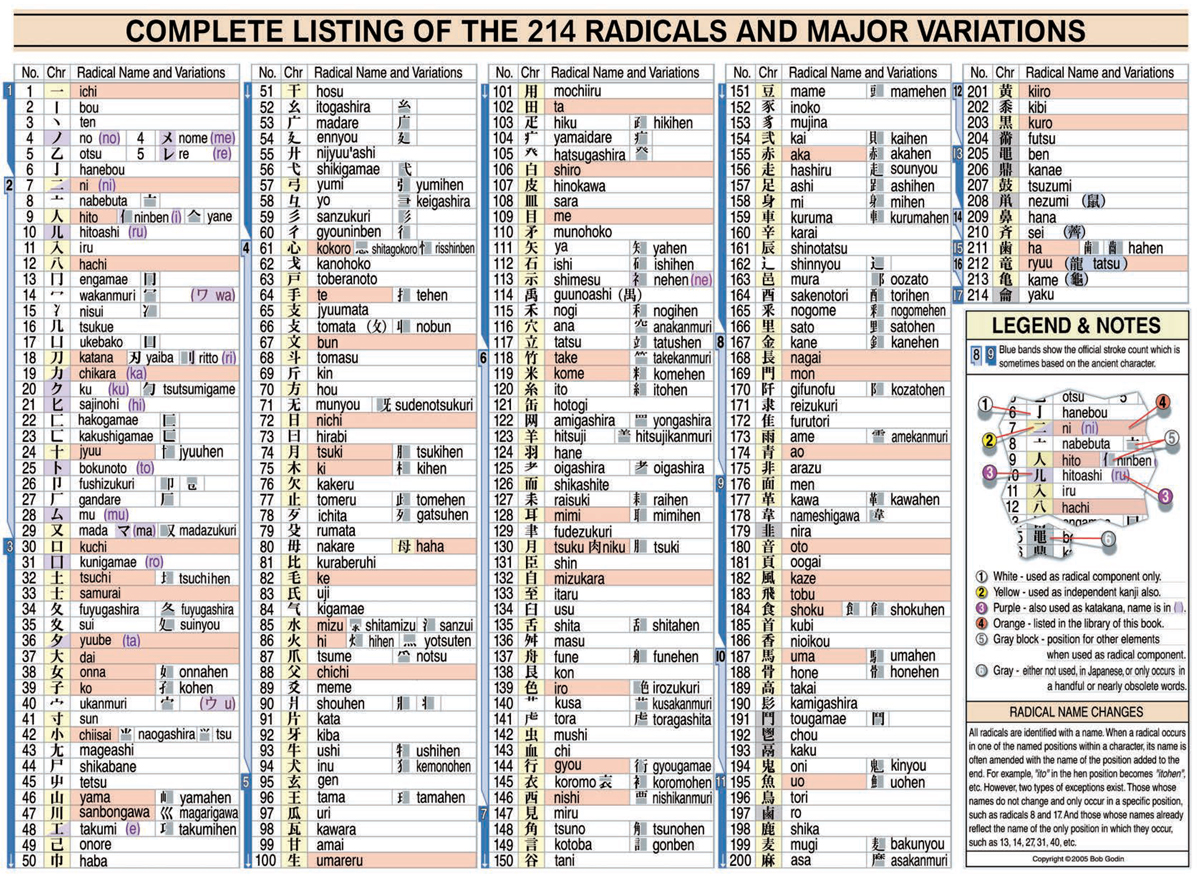
(Feel free to right click and view the image in another tab or download it and view it full size to see more detail.)
I've not seen such a chart in any of the dozens of other books I've come across. The numbered structure of increasing complexity of strokes here would certainly suggest an easier to build memory palace or songline.
I love this particular text as it provides an excellent overview of what is structurally happening in Japanese with lots of tidbits that are otherwise much harder won in reading other books.
There are many kanji books with various forms of what I would call very low level mnemonic aids. I've not found one written or structured by what I would consider a professional mnemonist. One of the best structured ones I've seen is A Guide to Remembering Japanese Characters by Kenneth G. Henshall (Tuttle, 1988). It's got some great introductory material and then a numbered list of kanji which would suggest the creation of a quite long memory palace/journey/songline.
Each numbered Kanji has most of the relevant data and readings, but provides some description about how the kanji relates or links to other words of similar shapes/meanings and provides a mnemonic hint to make placing it in one's palace a bit easier. Below is an example of the sixth which will give an idea as to the overall structure.
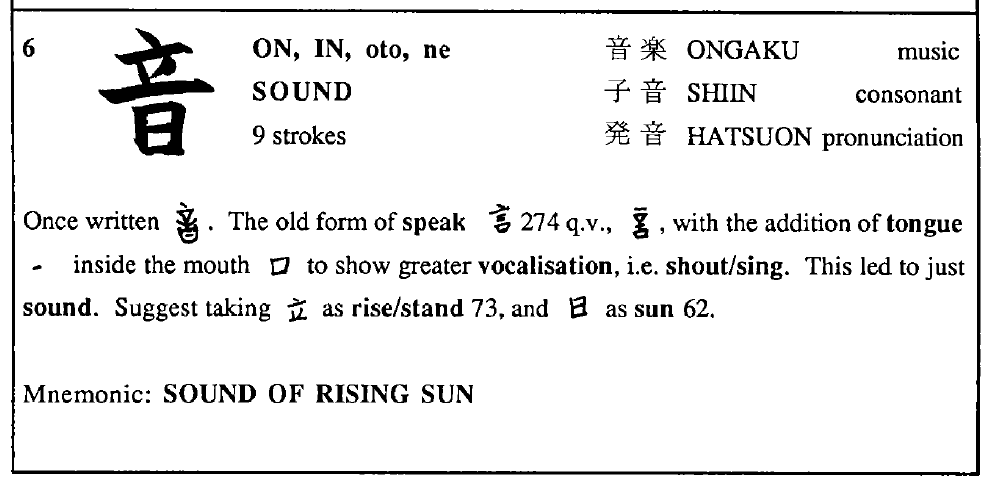
I haven't gotten very far into it yet, but I'd found an online app called WaniKani for Japanese that has some mnemonic suggestions and built-in spaced repetition that looks incredibly promising for taking small radicals and building them up into more easily remembered complex kanji.
I suspect that there are likely similar sources for these couple of books and apps for Chinese that may help provide a logical overall structuring which will make it easier to apply or adapt one's favorite mnemotechniques to make the bulk vocabulary memorization easier.
The last thing I'll mention I've found, that's good for practicing writing by hand as well as spaced repetition is a Kanji notebook frequently used by native Japanese speaking children as they're learning the levels of kanji in each grade. It's non-obvious to the English speaker, and took me a bit to puzzle out and track down a commercially printed one, even with a child in a classroom that was using a handmade version. The notebook (left to right and top to bottom) has sections for writing a big example of the learned kanji; spaces for the "Kun" and "On" readings; spaces for the number of strokes and the radical pieces; a section for writing out the stroke order as it builds up gradually; practice boxes for repeated practice of writing the whole kanji; examples of how to use the kanji in context; and finally space for the student to compose their own practice sentences using the new kanji.
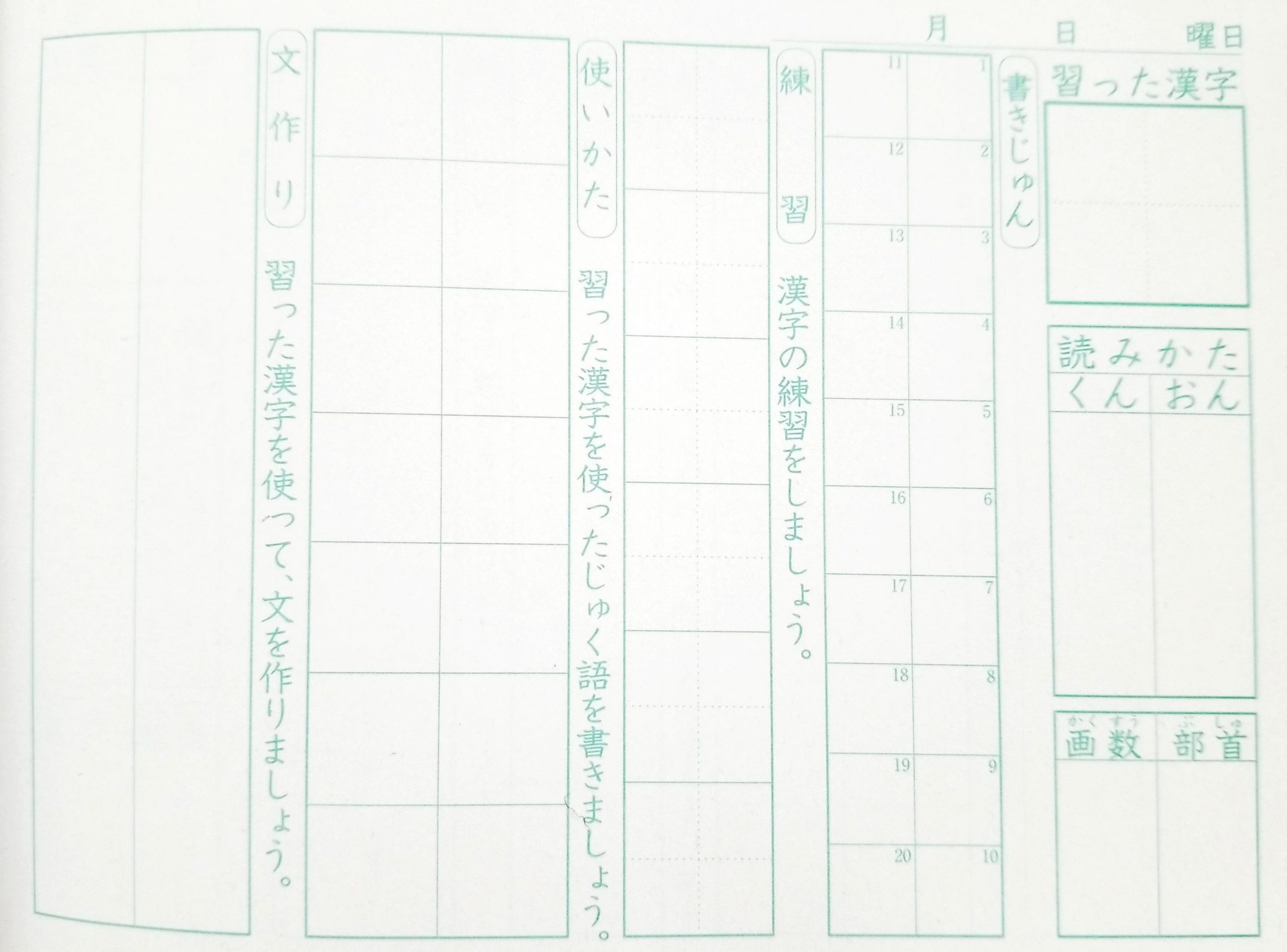
Regular use and practice with these can be quite helpful for moving toward mastery.
I also can't emphasize enough that regularly and actively watching, listening, reading, and speaking in the target language with materials that one finds interesting is incredibly valuable. As an example, one of the first things I did for Welsh was to find a streaming television and radio that I want to to watch/listen to on a regular basis has been helpful. Regular motivation and encouragement is key.
I won't go into them in depth and will leave them to speak for themselves, but two of the more intriguing videos I've watched on language acquisition which resonate with some of my experiences are:
-
-
hcommons.org hcommons.org
-
Students are also going through trauma. That will go under the mental health issues. The three deaths of students. We are still in a pandemic. Not to mention Tabor walking on campus and scolding us and telling us what we are doing wrong that could also be traumatic or very entertaining. Not only should we do the pass fail thing. But we should have better security. We should have better police. We should also have therapy sessions that deal with traumatic things that have been happening to us. Not only would just make us better students. This would make a better safe campus. And a lot of things have been going on in this fall semester. You know I’m still working on myself. It should not only be pass fail it should be we should work on campus as a whole.
-
-
www.nytimes.com www.nytimes.com
-
drive.google.com drive.google.com
-
interaction is most valued by teachers, but hindered by some students not using camera
despite teachers' lament, there is a compiling literature about the controversy: https://blog.stcloudstate.edu/ims/2021/07/13/dealing-with-digital-fatigue/ https://blog.stcloudstate.edu/ims/2021/01/15/why-turn-off-webcams/ https://blog.stcloudstate.edu/ims/2020/11/21/webcam-policies/
-
-
www.nytimes.com www.nytimes.com
-
There was no ancient poet called “Homer,” he argued. Nor were the poems attributed to him “written” by any single individual. Rather, they were the product of a centuries-long tradition of poet-performers.
Are there possibly any physical artifacts in physical archaeology that may fit into the structure of the thesis made by Lynne Kelly in Knowledge and Power in Prehistoric Societies?
What would we be looking for? Small mnemonic devices? Menhir? Standing stones? Wooden or stone circles? Other examples of extended ekphrasis similar to that of the shield of Achilles?
-
-
bugs.launchpad.net bugs.launchpad.net
-
This is actively being worked on - for those interested you can follow the progress in https://github.com/snapcore/snapd/pull/10836
-
-
stackoverflow.com stackoverflow.com
-
Manually reorder the reactive declaration statements, especially when there's an implicit dependency of the order of execution.
-
if you put the reactive statement $: validate(inputValue); after the function updateInputValue declaration, it's working as expected:
-
-
blog.viktomas.com blog.viktomas.com
-
I watched Christian from Zettelkasten.de taking notes from a book. He’s a professional note-taker, and it still took him two hours to take four notes in the first video - it does take forever to make good permanent notes.
An example of someone taking notes in public to model the process. Also an example of the time it takes to make notes.
Has Dan Allosso (@danallosso) done something along these lines as an example on his YouTube channel?
-
- Oct 2021
-
www.medrxiv.org www.medrxiv.org
-
Follmann, D., & Fay, M. (2021). Vaccine Efficacy at a Point in Time (p. 2021.02.04.21251133). https://doi.org/10.1101/2021.02.04.21251133
-
-
-
Another option is the use the functional library Ramda, while the syntax may be a bit different from the Ruby and Pure JS version, I find it to be more declarive: list = [null, "say", "kenglish", "co", null] R.reject(R.isNil, list) // return new array [ 'say', 'kenglish', 'co' ]
-
-
-
We will also show you how to de-link your Chrome profile from your Google account(s) by stopping Chrome from syncing with Google in the first place. This will help keep your Chrome profile separate from your Google account and enhance your online privacy.
-
To do that, Chrome automatically links your Chrome profile to a Google account when you sign in to any Google service on the web. That helps Google deliver a ‘seamless experience’ across all devices by letting you sync your history, bookmarks, passwords, etc., across multiple devices. Meanwhile, privacy-conscious users see this as a major threat to their online privacy and advise users to remove their Google account from Chrome.
-
As mentioned already, Chrome automatically signs you in to your Google account every time you sign into a Google service, like Gmail, YouTube, Google Photos, etc. It also links your current Chrome profile to that account. While Google says that it does so to offer a ‘seamless experience’, it is a privacy nightmare for many users.
-
-
www.ghacks.net www.ghacks.net
-
Some Chrome users may like the new functionality as it makes it easier for them to sign in or out of Chrome and Google on the Web. Others may dislike it for privacy and user-choice reasons. Think about it, if you sign in to Chrome you are automatically recognized by any Google property on the web as that Google user.
-
-
-
Boyd made use of the Second Law of Thermodynamics. In a closed system, entropy always increases and everything moves towards chaos. Energy spreads out and becomes disorganized. Although Boyd’s notes do not specify the exact applications, his inference appears to be that a fighter pilot must be an open system or they will fail. They must draw “energy” (information) from outside themselves or the situation will become chaotic. They should also aim to cut their opponent off, forcing them to become a closed system.
In che modo la [[Seconda legge della termodinamica]] si applica all' #incertezza e come possiamo utilizzarla come parte del modello OODA Loop ?
Il principio afferma che all'interno di un sistema chiuso tutto tenderà sempre all'entropia. Per questo bisogna essere dei sistemi aperti acquisendo ogni volta informazioni dal contesto, così da evitare che la situazione diventi caotica.
Tags
Annotators
URL
-
-
dl.acm.org dl.acm.org
-
We propose a tri-relationship embedding framework TriFN, which models publisher-news relations and user-news interactions simultaneously for fake news classification. We conduct experiments on two real-world datasets, which demonstrate that the proposed approach significantly outperforms other baseline methods for fake news detection.
It was said in the conclusion that the TriFN can have a good fake news detection performance in the early stage of information dissemination because of the interactions in social media. User credibility was also mentioned since low credibility users tend to spread fake news.
This means that users play a big part in detecting and reducing fake news in social media. Let's be responsible to only share credible news articles and report the misleading ones.
-
-
www.netflix.com www.netflix.comNetflix1
-
Lost in Translation
In the film, Lost in Translation, Bob and Charlotte begin their conversation learning what each of them is doing in Tokyo.
Bob: What do you do?
Charlotte: I’m not sure yet, actually. I just graduated last spring.”
Bob: What did you study?
Charlotte: Philosophy.
Bob: Yeah, there’s a good buck in that racket.
Charlotte: (Laughs.) Yeah. Well, so far it’s pro bono.
(33:45)
Edge Effects
In ecology, edge effects are changes in population or community structures that occur at the boundary of two or more habitats. Areas with small habitat fragments exhibit especially pronounced edge effects that may extend throughout the range. As the edge effects increase, the boundary habitat allows for greater biodiversity.
-
-
gschemistry.pressbooks.com gschemistry.pressbooks.com
-
The breakdown of water involves a rearrangement of the atoms in water molecules into different molecules,
Why would hydrogen and oxygen need to be separated for?
-
-
archive.nytimes.com archive.nytimes.com
-
Employees were ‘free’ to negotiate a work contract to their liking within the context of accepting the ‘prerogatives’ of managers to organised and remunerate their efforts as they saw fit (Fox, 1974).
Tags
Annotators
URL
-
-
human.libretexts.org human.libretexts.org
-
I see a man's pink tongue razing the horizon
metaphor
Tags
Annotators
URL
-
-
can.newonnetflix.info can.newonnetflix.info
-
Comedies, Dramas, Independent Films Lost in Translation
Tags
Annotators
URL
-
-
www.sciencedirect.com www.sciencedirect.com
-
O’Brien, T. C., Palmer, R., & Albarracin, D. (2021). Misplaced trust: When trust in science fosters belief in pseudoscience and the benefits of critical evaluation. Journal of Experimental Social Psychology, 96, 104184. https://doi.org/10.1016/j.jesp.2021.104184
-
-
www.mobindustry.net www.mobindustry.net
-
IT Technology Trends Driving Logistics in 2021
-
-
www.tandfonline.com www.tandfonline.com
-
Davies, A., Seaton, A., Tonooka, C., & White, J. (2021). Covid-19, online workshops, and the future of intellectual exchange. Rethinking History, 25(2), 224–241. https://doi.org/10.1080/13642529.2021.1934290
-
- Sep 2021
-
pluralistic.net pluralistic.net
-
The willingness to trade other peoples' fundamental rights for preferential tax treatment fits neatly into all three of these, as does the delusion that somehow this can be resolved with sufficient "personal responsibility."
We know enough about psychology and behavioral economics to know that "personal responsibility" is not going to save us.
This is in even higher relief when we see laws applied in unclosed systems or where other loopholes exist to help the privileged. Frank Wilhot's idea sums things up fairly well:
"Conservatism consists of exactly one proposition, to wit: There must be in-groups whom the law protects but does not bind, alongside out-groups whom the law binds but does not protect."
-
-
threadreaderapp.com threadreaderapp.com
-
https://threadreaderapp.com/thread/1442414902761689088.html Problematic is "problematic". This meta discussion does what it advises.
-
-
-
I'm trying to help in some way by bringing these issues to light so a discussion about them can take place.
-
-
Local file Local file
-
Shove et al
Some research is referenced to just by their names.
-
(Fletcher, 2014;Gwilt & Rissanen, 2011; Leerberg, Riisberg, & Boutrup, 2010;Rissanen & McQuillan, 2016
Many in-text citations are used just in the background. They include author's names and years instead of superscripts (which I think would be easier to read but oh well).
-
-
inst-fs-iad-prod.inscloudgate.net inst-fs-iad-prod.inscloudgate.net
-
The Virginians needed labor, to grow corn for subsistence, to grow tobaccofor export. They had just figured out how to grow tobacco, and in 1617 theysent off the first cargo to England. Finding that, like all pleasurable drugstainted with moral disapproval, it brought a high price, the planters, despitetheir high religious talk, were not going to ask questions about something soprofitable.
Told from this perspective and with the knowledge of the importance of the theory of First Effective Settlement, is it any wonder that America has grown up to be so heavily influenced by moral and mental depravity, over-influenced by capitalism and religion, ready to enslave others, and push vice and drugs? The founding Virginians are truly America in miniature.
Cross reference: Theory of First Effective Settlement
“Whenever an empty territory undergoes settlement, or an earlier population is dislodged by invaders, the specific characteristics of the first group able to effect a viable, self-perpetuating society are of crucial significance for the later social and cultural geography of the area, no matter how tiny the initial band of settlers may have been.” “Thus, in terms of lasting impact, the activities of a few hundred, or even a few score, initial colonizers can mean much more for the cultural geography of a place than the contributions of tens of thousands of new immigrants a few generations later.” — Wilbur Zelinsky, The Cultural Geography of the United States, Englewood Cliffs, NJ: Prentice-Hall, 1973, pp. 13–14.
-
-
inst-fs-iad-prod.inscloudgate.net inst-fs-iad-prod.inscloudgate.net
-
I had seen other residents at the Y.M.C.A. do
Blending in to belong to the new place, Copying actions, behaviour
-
-
www.bmj.com www.bmj.com
-
Male, Victoria. ‘Menstrual Changes after Covid-19 Vaccination’. BMJ 374 (16 September 2021): n2211. https://doi.org/10.1136/bmj.n2211.
-
-
-
Hors des heures de cours, les étudiants peuvent intervenir sur des forums écrits ou vidéos. Ils peuvent également utiliser un outil d'annotation collaborative comme Hypothesis pour partager leurs notes de lecture.
Rough translation: Outside of class time, students can contribute to written forums or videos. They can also use a collaborative annotation tool such as Hypothesis to share their reading notes.
-
-
duckduckgo.com duckduckgo.com
-
https://hypothes.is/search?q=tag:'0-origined+index'
Tags
Annotators
URL
-
-
www.nytimes.com www.nytimes.com
-
One last resource for augmenting our minds can be found in other people’s minds. We are fundamentally social creatures, oriented toward thinking with others. Problems arise when we do our thinking alone — for example, the well-documented phenomenon of confirmation bias, which leads us to preferentially attend to information that supports the beliefs we already hold. According to the argumentative theory of reasoning, advanced by the cognitive scientists Hugo Mercier and Dan Sperber, this bias is accentuated when we reason in solitude. Humans’ evolved faculty for reasoning is not aimed at arriving at objective truth, Mercier and Sperber point out; it is aimed at defending our arguments and scrutinizing others’. It makes sense, they write, “for a cognitive mechanism aimed at justifying oneself and convincing others to be biased and lazy. The failures of the solitary reasoner follow from the use of reason in an ‘abnormal’ context’” — that is, a nonsocial one. Vigorous debates, engaged with an open mind, are the solution. “When people who disagree but have a common interest in finding the truth or the solution to a problem exchange arguments with each other, the best idea tends to win,” they write, citing evidence from studies of students, forecasters and jury members.
Thinking in solitary can increase one's susceptibility to confirmation bias. Thinking in groups can mitigate this.
How might keeping one's notes in public potentially help fight against these cognitive biases?
Is having a "conversation in the margins" with an author using annotation tools like Hypothes.is a way to help mitigate this sort of cognitive bias?
At the far end of the spectrum how do we prevent this social thinking from becoming groupthink, or the practice of thinking or making decisions as a group in a way that discourages creativity or individual responsibility?
-
-
news.slashdot.org news.slashdot.org
-
(They blame Chrome's "feature" addition treadmill, where "they keep adding stupid kitchen sinks for the sole and only purpose to make others unable to keep up.")
-
-
finiteeyes.net finiteeyes.net
-
Build pathways between communal and private work. Too often, we celebrate one or the other, but thinking actually works best when it has the opporunity to be done both in private and alongside other people. Proximity and ease of movement between the two modes matters. If a person can work on ideas alone and privately for a little while, then easily bring those ideas to a group, then move back to the private space, and continue this cycle as necessary, the thinking will be better.
This is a model that is tacitly being used by the IndieWeb in slowly developing better social media and communication on the web.
-
-
-
To enable PostCSS, Sass or Less support, add CSS support first and then add the relevant pre-processors:
-
-
-
If you fail to changes this, you may experience performance issues, and other bugs related to multiple copies of React, like issue 2932.
-
-
en.wikipedia.org en.wikipedia.org
-
https://en.wikipedia.org/wiki/Minimal_group_paradigm
Worth looking up the relationship of this to the creation of institutional racism and potential means of dismantling it.
-
-
www.youtube.com www.youtube.com
-
The idea of Geisha has a similarity to tummelling, but doesn't translate as well to English for historical reasons. (This is similar to Anthony Bourdain's take/discussion of Geisha in his series A Cook's Tour season 1, episode 2: "Dining with Geishas").
Tummeller is someone who bridges the in groups and the outgroups.
-
https://youtu.be/qYsMtroVLeA?t=287
The big thing that I want to talk about here is out groups. This is a phenomenon that we that we see, which is that it's very very easy for people to decide that someone else is not like them they're different and they should be shunned and talked about.
This is the minimal group paradigm. Thanks to Rashmi for giving that term. [It] says the smallest possible difference will be magnified into in group and an outgroup. Kevin Marks, Web 2.0 Expo NY 09: "...New Words You Need to Know to Understand the Web"
Perhaps we can decrease the levels of fear and racism in our society by tummelling? By bringing in outsiders, treating them with dignity and respect within your own group of friends, you can help to normalize their presence by decreasing the irrational fears that others have built up and carry with them about these supposed outsiders.
-
-
ecampusontario.pressbooks.pub ecampusontario.pressbooks.pub
-
This video was very educating. It was especially crazy to me to learn that about a language a week dies.
-
-
learn-eu-central-1-prod-fleet01-xythos.s3.eu-central-1.amazonaws.com learn-eu-central-1-prod-fleet01-xythos.s3.eu-central-1.amazonaws.com
-
the primary causes of extreme poverty are immaterial, theylie in certain deficiencies in education, organization, and discipline”(p. 159). Poorcountries, in his view, did not need more technology or physical infrastructure ormore foreign aid to eliminate poverty.
-
-
stackoverflow.com stackoverflow.com
-
Node Sass does not yet support your current environment indicates that the version of node-sass you are trying to run is not compatible with the version of node installed.
-
-
ubuntuforums.org ubuntuforums.org
-
sudo apt-get autoclean sudo apt-get autoremove sudo apt-get clean sudo apt update sudo apt-get dist-upgrade --fix-missing sudo apt-get dist-upgrade --fix-broken sudo apt full-upgrade sudo apt -f install dpkg --configure -a
-
-
thoughtbot.com thoughtbot.com
-
most recently the release of ActiveStorage in Rails 5.2
-
- Aug 2021
-
woodzwolfy.medium.com woodzwolfy.medium.comMedium1
-
Tips to fix HP Printer Error State Windows 10
-
-
-
Now consider we want to handle numbers in our known value set: const KNOWN_VALUES = Object.freeze(['a', 'b', 'c', 1, 2, 3]) function isKnownValue(input?: string | number) { return typeof(input) === 'string' && KNOWN_VALUES.includes(input) } Uh oh! This TypeScript compiles without errors, but it's not correct. Where as our original "naive" approach would have worked just fine. Why is that? Where is the breakdown here? It's because TypeScript's type system got in the way of the developer's initial intent. It caused us to change our code from what we intended to what it allowed. It was never the developer's intention to check that input was a string and a known value; the developer simply wanted to check whether input was a known value - but wasn't permitted to do so.
-
-
github.com github.com
-
therefore in practice it's a bit academic to worry about which lines inside that block the compiler should be happy or unhappy about. From falsehood, anythihng follows. So the compiler is free to say "if the impossible happens, then X is an error" or "if the impossible happens, then X is not an error". Both are valid (although one might be more or less surprising to developers).
-
I wrote down how I understand it using layman's terms for anyone finding this issue in the future.
-
-
charlypoly.com charlypoly.com
-
It means that when having a type guard:TypeScript and JavaScript runtime are tied to the same behaviour.
-
Inside the if statement, TypeScript will assume that amount cannot be anything else than a string, which is true also at the runtime thanks to typeof JavaScript operator.
-
-
stackoverflow.com stackoverflow.com
-
forum.artofmemory.com forum.artofmemory.com
-
I would have seen memory palaces as a simplified version of songlines, but my Indigenous colleague has now pointed out that sometimes songlines are taught before the person goes on Country - that’s how they navigated: teach the songlines and you can then travel knowing where food sources and waterholes are. So my theory is falling down already. But the songline always involves movement (not always dance), song, narrative and a mesh of genres of information.
Verification of the anecdotal evidence I mentioned before. Teaching of songlines without actually being on Country.
-
-
kimberlyhirsh.com kimberlyhirsh.com
-
https://kimberlyhirsh.com/micro-camp-21
Can't wait for the video to share with others.
-
-
www.pasadenastarnews.com www.pasadenastarnews.com
- Jul 2021
-
github.com github.com
-
Auto-Detect & install BigCommerce's stencil-cli Auto-Detect & install Meteor Auto-Detect & install Shopify's themekit
Simpler option: https://github.com/apollographql/apollo-server/blob/main/.envrc
-
-
in.pinterest.com in.pinterest.com
-
typhoid diet chart in hindi(health and disease)
typhoid diet chart in hindi(health and disease):in this pin you can see about typhoid diet chart in hindi and food in typhoid. food should be eat and not in typhoid
-
-
www.flowerbrackets.com www.flowerbrackets.com
-
Multiple inheritance is one of the object oriented feature where a class or a sub class can inherit features from more than one parent class or super class.
https://www.flowerbrackets.com/multiple-inheritance-in-java/
-
-
-
Can A.I. Grade Your Next Test?Neural networks could give online education a boost by providing automated feedback to students.
What problem is AI solving in education?
Tags
Annotators
URL
-
-
blog.appsignal.com blog.appsignal.com
-
the interesting thing here is that there are comments that say which concern depends on which.
-
-
www.frontiersin.org www.frontiersin.org
-
Yap, Suhui, Albert Lee, Li-Jun Ji, Ye Li, and Ying Dong. “Cultural Differences in People’s Psychological Response to COVID-19.” Frontiers in Psychology 0 (2021). https://doi.org/10.3389/fpsyg.2021.636062.
-
-
medium.com medium.com
-
It’s fun but when would we ever use things like this in actual code?When it’s well tested, commented, documented, and becomes an understood idiom of your code base.We focus so much on black magic and avoiding it that we rarely have a chance to enjoy any of the benefits. When used responsibly and when necessary, it gives a lot of power and expressiveness.
-
-
news.ycombinator.com news.ycombinator.com
-
as a more experienced user I know one can navigate much more quickly using a terminal than using the hunt and peck style of most file system GUIs
As an experienced user, this claim strikes me as false.
I often start in a graphical file manager (nothing special, Nautilus on my system, or any conventional file explorer elsewhere), then use "Open in Terminal" from the context menu, precisely because of how much more efficient desktop file browsers are for navigating directory hierarchies in comparison.
NB: use of a graphical file browser doesn't automatically preclude keyboard-based navigation.
-
-
stackoverflow.com stackoverflow.com
-
Wow, Aaron himself just answered it!
-
answered Oct 12 '09 at 18:28
-
-
boffosocko.com boffosocko.com
-
Not all the ancients are ancestors.
I'll definitely grant this and admit that there may be independent invention or re-discovery of ideas.
However, I'll also mention that it's far, far less likely that any of these people truly invented very much novel along the way, particularly since Western culture has been swimming in the proverbial waters of writing, rhetoric, and the commonplace book tradition for so long that we too often forget that we're actually swimming in water.
It's incredibly easy to reinvent the wheel when everything around you is made of circles, hubs, and axles.
-
-
about.gitlab.com about.gitlab.com
-
Epics can contain both issues and epics as children
-
-
www.theguardian.com www.theguardian.com
-
the Guardian. ‘10% of People of Colour in Great Britain Would Refuse Covid Jab - YouGov Data’, 7 March 2021. http://www.theguardian.com/society/2021/mar/07/10-of-uks-people-of-colour-would-refuse-covid-vaccine-yougov-data.
-
-
tracydurnell.com tracydurnell.com
-
Is it useful to the person writing to know that what’s written may be readable by others and that spurs deeper thought in reflection – or is that more blog-like than note-like?
I often find that doing the work in public ups the quality and effort I put into the thing because I know there's at least the off-hand chance that someone else might read it.
Generally this means a better contextualized product for myself when I come back to revisit it later, even if no one else saw it. Without it, sometimes my personal scribbles don't hold up when I revisit them, and I can't tell what I had originally intended because I didn't flesh out the idea enough.
-
- Jun 2021
-
www.migrationencounters.org www.migrationencounters.org
-
hypothes.is hypothes.is
-
Giving peers permission to engage in dialogue about race and holding a lofty expectation that they will stay engaged in these conversations throughout the semester or year is the first of the four agreements for courageous conversation. While initially, some participants may be eager to enter into these conversations, our experience indicates that the more personal and thus risky these topics get, the more difficult it is for participants to stay committed and engaged." Singleton and Hays
-
"Many North American music education programs exclude in vast numbers students who do not embody Euroamerican ideals. One way to begin making music education programs more socially just is to make them more inclusive. For that to happen, we need to develop programs that actively take the standpoint of the least advantaged, and work toward a common good that seeks to undermine hierarchies of advantage and disadvantage. And that, inturn, requires the ability to discuss race directly and meaningfully. Such discussions afford valuable opportunities to confront and evaluate the practical consequences of our actions as music educators. It is only through such conversations, Connell argues, that we come to understand “the real relationships and processes that generate advantage and disadvantage”(p. 125). Unfortunately, these are also conversations many white educators find uncomfortable and prefer to avoid."
Tags
- As music educators we do our best to include cultures and introduce new ideas because of what is relevant at the time. Yet we don't go to the next level and dive into the importance of "why" and how we as citizens along with our students can get involved and take positive actions. This may be due to the lack of autonomy in the classroom and/or time to teach in general.
- Having explicit and concise rules for the conversation is important to create a safe space for more participation in the tougher questions. The facilitator has to be consistently doing this.
Annotators
URL
-
-
psyarxiv.com psyarxiv.com
-
Gronfeldt, B., Cichocka, A., Cislak, A., Sternisko, A., & Irem. (2021). A Small Price to Pay: National Narcissism Predicts Readiness to Sacrifice In-group Members to Defend the In-group’s Image [Preprint]. PsyArXiv. https://doi.org/10.31234/osf.io/7fmrx
-
-
jpetazzo.github.io jpetazzo.github.io
-
but we think that it’s simpler, as well as easier to write and to maintain, to go with the single actor model of Docker.
-
-
github.com github.com
-
Please keep in mind that the GitHub issue tracker is not intended as a general support forum, but for reporting bugs and feature requests.
-
-
mywiki.wooledge.org mywiki.wooledge.org
-
Bash (like all Bourne shells) has a special syntax for referring to the list of positional parameters one at a time, and $* isn't it. Neither is $@. Both of those expand to the list of words in your script's parameters, not to each parameter as a separate word.
-
-
superuser.com superuser.com
-
Instead of using a for loop, which will fail on spaces unless you redefine the IFS variable, I would recommend using a while loop combined with find.
-
-
github.com github.com
-
Happy Third Birthday #24728!
-
-
graphql-ruby.org graphql-ruby.org
-
This kind of error handling does express error state (either via HTTP 500 or by the top-level "errors" key), but it doesn’t take advantage of GraphQL’s type system and can only express one error at a time.
-
-
graphql-ruby.org graphql-ruby.org
-
(Always call super to inherit the default behavior.)
-
-
github.com github.com
-
I think it's just a bad English/mis-translation problem. I'm guessing @pmmmwh assumed 'master' meant like 主 in 奴隸主 (slave owner/master). Actually a better translation would be 師 like 功夫大師 (Kung Fu master). The specimen copies are made from.
-
-
twitter.com twitter.com
-
So ActionCable needs Redis! Is this the first time Rails is aligning with a vendor product? Why not abstract it like AR/AJ?
-
-
evilmartians.com evilmartians.com
-
For example, Database Cleaner for a long time was a must-have add-on: we couldn’t use transactions to automatically rollback the database state, because each thread used its own connection; we had to use TRUNCATE ... or DELETE FROM ... for each table instead, which is much slower. We solved this problem by using a shared connection in all threads (via the TestProf extension). Rails 5.1 was released with a similar functionality out-of-the-box.
-
-
www.mutuallyhuman.com www.mutuallyhuman.com
-
This is why for a recent Angular+Rails project we chose to use a testing stack from the backend technology’s ecosystem for e2e testing.
-
We chose to define the frontend in one technology stack (Angular+TypeScript/JavaScript) and the backend in another (Ruby+Ruby on Rails), but both came together to fulfill a singular product vision.
-
-
blogs.bmj.com blogs.bmj.com
-
The BMJ. ‘Left in Limbo—Barriers to Covid “Passports” for Trial Participants Will Deter People from Taking Part in Research’, 7 June 2021. https://blogs.bmj.com/bmj/2021/06/07/left-in-limbo-barriers-to-covid-passports-for-trial-participants-will-deter-people-from-taking-part-in-research/.
-
-
naildrivin5.com naildrivin5.com
-
It also makes it hard to centralize type coercions and default values.
-
-
disqus.com disqus.com
-
While rails does have nice CSRF protection, in my instance it limited me.
-
-
hacks.mozilla.org hacks.mozilla.org
-
if you just need a screenshot of a webpage, that’s built in:
-
-
themillions.com themillions.com
-
This is a phenomenal way to do a look back at a year in reading. I'll have to consider how to pull it off for myself this year.
-
-
-
Introduce behaviour that is likely to surprise users. Instead have due consideration for patterns adopted by other commonly-used languages.
-
-
stackoverflow.com stackoverflow.com
-
I see a 'virtual attribute' as something we're forced to implement when using frameworks, ORMs and the like. Something that lets us inject our code into the path of whatever metaprogramming has been put in place for us. In a simple PORO like this, I don't see how it has meaning; it's just a method. :)
Hmm, good point. Maybe so. Though I think I'm fine with calling it a virtual property here too. :shrug:
-
-
en.wikipedia.org en.wikipedia.org
-
DigiNotar was a Dutch certificate authority owned by VASCO Data Security International, Inc.[1][2] On September 3, 2011, after it had become clear that a security breach had resulted in the fraudulent issuing of certificates, the Dutch government took over operational management of DigiNotar's systems.[3]
Dutch Certificate Authority gets hacked.
-
-
science.sciencemag.org science.sciencemag.org
-
Lessler, J., Grabowski, M. K., Grantz, K. H., Badillo-Goicoechea, E., Metcalf, C. J. E., Lupton-Smith, C., Azman, A. S., & Stuart, E. A. (2021). Household COVID-19 risk and in-person schooling. Science, 372(6546), 1092–1097. https://doi.org/10.1126/science.abh2939
-
-
outdoors.stackexchange.com outdoors.stackexchange.com
-
You can watch videos, but videos can't watch you.
-
No article or video can replace qualified instruction and experience
-
-
-
ddrscott.github.io ddrscott.github.io
-
SQL is all about nested subqueries. It's hard to escape without creating views, but who has time to lookup that syntax and get their DBA's permission to run the DDL?!?
-
-
www.migrationencounters.org www.migrationencounters.org
-
In Miss S. class, I remember there were two boys who were nice to me, J___ and— what's his name? Sorry. I still know him. He's still a good friend of mine. O___. They both kind of spoke Spanish, so they kind of helped me out as well, but I wasn't allowed to speak to anyone. The teacher was not having it … She was extremely strict. I think she was the kind of teacher that should not have ever taken up teaching as a job because some people just don't have the vocation. Is that the word in English? They don't have that in them and I don't think she had it, but they helped out a lot. J___ and Osvaldo, thank you wherever you are now. I know O___ is getting married soon, so yes.
Time in US - Fitting in - making friends - primary education
-
-
msudenver.instructure.com msudenver.instructure.com
-
But, supposing all these conjectures to be false, you cannot contest the inestimable benefit which I shall confer on all mankind to the last generation, by discovering a passage near the pole to those countries, to reach which at present so many months are requisite; or by ascertaining the secret of the magnet, which, if at all possible, can only be effected by an undertaking such as mine.
Finally (in this second paragraph), we again have insight into the political and scientific issues of the day: the search for the famed "Northwest Passage" (big, big deal) and the awareness of a major source of danger for polar navigation: the distortion produced in magnetic equipment as one came nearer to the source, at the pole.

It is obvious, is it not?, that most people are motivated by social goods: fame, power, money, and prestige. Because that is the world we live in.
It's all about the Benjamins! Then and now!
-
-
psyarxiv.com psyarxiv.com
-
Polack, R. G., Sened, H., Aubé, S., Zhang, A., Joormann, J., & Kober, H. (2021). Connections during Crisis: Adolescents’ social dynamics and mental health during COVID-19. PsyArXiv. https://doi.org/10.31234/osf.io/x94kv
-
- May 2021
-
kit.svelte.dev kit.svelte.dev
-
To set multiple cookies in a single set of response headers, you can return an array:
-
-
devonzuegel.com devonzuegel.com
-
I have received a lot of positive feedback for noting my epistemic status and effort at the top of my posts. This is hilarious, because I originally started using these as a hack in order to publish half-baked ideas that I'd otherwise not feel comfortable sharing.
This is an interesting hack for getting one to hit the publish button.
I wonder if people have renamed the "publish" button in their CMS to make hitting it easier?
My own anecdotal evidence is that hitting it often can certainly make it seem trivial, particularly if one is posting their status updates to their site along with everything else.
<small><cite class='h-cite via'>ᔥ <span class='p-author h-card'>Maggie Appleton</span> in A Brief History & Ethos of the Digital Garden (<time class='dt-published'>05/28/2021 18:08:16</time>)</cite></small>
-
-
maggieappleton.com maggieappleton.com
-
Gwern.net was one of the earliest and most consistent gardeners to offer meta-reflections on their work. Each entry comes with:topic tagsstart and end datea stage tag: draft, in progress, or finisheda certainty tag: impossible, unlikely, certain, etc.1-10 importance tagThese are all explained in their website guide, which is worth reading if you're designing your own epistemological system.
I've noticed that Dan Mackinlay has some public notebooks with an interesting system for indicating knowledge process too.
-
-
syslog.ravelin.com syslog.ravelin.com
-
Before we dive into the details of the actual migration, let’s discuss the theory behind it.
-
-
github.com github.com
-
None of the existing repository filtering tools did what I wanted; they all came up short for my needs. No tool provided any of the first eight traits below I wanted, and all failed to provide at least one of the last four traits as well:
-
-
en.wikipedia.org en.wikipedia.org
-
As the token is unique and unpredictable, it also enforces proper sequence of events (e.g. screen 1, then 2, then 3) which raises usability problem (e.g. user opens multiple tabs). It can be relaxed by using per session CSRF token instead of per request CSRF token.
-
-
joyvillegurugram.com joyvillegurugram.com
-
Joyville Gurgaon Sector 102
Shapoorji Pallonji Joyville Sector 102 Gurgaon is a premium residential project in close proximity to Delhi. Contemporary construction, state-of-the-art amenities, top-notch security, and huge green expanse make the project highly demanding. Nestled right close to major establishments like hospitals, schools, malls, and offices.
-
-
sanjaykumarro.com sanjaykumarro.com
-
typhoid fever treatment and food.
typhoid ke lakshan.टाइफायड बुखार की शुरवात तेज बुखार से होती है और बुखार का तापमान 103-104 डिग्री फ़ारेनहाइट,39-40 डिग्री सेल्सियस हो जाता है।बुखार चडता है फीर उतरता है, सर्दी लगना, सिरदर्द होना, पेट मे दर्द होना, उलटी लगना और इसी के साथ-साथ दस्त भी होने लगते है। मांसपेशियों और हड्डीयो मे दर्द, कमजोरी आना, भुख ना लगना और शरीर पर छोटे-छोटे दाने भी होने लगते है।
-
Kya hota hai typhoid ke lakshan?
typhoid ke lakshan.टाइफायड बुखार की शुरवात तेज बुखार से होती है और बुखार का तापमान 103-104 डिग्री फ़ारेनहाइट,39-40 डिग्री सेल्सियस हो जाता है।बुखार चडता है फीर उतरता है, सर्दी लगना, सिरदर्द होना, पेट मे दर्द होना, उलटी लगना और इसी के साथ-साथ दस्त भी होने लगते है। मांसपेशियों और हड्डीयो मे दर्द, कमजोरी आना, भुख ना लगना और शरीर पर छोटे-छोटे दाने भी होने लगते है।
-
Causes of typhoid in hindi (टाइफायड के कारण)
Causes of typhoid in hindi टाइफायड बुखार एक इंफेक्शन है। इसमे पेट मे इंफेक्शन होता है। टाइफायड को मियादी बुखार और मोतीझरा भी कहते है।ये बुखार वातावरण मे सबसे ज्यादा होने वाला रोग है। यह बुखार साल्मोनेला टाइफी नामक बैक्टीरिया से होता है।
girl with high fever, causes of typhoid in hindi girl with high fever, causes of typhoid in hindi यह बुखार गँदा खाना और गँदा पानी पीने से भी होता है, बासि खाना खाने से भी होता है,
क्योंकि बासि खाने मे इस बैक्टीरिया के होने की संभवनाये भड जाती है।
खाने की समय सीमा समाप्त होने पर खाना खाने से यह बुखार हो सकता है,
और या तो बीमार व्यक्ति का झुढा खाना या पानी पीने से भी य बुखार होता है।
रसोई घर साफ ना होने पर, सामानया बुखार की देख बाल ना करने पर भी य बुखार हो सकता है।और यह बुखार जब भी होता है जब व्यक्ति वाशरूम से बाहर आने पर अच्छे से हाथ नही धोता और टाइफायड का बुखार एक व्यक्ति से दुसरे व्यक्ति मे फलता है।these are causes of typhoid in hindi.
-
about typhoid in hindi
about typhoid in hindi. टाइफाइड बुखार एक विशिष्ट प्रकार का साल्मोनेला के कारण एक जीवाणु संक्रमण है।
-
-
academic.oup.com academic.oup.com
-
SARS-CoV-2 positive children
Some children present with severe secondary effects in response to COVID-19, similar to Kawasaki disease, termed multisystem inflammatory disease in children (MIS-C). MIS-C patients present with higher frequencies of CD4+ and CD8+ T cells and lower levels of IL-17A, ESDN and TNF-β (1, 2, 3, 4). Additionally, children with MIS-C demonstrate an increase in IgG antibodies but low IgM antibodies (2). Data suggests that binding of autoantibodies to proteins involved in immune cell signalling and in within the vasculature might explain the autoimmune reactivity contributing to MIS-C pathology (2, 4).
1)Verdoni L, Mazza A, Gervasoni A, Martelli L, Ruggeri M, Ciuffreda M, et al. An outbreak of severe Kawasaki-like disease at the Italian epicentre of the SARS-CoV-2 epidemic: an observational cohort study. Lancet. 2020;395(10239):1771-8.
2)Consiglio CR, Cotugno N, Sardh F, Pou C, Amodio D, Rodriguez L, et al. The Immunology of Multisystem Inflammatory Syndrome in Children with COVID-19. Cell. 2020;183(4):968-81 e7.
3) Vella L, Giles JR, Baxter AE, Oldridge DA, Diorio C, Kuri-Cervantes L, et al. Deep Immune Profiling of MIS-C demonstrates marked but transient immune activation compared to adult and pediatric COVID-19. medRxiv. 2020.
4) Gruber CN, Patel RS, Trachtman R, Lepow L, Amanat F, Krammer F, et al. Mapping Systemic Inflammation and Antibody Responses in Multisystem Inflammatory Syndrome in Children (MIS-C). Cell. 2020;183(4):982-95 e14.
-
-
brainbaking.com brainbaking.com
-
A relatively comprehensive view of Wouter Groeneveld's commonplacing workflow. There are a few bits missing here and there, but he's got most of the bigger basics down that a majority of people seem to have found and discovered.
He's got a strong concept of indexing, search, and even some review, which many miss. There's some organic work toward combinatorial thought, but only via the search piece.
I should make a list of the important pieces for more advanced versions to have. I've yet to see any articles or work on this.
-
-
psyarxiv.com psyarxiv.com
-
Imada, H., & Mifune, N. (2021). Pathogen Threat and In-Group Cooperation. PsyArXiv. https://doi.org/10.31234/osf.io/kebyd
-
-
prestigegroupnoida150.in prestigegroupnoida150.in
-
Prestige Sector 150 Noida
Prestige Group Sector 150 in Noida is the latest project of a well-known real estate builder i.e Prestige group’s pioneer to yield one of the best residential property in Noida including 2/3/4 BHK luxury & lavish apartments with great amenities. There are lots of residential facilities such as Vaastu compliant design, double-height entrance lobby, Tower heights- G+19 & G+22, and facing green landscape. etc. Apart from that, you can also get state-of-the-art facilities such as a green area, swimming pool, clubhouse, children play area, power backup, etc.
-
-
insilico.com insilico.com
-
20 targets for validation that we narrowed down to one novel intracellular target
one out of 20 targets was selected for further study. The target is an intracellular target, but the target is not disclosed.
-
The target novelty and disease association scoring was assessed by a natural language processing (NLP) engine, which analyses data from millions of data files, including patents, research publications, grants, and databases of clinical trials
Method and data In Silico used for target identification
-
-
doctorow.medium.com doctorow.medium.com
-
The genius of the blog was not in the note-taking, it was in the publishing. The act of making your log-file public requires a rigor that keeping personal notes does not. Writing for a notional audience — particularly an audience of strangers — demands a comprehensive account that I rarely muster when I’m taking notes for myself. I am much better at kidding myself my ability to interpret my notes at a later date than I am at convincing myself that anyone else will be able to make heads or tails of them.Writing for an audience keeps me honest.
I've seen this sentiment before as well.This is also well attested in writing code too.
Writing for the public keeps you honest and makes one put more work into the product than they otherwise might.
-
-
hiphopfoundations.org hiphopfoundations.org
-
The Kay-Gees
"I Believe in Music" is a 1970 song written and recorded by Mac Davis and later included on his second album I Believe in Music.
-
-
mijn.bsl.nl mijn.bsl.nl
-
orchitis
Orchitis of orchiditis is een ontsteking van de testes. Orchitis wordt veelal veroorzaakt door SOA's als chlamydia en gonorroe. Bij het doormaken van de bof door jongens vanaf de puberteit is orchitis een veel geziene complicatie.
-
-
stackoverflow.com stackoverflow.com
-
Why, it's a pleasure, and thank you kindly; glad to have been of help! =)
-
-
twitter.com twitter.com
-
ReconfigBehSci. (2020, November 13). RT @nicebread303: Level up @zotero with these 2 plugins: - @scite: Gives you 3 new cols: Mentioning, Supporting, Disputing (https://t.co/I… [Tweet]. @SciBeh. https://twitter.com/SciBeh/status/1328008909299257346
-
-
www.campaignmonitor.com www.campaignmonitor.com
-
So The Screener really just acts as a second layer of consent—almost like a confirmed opt in.
-
The difference is that this happens in the email client, not at the subscription step. Why is this a big deal? Because, even though they just subscribed to your email, there’s a chance your email won’t get a thumbs up.
-
-
stackoverflow.com stackoverflow.com
-
But in the dark world of HTML email, where the motto is "code like it's 1996" because Outlook uses the rendering engine from MS Word and Gmail removes almost everything, every method for making two elements overlap that I can think of is unsuitable due to poor client support
-
-
hashnode.com hashnode.com
-
HTML in emails is somehow in a forgotten world and is about lots of years behind us.
-
-
content.myemma.com content.myemma.com
-
Embedded CSS: This style is becoming more popular with the rise of mobile and responsive emails. Embedded CSS codes are determined in one place of an email, generally in the <head> section as a <style>. Some email servers still strip the information out of this section, which can cause display problems.
-
-
css-tricks.com css-tricks.com
-
Although a lot of email development is stuck in the past, that doesn’t mean we can’t modernize our campaigns right along with our websites. Many of these tips can be baked right into your email boilerplate or code snippets, allowing you to create more accessible HTML emails without too much thought.
-
Please have a look at (in same order)
-
-
www.gkogan.co www.gkogan.co
-
Email require their own flavor of HTML and CSS. Want to have rows or columns in your layout? You'll have to use <table> tags—a method long buried by web developers. There's also no support for external stylesheets, element position styling, and so on...
-
-
www.multiplikatoren-projekt.peoplemanagement.uni-muenchen.de www.multiplikatoren-projekt.peoplemanagement.uni-muenchen.de
-
verbs in conjugation VII
-
- Apr 2021
-
psyarxiv.com psyarxiv.com
-
Ahuvia, I., Sung, J., Dobias, M., Nelson, B., Richmond, L., London, B., & Schleider, J. L. (2021, April 25). College student interest in teletherapy and self-guided mental health supports during the COVID-19 pandemic. https://doi.org/10.31234/osf.io/8unfx
-
-
commercialpropertiesnoida.com commercialpropertiesnoida.com
-
food courts
Superb construction, exclusive design, and modern architecture are some of the unique features of the project Gulshan One129 project recently launched by Gulshan Homz. From office space to commercial food court space in Noida, the mall caters to all your requirements. Each retail shop is excellently designed for better visibility and space utilization. If you are looking for a commercial property in Noida sector 129, book your space now and get the possession on or before June 2021.
-
-
store.steampowered.com store.steampowered.com
-
All in all, get this game when it's not on sale so you can pay full price for this gem!!!
-
-
store.steampowered.com store.steampowered.com
-
wrote this review initially to accommodate a requirement for the Summer Sale 2019 event
-
-
constitution.congress.gov constitution.congress.gov
-
cept as
Angrily, I begin annotating in the thing called "written word" this second attempt at noting the significance of the words "13a" and the end of slavery with this day, 4/22/2021.
It's 40 years after the "Novus Ordo Seclorum" speech heralding a "new order of the ages" and 60 years after the Kennedy speech about a ruthless monolithic conspiracy; all relating to what apparently is Latin for "Unicorn" and my own interpretation of these words:
Legatus, Semper Fi, Babylon the Great, Medusa
Specifically a "fusion of law and land" that actually marks this place and this document as something like a connection between "living" and plain old ink on paper.
Legislature, Legislation, Legacy of Novus Ordo ... and "at us" Legatus--something like the Monolithic "thing of ten" that also today God noted was "a funny thing to shun" in connection to the word "Phoenecian" which also links another silly bird and "CIA" to something Earthene
A legatus (anglicised as legate) was a high-ranking Roman military officer in the Roman Army, equivalent to a modern high-ranking general officer. Initially used to delegate power, the term became formalised under Augustus as the officer in command of a legion.
From the times of the Roman Republic, legates received large shares of the military's rewards at the end of a successful campaign. This made the position a lucrative one, so it could often attract even distinguished consuls or other high-ranking political figures within Roman politics (e.g., the consul Lucius Julius Caesar volunteered late in the Gallic Wars as a legate under his first cousin once removed, Gaius Julius Caesar).
... amd I recall a time before C3P0 had a silver leg and gold was a thing of "carbonite steel ethereality"
-
-
www.carbonbrief.org www.carbonbrief.org
-
New research shows that lake "stratification periods" – a seasonal separation of water into layers – will last longer in a warmer climate. These longer periods of stratification could have "far-reaching implications" for lake ecosystems, the paper says, and can drive toxic algal blooms, fish die-offs and increased methane emissions.
Eine neue Studie ergibt, dass die globale Erhitzung die Ökosysteme von Seen weltweit schädigt. Die Periode, in der sich das Wasser in Schichten teilt, dauert länger. Dramatische Veränderungen mit Schäden für die Biodiversität lassen sich z.B. in den großen amerikanischen Seen beobachten. Kurzbericht: Climate Change Could Cause ‘Irreversible Impacts’ to Lakes - EcoWatch, Details: Climate change could cause ‘irreversible impacts’ to lake ecosystems | Carbon Brief, Studie: Phenological shifts in lake stratification under climate change | Nature Communications
-
-
rampages.us rampages.us
-
Nevertheless, Milton does not force the issue concerningbelief in God's mere existence, for that is something he simply assumes; forhim God's existence is a premise much more than a conclusion (see YP 6:130-2). In spite of the radical polarities of belief about God in ParadiseLost, its humans and devils and angels are united in this: they all believethat he is
I'm glad this is brought up. I think its really interesting that Milton, a devout Christian, was able to write something that retold a story from the bible- the characters being Christian icons- without needing to convince the readers that God is real/Christianity is the path to salvation. His intention was not to convert readers, but to write! By carefully crafting PL's character relationships, the importance of faith is naturally conveyed through the dialogue between all characters.
-
-
github.com github.com
-
Please do not directly email any Sidekiq committers with questions or problems. A community is best served when discussions are held in public.
-
-
-
about the eonxr platform that might work in terms of education so um a little bit of background i've been a faculty member for nearly 35 years and so my main interest here is in the learning
Tags
Annotators
URL
-
-
news.elearninginside.com news.elearninginside.com
-
The core problem here is that we really don’t know exactly how the brain learns information or skills. And for what we do know, we don’t have the ability to directly observe when it is happening in the brain. That would be painful and dangerous. So we have to rely on something external to the brain serving as evidence that learning happened.
What we call assessment is really an attempt to create a proxy indicator for what we call learning.
It seems weird to think of it that way; we don't really understand learning so we create tasks for students to complete in the hope those tasks somehow give us some insight into the thing that we don't really understand.
-
quizzes, tests, exams, assignments – none of those can measure learning or skill mastery. Not directly at least.
-
exams or tests themselves are not essential
-
This article is ostensibly a response to the use of proctoring software in higher education.
But in order to do that properly the author has also delved into learning and assessment.
It's a well-written piece that questions some of our taken-for-granted assumptions around assessment.
-
-
www.kickstarter.com www.kickstarter.com
-
These are games that make arguments and encourage discussion. They don't shy away from difficult subjects.
-
-
sariazout.substack.com sariazout.substack.com
-
This post articulates a lot of what I've been thinking about for the past 18 months or so, but it adds the additional concept of community integration.
Interestingly, this aligns with the early, tentative ideas around what the future of In Beta might look like as a learning community, rather than a repository of content.
-
-
-
But in all this incongruous abundance you'll certanly find the links to expect It's just what is wanted: the tool, which is traditionally used to communicate automatically with interactive programs. And as it always occurs, there is unfortunately a little fault in it: expect needs the programming language TCL to be present. Nevertheless if it doesn't discourage you to install and learn one more, though very powerful language, then you can stop your search, because expect and TCL with or without TK have everything and even more for you to write scripts.
-
-
empty.sourceforge.net empty.sourceforge.net
-
In some cases empty can be the simplest replacement for TCL/expect or other similar programming tools because empty:
-
-
linusakesson.net linusakesson.net
-
-
This is hard because Apple does not want you to and a failed installation might render the ipad useless.
-
-
psyarxiv.com psyarxiv.com
-
Morrow, Alison, Sara Jenks, and Becky Batchelor. ‘The Effect of Antibody Test Result Knowledge on Transmission Reducing Behaviours’. PsyArXiv, 13 April 2021. https://doi.org/10.31234/osf.io/unm7r.
-
-
meta.stackexchange.com meta.stackexchange.com
-
No longer a free trial but free forever
-
-
store.steampowered.com store.steampowered.com
-
It is, however, priced at a measly two dollars, less on sale or in a bundle, so only the whiniest of whiners should find reason to complain here. Suffice it to say, self-professed haters of short games and "walking simulators" should abandon this Store page at once, and spend that spare couple of bucks on yet another "skin" for that first-person multiplayer frag-fest you've already wasted three thousand hours of your life on. (Whoops, is my cynicism showing? Sorry about that. I've got nearly two thousand hours up on Left 4 Dead 2 myself, so I'm hardly one to judge. That said, I would never spend money on "skinning" a character I don't even get to see, haha.)
-
-
reallifemag.com reallifemag.com
-
unsuspecting childlikeness
I'd also add [learned helplessness] (https://www.britannica.com/science/learned-helplessness) - the constant need for entertainment is definitely a problem, but if we take a deterministic view of these broader design trends the long-term ramifications are even more disturbing - the rise of Web 2.0 has seen a massive shift towards user-friendly platforms, but in addition to cultural infantilization we are seeing a significant decrease in tech literacy - and sometimes these trends manifest simultaneously. For instance, I'm writing this annotation in Chrome, but if I lose internet access my browser tab would allow me to play the endlessly addictive "Chrome Dino" browser game until my connection was restored - this is a fairly innocuous little easter egg (not coincidentally a term also used by Yelp UI designer Yoni De Beule in one of the articles I linked to above), but it does raise some broader questions about the amount of tech literacy and user autonomy these companies want us to have - features like these suggest that passivity is their preferred state for consumers, which is troubling.
-
My surprise that no one is insulted by this is quickly overtaken by surprise that Venmo is condoning alcohol consumption among kindergarteners, the only group in America who is routinely asked, with educational toys like Leapfrog, to match short words with pictures.
I appreciate what Barron is getting at here but I think he's taking an extremely contrarian stance to get at his point. Obviously Venmo is not condoning childhood alcohol consumption - a better and more nuanced take (which he alludes to elsewhere in the article) is that the conditions of modern life have prolonged adolescence for millennials (and generation z) - the traditional signifiers of adulthood are gone and the aesthetics of contemporary corporate app and internet design have adjusted to reflect this shift.
-
-
outline.com outline.com
-
This is a summary of the Alice's Adventures in Wonderland
-
-
www.homedepot.com www.homedepot.com
-
Full disclosure: I have been provided with a free Ryobi One + Cordless 4 gallon backpack chemical sprayer for review purposes. I don’t know anyone who works for the manufacturer and have no affiliation with Ryobi. The following review is my honest opinion and has not been influenced by the free product.
-
-
www.amazon.com www.amazon.com
-
I'm a real person and did NOT receive this item at a discount in lieu of a positive review. By clicking "helpful" at the bottom of this review, it will help move "real" reviews to the top. Thanks in advance.
-
-
store.steampowered.com store.steampowered.com
-
Planning note:
-
-
docdrop.org docdrop.org
-
a French institution is kind of interested in terms of sharing materials and open educational materials because there's way less opportunities for us to work with publisher materials there's just not the same amount of resources out there
One key hunch about differences between language communities.
Tags
Annotators
URL
-
-
www.kickstarter.com www.kickstarter.com
-
Academy Games has always prided itself in the quality of its rules. Most of our rules are taught in stages, allowing you to start playing as soon as possible without needing to read everything. We are very careful about the order we teach rules and rely heavily on graphics and pictures to facilitate understanding. We also include a large number of detailed picture examples, often with 3D renders, that help you understand the context of the rules.
-
-
guides.rubyonrails.org guides.rubyonrails.org
-
The hostname's first n segments, starting from the right (the TLD).
-
- Mar 2021
-
en.wikipedia.org en.wikipedia.org